If you work with Active Directory you may already know what is roaming profiles is. Roaming profiles allows to sync application and user settings to a file share. When same user login from another computer in to same domain, those settings will sync back from file share. It allows users to have same user experience and data in different corporate devices. Azure Active Directory users may also login from multiple Azure domain joined devices. Enterprise state roaming allows to sync user settings and application settings securely across corporate azure domain joined devices.
Secured Sync – When this feature enables it will activate free limited Azure Rights Management subscription. It will use to encrypt and decrypt data which is sync to cloud. This will ensure the security of data used by Enterprise State Roaming feature.
Data Storage – Data storage location for Enterprise State Roaming feature will be align with your Azure Active Directory subscription region. It will not sync between different regions.
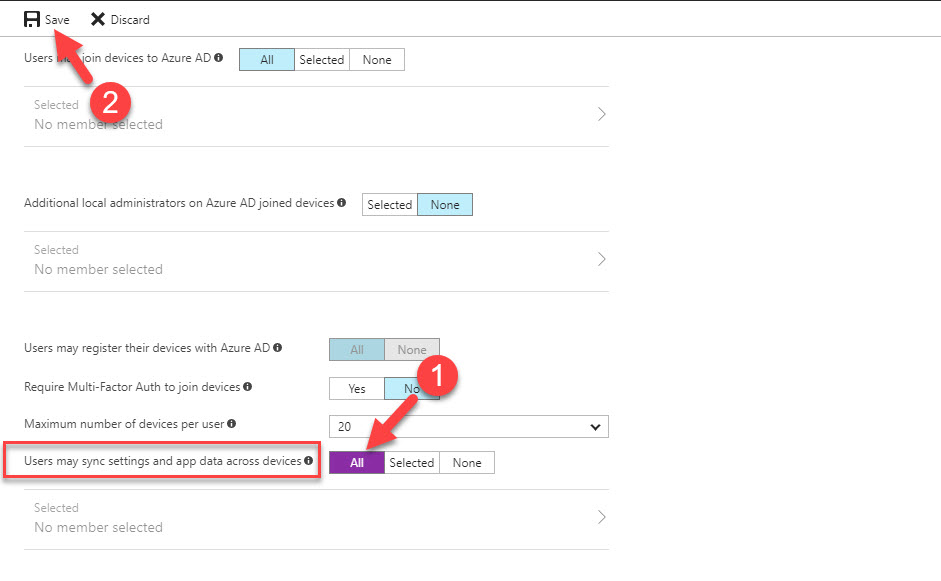
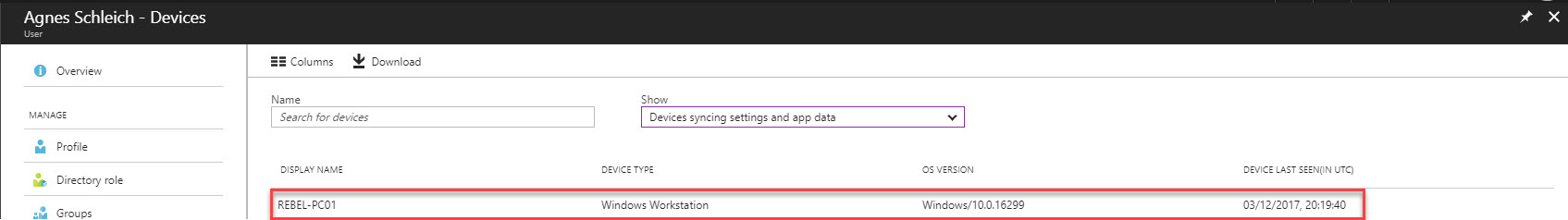
Better Control – This feature can be enable for entire directory or only for selected users. Sync data for each device can review using portal. With help of Azure Support, administrators also can forcefully remove sync data for a device.
Data Retention – If user account been deleted from directory, profile data will be deleted after 90 days. Administrators also can request (from azure support) to delete specific data from a user profile. If data not been access for 1 year it will consider it as stale data and remove forcefully. It will also happen if Enterprise State Roaming feature is disable in later time.
Let’s see how we can enable this feature. In order to enable this feature, you must have Azure AD Premium or Enterprise Mobility + Security (EMS) license. Azure AD join devices must be running with Windows 10 (Version 1511, Build 10586 or greater)