If you have worked with Microsoft Active Directory before, you may be familiar with ‘Organizational Units‘. These units allow you to logically group users, groups, or computers into a single administrative scope. By using Organizational Units, you can delegate administrative tasks and permit specific users to manage the resources within that unit.
What about the cloud? Even in the cloud, we may have similar administrative requirements. Let’s look at the following example.
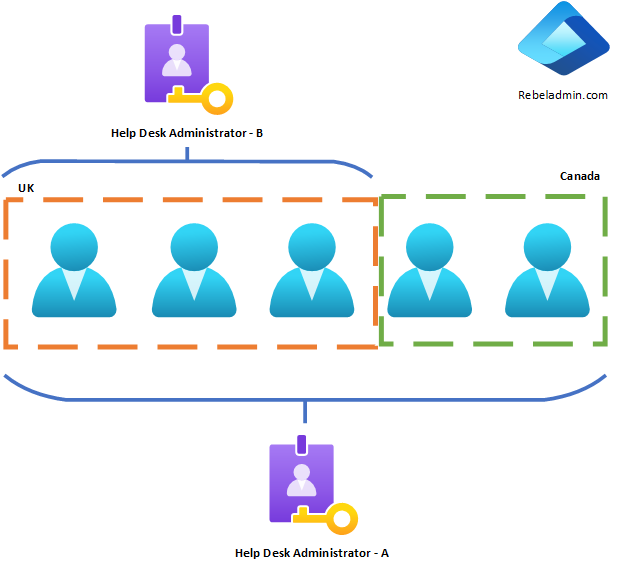
In the rebeladmin.com Entra ID tenant, users are divided into two geographical areas: the UK and Canada. Despite being a single tenant, these two regions have separate IT teams. If we assign the help desk administrator role to an IT administrator in the UK team, it won’t prevent them from resetting the password of a user in Canada. This compromises the organization’s principle of least privilege. We can address this issue using Entra ID Administrative Units. By using administrative units, we can restrict role permissions to a specific subset of users, groups, or devices.
Administrative Roles
By default, the following built-in administrative roles can be assigned to an administrative unit.
| Role | Description |
| Authentication Administrator | Can access to view, set and reset authentication method information for any non-admin user. |
| Cloud Device Administrator | Limited access to manage devices in Microsoft Entra ID. |
| Groups Administrator | Members of this role can create/manage groups, create/manage groups settings like naming and expiration policies, and view groups activity and audit reports. |
| Helpdesk Administrator | Can reset passwords for non-administrators and Helpdesk Administrators. |
| License Administrator | Can manage product licenses on users and groups. |
| Password Administrator | Can reset passwords for non-administrators and Password Administrators. |
| Printer Administrator | Can manage all aspects of printers and printer connectors. |
| Privileged Authentication Administrator | Can access to view, set and reset authentication method information for any user (admin or non-admin). |
| SharePoint Administrator | Can manage all aspects of the SharePoint service. |
| Teams Administrator | Can manage the Microsoft Teams service. |
| Teams Devices Administrator | Can perform management related tasks on Teams certified devices. |
| User Administrator | Can manage all aspects of users and groups, including resetting passwords for limited admins. |
Apart from above any custom role also can be assigned to an administrative unit as long as it has permission relevant to users, groups or devices.
Important facts about Entra ID Administrative Units
- Groups can be added to Entra ID administrative units, but this does not mean that the members of the group are also in scope. With the relevant permissions in place, an administrator can manage the name and membership of the group, but not the properties of the group members.
- Dynamic queries can be used to add users or devices to administrative units, but not groups.
- If the membership type is dynamic user or dynamic device, users or devices cannot be added to the scope manually.
- Administrators can use Microsoft Graph/PowerShell, Microsoft Entra admin center, and Microsoft 365 admin center to manage users, groups, and devices in their administrative units. However, only certain tasks are permitted via the Microsoft 365 admin center. More information can be found on https://learn.microsoft.com/en-us/entra/identity/role-based-access-control/administrative-units#administrative-unit-management.
- At least the Privileged Role Administrator role is required to create and manage Entra ID administrative units.
- The role permissions assigned within an administrative unit are only applicable to the scope of that unit. Any permissions applied to the same administrators outside the scope remain unchanged.
- Service principals and guest users can be added to the Entra ID administrative unit scope, but they will not be able to use the assigned role unless they have directory read permissions. By default, service principals and guest users do not have directory read permissions.
Privileged Identity Management (PIM) for Groups and Administrative Units
Privileged Identity Management (PIM) for groups is a super important feature in Microsoft Entra ID Governance. It helps organizations manage just-in-time membership and ownership of groups.
When users are added as eligible members of Privileged Access Groups (PAGs), it removes standing privilege, which boosts security by making sure elevated access is only granted when needed. This method allows for multiple roles to be assigned with a single PIM activation, making the process smoother and less complicated. However, it’s crucial that PGs are assigned to the Administrative Unit role to keep the system’s integrity intact and ensure that only authorized changes are made by eligible members.

In this demo, I’ll be using Privileged Access Groups with Administrative Units to eliminate standing permissions. To create PAGs please follow my blog post https://www.rebeladmin.com/manage-privileged-access-groups-with-azure-ad-privileged-identity-management-azure-ad-pim/
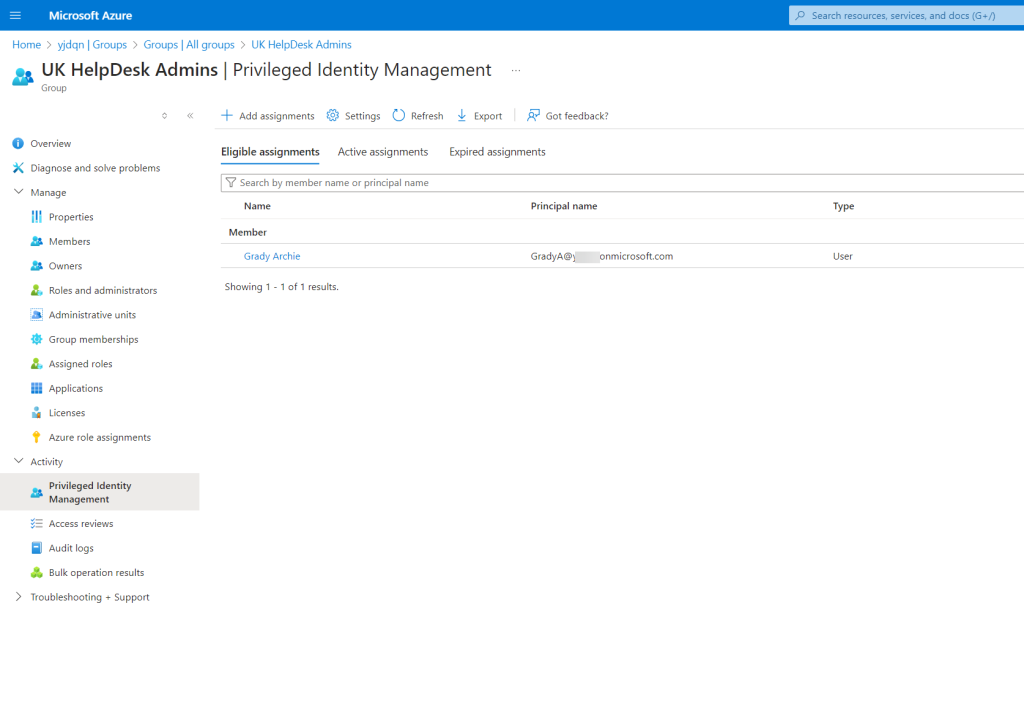
Let’s dive into how we can use administrative units. In this demo, I’ll replicate the setup explained earlier in the article and restrict UK user management to the UK help desk administrator. I already have a Privileged Access Group called ‘UK HelpDesk Admins,’ and the group’s membership will be managed using PIM.
Before we start, ensure that you have at least a Microsoft Entra ID P1 license available for the administrators who will be assigned to the Entra ID Administrative Unit. For more information about the required licenses, please visit the official documentation https://learn.microsoft.com/en-us/entra/identity/role-based-access-control/administrative-units#license-requirements
Create Administrative Unit
- Sign in to the Entra portal as a Privileged Role Administrator or higher.
- Navigate to Identity > Roles and admins > Admin units.
- Click on “+ Add” to open the wizard for creating Entra ID administrative unit.
- Provide a name and description for the Administrative Unit, then click “Next: Assign roles >“.
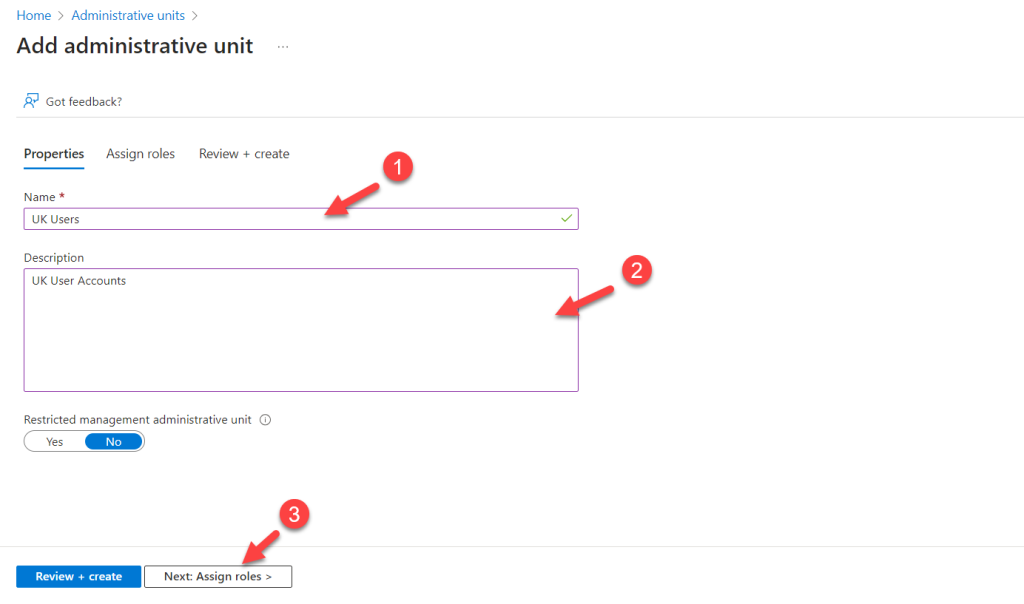
- On the next page, do not select Helpdesk Administrator as the role. I will add the Privileged Access Group to the role later. Click “Next: Review + create >” to continue.
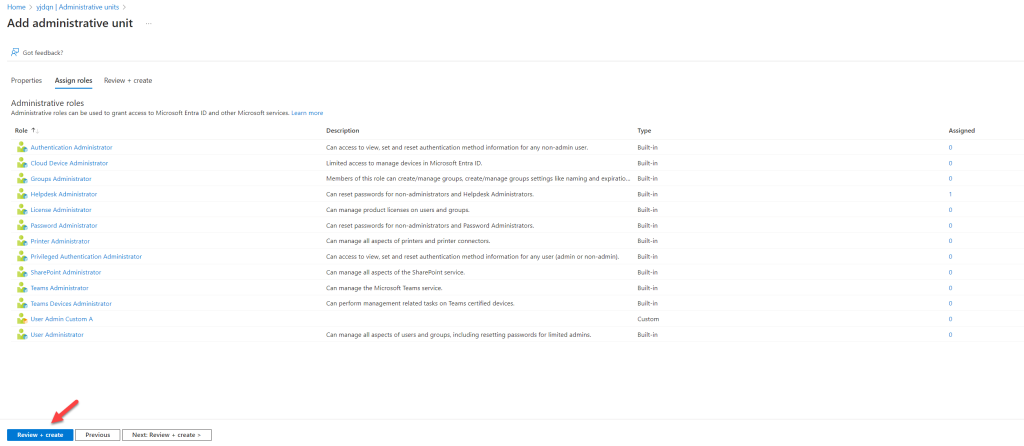
- Review the settings on the next page and click “Create” to complete the administrative unit creation process.
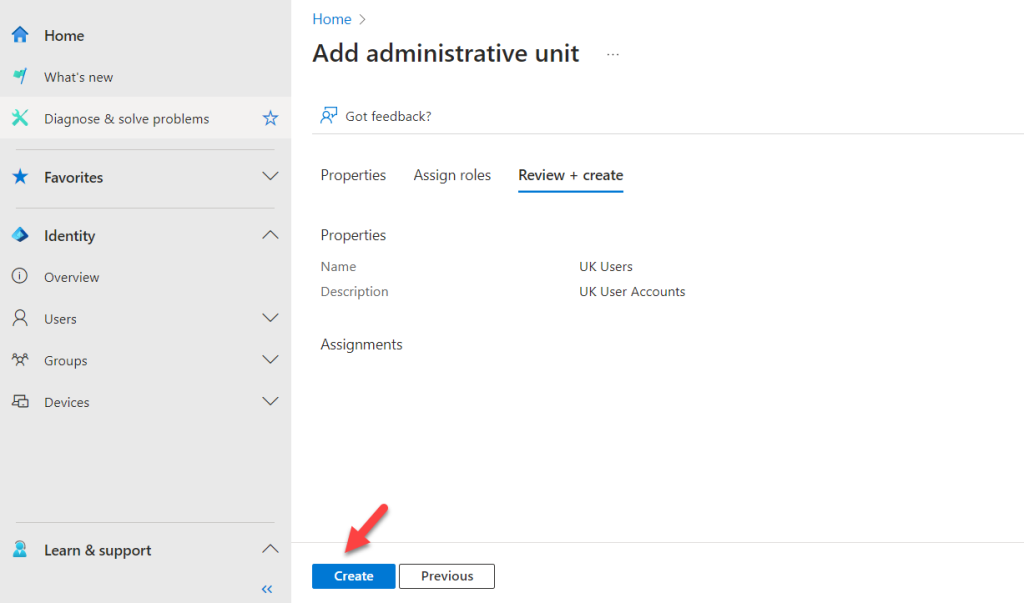
This completes the administrative unit creation process. In the next steps, let’s add users to the scope.
Add users to the Entra ID administrative unit scope
To add users to the scope:
- Sign in to the Entra portal as a Privileged Role Administrator or higher.
- Navigate to Identity > Roles and admins > Admin units.
- From the list, click on the relevant Administrative Unit.
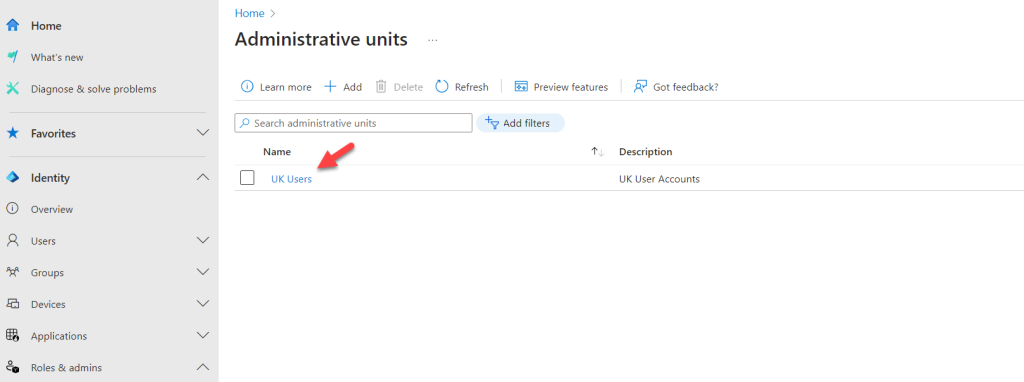
- Click on Properties.
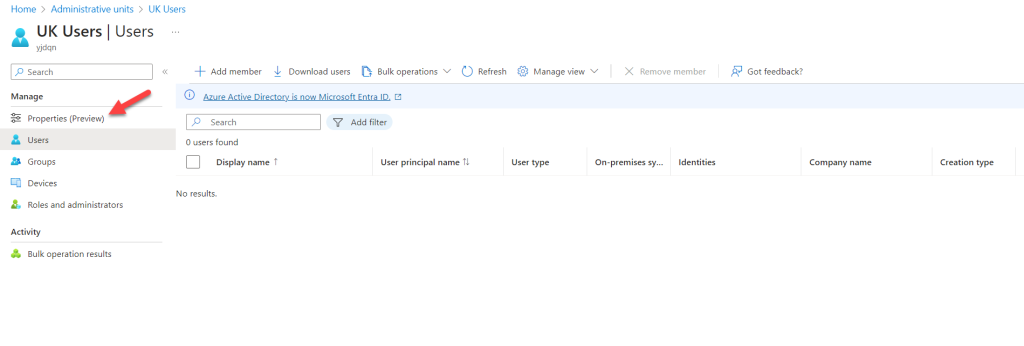
- In this group, I will use dynamic membership for the users. To do this, click on the drop-down under Membership type and select Dynamic User.
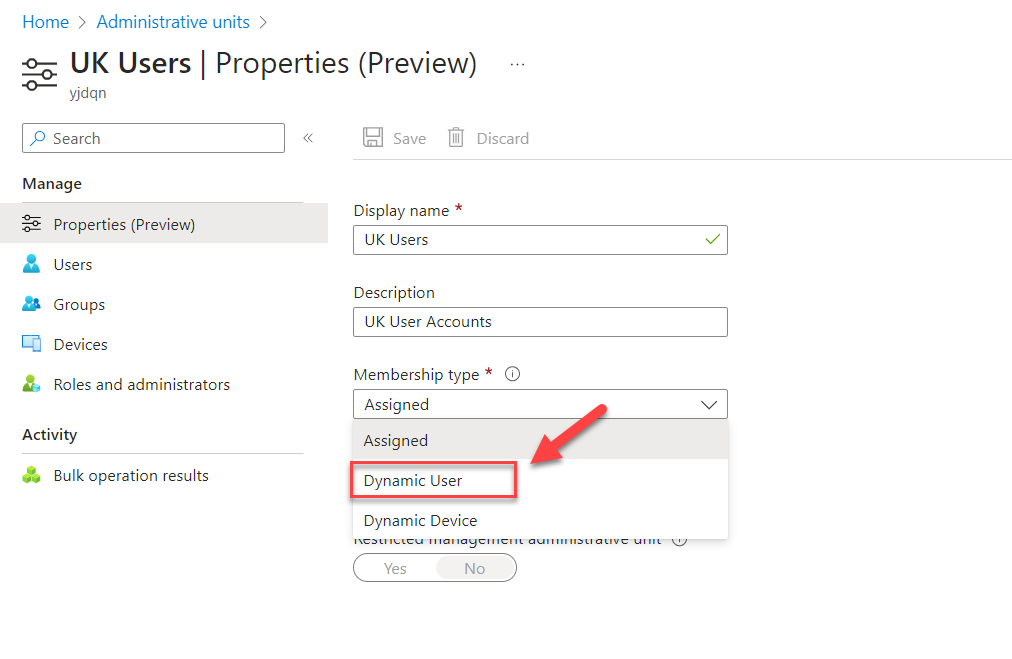
- Click on Add dynamic query to define the condition.
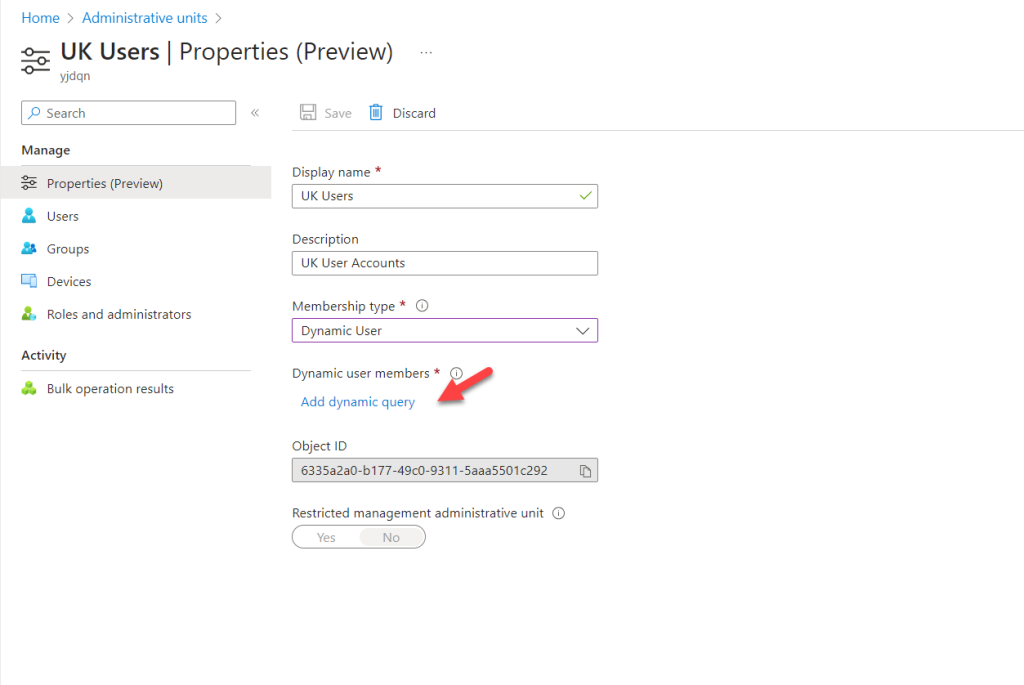
- Here, I am using the country as the field. Any user who has the UK as their country will be a member of this Administrative Unit. Once the rule is in place, click on Save.
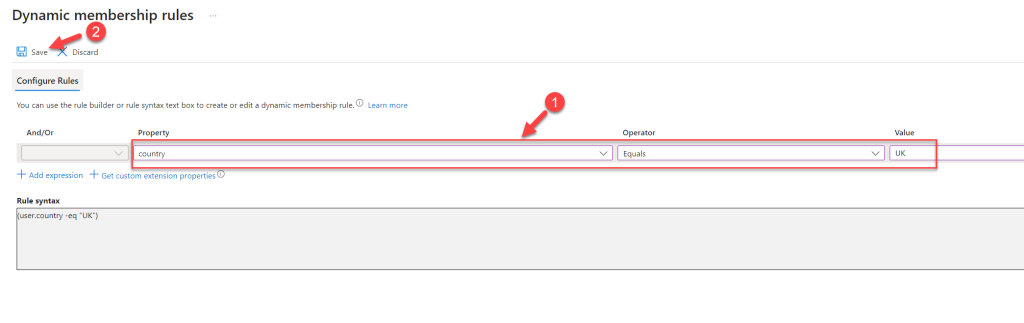
- In the main window, also click on Save to apply the new configuration.
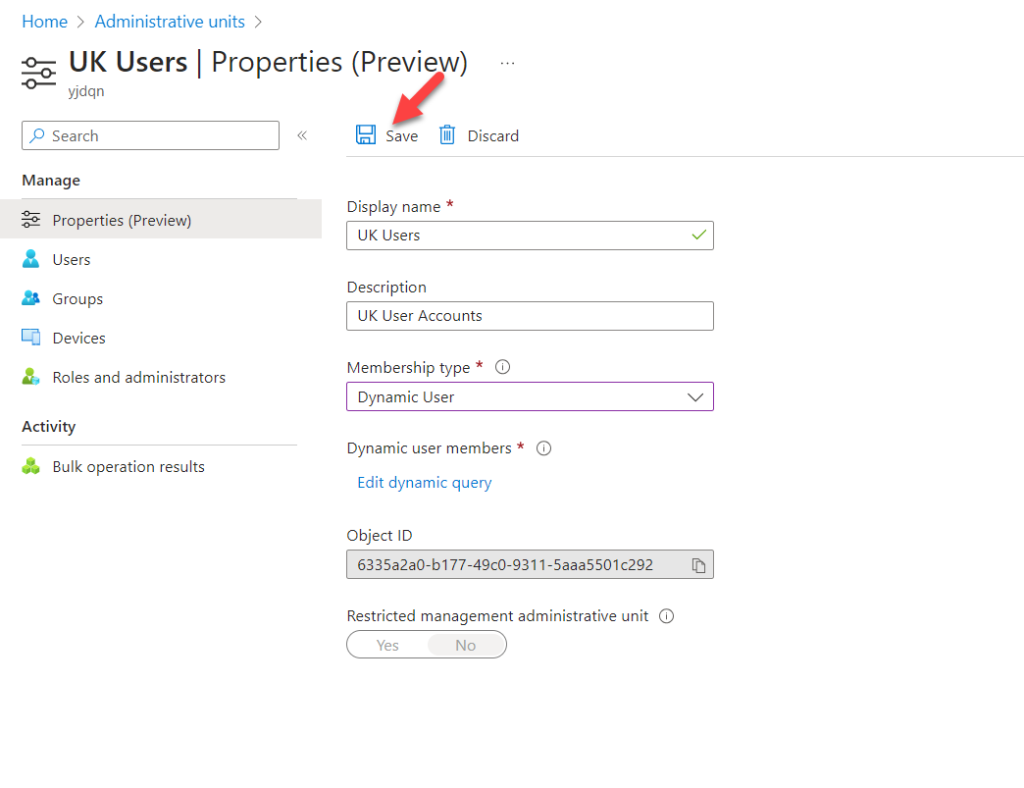
This completes the user assignment process. The next step is to assign a role to the Administrative Unit.
Assign Role to Entra ID Administrative Unit
To assign helpdesk administrator role,
- Sign in to the Entra portal as a Privileged Role Administrator or higher.
- Navigate to Identity > Roles and admins > Admin units.
- From the list, click on the relevant Administrative Unit.
- Click on Roles and administrators.
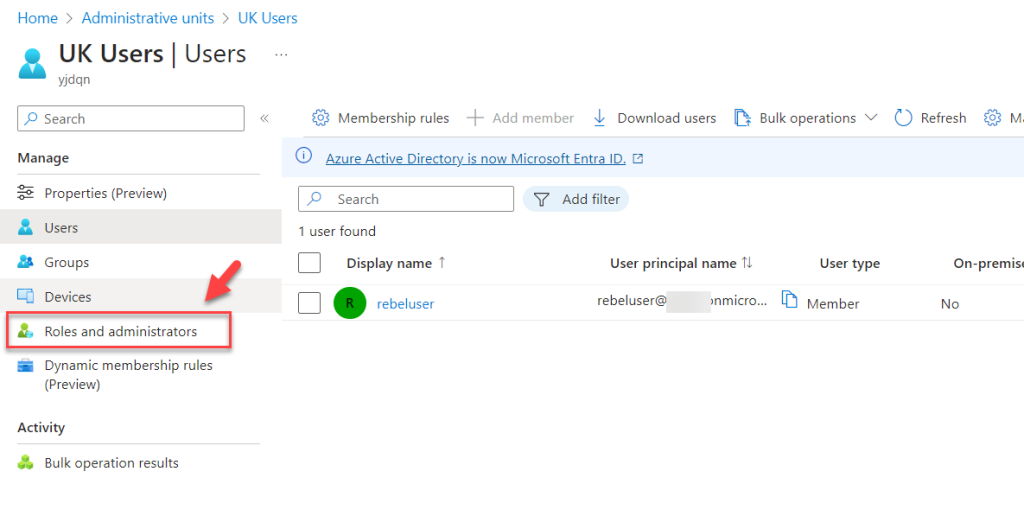
- From the list, select Helpdesk Administrator.
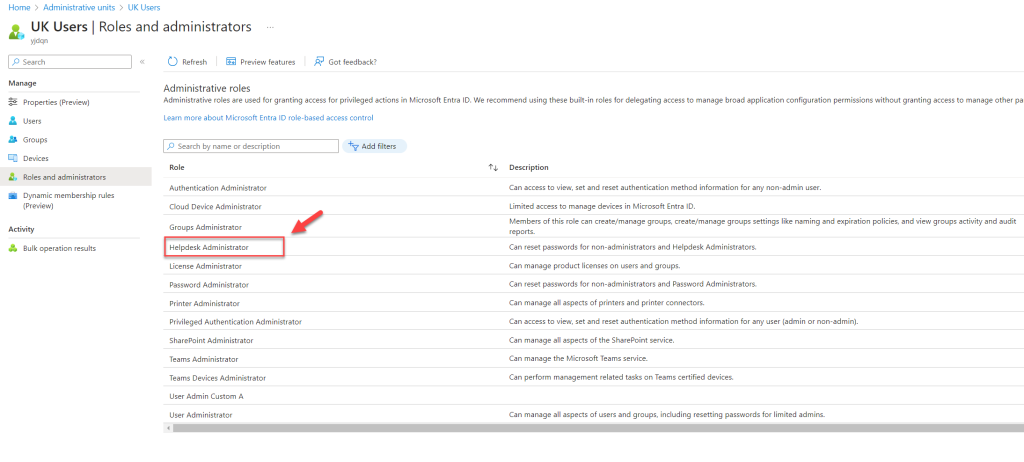
- Here, I will add the Privileged Access Group I created earlier as active assignments. To do this, click on + Add assignment.
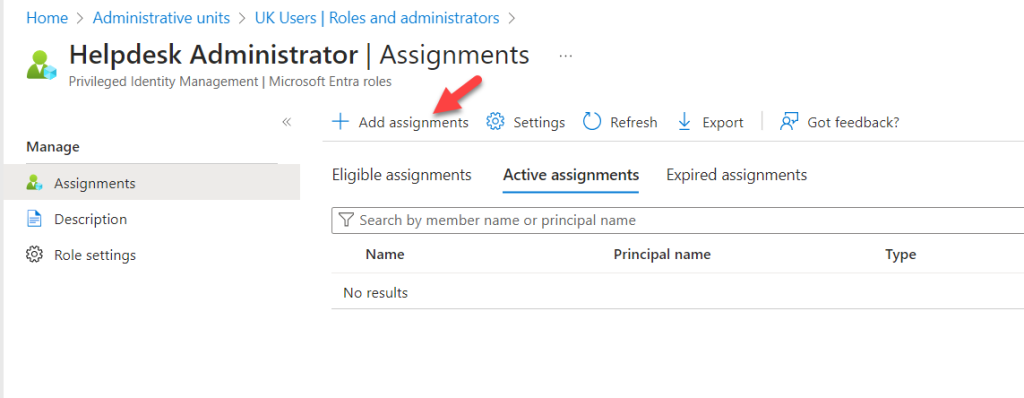
- From the list of members, select the relevant group and click Next.
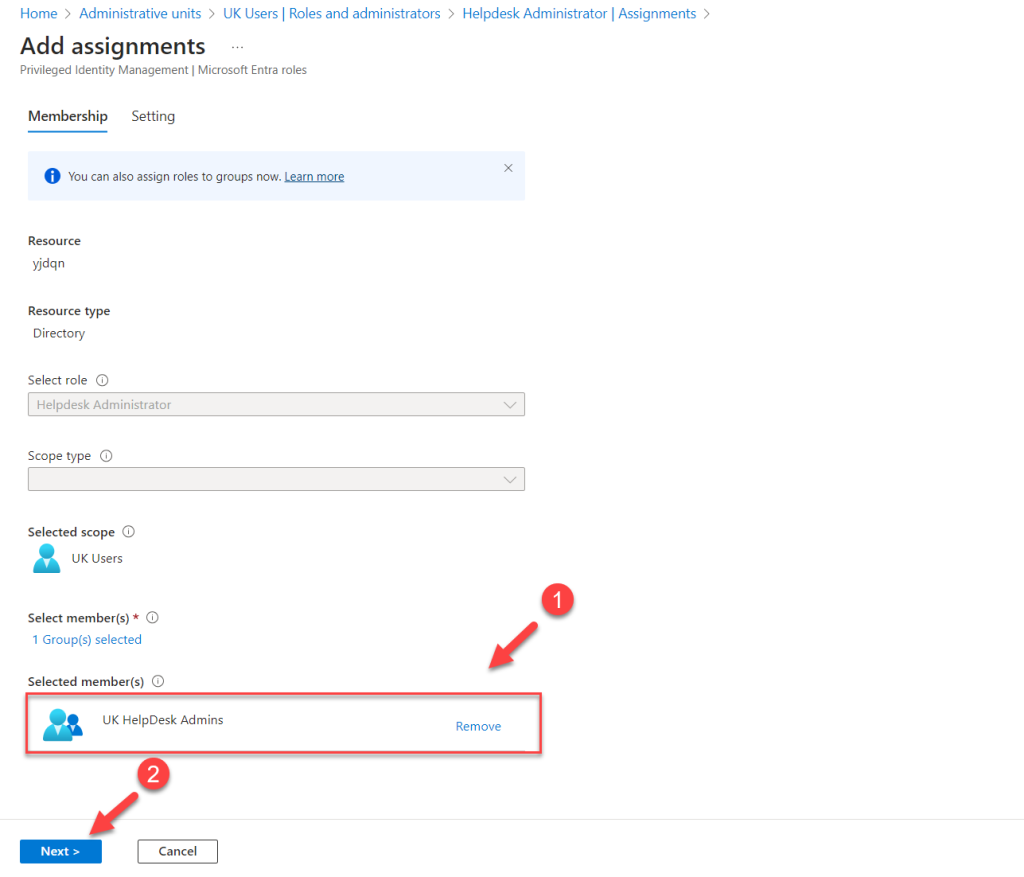
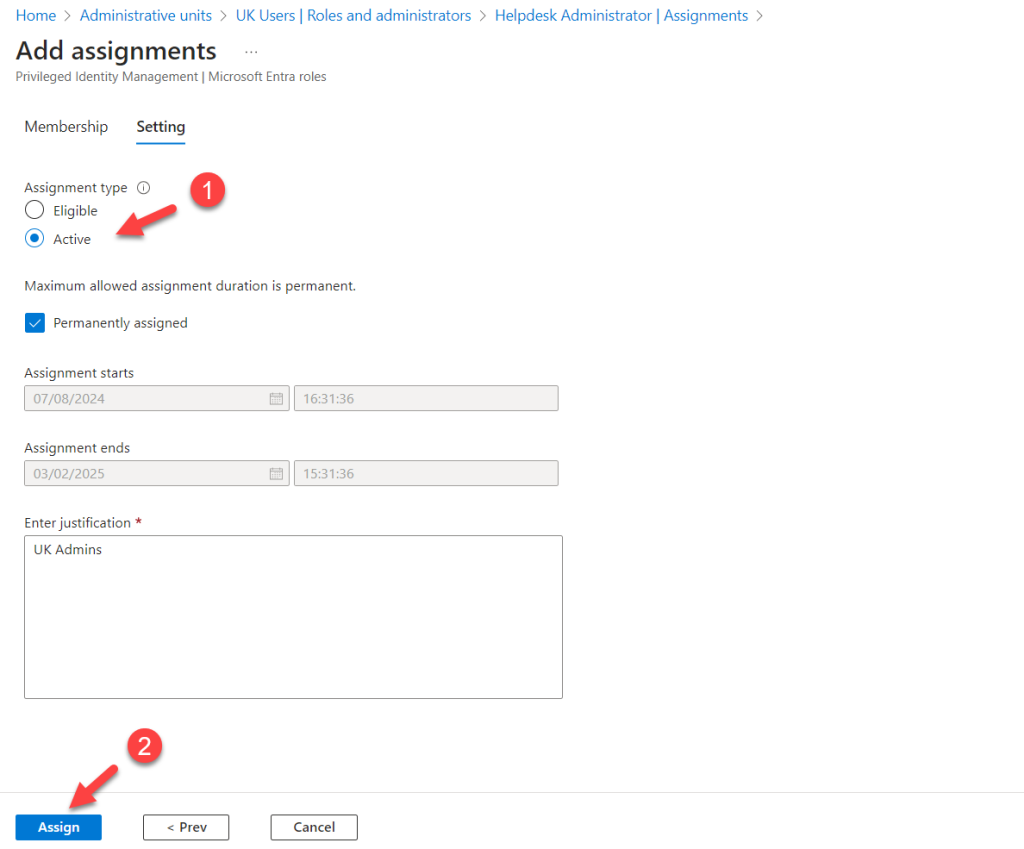
- In the next window, select the assignment type as Active. To complete the assignment process, click Assign.
- Once the role is assigned, you will see that the scope of the role is set to the Administrative Unit.
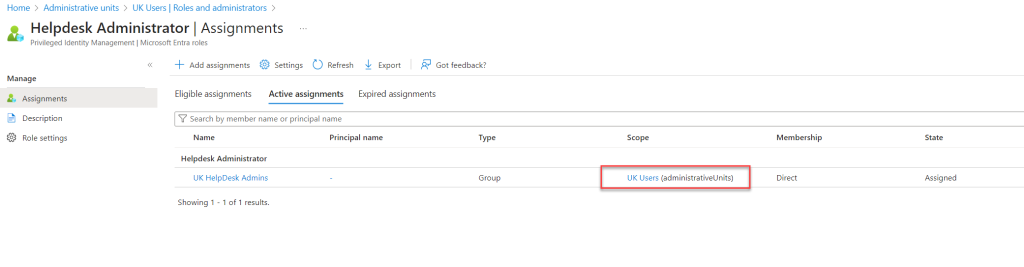
This completes the role assignment process.
Testing
It’s time to test the configuration.
To do this, I’ll log in as a user who is an eligible member for the Help Desk Administrator role assigned to the UK Users administrative unit. Once logged in, I’ll select a user within the Entra ID Administrative Unit scope.
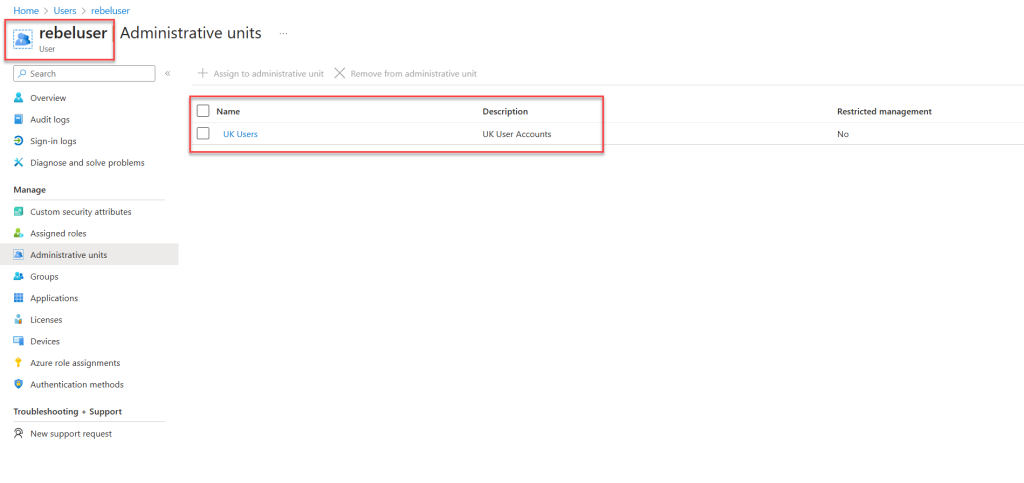
When I attempt to reset the password for this user, I receive an error. This is expected since the user doesn’t have the Help Desk Administrator permission yet.
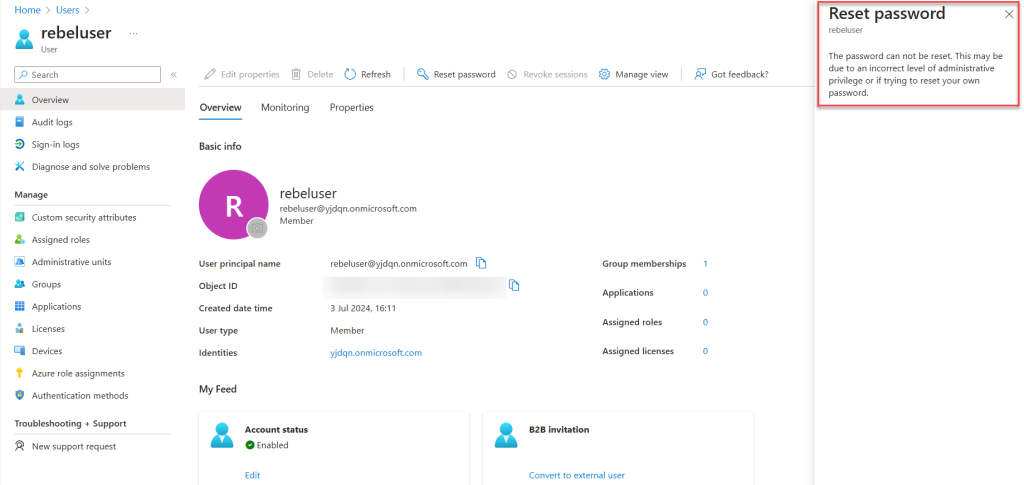
Next, I’ll activate membership for the UK HelpDesk Admins privileged access group using PIM. This will grant the Help Desk Administrator permission to the user.
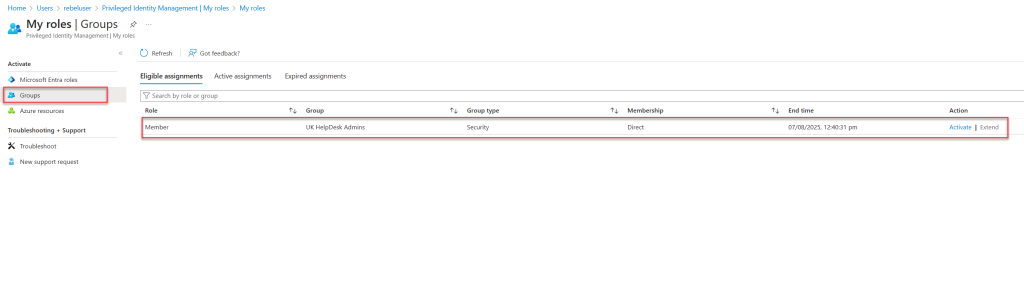
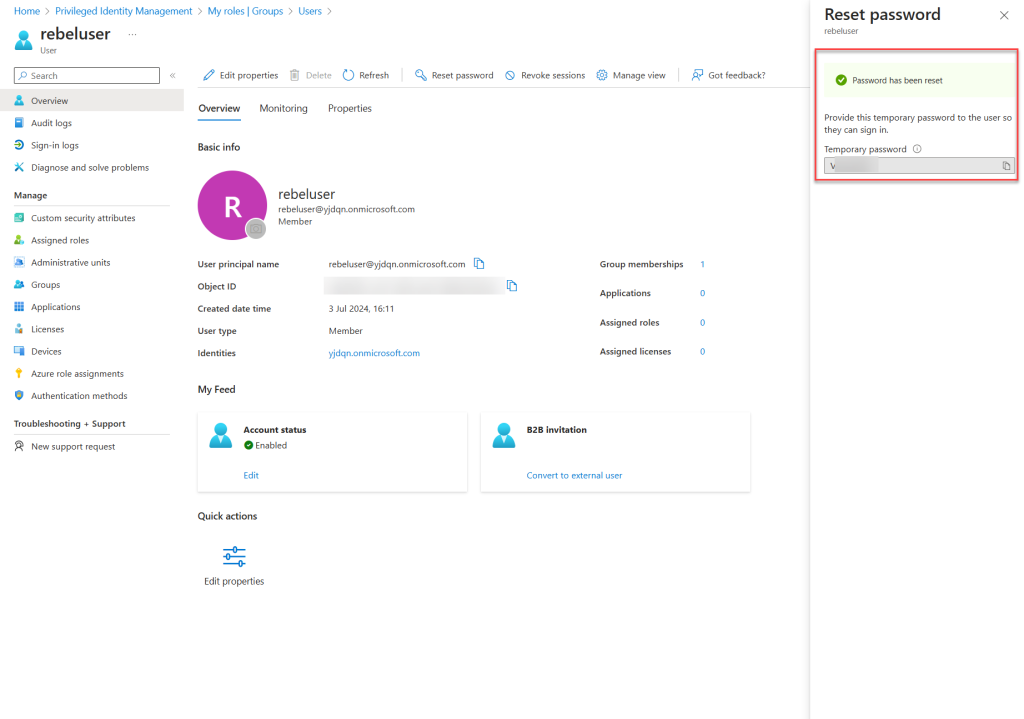
After the membership is granted, I’ll try to reset the password for the same test user again. As expected, I can reset the password without any issues.
For the next test, I’ll attempt to reset the password for a user outside the Entra ID Administrative Unit scope. As expected, even though I have the Help Desk Administrator role, I cannot reset the password for a user outside the Administrative Unit scope.
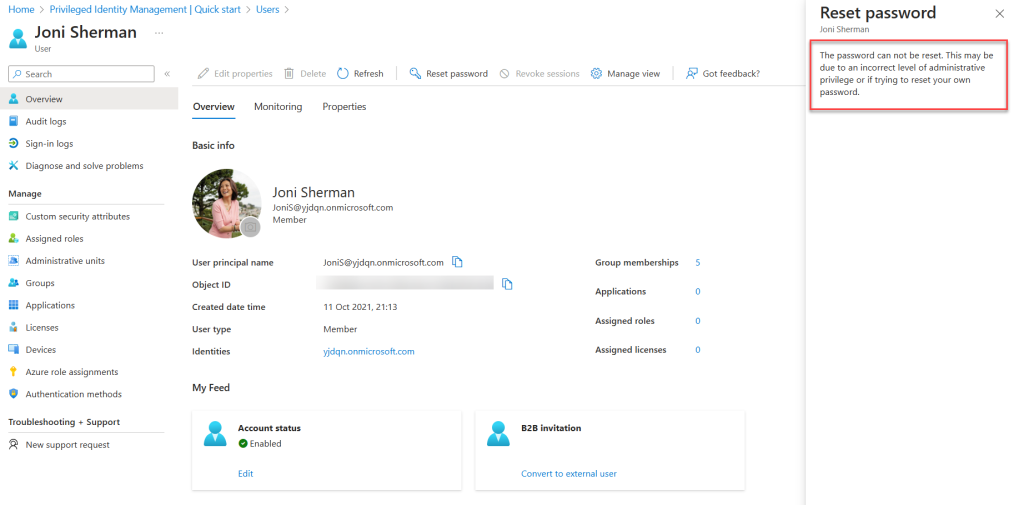
I hope this gives you a better understanding of how Entra ID Administrative Units work. In the example above, a user with the Help Desk Administrator role assigned outside the Administrative Unit can still reset the password for a user within the Administrative Unit scope. We can restrict this using Restricted Administrative Units, which I’ll cover in the next blog post. If you have any questions, feel free to contact me at rebeladm@live.com.


