In my previous blog post, I discussed what Entra ID Administrative Units are and how they can be implemented to limit the administrative scope of a role to a specific logical group. If you haven’t read it yet, I recommend checking it out before continuing with this article: https://www.rebeladmin.com/step-by-step-guide-entra-id-administrative-unit/.
In that post, I also presented a use case where an organization aims to restrict Helpdesk Administrator role privileges based on geographical areas.
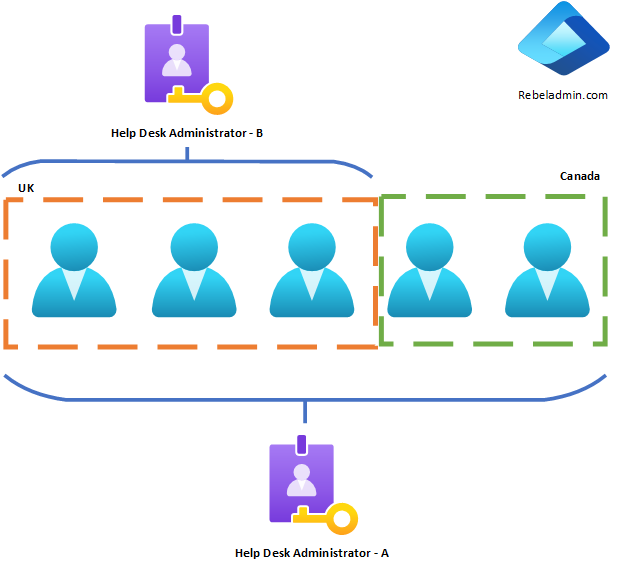
In the rebeladmin.com Entra ID tenant, users are divided into two geographical areas: the UK and Canada. Although it’s a single tenant, these regions have separate IT teams. If we assign the Helpdesk Administrator role to an IT administrator in the UK team, they would still be able to reset the password of a user in Canada, which violates the organization’s principle of least privilege. We can resolve this issue by using Entra ID Administrative Units. By creating separate administrative units for UK and Canada users, we can ensure that Helpdesk Administrators are restricted to managing only the users within their designated units.
However, this setup won’t stop Helpdesk Administrators with tenant-wide role privileges from modifying user accounts within these administrative units. For example, if Helpdesk Administrator A has the helpdesk role assigned at the tenant level, they can manage both UK and Canada user accounts without any restrictions. In some cases, there may be a need to prevent even tenant-level privileged accounts from modifying objects within specific administrative units. In the scenario above, due to operational and compliance requirements, UK users should not be managed by any tenant-level Helpdesk Administrator. We can achieve this by implementing a Restricted Management Administrative Units.
How Entra ID Restricted management administrative units works ?
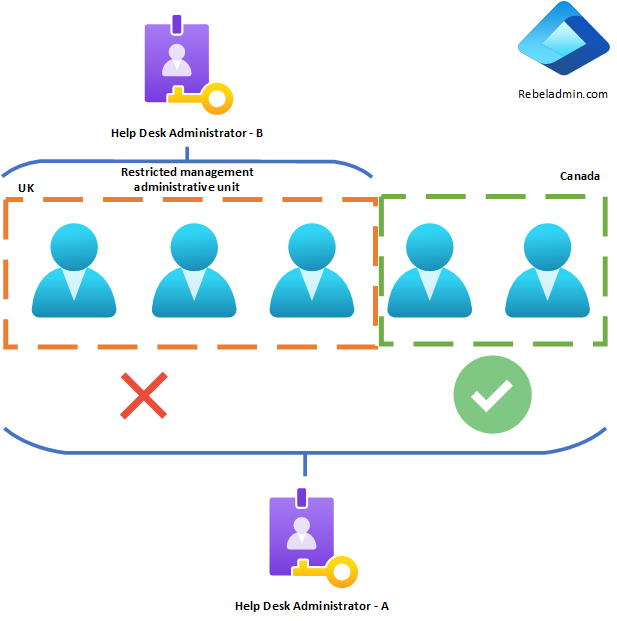
In the example above, by setting up a Restricted management administrative units for UK users, we can ensure that only the Helpdesk Administrators specifically assigned to that unit can modify user objects within its scope. This restriction applies to all other administrators, including Global Administrators, who will be unable to alter these user accounts unless they bring the account into their administrative scope.
Restricted management administrative units limitations
There are a few limitations to Restricted management administrative units (RMAUs):
- Only Users, Devices, and Security Groups can be included in an RMAU. M365 Groups, Distribution Groups, and Mail-Enabled Security Groups cannot be part of an RMAU.
- The RMAU setting must be enabled during the administrative unit’s creation process and cannot be changed afterward.
- Groups within an RMAU cannot be managed using Privileged Identity Management (PIM) or Microsoft Entra Entitlement Management. However, you can use Privileged Access Groups to assign admin roles without granting standing privileges. Learn more about Privileged Access Groups here.
- Only a limited number of built-in roles can be assigned to an Administrative Unit (refer to the previous blog post for more details). Custom roles can also be set up, but the administrative actions within the unit are restricted by the role’s permissions. For example, a Helpdesk Administrator can reset user passwords but cannot reset a Global Administrator’s password.
- When an RMAU is deleted, it may take up to 30 minutes for all related restrictions to be removed from its members.
Privileged Identity Management (PIM) for Groups and Restricted management administrative units
Privileged Identity Management (PIM) for groups is a super important feature in Microsoft Entra ID Governance. It helps organizations manage just-in-time membership and ownership of groups.
When users are added as eligible members of Privileged Access Groups (PAGs), it removes standing privilege, which boosts security by making sure elevated access is only granted when needed. This method allows for multiple roles to be assigned with a single PIM activation, making the process smoother and less complicated. However, it’s crucial that PGs are assigned to the RMAU role to keep the system’s integrity intact and ensure that only authorized changes are made by eligible members.

Another benefit of this approach is that PAG can be assigned in to multiple Restricted management administrative units roles.
In this demo, I’ll be using Privileged Access Groups with Restricted management administrative units to eliminate standing permissions. To create PAGs please follow my blog post https://www.rebeladmin.com/manage-privileged-access-groups-with-azure-ad-privileged-identity-management-azure-ad-pim/
Let’s dive into how we can use Restricted management administrative units. In this demo, I’ll replicate the setup explained earlier in the article and restrict UK user management to the UK help desk administrator. I already have a Privileged Access Group called ‘UK HelpDesk Admins,’ and the group’s membership will be managed using PIM.
Create RMAU
- Sign in to the Entra portal as a Privileged Role Administrator or higher.
- Navigate to Identity > Roles and admins > Admin units.
- Click on “+ Add” to open the wizard for creating Entra ID administrative unit.
- Provide a name and description for the RMAU. Then select Yes for Restricted management administrative unit. click “Next: Assign roles >“
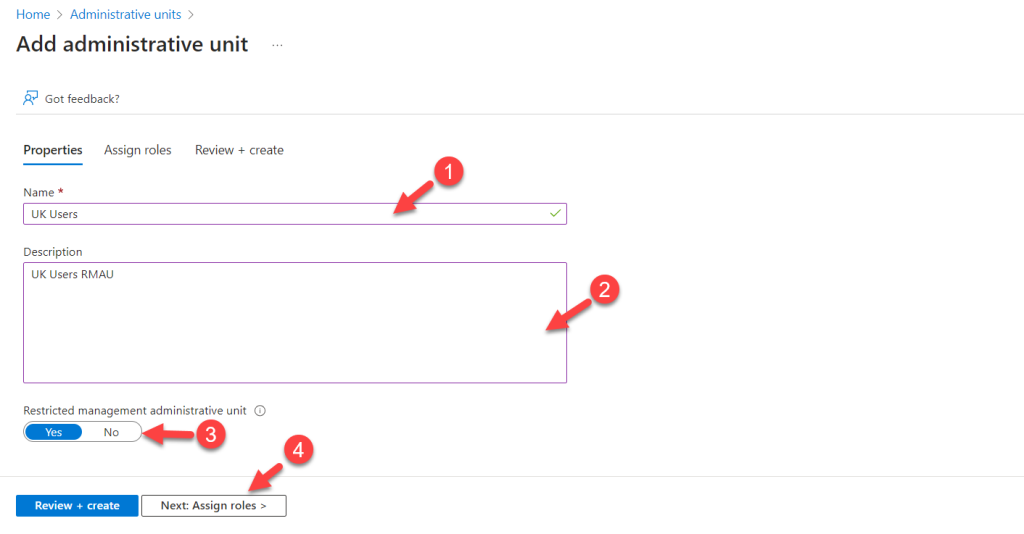
- On the next page, do not select Helpdesk Administrator as the role. I will add the Privileged Access Group to the role later. Click “Next: Review + create >” to continue.
- Review the settings on the next page and click “Create” to complete the administrative unit creation process.
- Once RMAU is created, we can see its now listed as RMAU in Administrative Units home page.
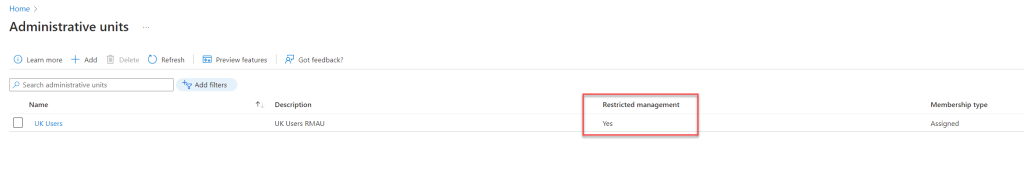
Add users to the Entra ID RMAU scope
The next step in the configuration is to add users to the RMAU. This process is the same as adding users to any Administrative Unit. I’ve explained this in detail in my previous blog post: https://www.rebeladmin.com/step-by-step-guide-entra-id-administrative-unit/. Please refer to the section titled “Add users to the Entra ID administrative unit scope” and follow the steps outlined there.
Assign Role to Entra RMAU
Once the users have been assigned to the scope, the next step is to assign the Helpdesk Administrator role to the RMAU. This process is also detailed in my previous blog post: https://www.rebeladmin.com/step-by-step-guide-entra-id-administrative-unit/. Please refer to the section titled “Assign Role to Entra ID Administrative Unit” for step-by-step instructions.
In this case, a Privileged Access Group (PAG) will be used with the role instead of assigning individual users. Once the role is assigned, you’ll notice that its scope is limited to the RMAU that was created earlier.
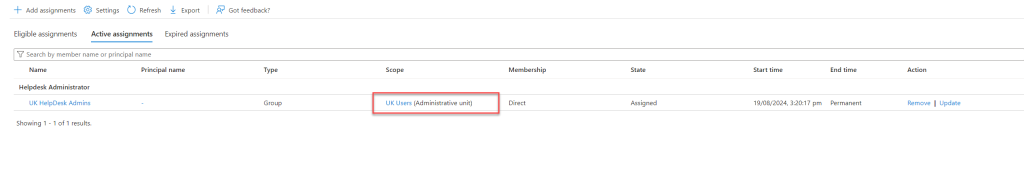
Testing
It’s time to test the configuration.
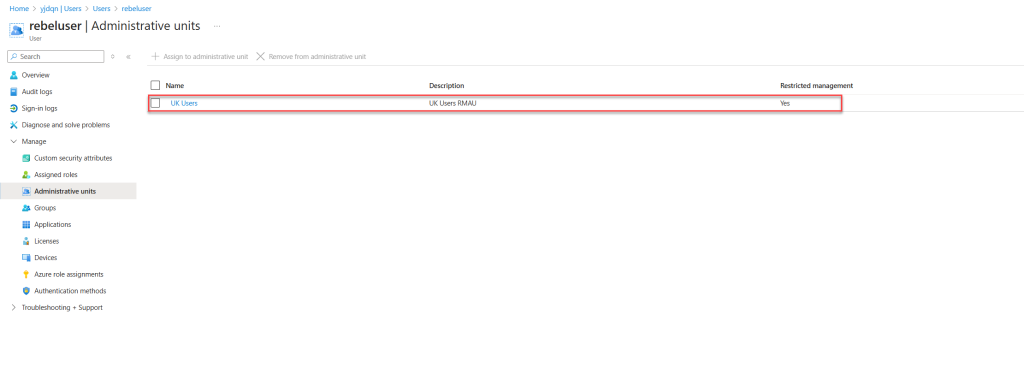
To do this, I’ll log in as a user who is an eligible member for the Help Desk Administrator role assigned to the UK Users administrative unit. Once logged in, I’ll select a user within the Entra ID Administrative Unit scope.
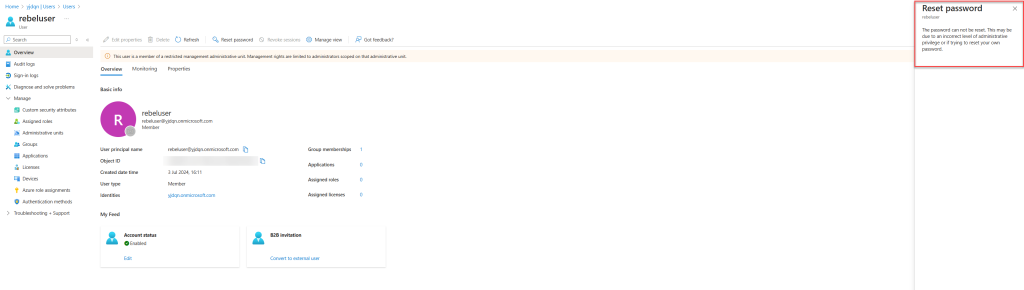
When I attempt to reset the password for this user, I receive an error. This is expected since the user doesn’t have the Help Desk Administrator permission yet.
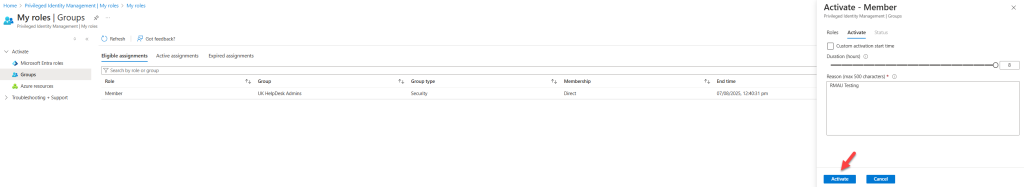
Next, I’ll activate membership for the UK HelpDesk Admins privileged access group using PIM. This will grant the Help Desk Administrator permission to the user.
After the membership is granted, I’ll try to reset the password for the same test user again. As expected, I can reset the password without any issues.
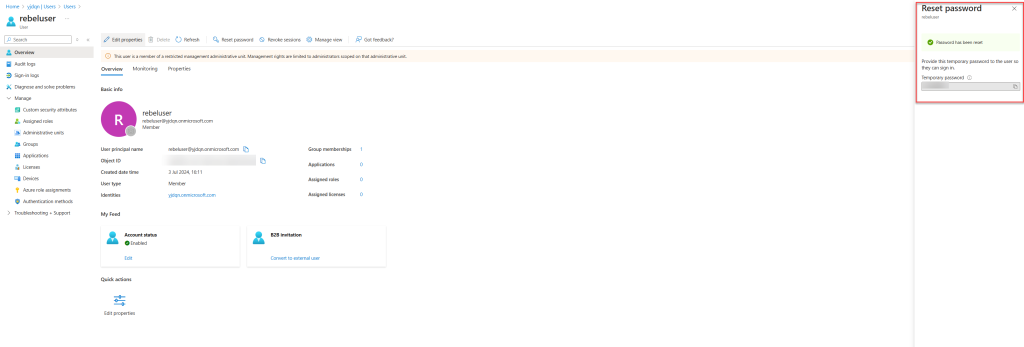
For the next test, I’ll attempt to reset the password for a user outside the Entra ID RMAU scope. This particular user is a global administrator. As expected, even though I have the Global Administrator role, I cannot reset the password for a user outside the RMAU scope.
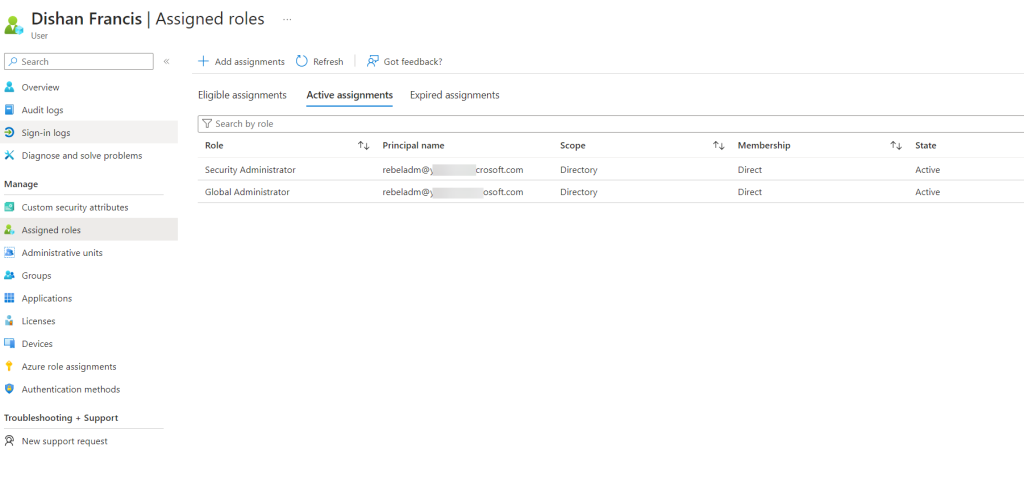
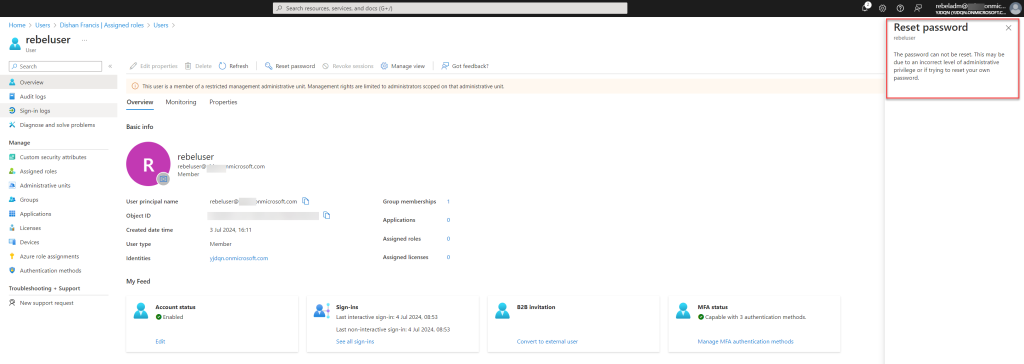
I hope this helps you gain a clearer understanding of how Entra ID Restricted Management Administrative Units operate. In the example above, no one outside the RMAU’s assigned administrative roles, not even a Global Administrator, can modify the objects within it. If you have any questions, feel free to reach out to me at rebeladm@live.com


