In active directory environment, LDAP (Lightweight Directory Access Protocol) is responsible for read and write data from AD. By default LDAP traffic transmitted un-secure. You can make this secured transmit based on SSL. In security prospective even in more “local” network it’s important to make secure even though most of engineers not using it. But when you have hybrid or cloud only setup this is more important. Idea of this post is to demonstrate how to enable secure LDAP on Azure AD managed domain.
There is few prerequisite required to perform this task.
1) Azure AD Domain Service – Azure AD domain service must be enabled and configured with all prerequisite. If you need any help over please refer to my last few posts which explain how to configure.
2) SSL Certificate – It is need to have valid SSL certificate and it need to be from valid certificate authority such as public certificate authority, enterprise certificate authority. Also you can still use self-sign SSL certificate.
In my demo,
1) I have already configured a Azure AD managed domain and running with active subscription
2) I got an Azure VM connected to Azure managed domain and I will be using it to demonstrate to enable Secure LDAP.
3) I am going to use self-signed certificate to create the secure LDAP
Create self-signed certificate
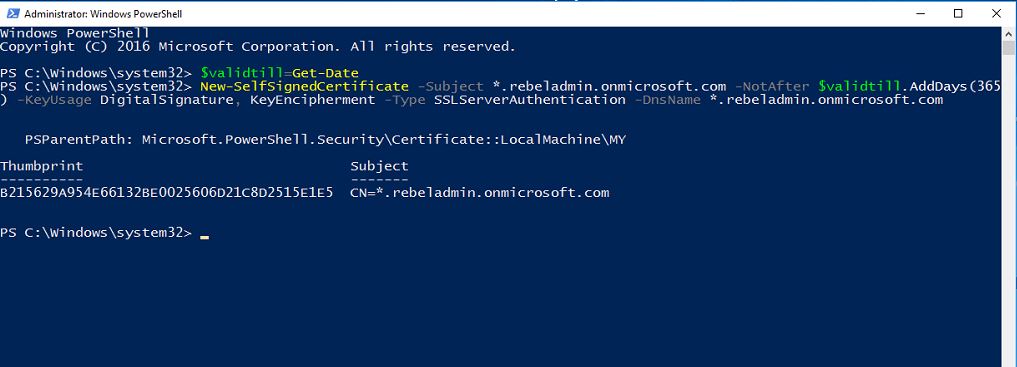
1) Log in to domain joined server, or PC and open windows power-shell session as administrator.
2) Execute following
$validtill=Get-Date
New-SelfSignedCertificate -Subject *.rebeladmin.onmicrosoft.com -NotAfter $validtill.AddDays(365) -KeyUsage DigitalSignature, KeyEncipherment -Type SSLServerAuthentication -DnsName *.rebeladmin.onmicrosoft.com
In here you can replace rebeladmin.onmicrosoft.com with your managed domain name.
This will generate the self-sign certificate.
Export the SSL Certificate
Now we have the certificate, but we need to export it to use to enable secure LDAP.
1) Log in to the PC or Server which generated certificate as administrator
2) Go to run > mmc
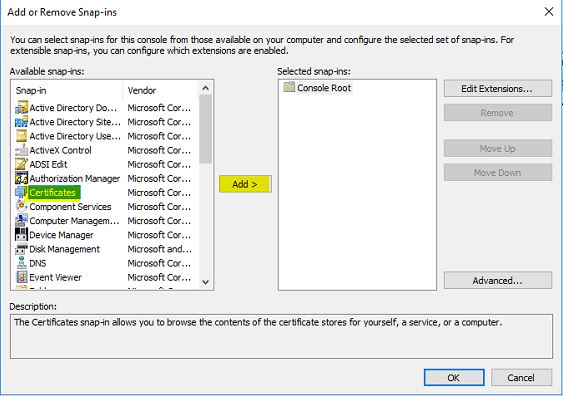
3) File > Add/remove Snap-in
4) Select Certificates and click on button Add
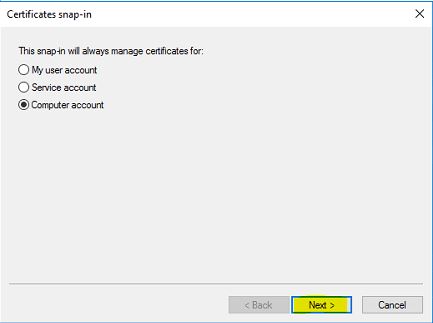
5) Then select the Computer Account and click next
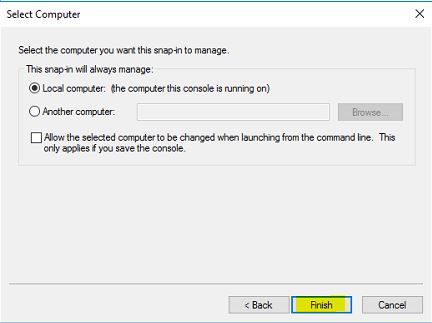
6) Select local computer and click on finish
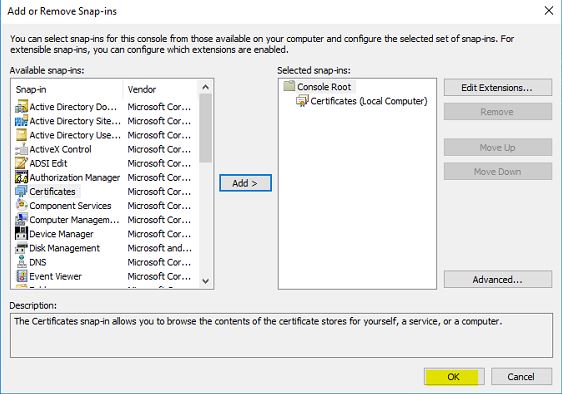
7) Click on OK to open the certificate mmc
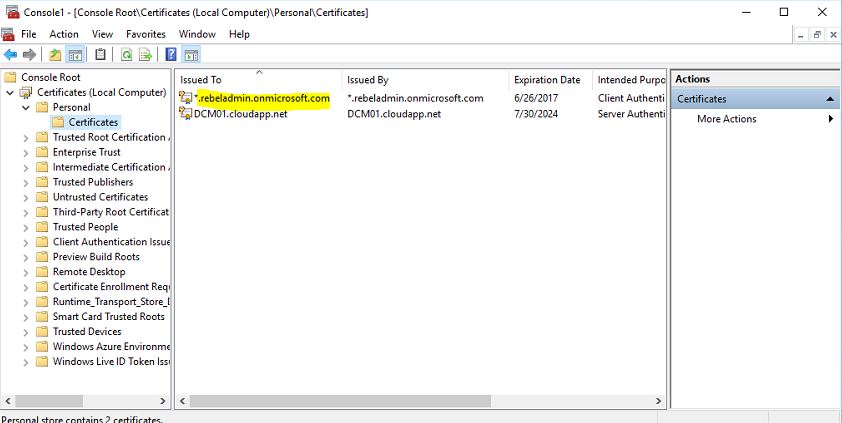
8) Then in console go to Personal > Certificates and you can see the new self-signed certificate we just created in previous step
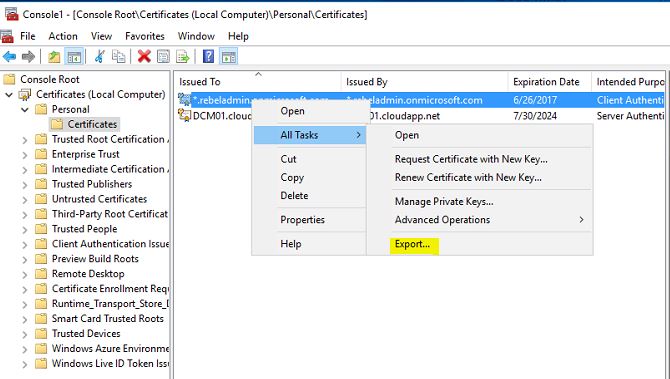
9) Right click on the certificate and click on All tasks > export
10) Then its start the certificate export wizard, click on next to start
11) In this window select option “Yes, export the private key” and click on next
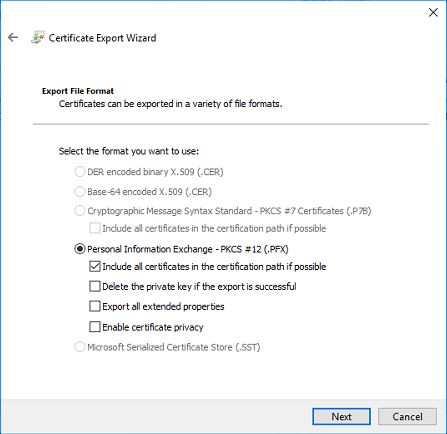
12) Leave the .pfx option selected and click next
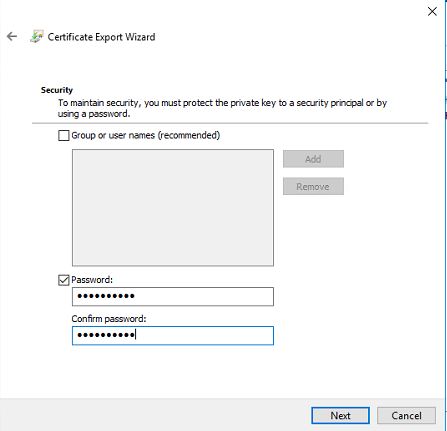
13) In next window define a password and click on next
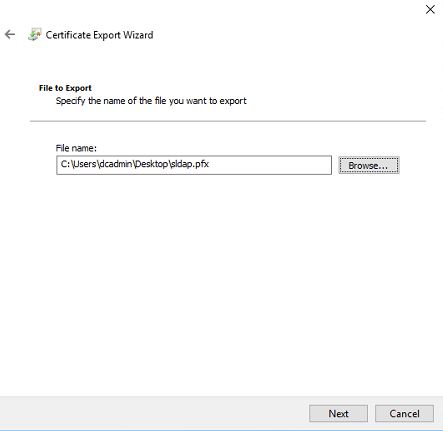
14) Then define the location to save the file and click on next
15) Click on finish to complete the export process
Enable Secure LDAP
Now we got the SSL exported and ready. Now it’s time to enable the secure LDAP.
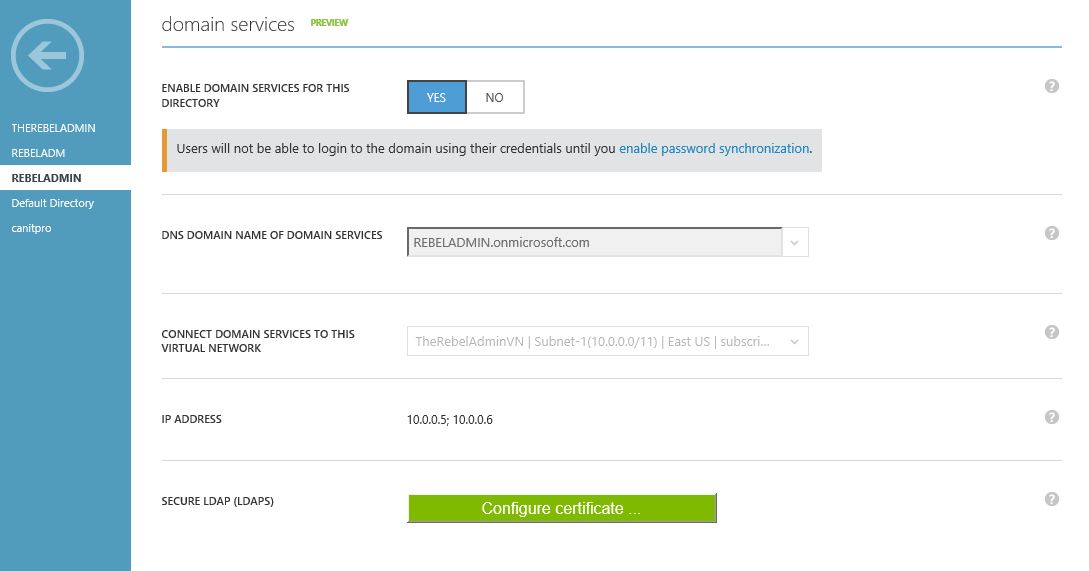
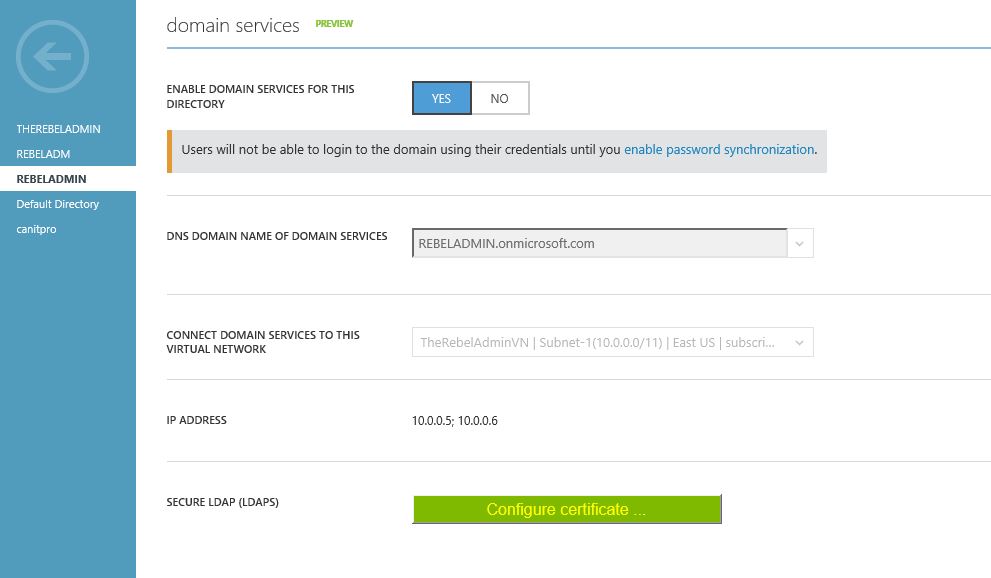
1) Log in to the azure portal and load the Azure Domain Services configuration page for your relevant directory
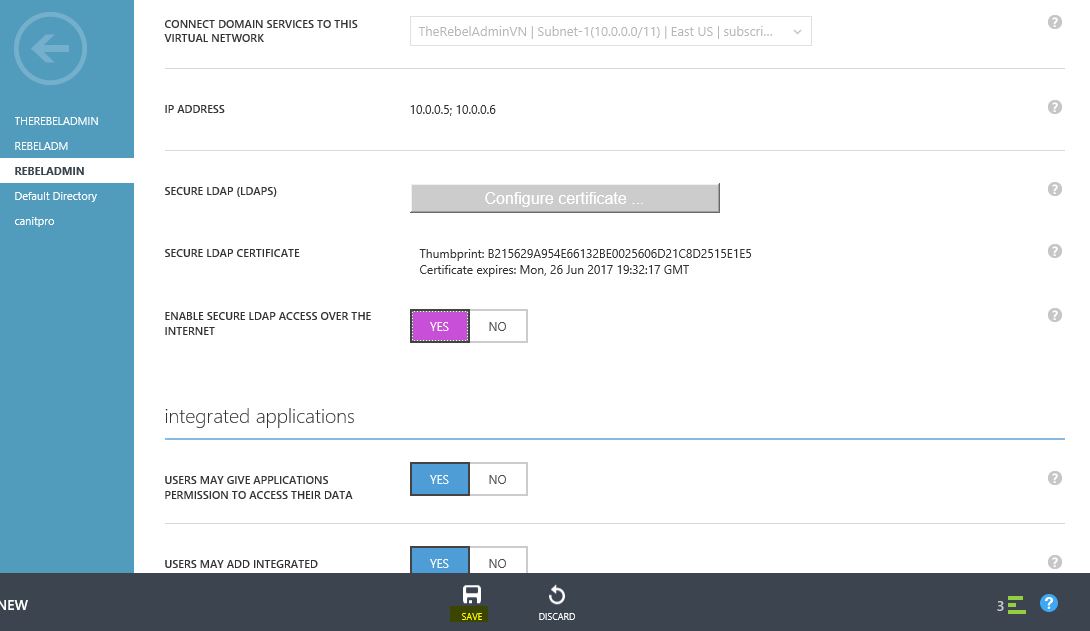
2) Then to the domain service section and click on “configure certificate” button
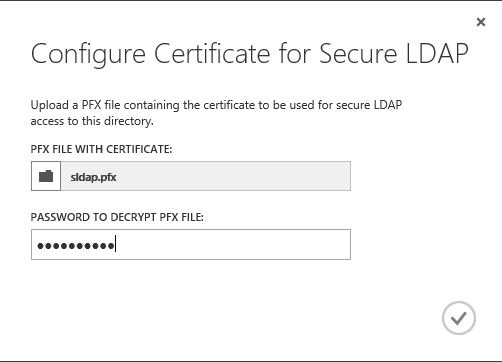
3) Then brows for the .pfx file we just exported and provide the password, then click ok to proceed
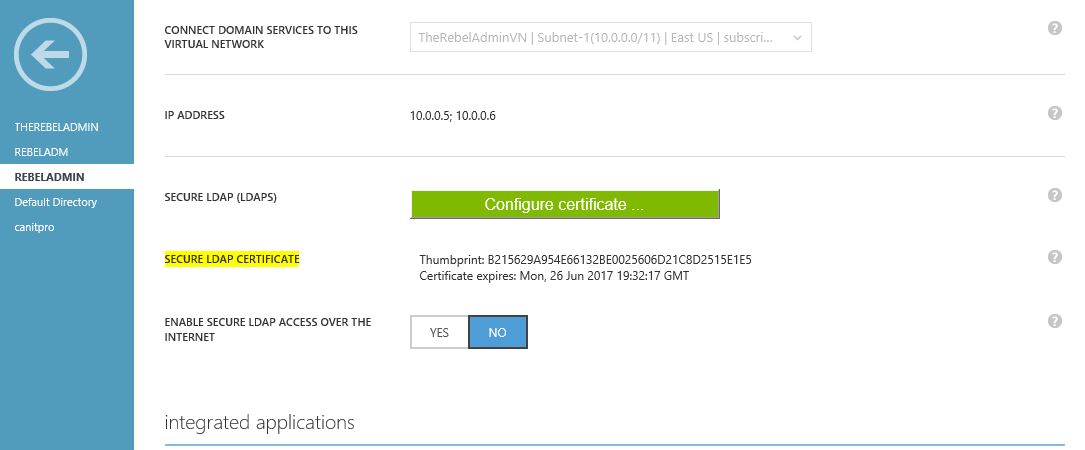
4) After few minutes we can see the secure LDAP is enabled
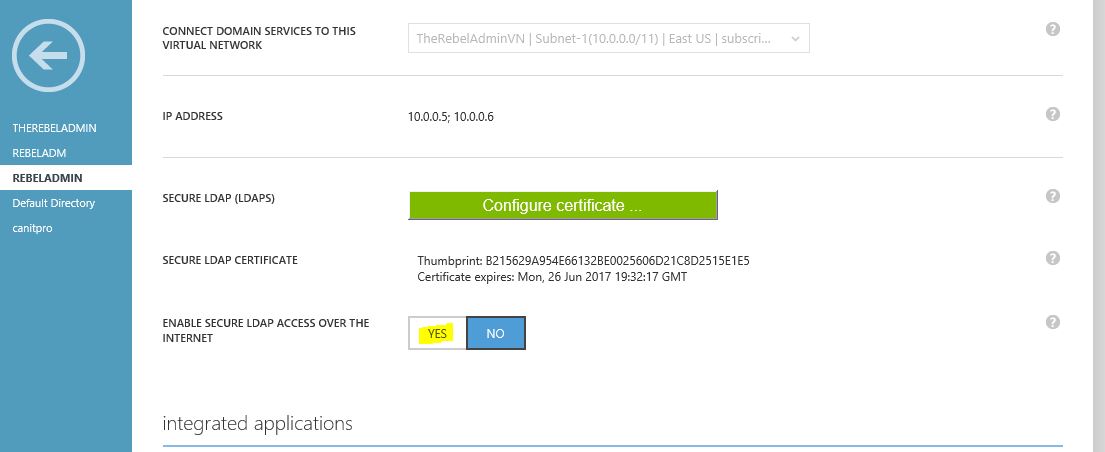
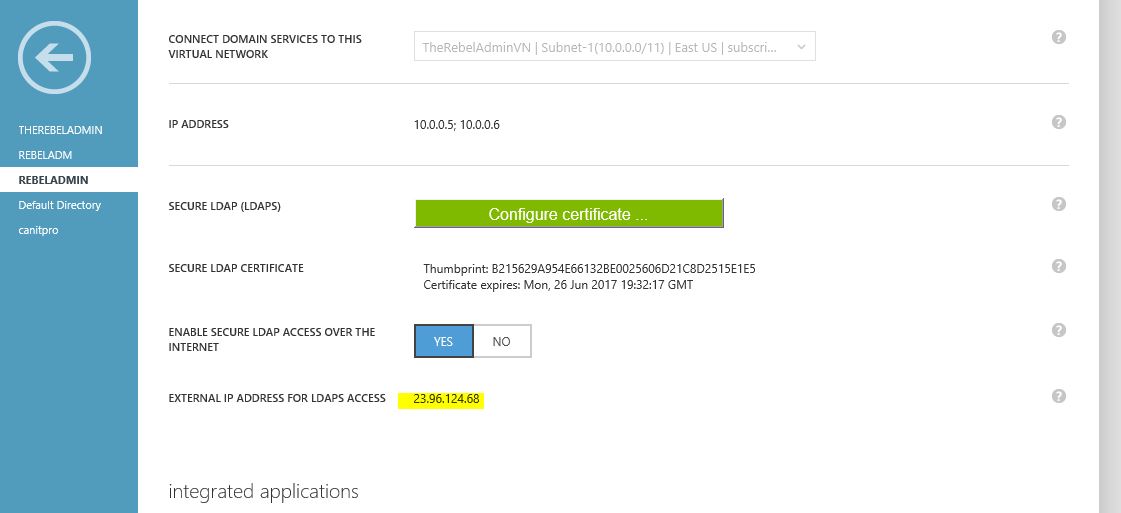
5) The next step is to enable the secure LDAP connection over the internet for your managed domain. For that click on the “Yes” for the option “Enable secure LDAP access over the internet” and the click save
6) After few minute we can see the feature is enabled and also displaying the public ip address which can use on this.
7) If you wish to use secure ldap over the internet you need to create DNS entry in your dns provider and create A record to point domain to the public ip address its given.
Hope this was helpful post and if you have any question on this feel free to contact me on rebeladm@live.com