This is the part 2 of the series of articles which will explain the setup and configuration of windows azure active directory. If you still not ready it you can find it here.
Step-by-Step Guide to setup windows azure active directory – Part 01
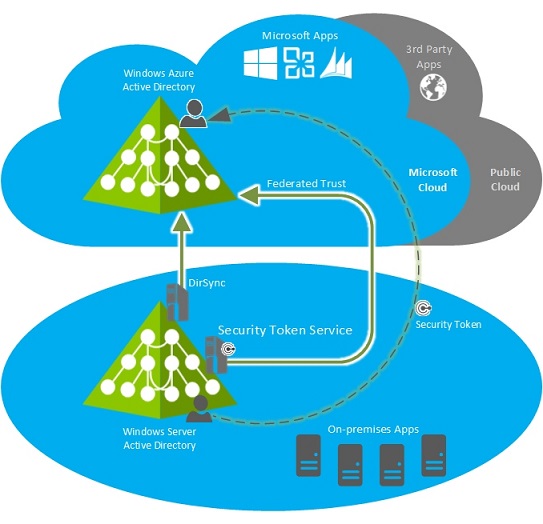
In part 01 we install a WAAD instance and add a domain. In this post let’s see how we can configure integration with local domain infrastructure.
WAAD can integrate with Local AD on 3 way.
1) DirSync with Password Sync – Using this sync local users can log in to the windows azure service using same user name and password. But this is only sync the password. This is not providing SSO.
2) DirSync with SSO – This is the most seamless integration method. To setup SSO it needs to have security token service installed and configured in local AD infrastructure such as active directory federation services (AD FS)
3) Multi-Forest DirSync with SSO – This is very similar to the above option but this is works with multiple forest infrastructure. It’s quite complex but still seamless method for authentication.
In this demo I am going to use DirSync with SSO option. I will be using AD FS as the STS. This provides SSO experience for users to log in to local resources as well as cloud services.
The detail check list for this process available on here it includes detail description about all the steps.
Here I list few major points which you should consider.
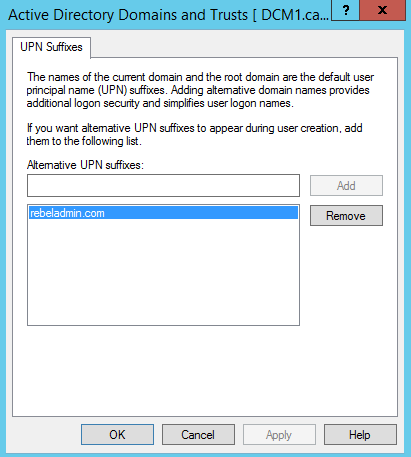
1) The domain name you going to integrate should be a public domain name. Which means if you using domain name such as contoso.local you should add complete UPN suffix such as contoso.com. you can find a post I wrote about changing UPN on http://www.rebeladmin.com/2015/01/how-to-configure-multiple-user-principal-name-upn-suffixes/
2) AD must be running with windows server 2003 R2 or greater.
3) Based on the STS model you will need use the WAAD module for windows PowerShell to establish federation trust between azure AD and local AD.
AD FS
In demo I am using active directory federation service (AD FS) as the STS. I am not going to demonstrate how it can be set up in here. But if you not aware how to setup AD FS you can follow up the series of articles I wrote about AD FS. It can be found on http://www.rebeladmin.com/?s=Active+Directory+Federation+Services+%28AD+FS%29+
UPN Suffix
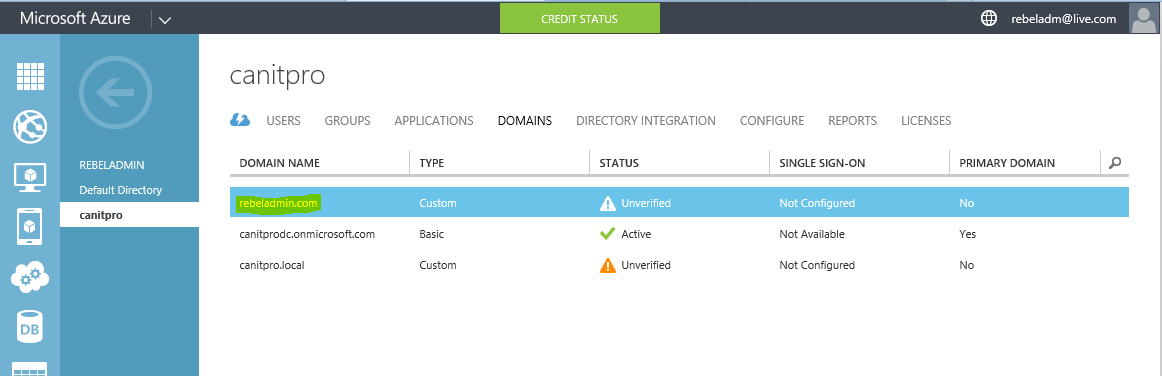
Before the integration process I add UPN suffix with public domain name to use for SSO. I also match it with the domain I added in Azure AD instance.
Install Azure AD PowerShell module for AD FS
To install the Azure AD PowerShell module for AD FS, log in to server as domain admin or enterprise admin. First install the Microsoft Online Services Sign-In Assistant for IT Professionals RTW from http://go.microsoft.com/fwlink/?LinkID=286152. Then download the module from http://go.microsoft.com/fwlink/p/?linkid=236297
Once download completes, double click on the installation file. Click next to continue.
In next window accept the terms and click next.
In next window select the installation path and click next.
Then click install, to start the installation process.
Setup Trust Relationship between AD FS and Azure AD
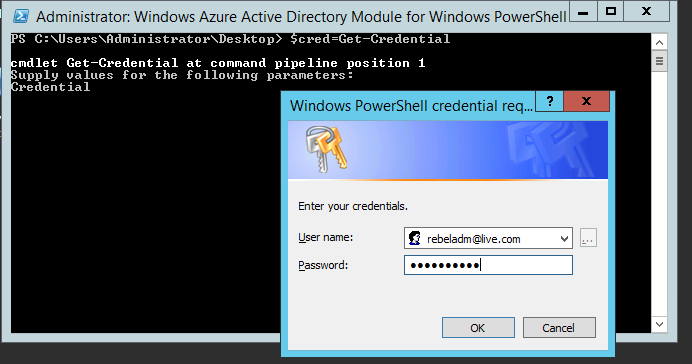
Load the PowerShell module we installed on above step.
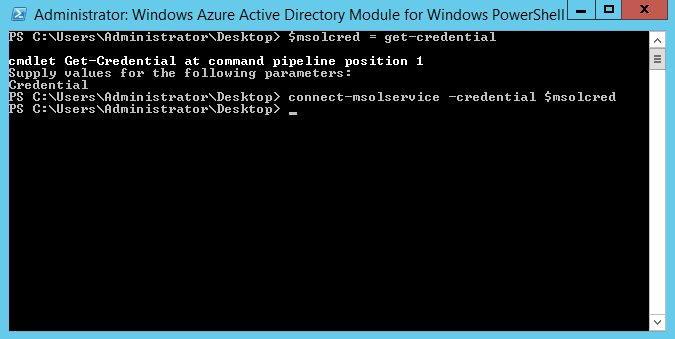
Run $msolcred = get-credential command. Once it prompt for the login, type the cloud administrator logins ( Global Admin user under the WaaD instance.
Then run connect-msolservice -credential $msolcred and it will connect you to the Azure AD.
If you are executing this commands from different server than AD FS server you need to run Set-MsolAdfscontext -Computer <AD FS primary server> . You need to replace <AD FS primary server> with AD FS server FQDN.
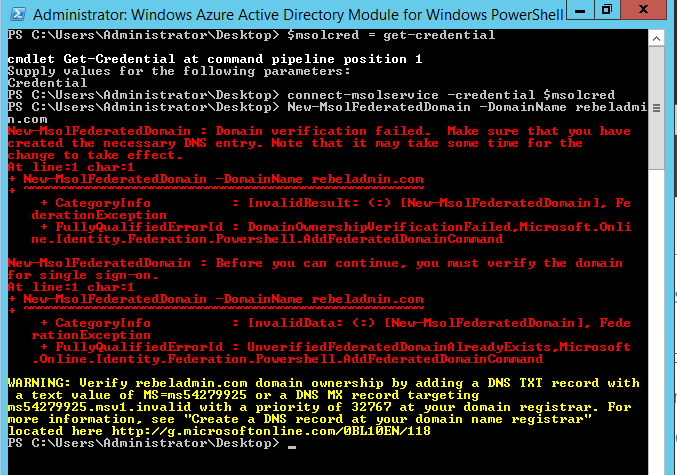
Then run New-MsolFederatedDomain –DomainName <domain> and <domain> need to replace with domain name which will use for SSO.
Then you will get error similar to following. As it says we need to create proper DNS entry on our public DNS zone. I go ahead and created it as error says.
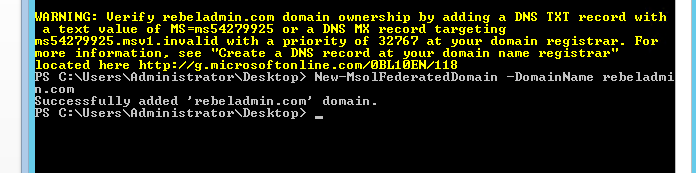
Then I can add domain using same command successfully. (Please note it take time to propagate dns changes once you do it in public dns)
Now we have create the trust between Azure AD and local AD. Next step is to do the sync.
DirSync in Action
Go to https://go.microsoft.com/fwLink/?LinkID=278924&clcid=0x409 and download the DirSync Tool.
Once download finishes, double click on it. Then click next to continue.
In next window accept the terms and click next.
In next window can specify the installation path. Once done click on next to continue.
Then it will start to do the installation.
Once it finish select the option to “start the configuration wizard now” and click finish.
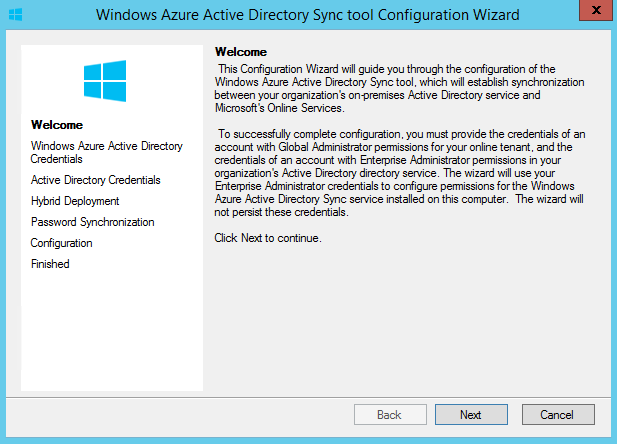
Then it will start the configuration wizard. Click next to continue
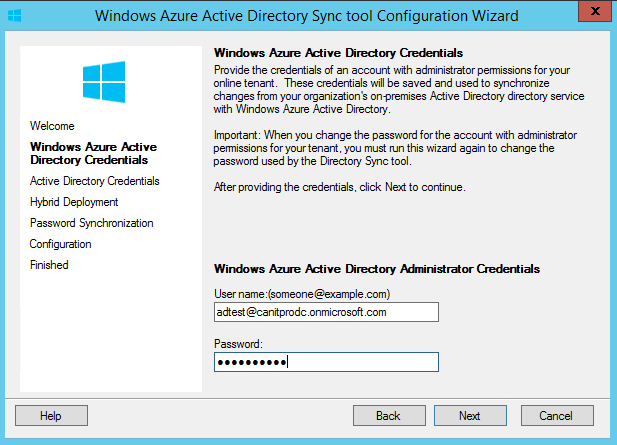
Then it ask for the Azure Ad credential. Provide the cloud administrator account info and click next.
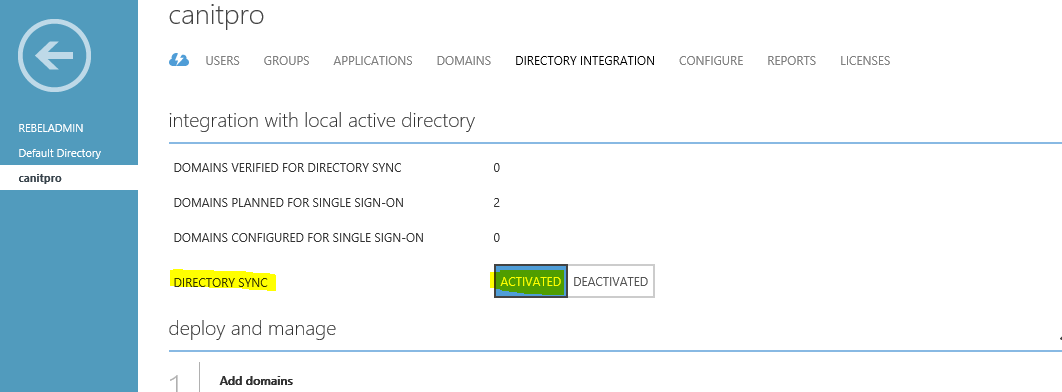
If you not set the directory sync to activate state in azure you will get error. You must activate it before continue.
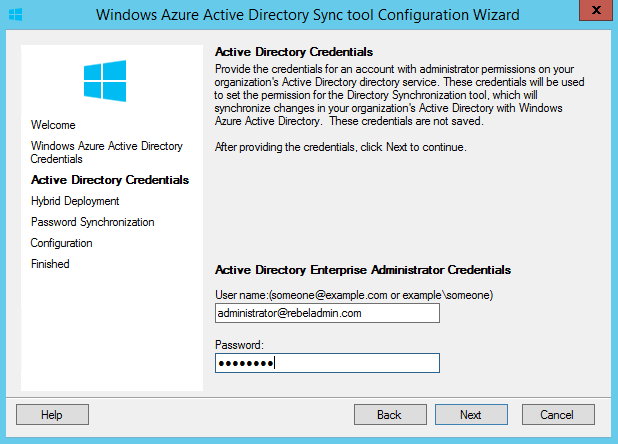
In next window it ask for local AD enterprise admin credentials. Once done click next to continue.
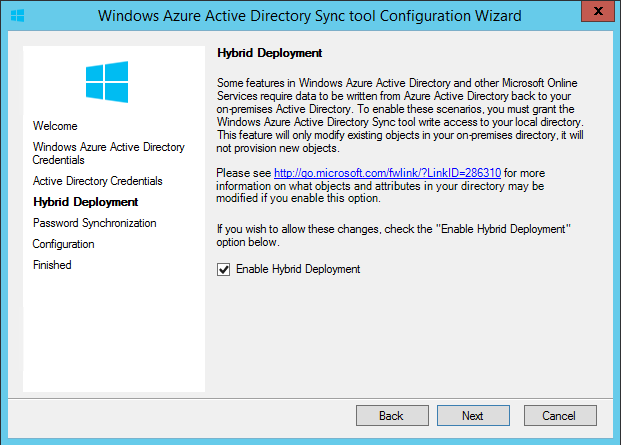
In next window it asks if need to enable hybrid deployment. In here we giving permissions to azure AD to write changes to local AD. If you wish to allow, select the option and click next.
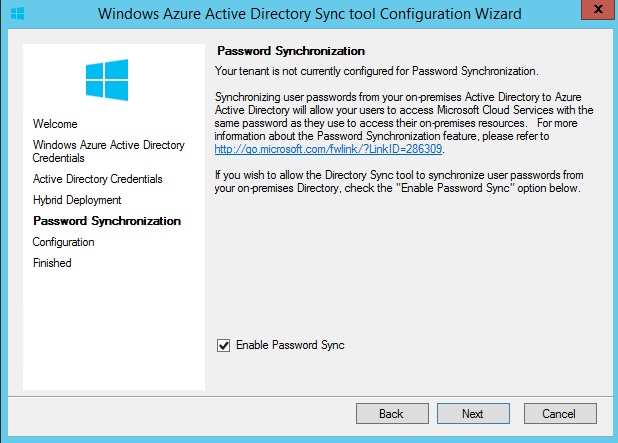
Then it ask about password sync. It is required feature so I enable it and click next.
Then it starting the configuration.
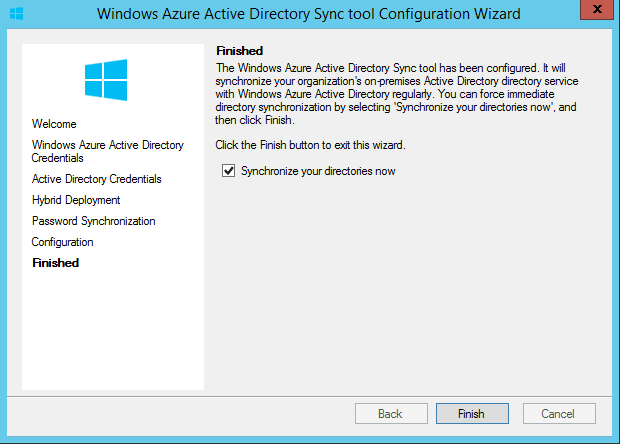
Once its completed, click next. Then it gives option to start the sync now. Click finish to start the sync.
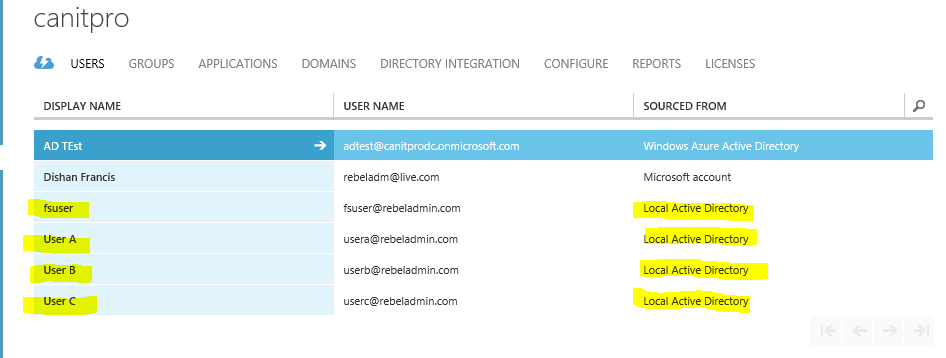
Once sync is done we can see azure AD updated with user accounts etc.
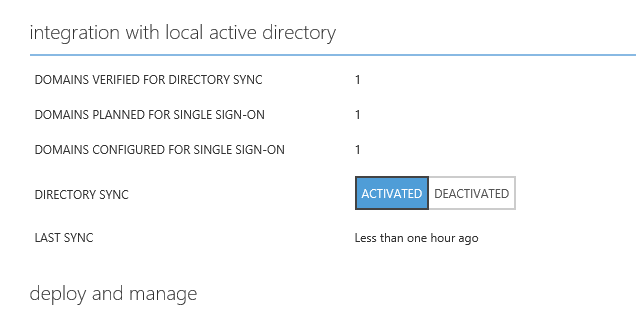
Also Directory integration page shows when was the last sync happens etc.
This ends the long article which were explaining the DirSync configuration with SSO.
If you have any question feel free to contact me on rebeladm@live.com
Image Source : https://msdn.microsoft.com/en-us/library/azure/dn441213.aspx




Thanks much
Thank you so much, clear and concise!!!
GREAT HELP!
THANKS !! EXACTLY WHAT I WAS LOOKING FOR..
Nice Article