Azure AD B2B allows organizations to share company applications and other services/resources with external users. Before, this external user should have one of following to initiate connection with the organization who sents the B2B inivitation.
1) Azure AD Account
2) Microsoft Account
3) Google Federation ( More info : http://www.rebeladmin.com/2019/02/step-step-guide-setup-federation-google-azure-ad-b2b/ )
Email one-time passcode authentication (OTP) feature now allow B2B users to authenticate using one time passcode if they cant use one of the above methods. Once OTP is issued it is only valid for 30 minutes. If user didn’t use it with in 30 minutes, he/she need to request new OTP code for authentication. Once authenticated, session will be valid for 24 hours.
This feature is still under public preview. OTP users must use the https://myapps.microsoft.com/?tenantid=<tenant id> , https://portal.azure.com/<tenant id> or https://myapps.microsoft.com/<verified domain>.onmicrosoft.com when they authenticate. In above <tenant id> should replaced with the organization’s tenant ID. <verified domain> should replace using the default domain details.
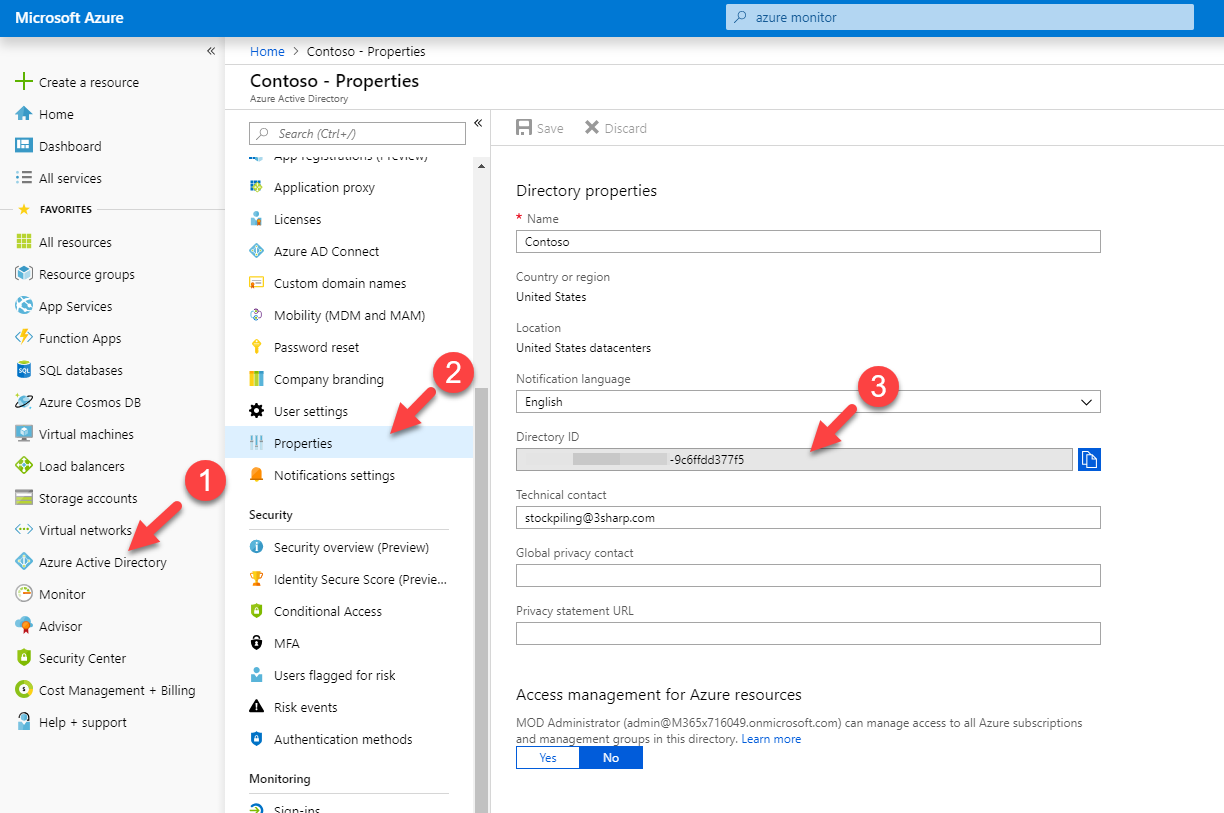
You can find the tenant id using,
Azure Portal | Azure Active Directory | Properties | Directory ID
Let’s see how we can enable this new OTP feature.
To do that,
1) Log in to Azure portal as Global Administrator
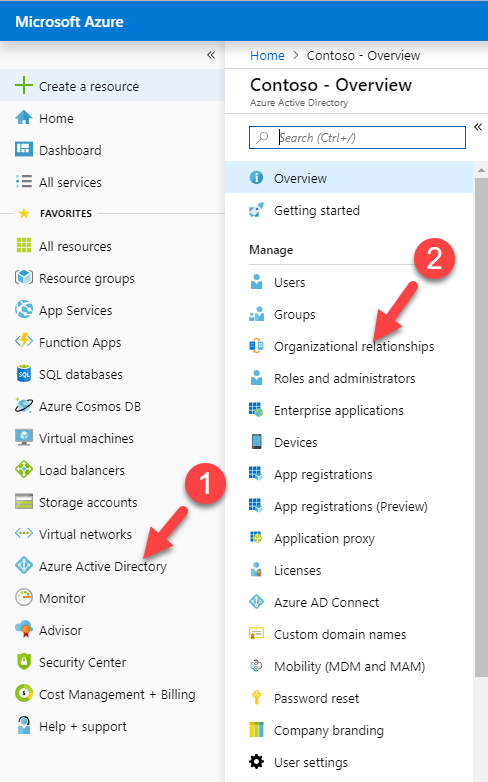
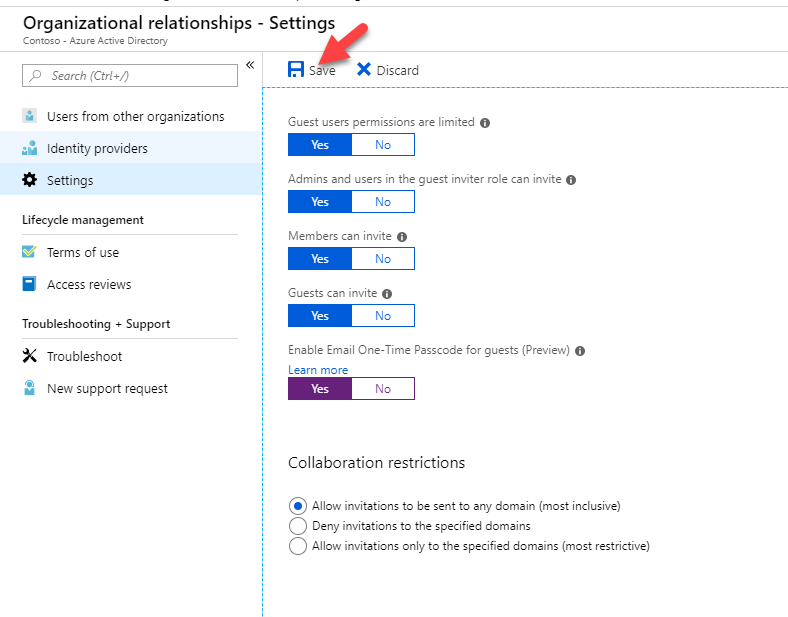
2) Go to Azure Active Directory | Organizational relationships
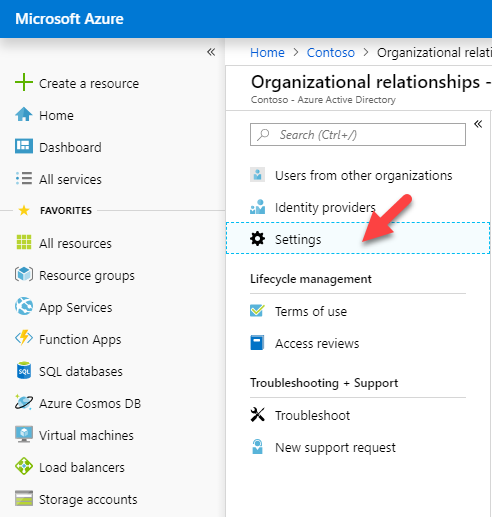
3) Then go to Settings
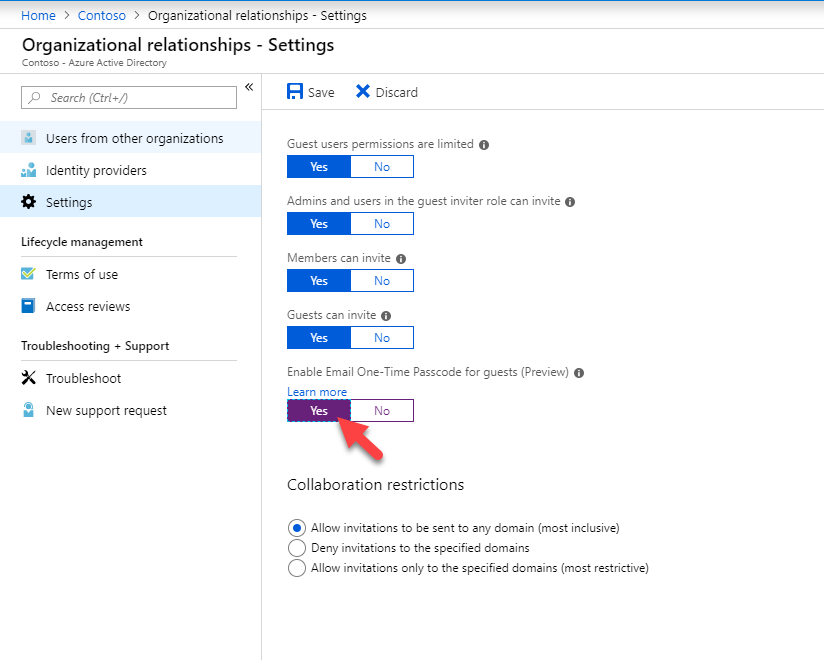
4) In new window, select Yes under Enable Email one-time passcode for guests (preview)
5) Then click on Save, to apply new settings.
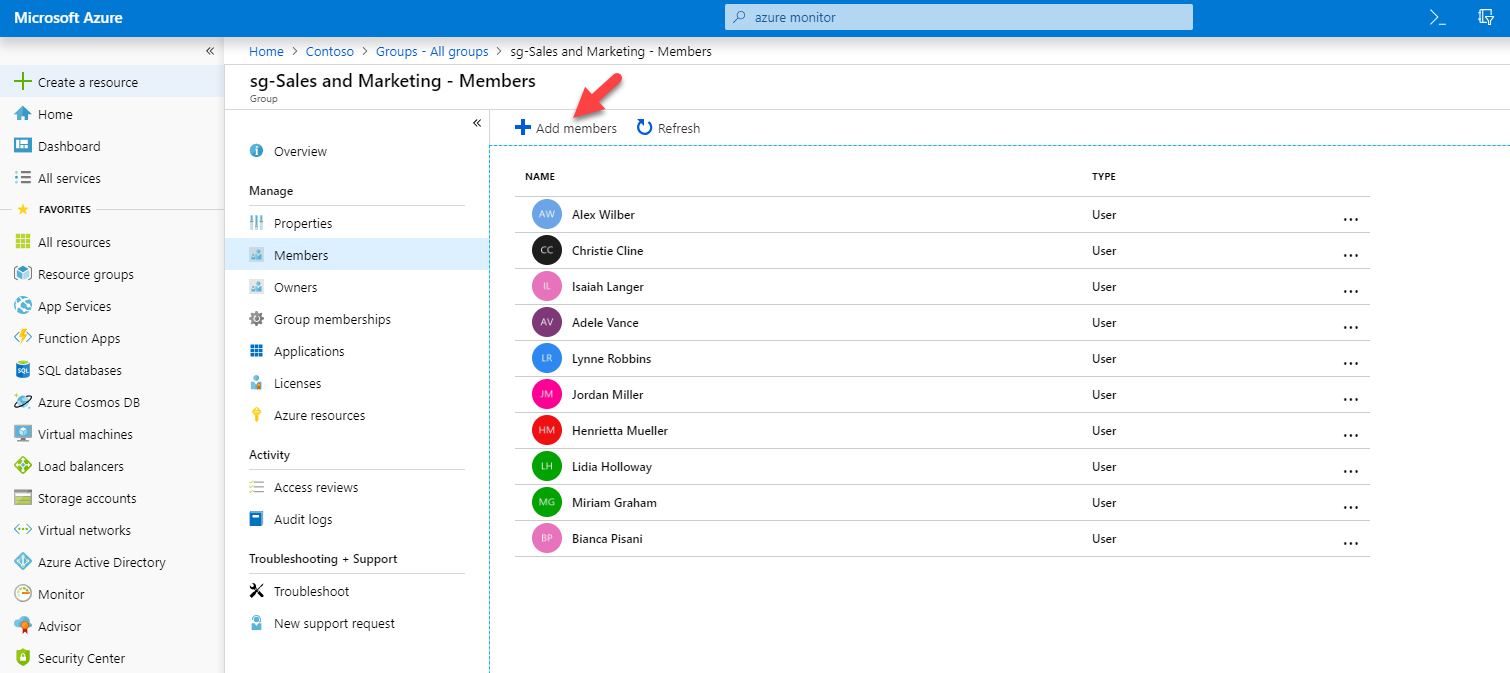
6) Now I need to send an inivitation. In my demo I am going to invite external user to sg- Sales and Marketing group. To do that, I went to Azure Active Directory | Groups | sg- Sales and Marketing | Members and click on Add Members
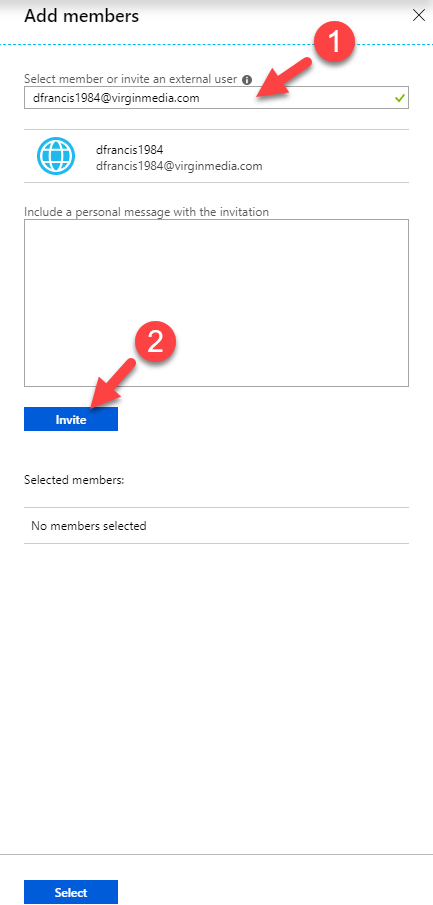
7) Then type the external user email address and click on Invite
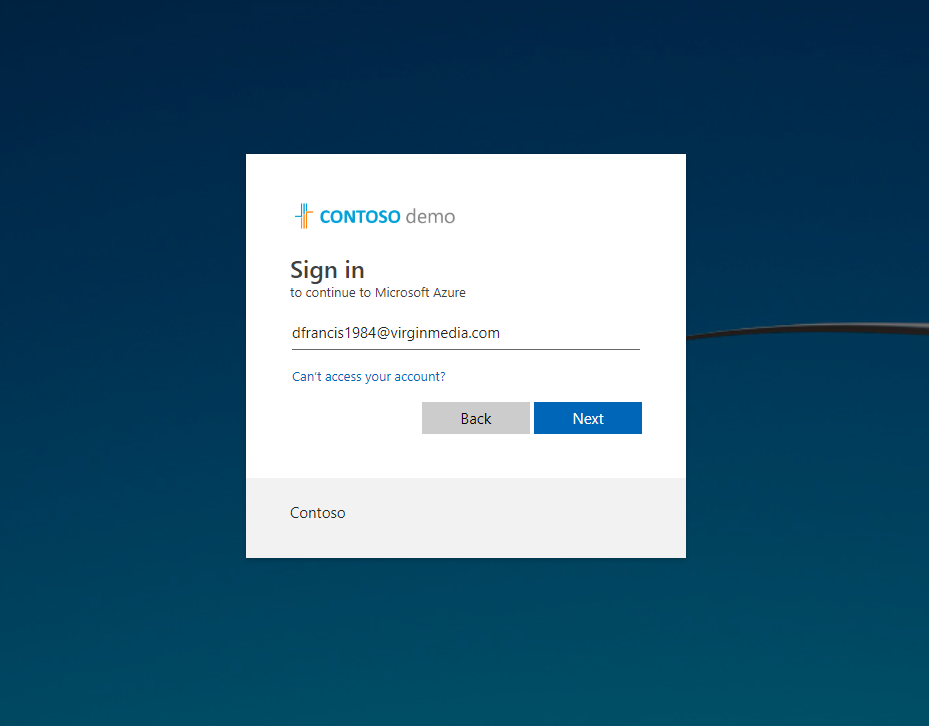
8) As expected, external user recived the email inivitation but we have to use https://portal.azure.com/<tenant id> for sign up.
9) In sign up page, type the external user’s email id.
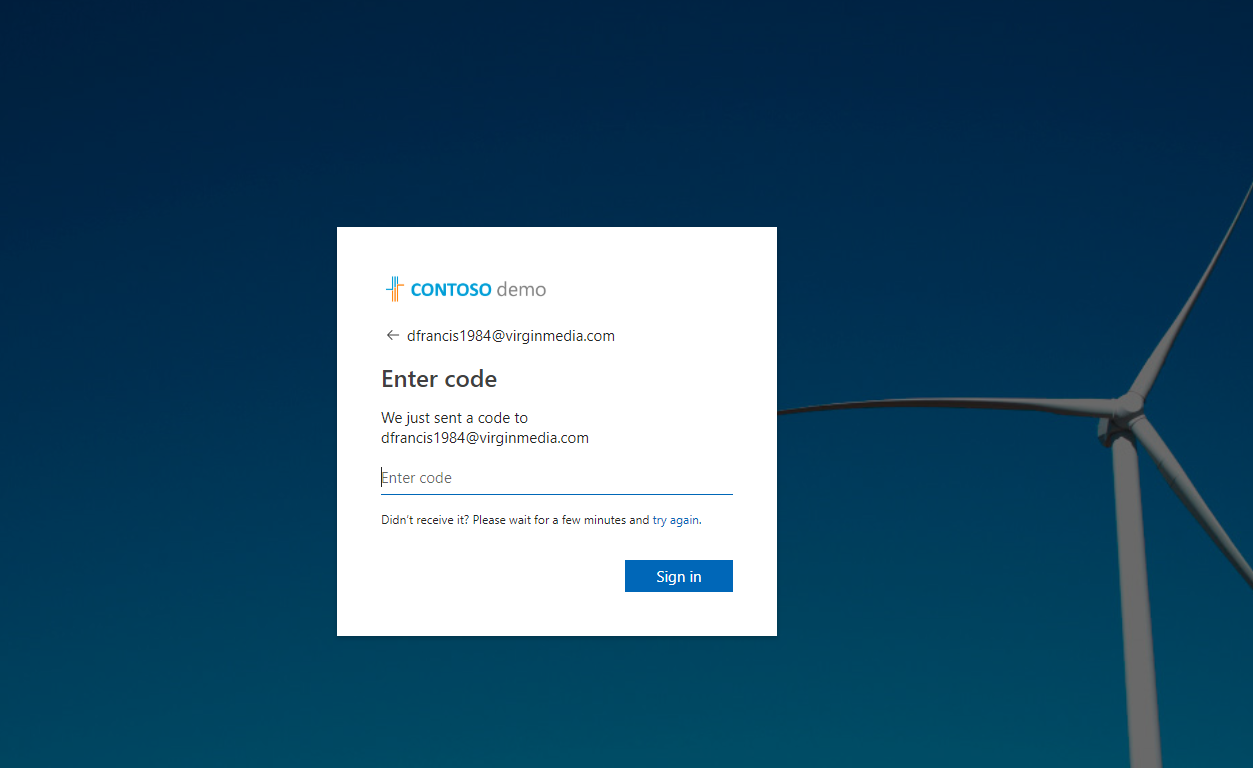
10) In next page, as expected it sent one time code.
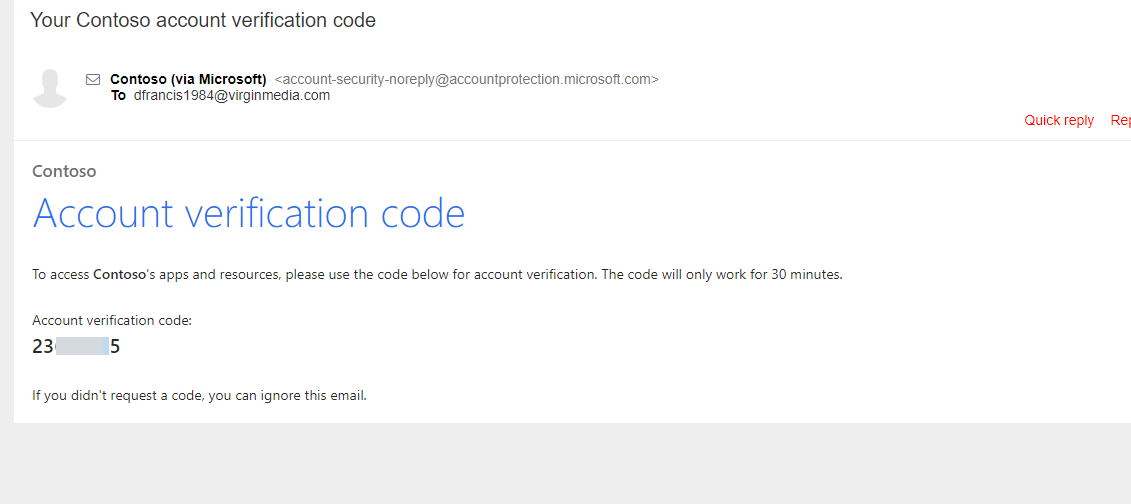
11) When I check the email, I can email with OTP.
12) I go ahead and used the code. As expected, it allowed me to login with out any additional work.
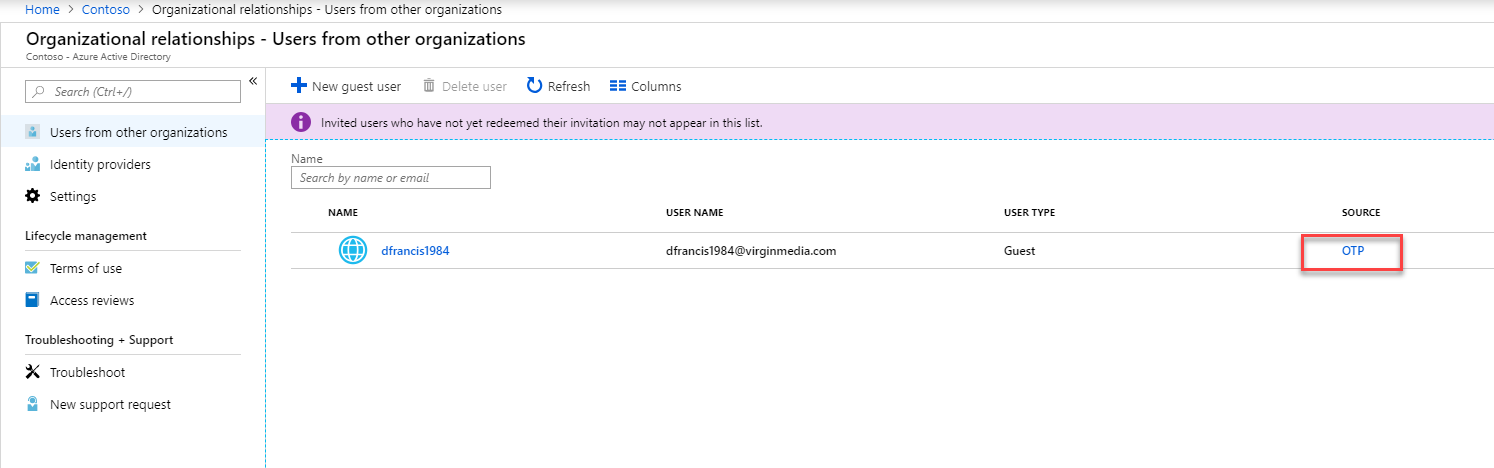
13) If we go to Azure Active Directory | Organizational relationships | Users from other organizations we can see the new user and it shows the source as OTP
Cool isn’t it? This marks the end of this blog post. If you have any questions feel free to contact me on rebeladm@live.com also follow me on twitter @rebeladm to get updates about new blog posts.



Is it also possible to set a redirect_url so after accepting the user gets redirect to a sharepoint page?