In my previous blog post, I explained how to setup an Azure Traffic Manager. In there, I used GUI method to set it up. In this post I am going to show how we can set up Azure Traffic Manager using Azure PowerShell.
In this demo, I am going to demonstrate how we can use Azure traffic managers to improve the application/service performance by pointing users to the closest endpoint. This demo includes the following tasks,
1. Setup two new resource groups (East US, UK South)
2. Setup two new windows VM (East US, UK South)
3. Setup IIS with sample web page
4. Create a Traffic Manager profile
5. Add endpoints to Traffic Manager profile
6. Testing
Setup two new resource groups (East US, UK South)
Let’s go ahead and start the setup process by creating a new Azure resource group.
For the configuration process, I will be using Azure PowerShell. Therefore, please make sure you have an Azure PowerShell module installed. More info about it can find under https://docs.microsoft.com/en-us/powershell/azure/install-az-ps?view=azps-2.6.0
1. Launch PowerShell console and connect to Azure using Connect-AzAccount
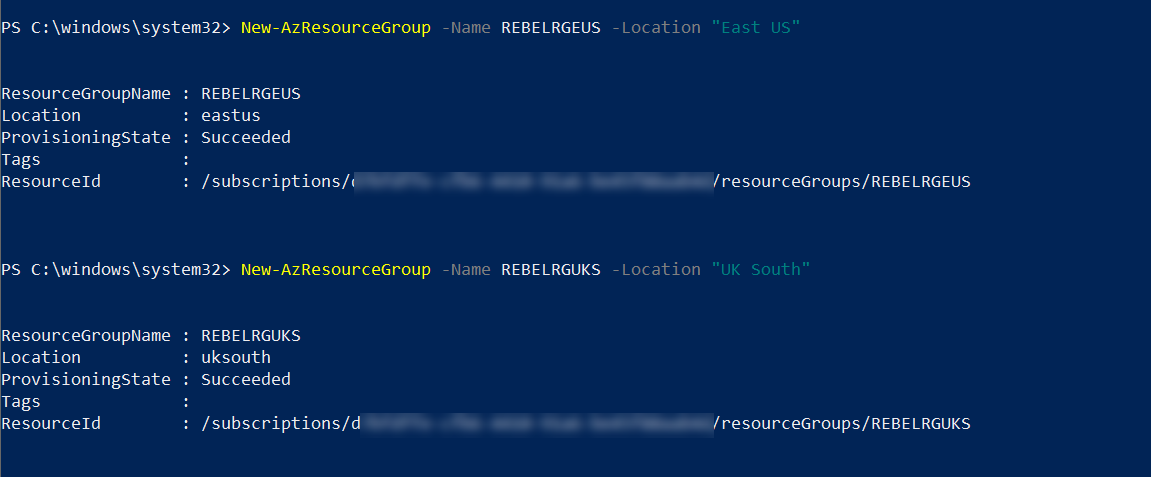
2. Then create a new resource group using,
New-AzResourceGroup -Name REBELRGEUS -Location “East US”
New-AzResourceGroup -Name REBELRGUKS -Location “UK South”
In the above, we are creating two resource groups. The first one called REBELRGEUS and it is created on East US Azure region.
The second group is called REBELRGUKS and it is created on UK South azure region.
Setup two new windows VM (East US, UK South)
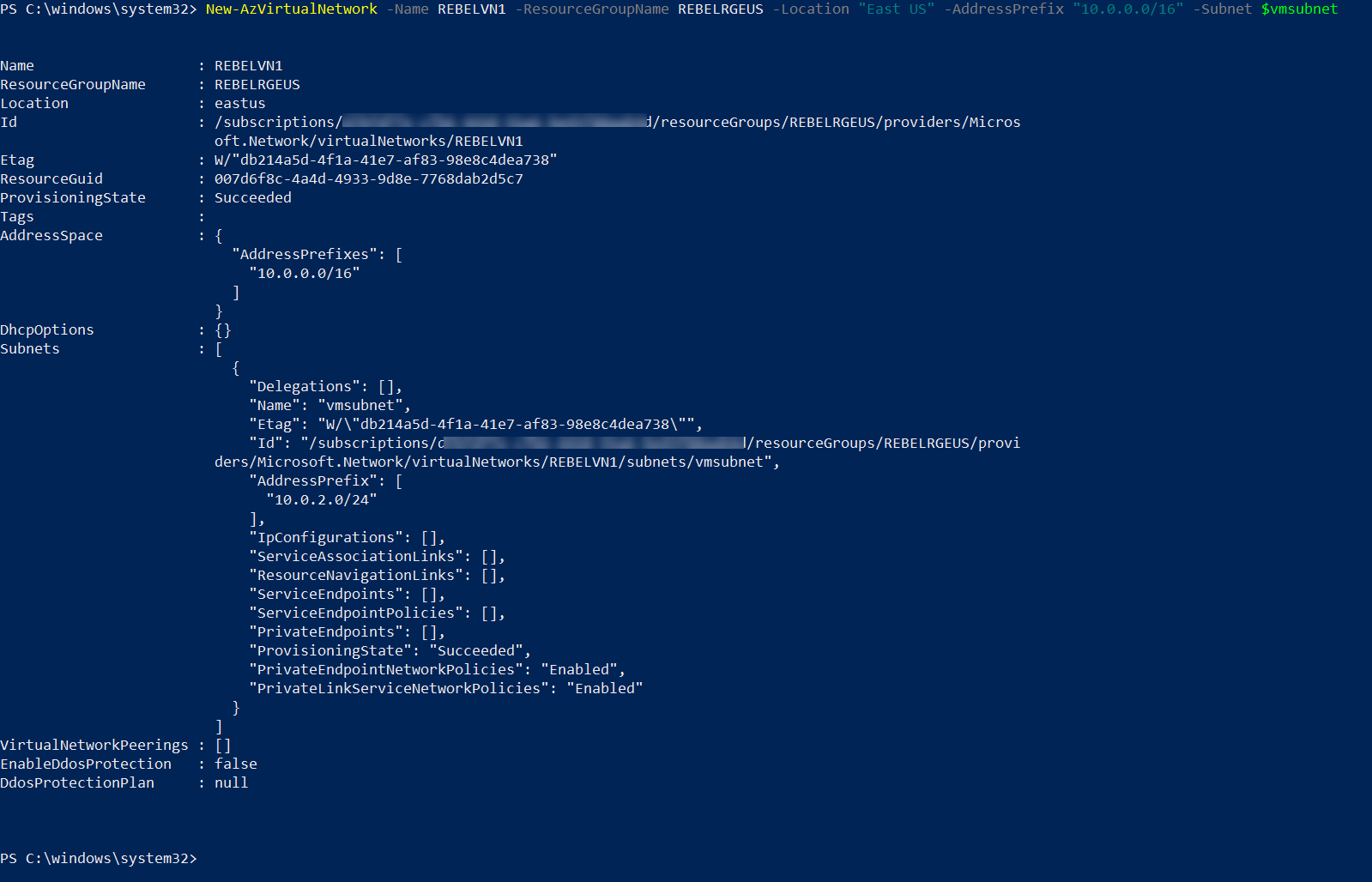
1. In this demo, I am going to use two back end servers. Before VM setup, let’s go ahead and create a new virtual network in REBELRGEUS resource group
$vmsubnet = New-AzVirtualNetworkSubnetConfig -Name vmsubnet -AddressPrefix “10.0.2.0/24”
New-AzVirtualNetwork -Name REBELVN1 -ResourceGroupName REBELRGEUS -Location “East US” -AddressPrefix “10.0.0.0/16” -Subnet $vmsubnet
In the above, REBELVN1 is the new virtual network name. It has 10.0.0.0/16 address space. It also has a new subnet 10.0.2.0/24 (vmsubnet) for virtual machines.
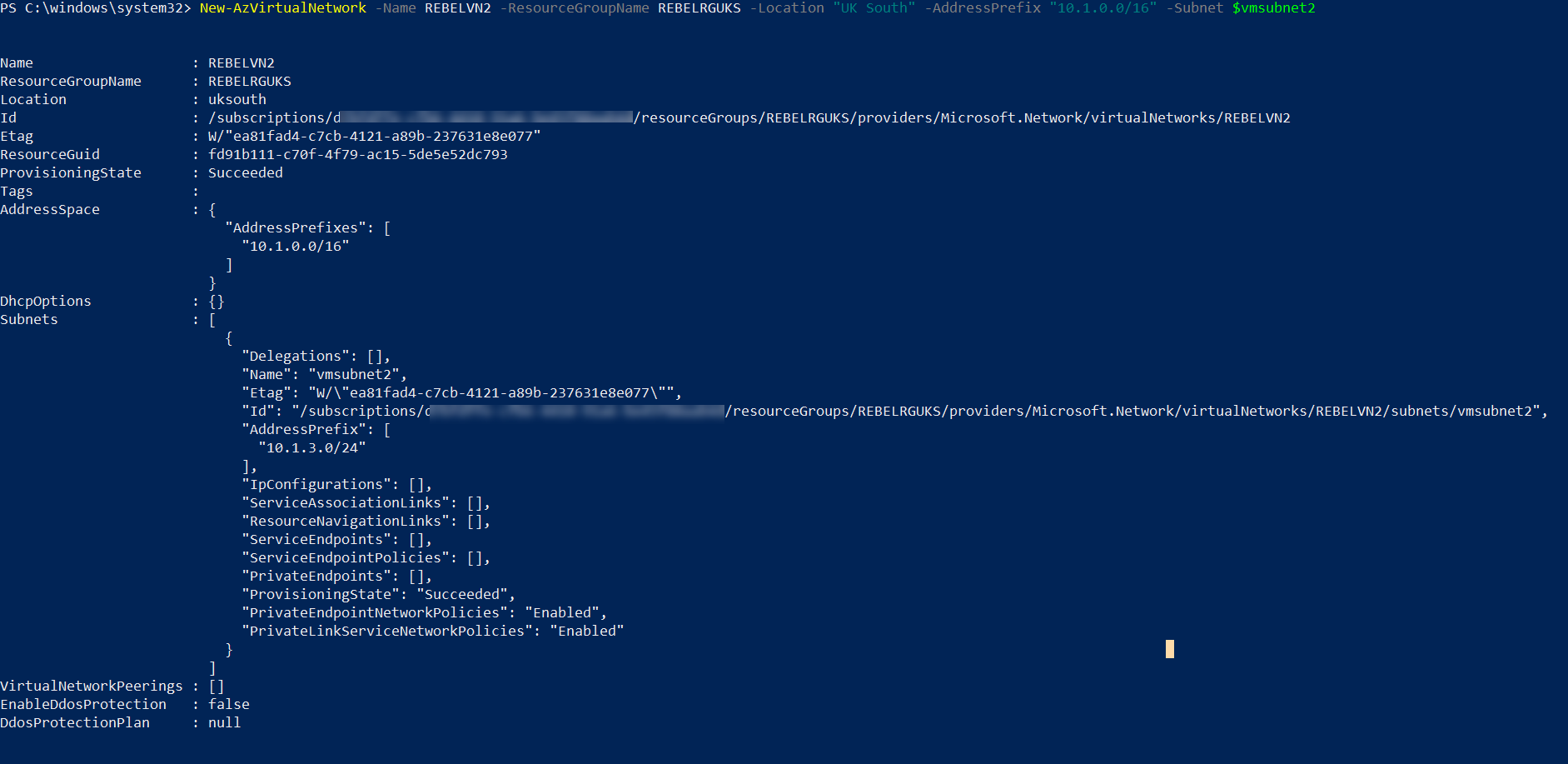
2. Then let’s go ahead and create another virtual network under REBELRGUKS resource group.
$vmsubnet2 = New-AzVirtualNetworkSubnetConfig -Name vmsubnet2 -AddressPrefix “10.1.3.0/24”
New-AzVirtualNetwork -Name REBELVN2 -ResourceGroupName REBELRGUKS -Location “UK South” -AddressPrefix “10.1.0.0/16” -Subnet $vmsubnet2
In the above, REBELVN2 is the new virtual network name. It has 10.1.0.0/16 address space. It also has a new subnet 10.1.3.0/24 (vmsubnet2) for virtual machines.
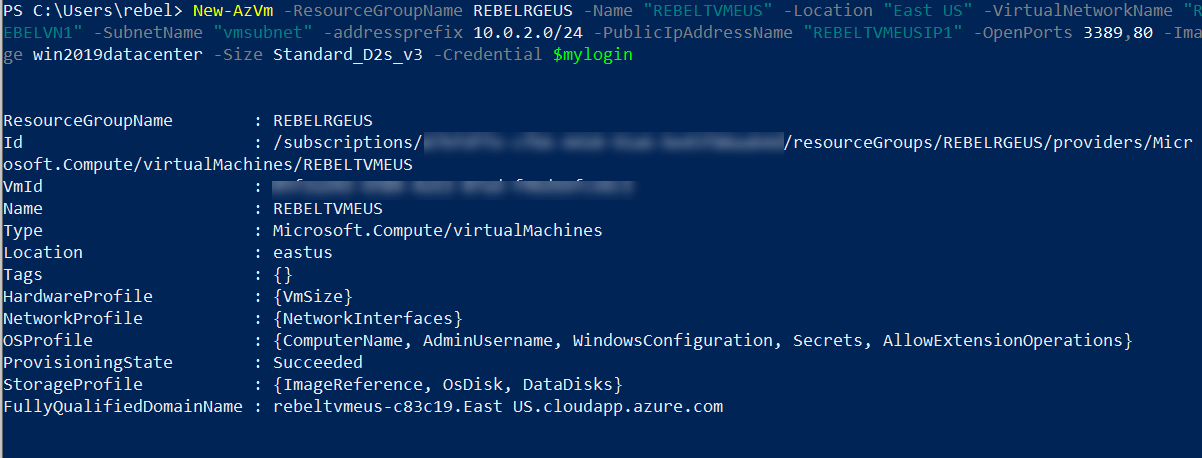
3. As the next step of the configuration, I am going to create a new virtual machine under REBELRGEUS resource group. This will be used for testing purposes.
$mylogin = Get-Credential
New-AzVm -ResourceGroupName REBELRGEUS -Name “REBELTVMEUS” -Location “East US” -VirtualNetworkName “REBELVN1” -SubnetName “vmsubnet” -addressprefix 10.0.2.0/24 -PublicIpAddressName “REBELTVMEUSIP1” -OpenPorts 3389,80 -Image win2019datacenter -Size Standard_D2s_v3 -Credential $mylogin
In the above, I am creating a virtual machine called REBELTVMEUS. It is running windows server 2019 data center edition. I have specified it using -Image parameter. It also using Standard_D2s_v3 vm size. For networking, it uses REBELVN1 virtual network and subnet 10.0.2.0/24. I also open port 3389 and 80 for external connectivity.
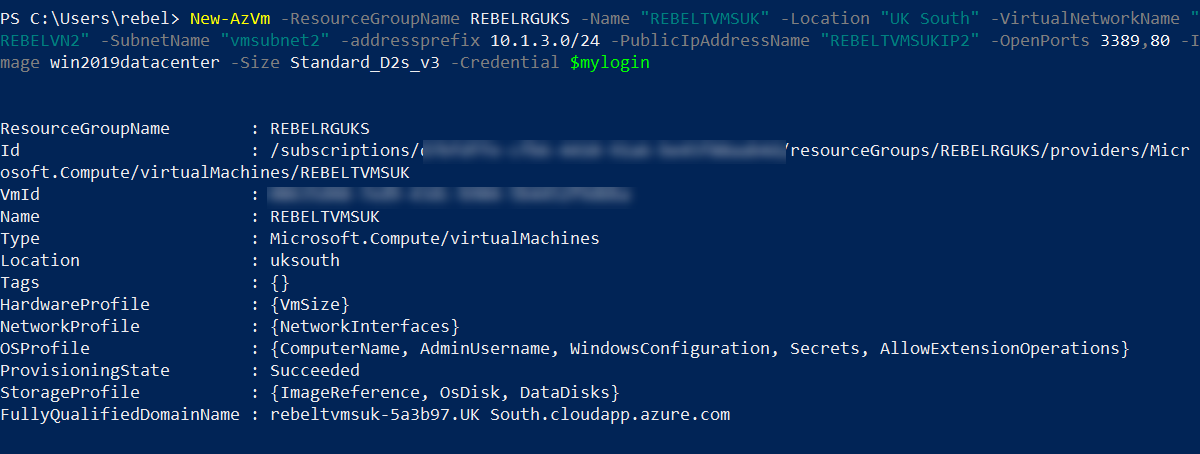
4. Same way, I am going to create a new virtual machine under REBELRGUKS resource group. This will also be used for testing purposes.
$mylogin = Get-Credential
New-AzVm -ResourceGroupName REBELRGUKS -Name “REBELTVMSUK” -Location “UK South” -VirtualNetworkName “REBELVN2” -SubnetName “vmsubnet2” -addressprefix 10.1.3.0/24 -PublicIpAddressName “REBELTVMSUKIP2” -OpenPorts 3389,80 -Image win2019datacenter -Size Standard_D2s_v3 -Credential $mylogin
In the above, I am creating a virtual machine called REBELTVMSUK. It is running windows server 2019 data center edition. I have specified it using -Image parameter. It also using Standard_D2s_v3 vm size. For networking, it uses REBELVN2 virtual network and subnet 10.1.3.0/24. Same as other VM, we need to open port 3389 & 80 for external access.
In the end, we have two virtual machines with the following config.
| Virtual Machine | Resource Group | Virtual Network | VM Subnet | IP Address |
| REBELTVMEUS | REBELRGEUS | REBELVN1 | vmsubnet | 10.0.2.4 |
| REBELTVMSUK | REBELRG2 | REBELVN2 | Vmsubnet2 | 10.1.3.4 |
Setup IIS with sample web page
Now we have two VMs running. For testing purposes, I am going to set up a simple IIS web page in both VMs. To do that,
1. Log in to VM as a local administrator
2. Open PowerShell Console as Administrator
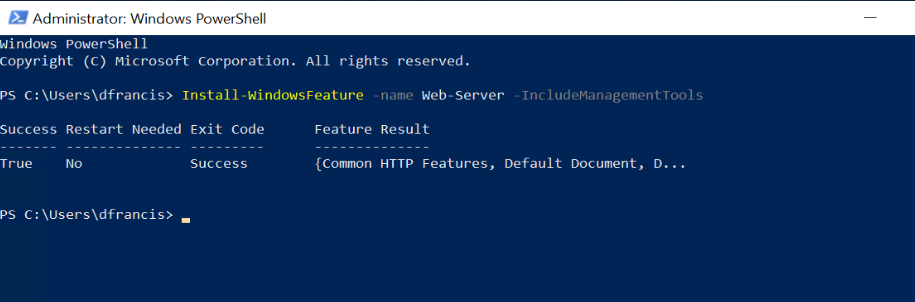
3. Run following to install the IIS role
Install-WindowsFeature -name Web-Server -IncludeManagementTools
4. Then remove default IIS page using,
remove-item C:\inetpub\wwwroot\iisstart.htm
5. As next step, create new content page using,
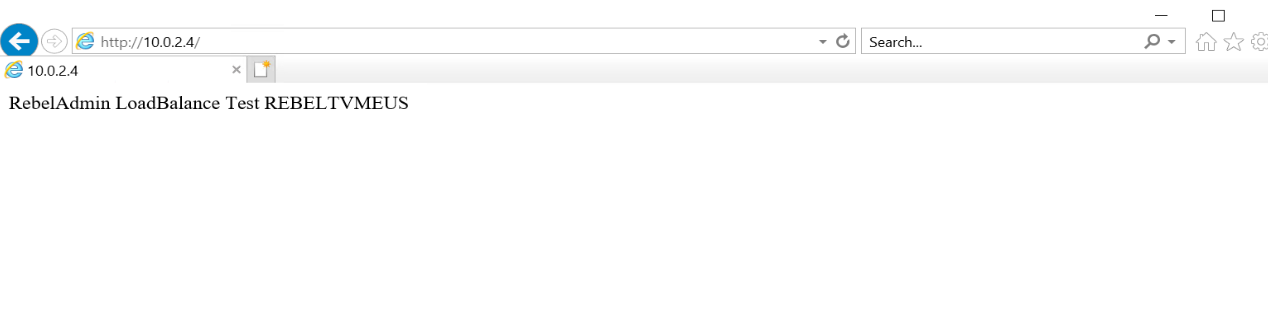
Add-Content -Path “C:\inetpub\wwwroot\iisstart.htm” -Value $(“RebelAdmin LoadBalance Test ” + $env:computername)
6. After that, we can test it via a web browser.
Create a Traffic Manager profile
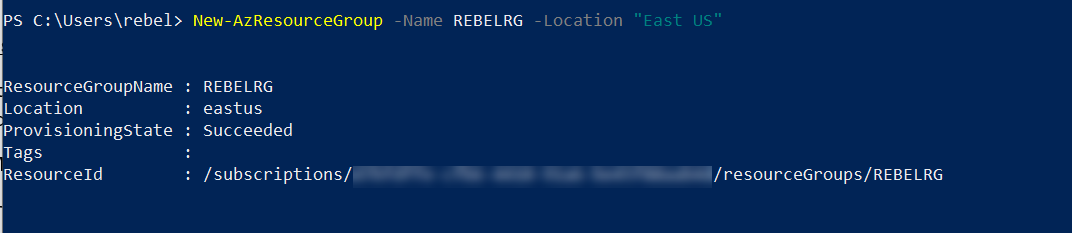
The next step of the configuration is to create the traffic manager profile. Let’s start this by creating new resource group for traffic manager profile.
New-AzResourceGroup -Name REBELRG -Location “East US”
After that let’s go ahead and create traffic manager profile using,
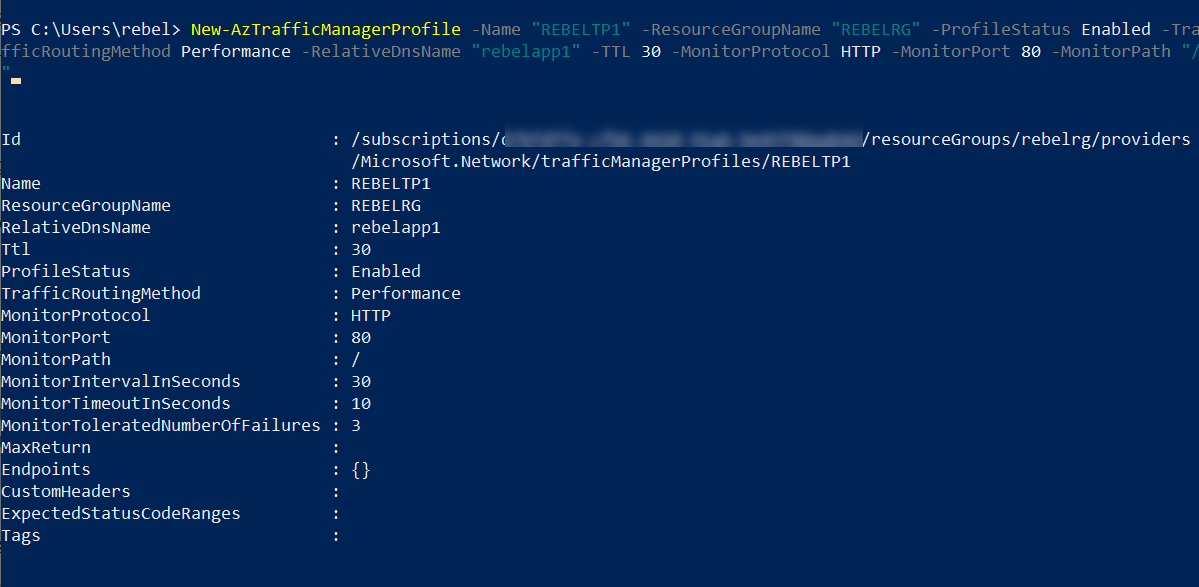
New-AzTrafficManagerProfile -Name “REBELTP1” -ResourceGroupName “REBELRG” -ProfileStatus Enabled -TrafficRoutingMethod Performance -RelativeDnsName “rebelapp1” -TTL 30 -MonitorProtocol HTTP -MonitorPort 80 -MonitorPath “/”
In above, the traffic manager profile name is REBELTP1. It is created under REBELRG resource group. The selected traffic routing method for the profile is Performance. This will allow users to connect to the nearest end point. The selected DNS name for the traffic profile is rebelapp1. This allows end users to connect to traffic profile using http://rebelapp1.trafficmanager.net. The monitor port for the profile is TCP port 80.
Add endpoints to Traffic Manager profile
After profile configuration, we need to add endpoints we created before. Before we add the endpoints, first we need to find the resource ids of the public ip addresses associated with the VMs.
$usvm = (Get-AzResource -Name REBELTVMEUSIP1 -ResourceType Microsoft.Network/publicIPAddresses).id
$ukvm = (Get-AzResource -Name REBELTVMSUKIP2 -ResourceType Microsoft.Network/publicIPAddresses).id
Above commands collect the virtual machine resource id values.
After that we can add end point using,
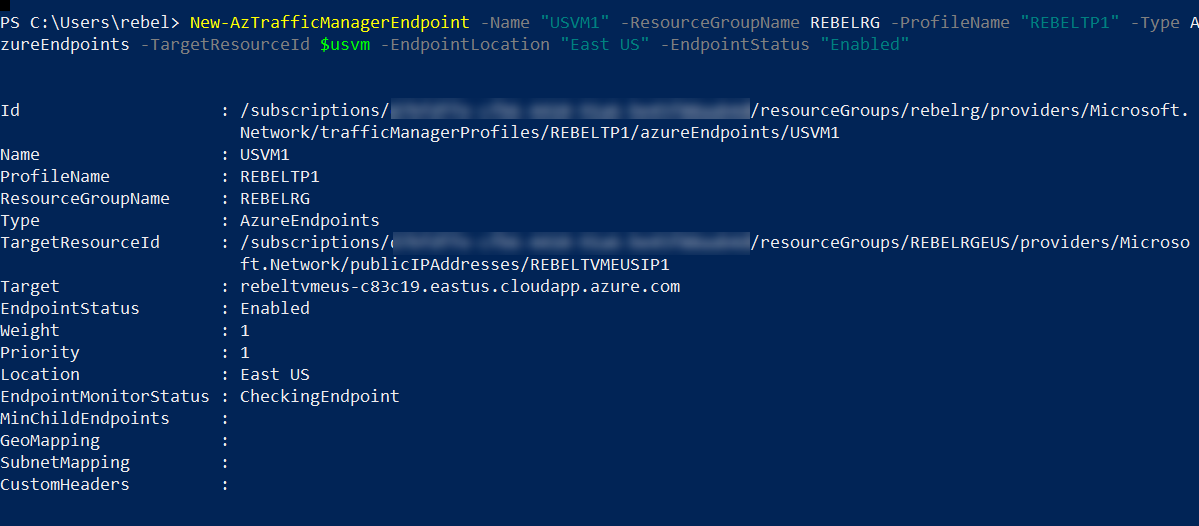
New-AzTrafficManagerEndpoint -Name “USVM1” -ResourceGroupName REBELRG -ProfileName “REBELTP1” -Type AzureEndpoints -TargetResourceId $usvm -EndpointLocation “East US” -EndpointStatus “Enabled”
In above, end point name is USVM1, It is adding public IP address of REBELTVMEUS VM.
New-AzTrafficManagerEndpoint -Name “UKVM1” -ResourceGroupName REBELRG -ProfileName “REBELTP1” -Type AzureEndpoints -TargetResourceId $ukvm -EndpointLocation “UK South” -EndpointStatus “Enabled”
In above, end point name is UKVM1, It is adding public IP address of REBELTVMSUK VM.
Testing
The configuration part is completed now. Let’s go ahead and check if it is working as expected.
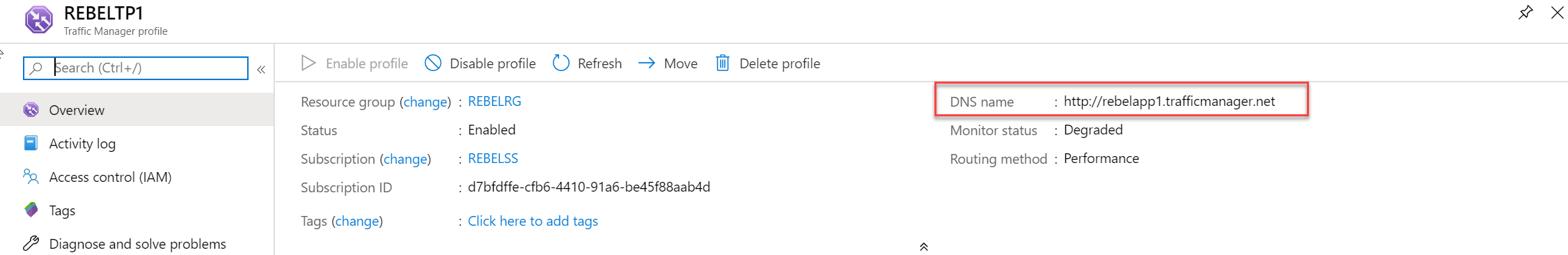
First, we need to verify the traffic manager profile URL. This is the URL we need to use for testing.
We can find this URL in the traffic manager profile.
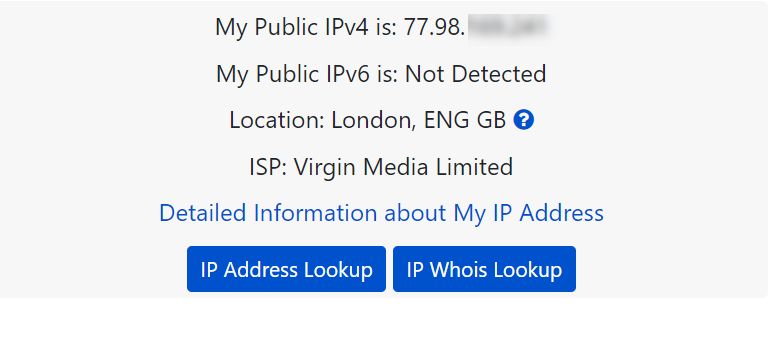
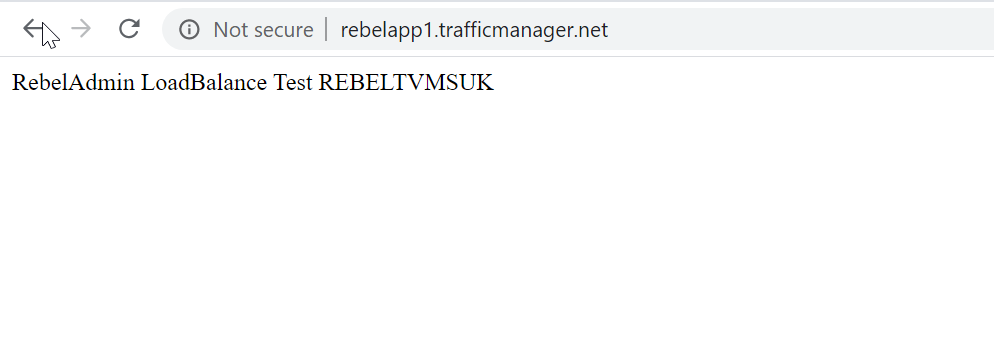
I have a pc which is connecting from UK.
When I access the URL from this particular pc, I can see its loading page from the VM we created in UK South region.
As we can see it is successfully directing traffic to the VM which has the lowest latency.
This marks the end of this blog post. If you have any further questions about this feel free to contact me on rebeladm@live.com also follow me on twitter @rebeladm to get updates about new blog posts.