In one of my previous post I explained how we can manage AD administration privileges using ACLs. If you didn’t read it yet you can find it using http://www.rebeladmin.com/2018/02/step-step-guide-manage-active-directory-permissions-using-object-acls/
This Delegate Control method also works similar to ACLs, but its simplified the process as its uses,
• Delegation of Control Wizard which can use to apply delegated permissions.
• Allows to use predefined tasks and assign permission to those
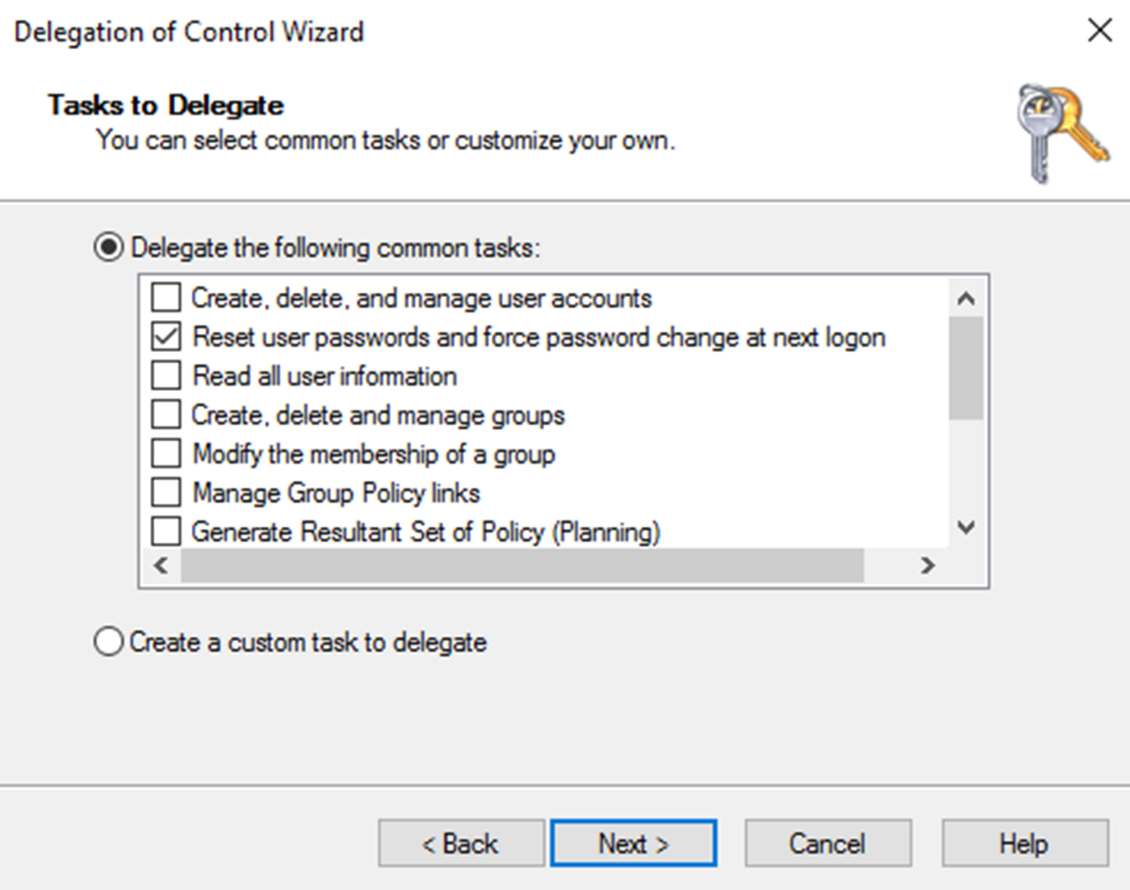
The Wizard contain following predefined tasks which can use to assign permissions.
• Create, delete, and manage user accounts
• Reset user passwords and force password change at next logon
• Read all user information
• Create, delete and manage groups
• Modify the membership of a group
• Manage Group Policy links
• Generate Resultant Set of Policy (Planning)
• Generate Resultant Set of Policy (Logging)
• Create, delete, and manage inetOrgPerson accounts
• Reset inetOrgPerson passwords and force password change at next logon
• Read all inetOrgPerson information
This also allows to create custom task to delegate permissions, if it’s not covered from the common task list.
Similar to ACLs, Permissions can apply in,
1) Site – Delegated permission will valid for all the objects under the given Active Directory Site.
2) Domain – Delegated permission will valid for all the objects under the given Active Directory Domain.
3) OU – Delegated permission will valid for all the objects under the given Active Directory OU.
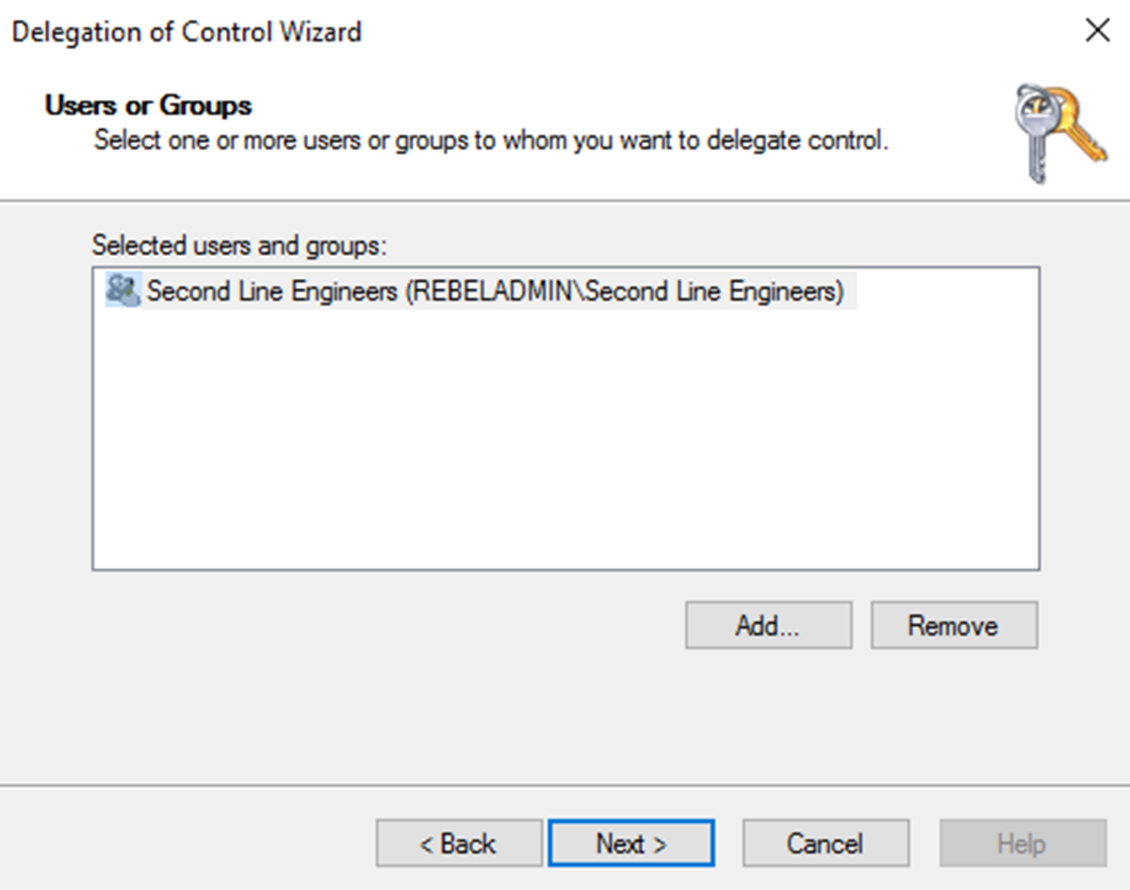
As an example, I have a security group called Second Line Engineers and Scott is a member of it. I like to allow members of this group to reset password for objects in OU=Users,OU=Europe,DC=rebeladmin,DC and nothing else.
1) Log in to Domain Controller as Domain Admin/Enterprise Admin
2) Review Group Membership Using
Get-ADGroupMember “Second Line Engineers”
3) Go to ADUC, right click on the Europe OU, then from list click on “Delegate Control”
4) This will open new wizard, in initial page click Next to proceed.
5) In next page, Click on Add button and add the Second Line Engineers group to it. Then click Next to proceed.
6) From the task to delegate window select Delegate the following common tasks option and from list select Reset user passwords and force password change at next logon. In this page, we can select multiple tasks. If none of those works, we still can create custom task to delegate. Once completes the selection, click next to proceed.
7) This completes the wizard and click on Finish to complete.
8) Now it’s time for testing. I log in to Windows 10 computer which has RSAT tools installed as user Scott.
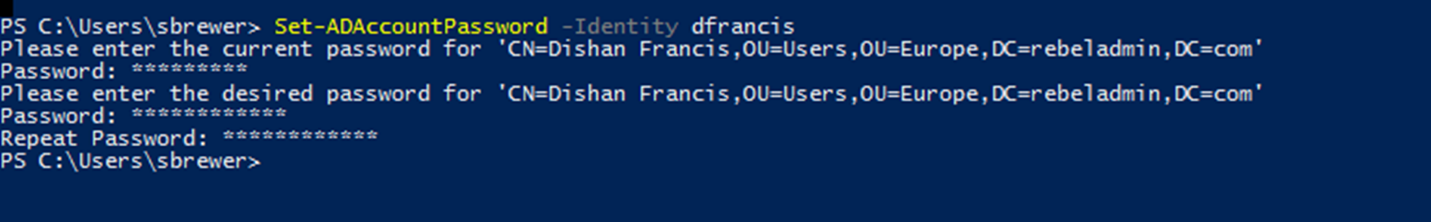
According to permissions, I should be able to reset password of an object under OU=Users,OU=Europe,DC=rebeladmin,DC
Set-ADAccountPassword -Identity dfrancis
This allows to change the password successfully.
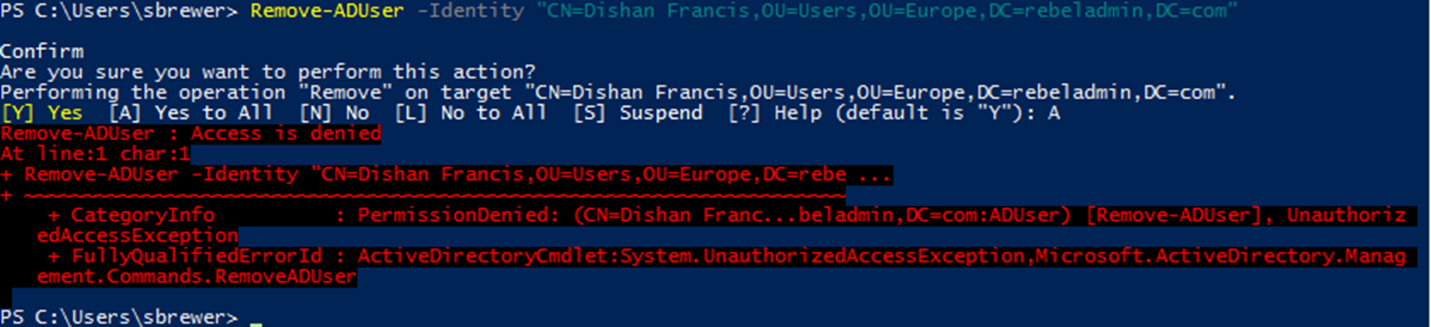
However, it should not allow to delete any objects. we can test it using,
Remove-ADUser -Identity "CN=Dishan Francis,OU=Users,OU=Europe,DC=rebeladmin,DC=com"
And as expected, it returns access denied error.
This marks the end of this blog post. If you have any questions feel free to contact me on rebeladm@live.com also follow me on twitter @rebeladm to get updates about new blog posts.