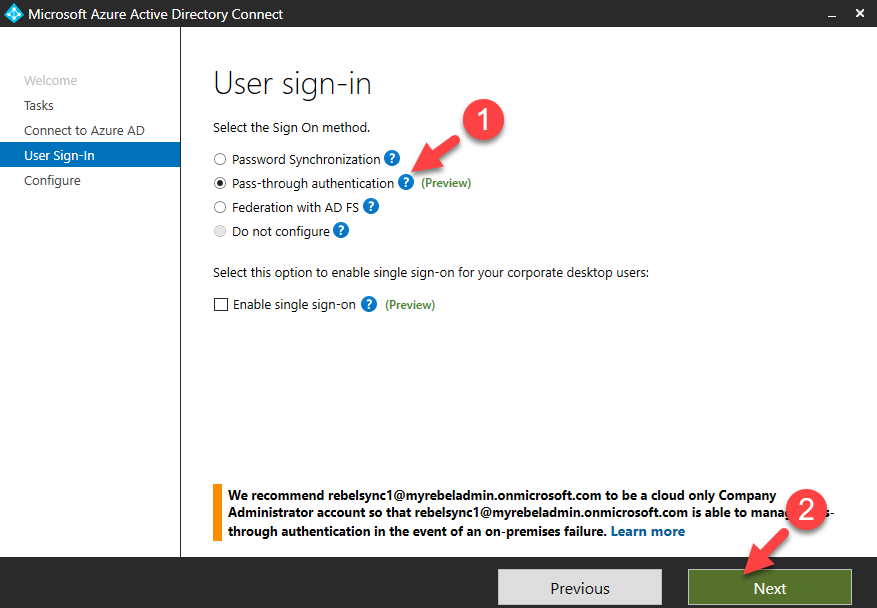
When organizations want to use same user name and passwords to log in to on-premises and cloud workloads (azure), there are two options. One is to sync user name and password hashes from on-premises active directory to azure AD. Other option is to deploy ADFS farm on-premises and use it to authenticate cloud based logins. But it needs additional planning and resources. On-premises AD uses hash values (which are generated by a hash algorithm) as passwords. They are NOT saved as clear text, and it is almost impossible to revert it to the original password even someone have hash value. There is misunderstanding about this as some people still think Azure AD password sync uses clear text passwords. Every two minutes, the Azure AD connect server retrieves password hashes from the on-premises AD and syncs it with Azure AD on a per user-basis in chronological order. In technical point of view, I do not see a reason why people should avoid password hash sync to azure AD. However, there are company policies and compliance requirements which do not accept any form of identity sync to external system even on hash format. Azure Active Directory Pass-through Authentication is introduced by Microsoft to answer these requirements. It allows users to authenticate in to cloud workloads using same passwords they are using in on-premises without syncing their password hash values to Azure AD. This feature is currently on preview. Which means it’s still not supported on production environment. But it is not too early to try it in development environments.
According to Microsoft, following can list as key features of Pass-through Authentication.
• Users use the same passwords to sign into both on-premises and cloud-based applications.
• Users spend less time talking to the IT helpdesk resolving password-related issues.
• Users can complete self-service password management tasks in the cloud.
• No need for complex on-premises deployments or network configuration.
• Needs just a lightweight agent to be installed on-premises.
• No management overhead. The agent automatically receives improvements and bug fixes.
• On-premises passwords are never stored in the cloud in any form.
• The agent only makes outbound connections from within your network. Therefore, there is no requirement to install the agent in a perimeter network, also known as a DMZ.
• Protects your user accounts by working seamlessly with Azure AD Conditional Access policies, including Multi-Factor Authentication (MFA), and by filtering out brute force password attacks.
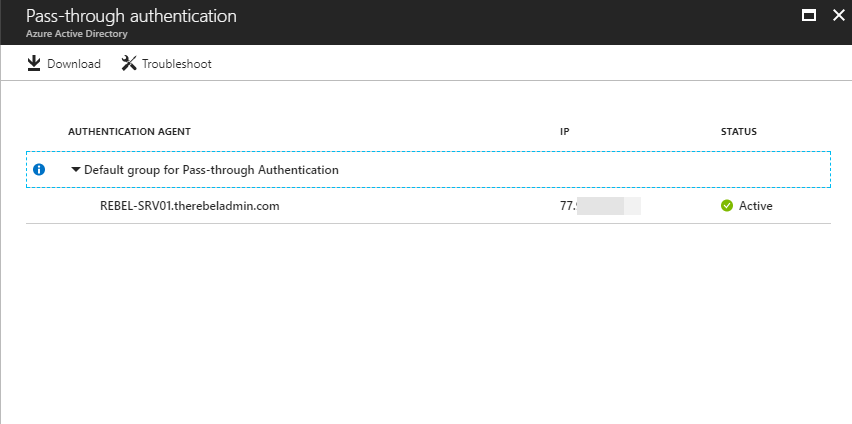
• Additional agents can be installed on multiple on-premises servers to provide high availability of sign-in requests.
• Multi-forest environments are supported if there are forest trusts between your AD forests and if name suffix routing is correctly configured.
• It is a free feature, and you don't need any paid editions of Azure AD to use it.
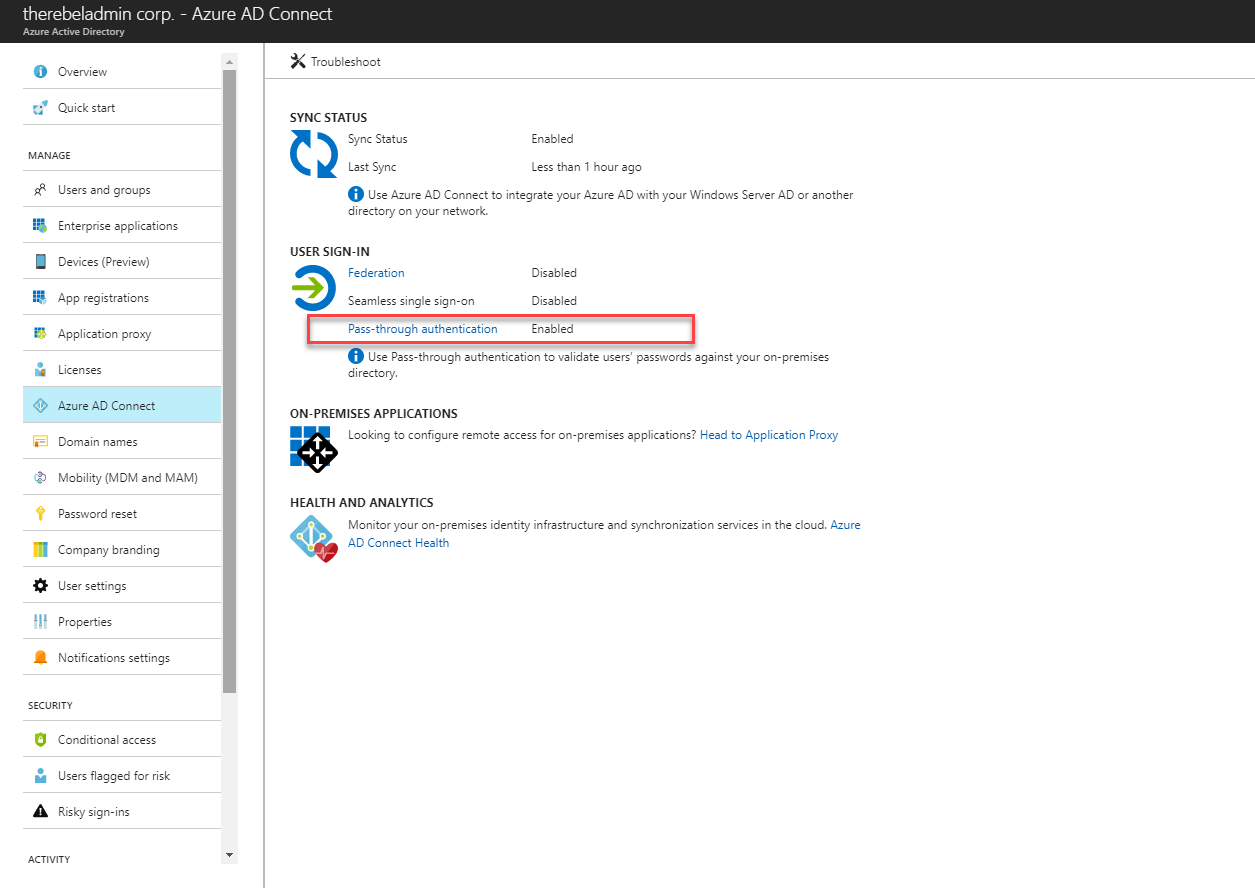
• It can be enabled via Azure AD Connect.
• It protects your on-premises accounts against brute force password attacks in the cloud.
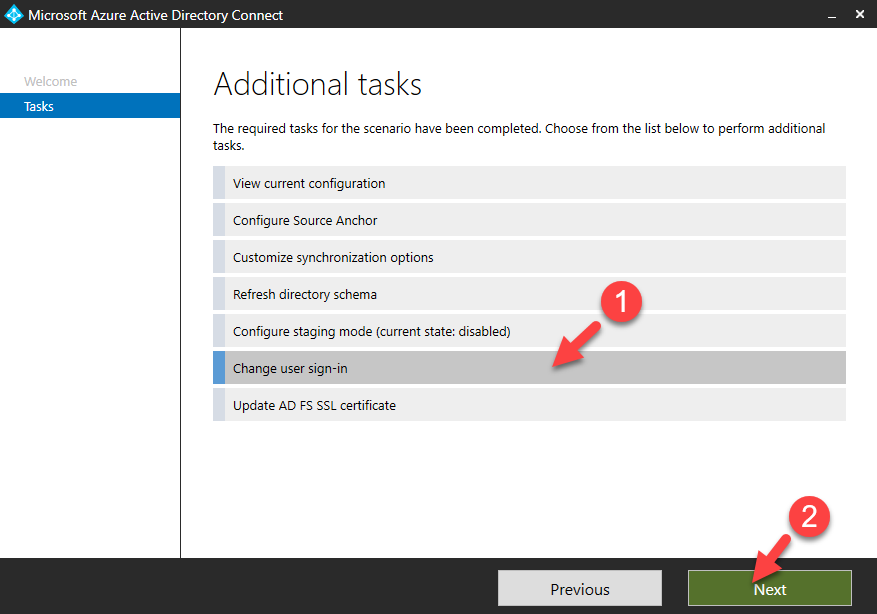
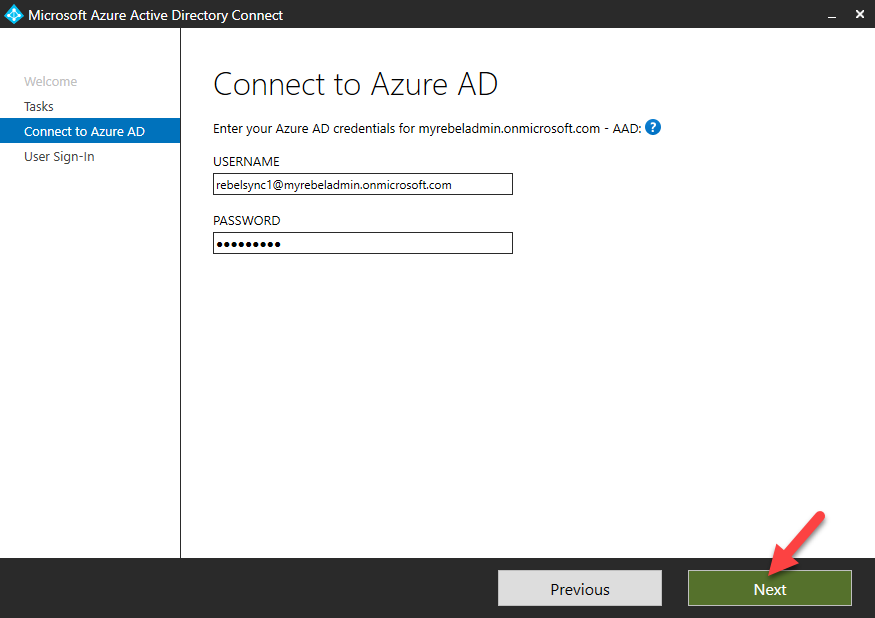
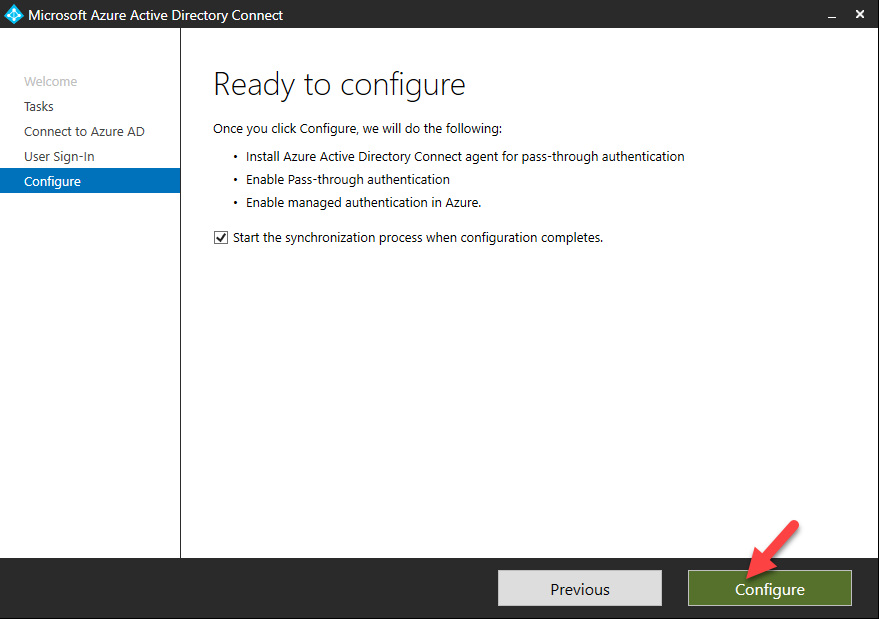
How it works?
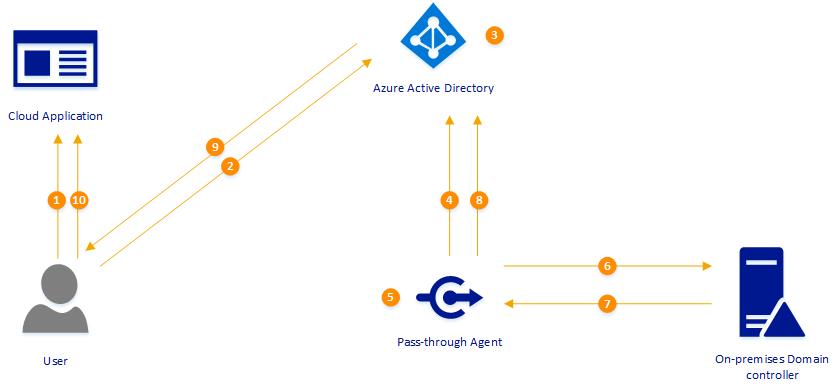
Let’s see how it really works. In following example, user is trying to access cloud based application (integrated with azure) using his on-premises username and the password. This organization is using pass-through authentication.
1. User is accessing the application URL using his browser.
2. In order to authenticate to the application, user is directed to Azure Active Directory sign-in page. User then type the user name, password and click on sign-in button.
3. Azure AD receives the data and it encrypt the password using public key which is used to verify the data authenticity. Then it places it’s in a queue where it will wait till pass-through agent retrieves it.
4. On-premises pass-through agent retrieves the data from Azure AD queue (using an outbound connection)
5. Agent decrypt the password using private key available for it.
6. Agent validates the user name and password information with on-premises Active Directory. It uses same mechanism as ADFS.
7. On-premises AD evaluate the request and provides the response. It can be success, failure, password-expire or account lockout.
8. Pass-through agent passes the response back to Azure AD.
9. Azure AD evaluate response and pass it back to user.
10. If response was success, user is allowed to access the application.



Nice Article
Thank you for sharing this information.
Thank you for sharing this information.
I didn’t have any expectations concerning that title, but the more I was astonished. The author did a great job. I spent a few minutes reading and checking the facts. Everything is very clear and understandable. I like posts that fill in your knowledge gaps. This one is of the sort.
Nice article, thanks for sharing informative post.
Thanks for the article.
Thanks