Azure AD has near 35 different Directory roles. Each of these roles have different level of privileges. Using Azure PIM access reviews, we can review access and activities of member’s in these privilege groups and adjust their memberships accordingly. let’s see why it is important to review access of privilege accounts periodically.
• Too much administrators – How many of you aware of all the administrators (including local admins) of your local AD infrastructure? I got you isn’t it! in local AD environment it is handful of privilege user groups, but Azure AD have near 35 roles. So, yes it will be difficult to keep track of the administrator with out proper review.
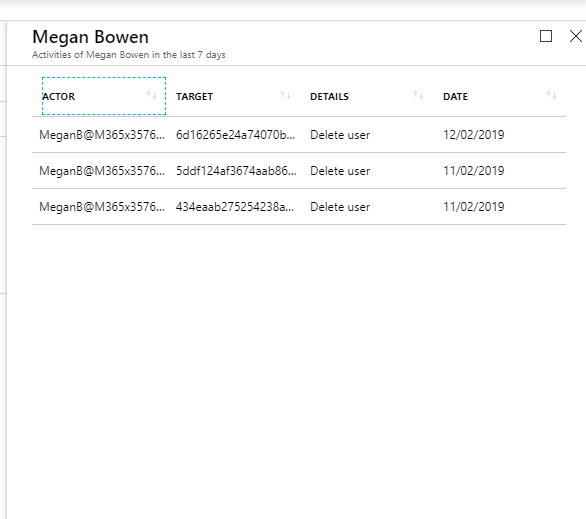
• Not doing what they supposed to do – Azure AD roles have predefined level of privileges. you may assign a higher privilege role to member as he/she can’t match privilege available under existing roles. How we know they are only doing what they supposed to do? using access reviews we can track down their activities and make sure they not misuse the privileges.
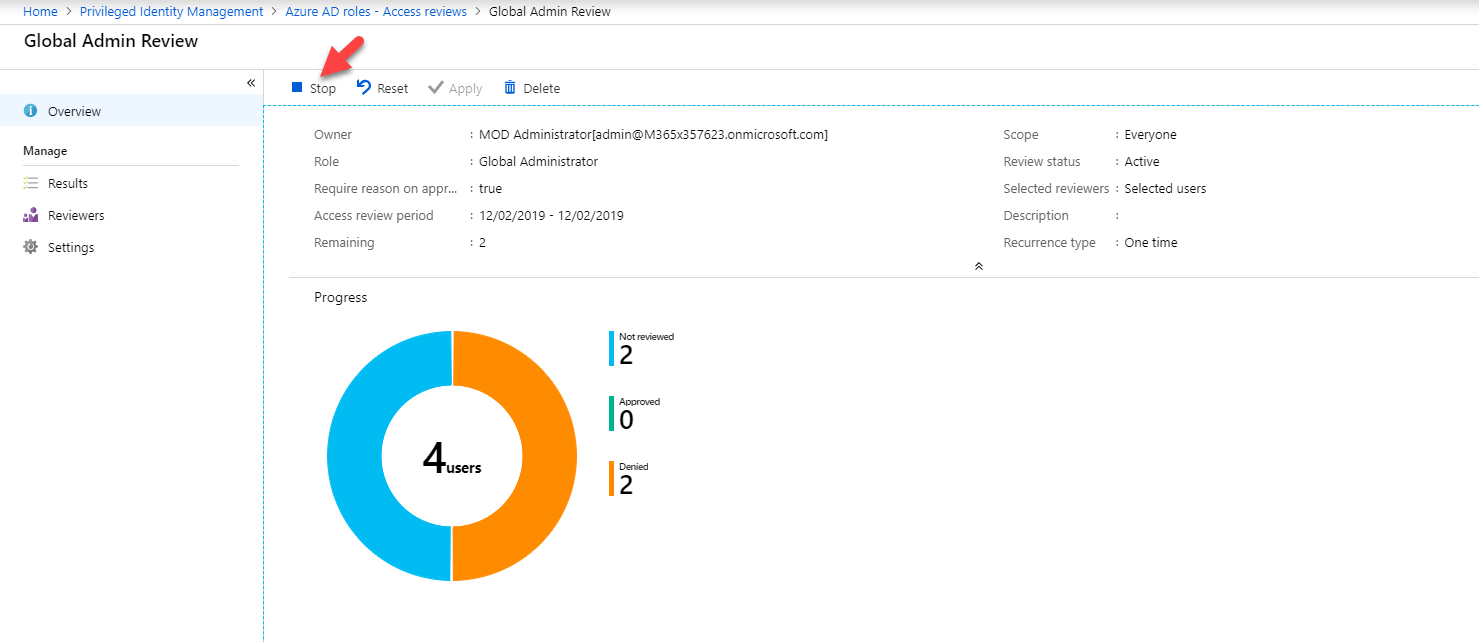
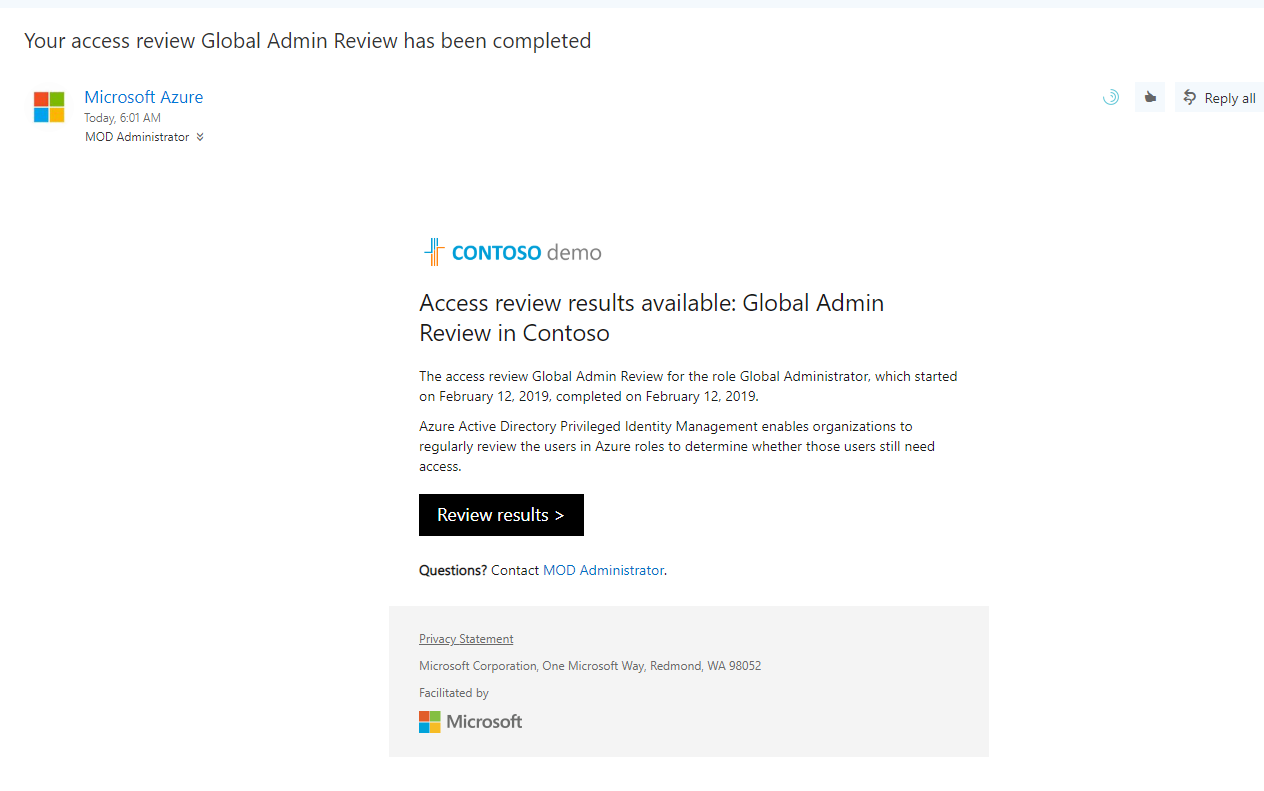
• Audit takes time – We can review the group memberships & their activities manually. But it takes time. if its manual tasks and also if it takes time most probably administrators will not do it more regularly. PIM access review is fully automated so you can schedule it run according to your requirements.
[su_note]You need to have supported subscription to use Azure PIM. It is available under Azure AD Premium P2, Enterprise Mobility + Security (EMS) E5, Microsoft 365 M5[/su_note]
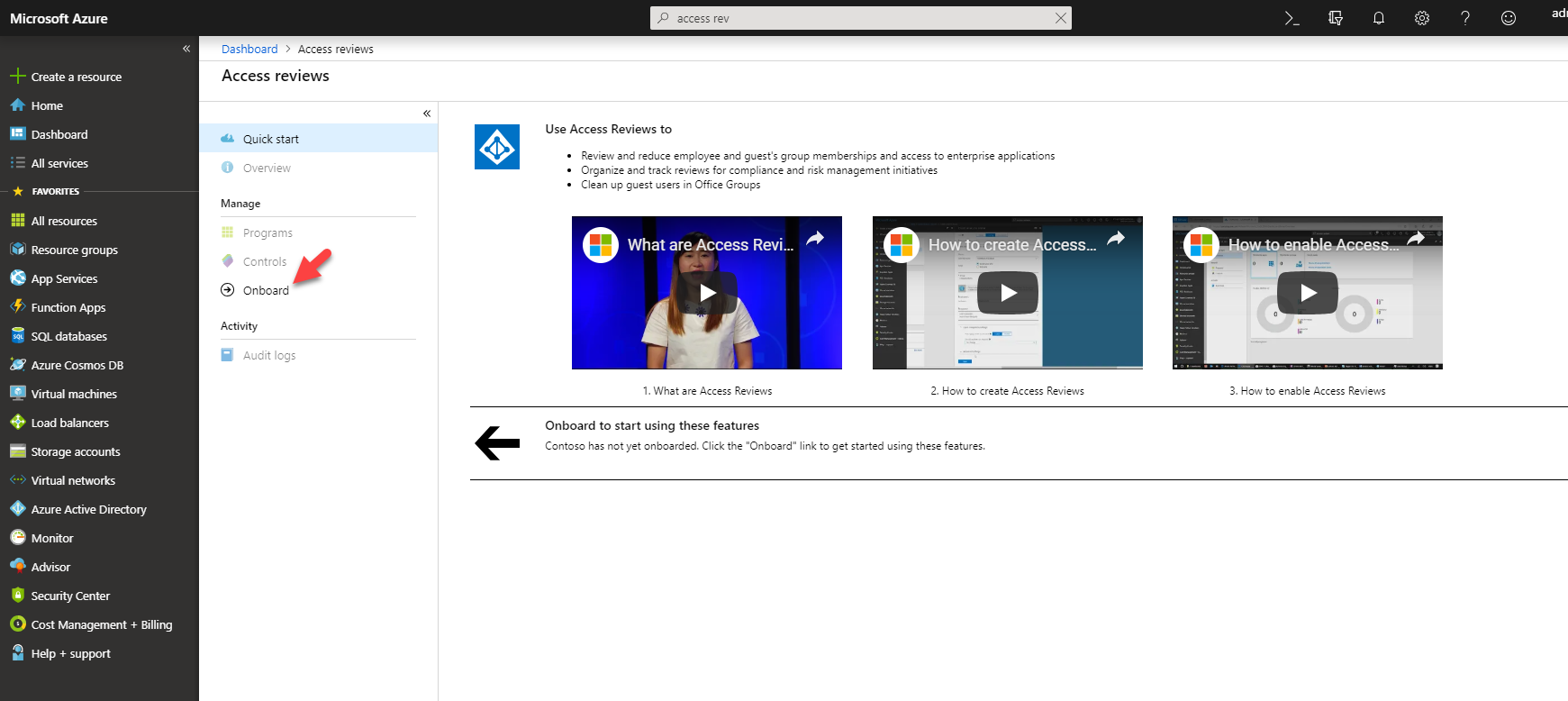
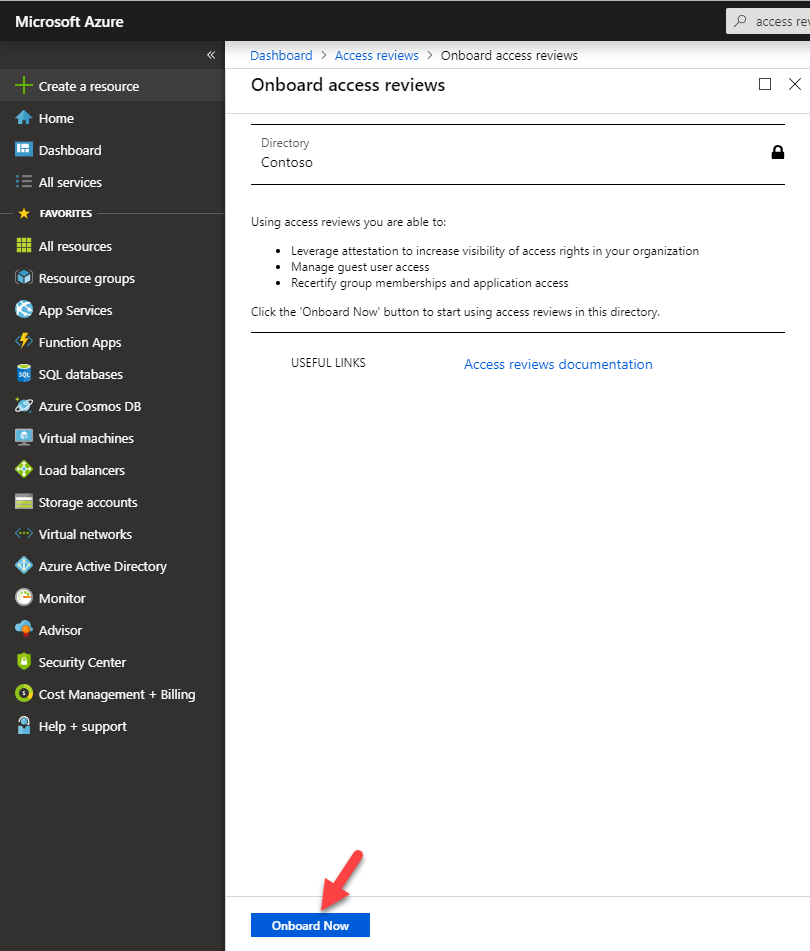
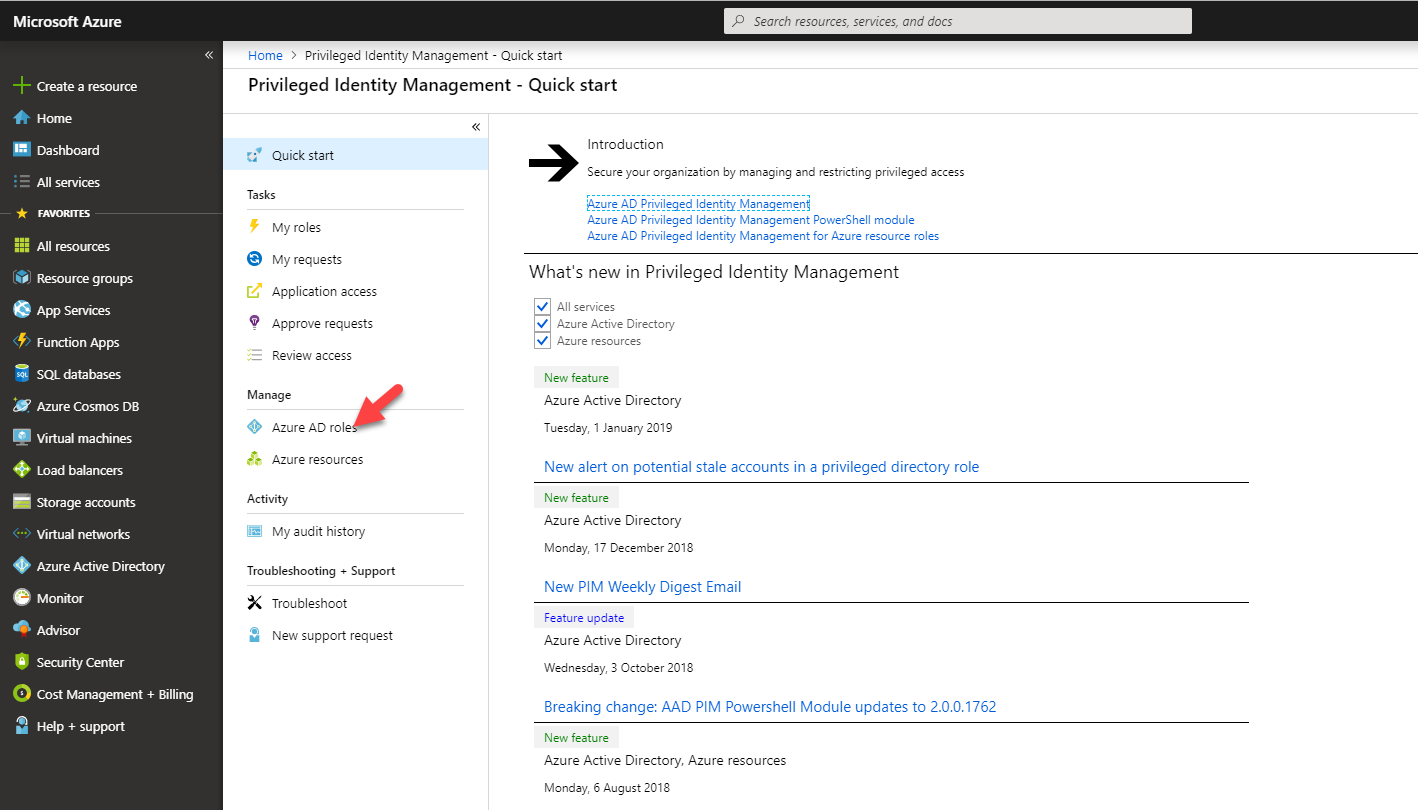
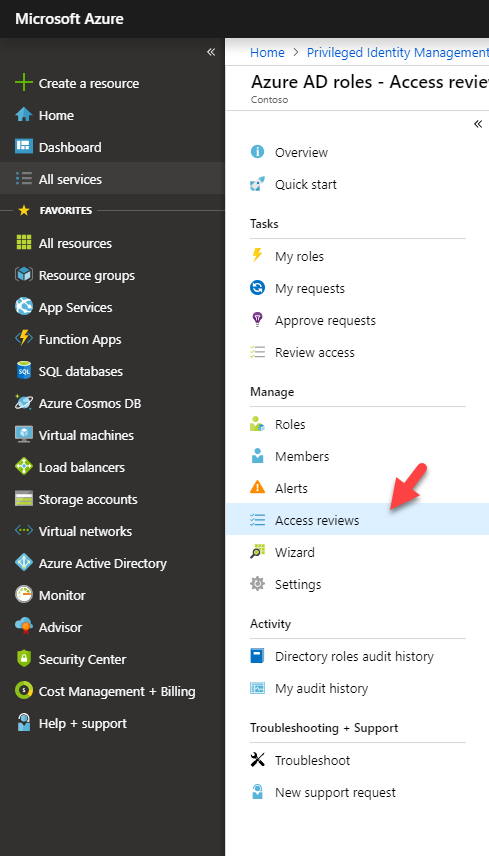
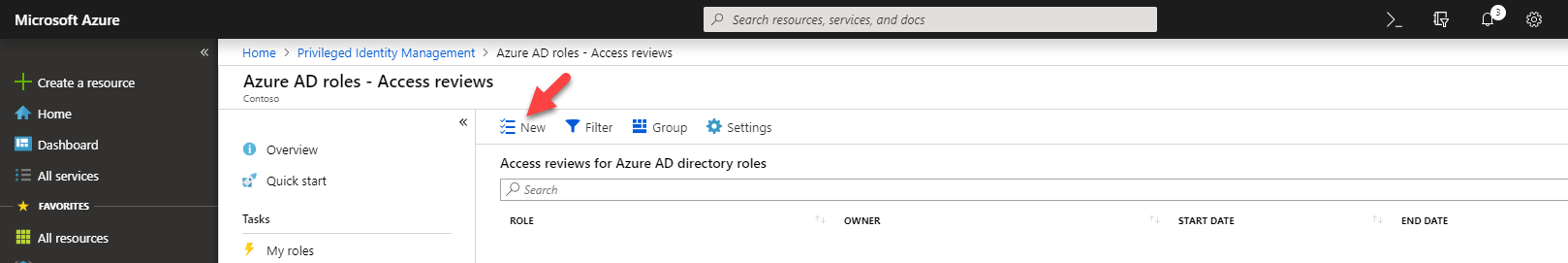
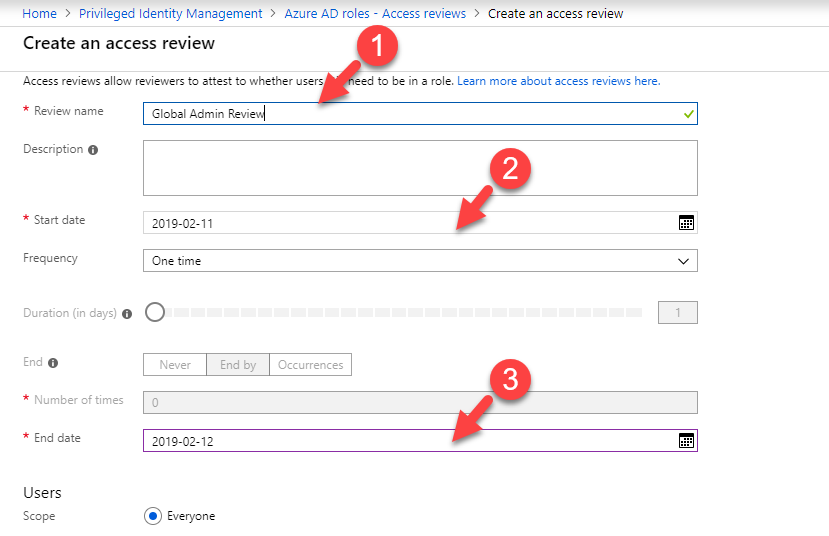
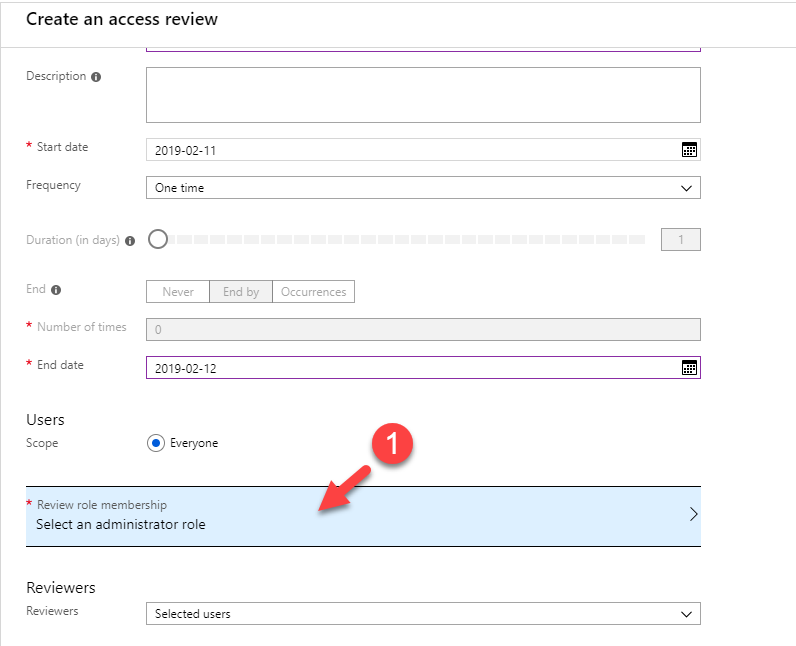
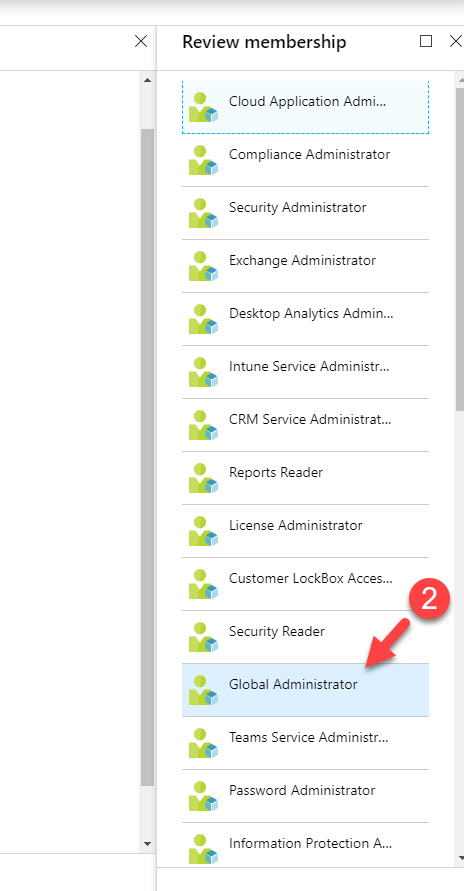
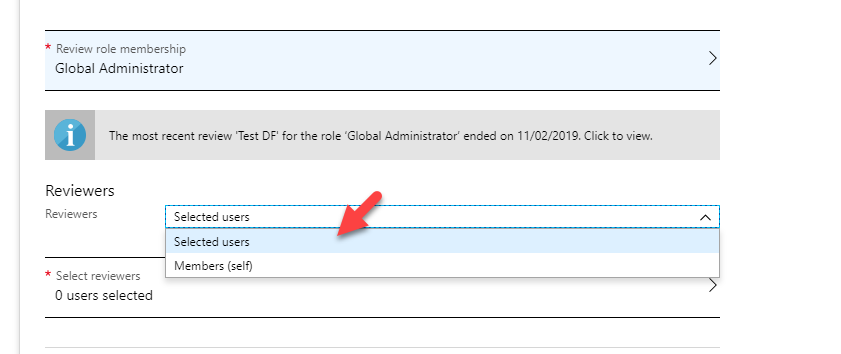
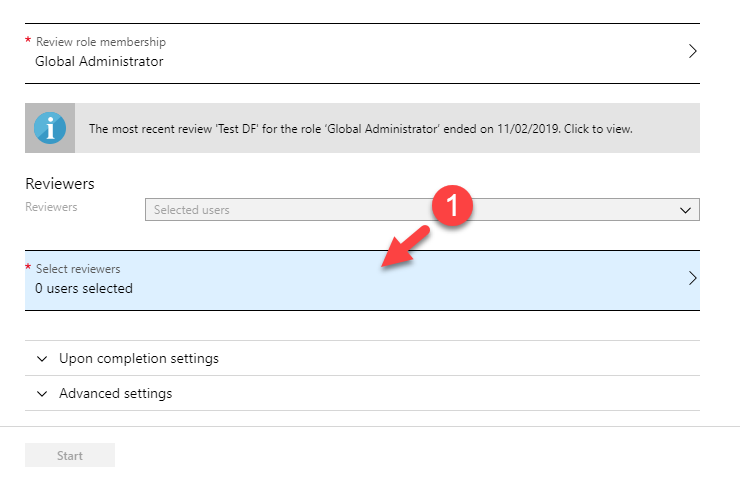
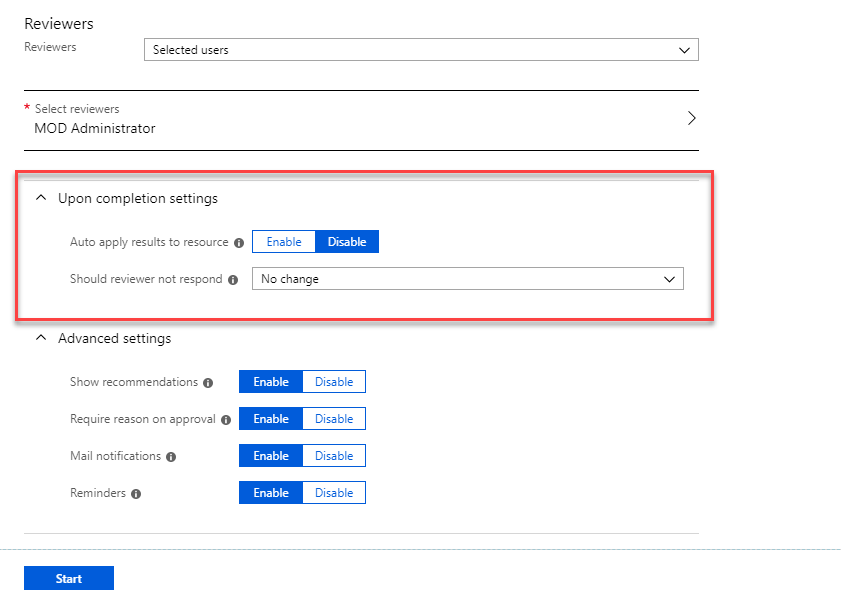
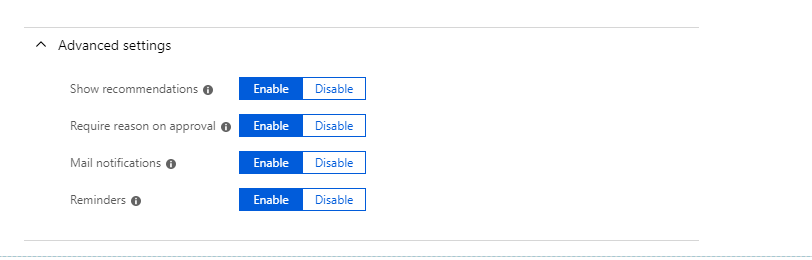
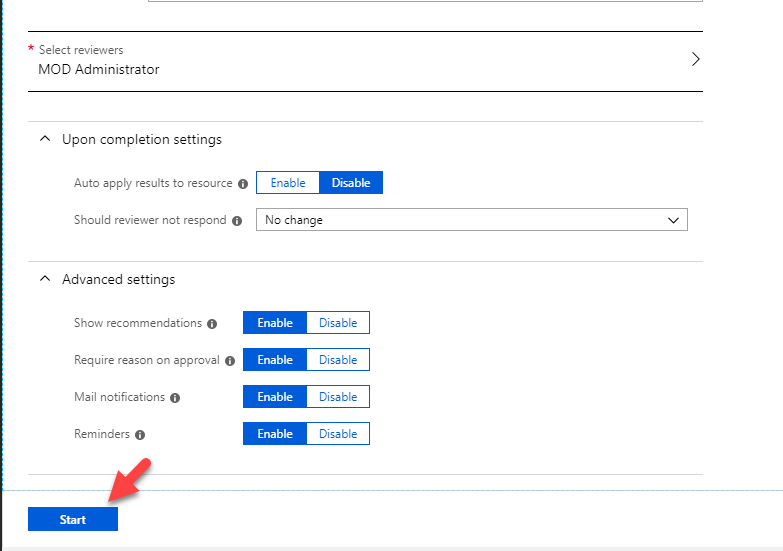
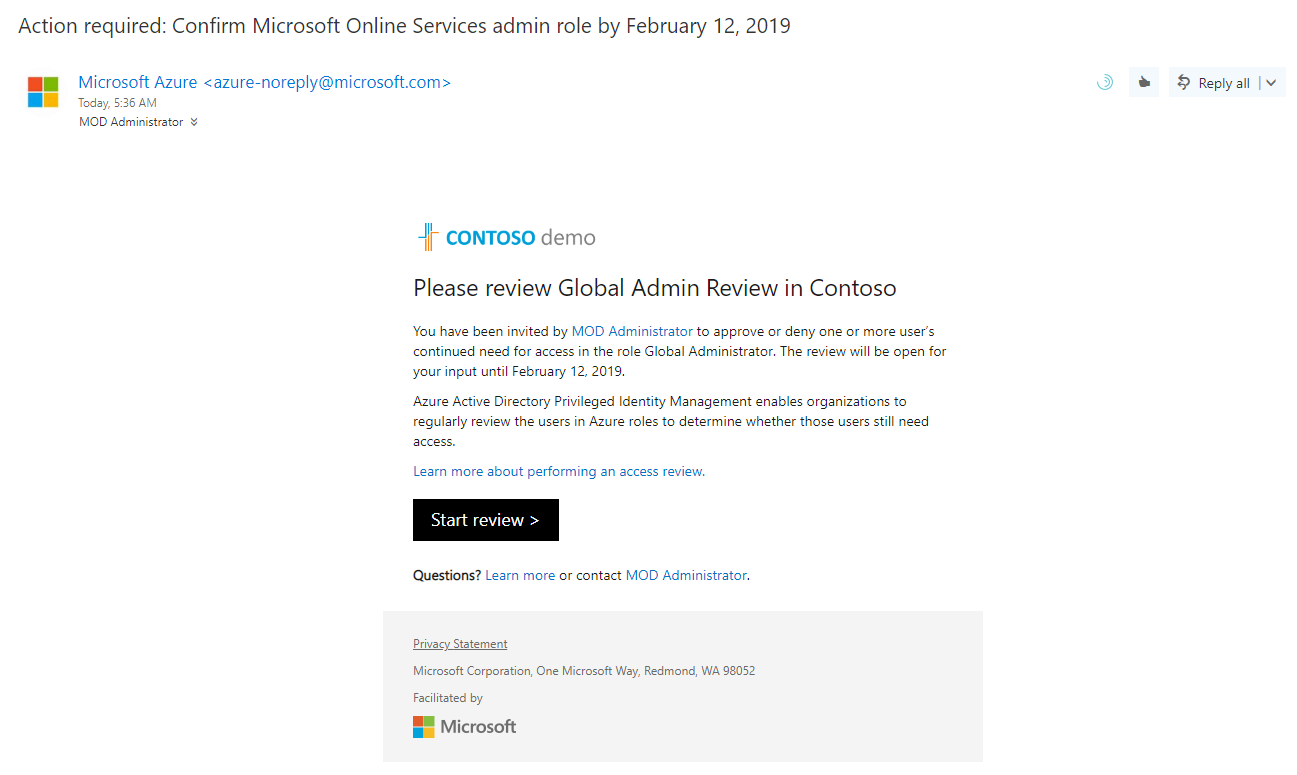
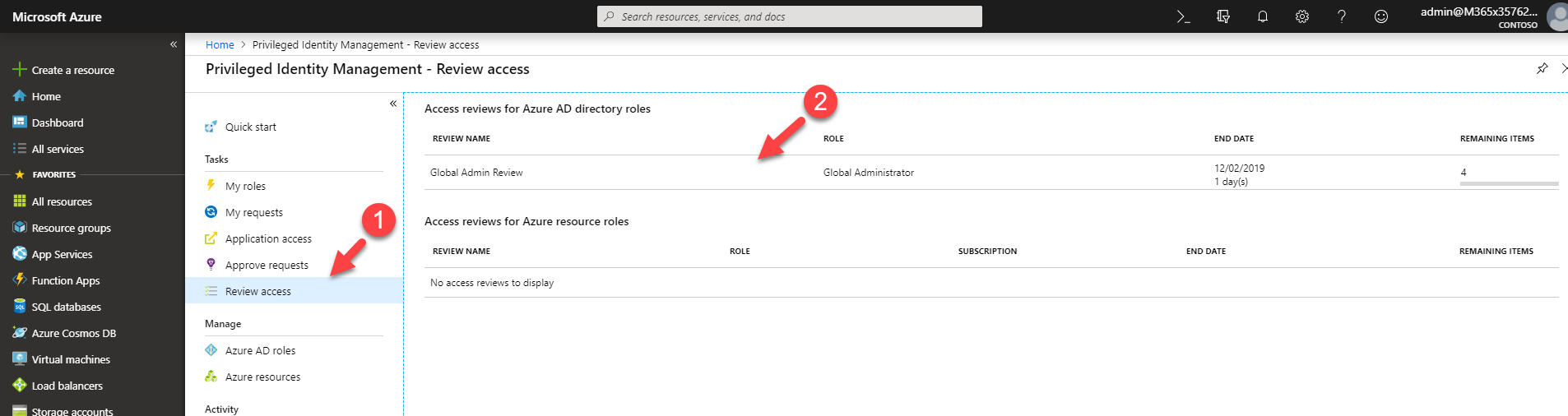
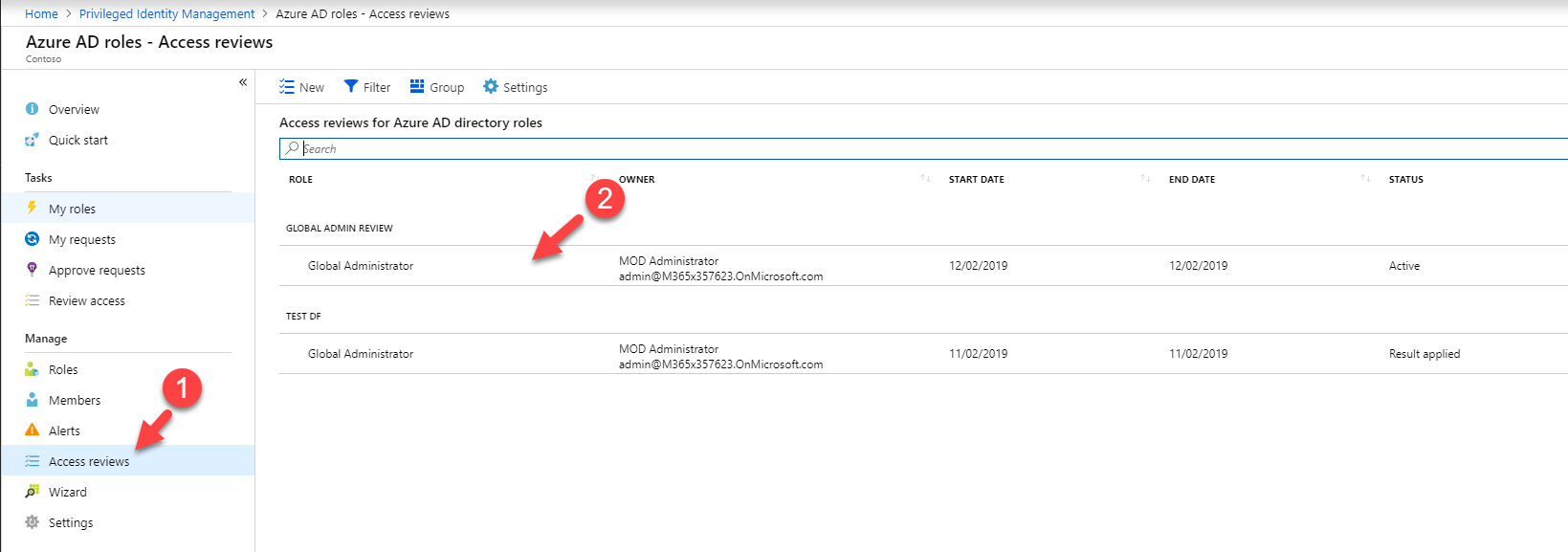
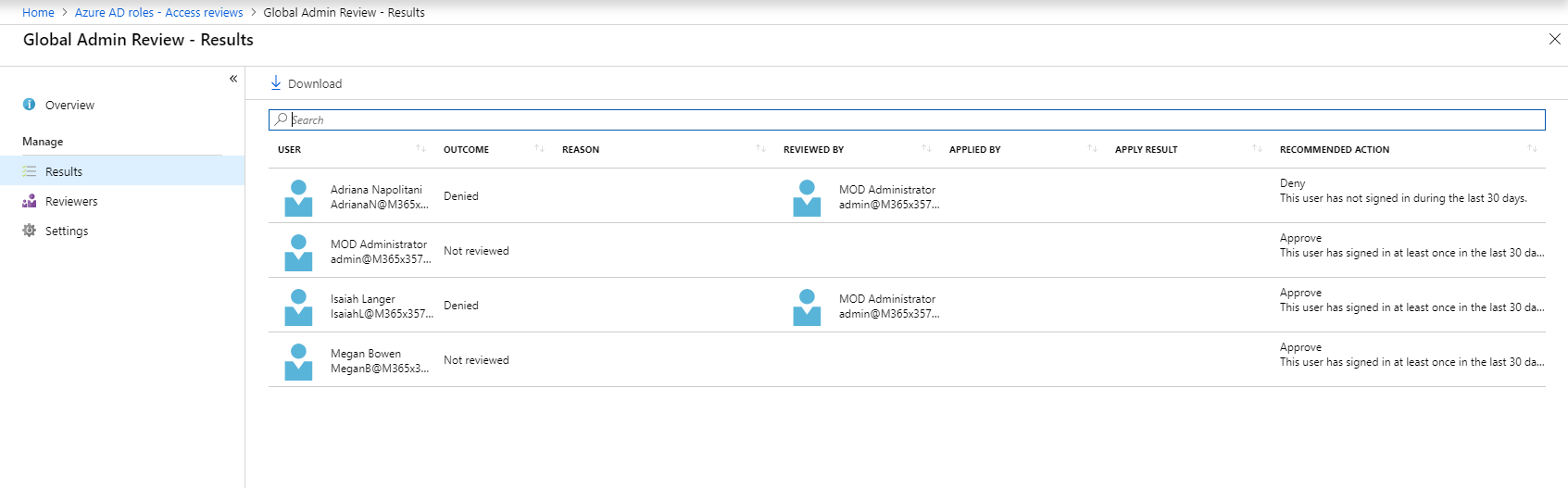
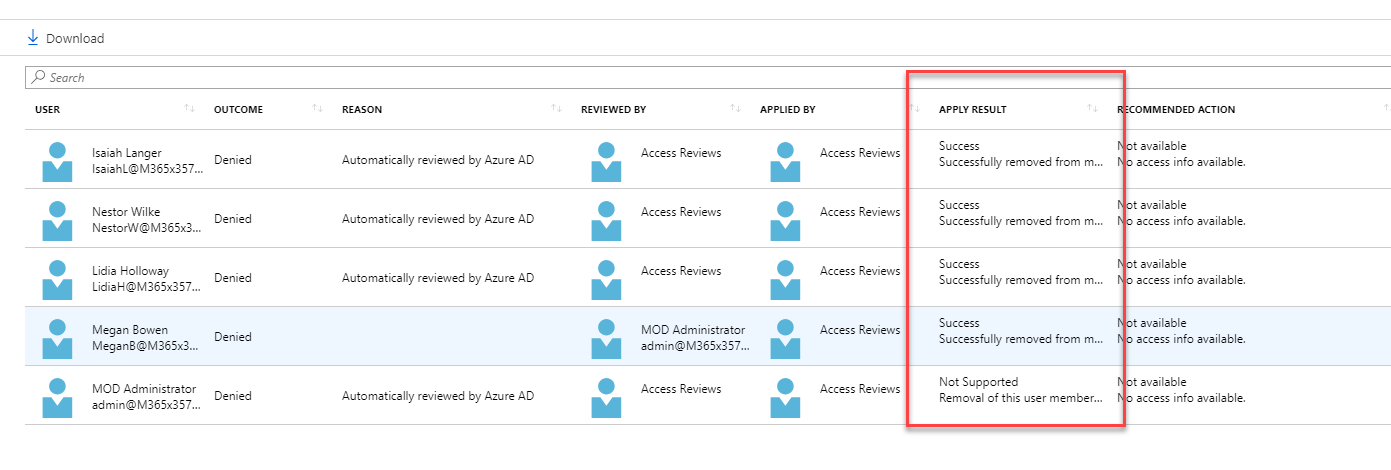
Now it is time to look in to implementation. In my demo I am going to create an access review for Global administrator role. To do this,


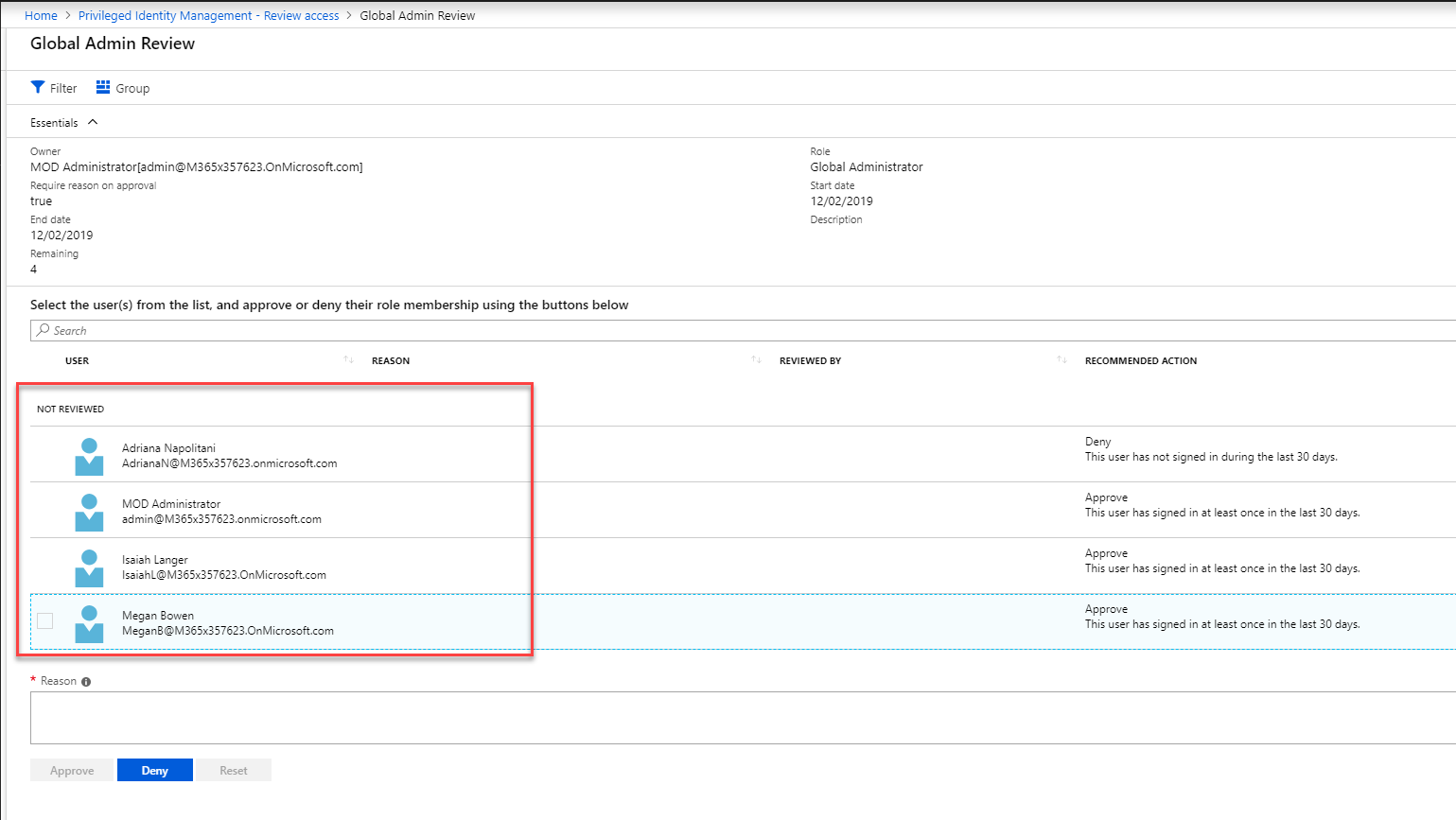
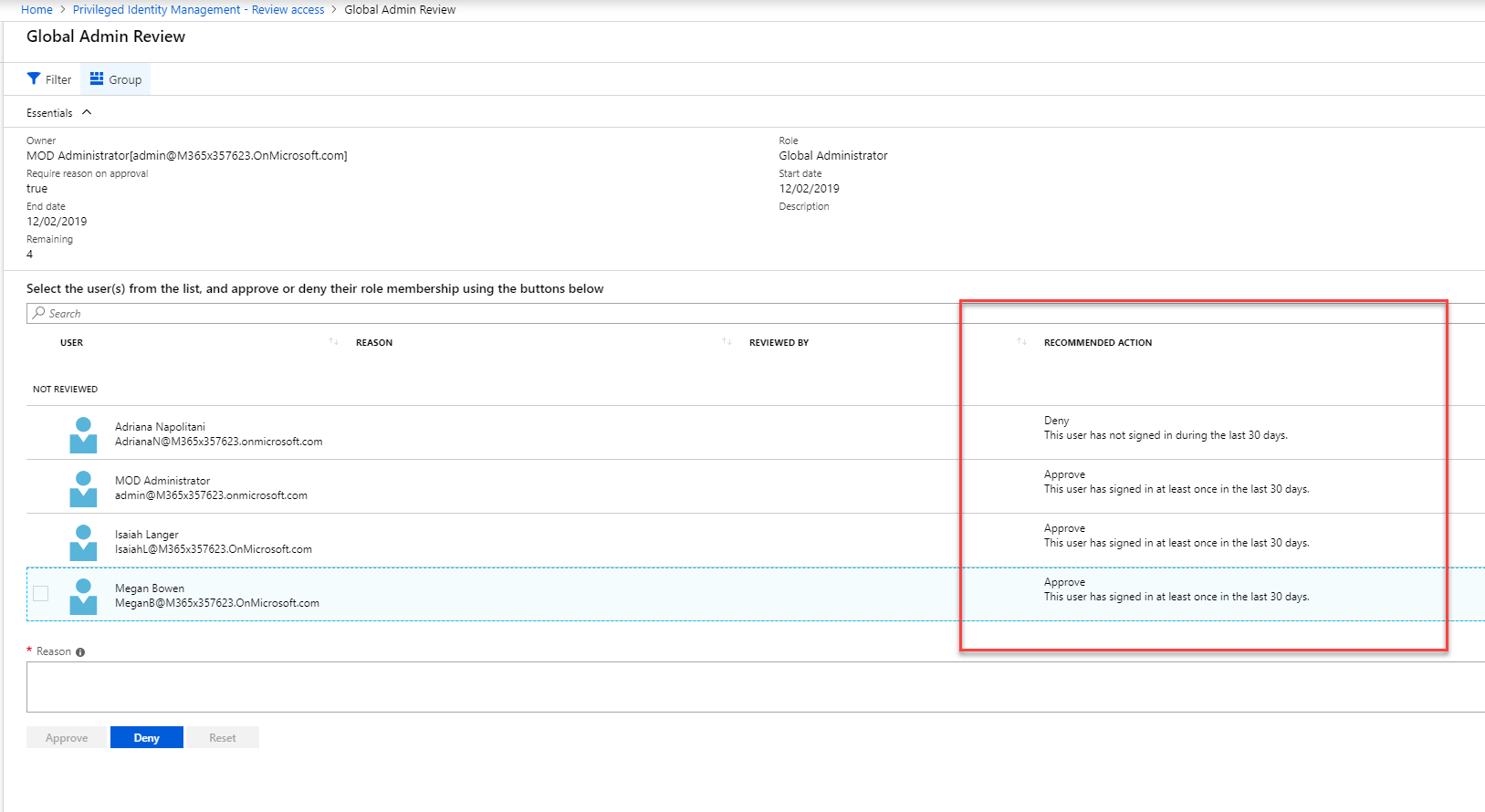
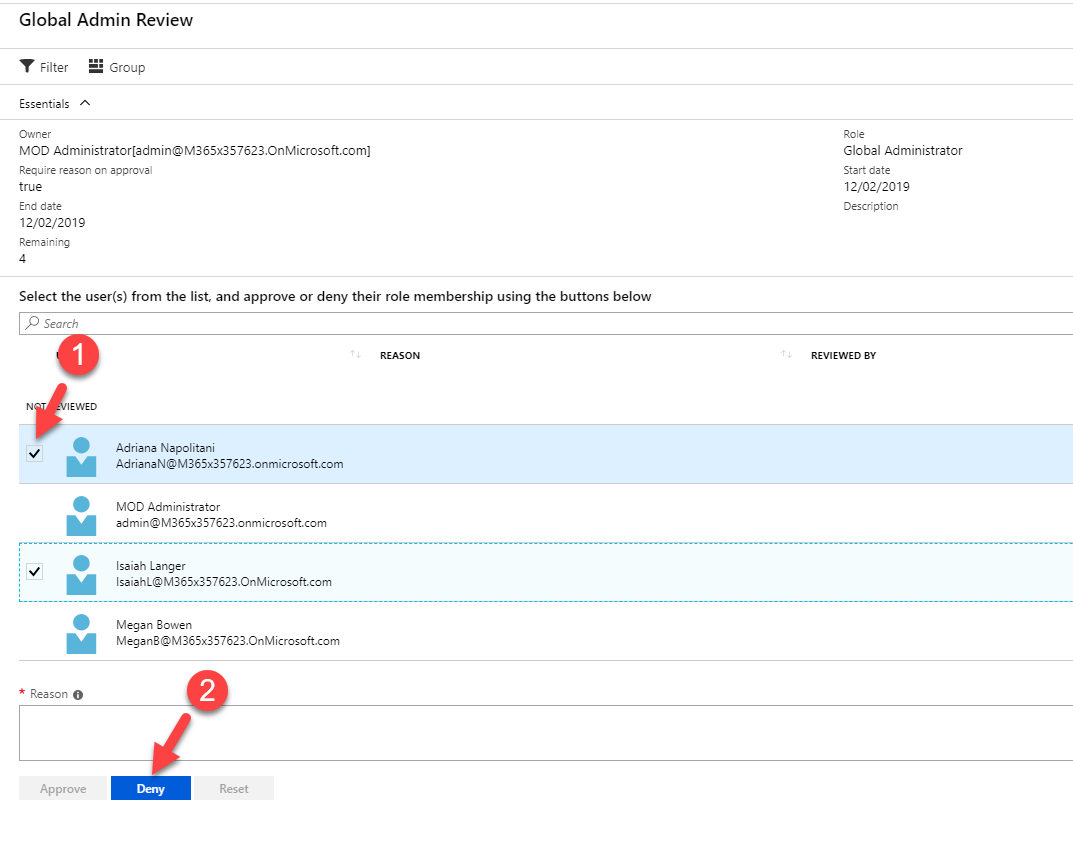
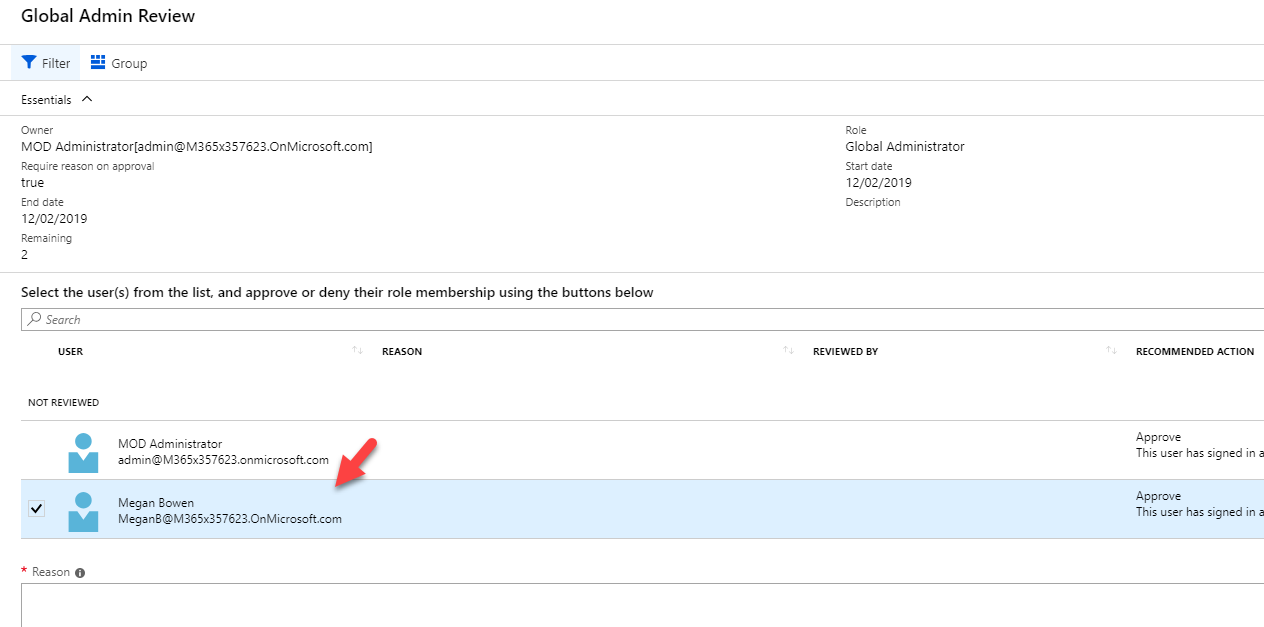


great article