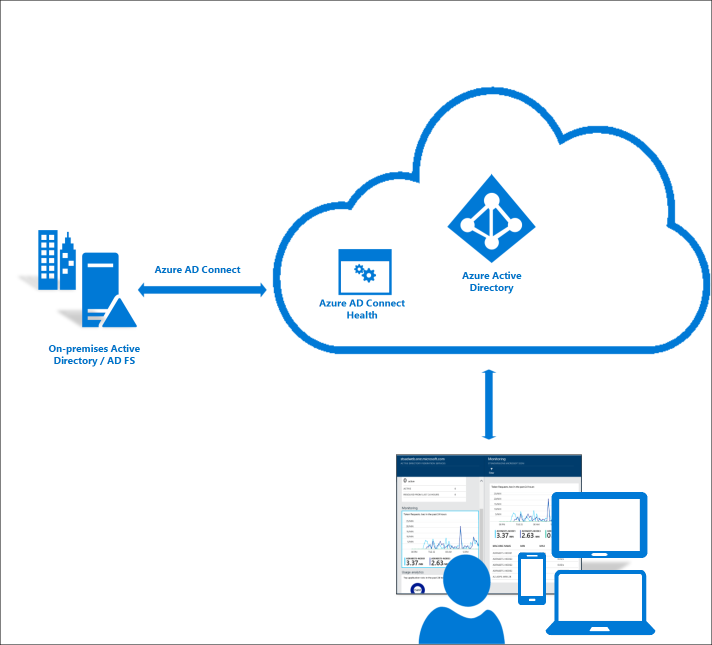
As system administrator, how you currently monitor your AD infrastructure? I am sure I will get lot different answers such as SCOM, Event viewer, Performance monitor, Third party application monitors etc. when the AD infrastructure expand, grow the effort and cost you need to put to monitor the AD infrastructure increase too. This is getting more complex if you using hybrid infrastructure. Integrating Azure AD with on-premises AD gives you reliable and productive identity platform for your cloud and on-premises resources. But same time it makes more important to maintain healthy on-premises AD infrastructure and sync service in order to achieve this goal.
Microsoft introduces “Azure AD Connect Health” to monitor your on-premises AD infrastructure. It will give opportunity to view alerts, performance, sync errors, configuration settings etc. Idea behind this is to build a central, cloud based approach to get more insight about the on-premises AD infrastructure.
Another feature of AD connect Health is the AD FS 2.0 & 3.0 support. This also can monitor the health of on-premises AD FS configuration.
According to Microsoft Azure AD connect health for sync provides following services,
• View and take action on alerts to ensure reliable synchronizations between your on-premises infrastructure and Azure Active Directory.
• Email notifications for critical alerts
• View performance data
Azure AD Connect Health for AD FS provides following services,
• View and take action on alerts for reliable access to AD FS protected applications including Azure AD
• Email notifications for critical alerts
• View performance data to determine capacity planning
• Detailed views of your AD FS login patterns to determine anomalies or establish baselines for capacity planning
Requirements
In order to use AD health connect service following requirements needs to fulfil,
1) Azure AD premium subscription
2) Azure AD connect health agent installed in target server (https://azure.microsoft.com/en-us/documentation/articles/active-directory-aadconnect-health-agent-install/)
3) If you monitoring AD FS, audit must be enabled (https://azure.microsoft.com/en-us/documentation/articles/active-directory-aadconnect-health-agent-install/#installing-the-azure-ad-connect-health-agent-for-ad-fs)
4) Outbound connectivity to following end points
new: https://management.azure.com
new: *.blob.core.windows.net
new: *.queue.core.windows.net
*.servicebus.windows.net – Port: 5671
https://*.adhybridhealth.azure.com/
https://*.table.core.windows.net/
https://policykeyservice.dc.ad.msft.net/
https://login.windows.net
https://login.microsoftonline.com
https://secure.aadcdn.microsoftonline-p.com
5) Following firewall ports needs to be open in any server running agent
TCP/UDP port 80
TCP/UDP port 443
TCP/UDP port 5671
So enough talking, let’s see how we can configure this service. For demo I am using on-premises AD server which is built on windows server 2016 TP4.
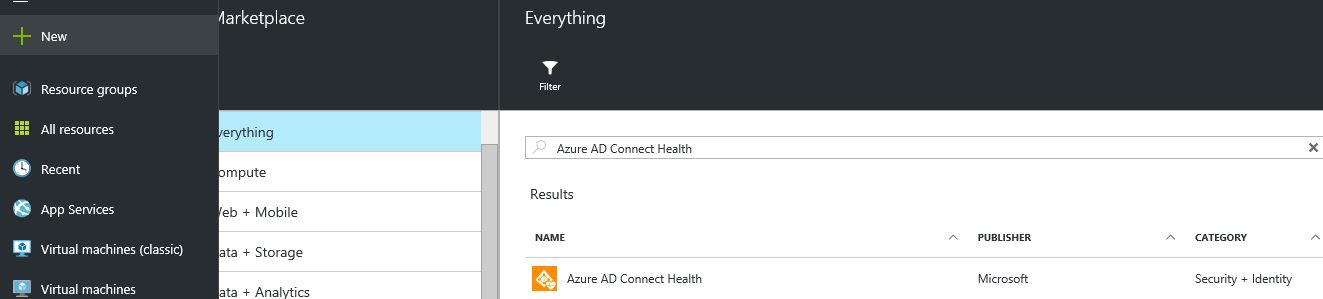
1) Log in to the Azure portal and search for “Azure AD Connect Health”
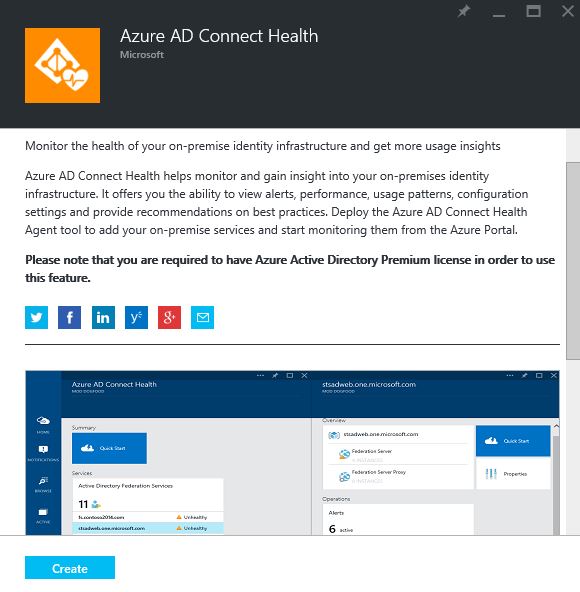
2) Select the service and in next window click on “Create”
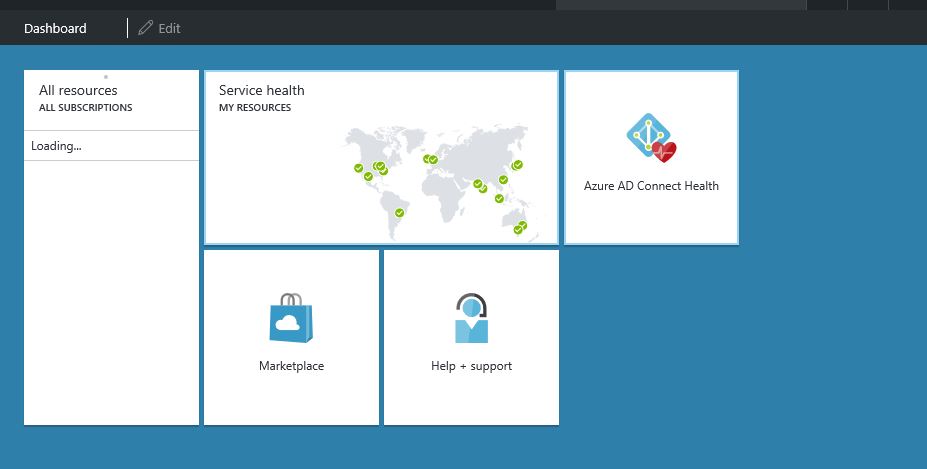
3) Once its created, it can see in portal dashboard
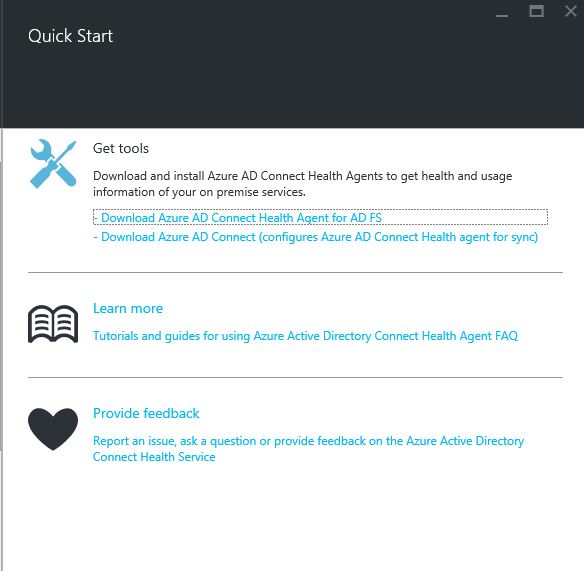
4) Then click on the shortcut to go to the detail service page. In here click on “Quick Start” button to start the process
5) In next window it give option to download the relevant agent. For the demo I need “Download Azure AD Connect (configures Azure AD Connect Health agent for sync)”
6) Once it’s downloaded to the target computer, double click it. ( you need to have required permissions on the target computer to do the installation)
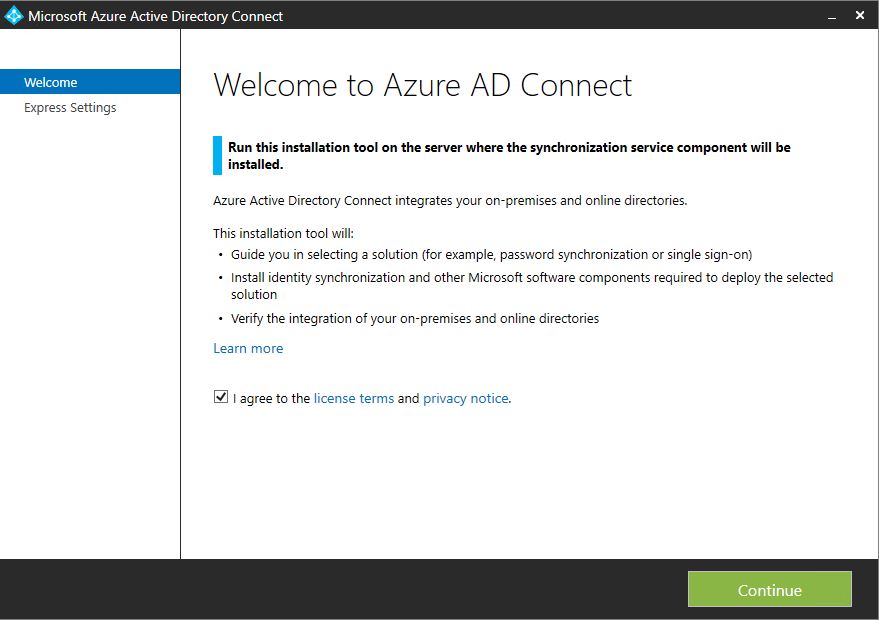
7) In the demo, the target server is do not have Azure AD connect configured. If you already had it, it is not necessary to do the agent install. Once installation is done, double click on the short cut for azure AD connect. Then in first window, accept the terms and click continue.
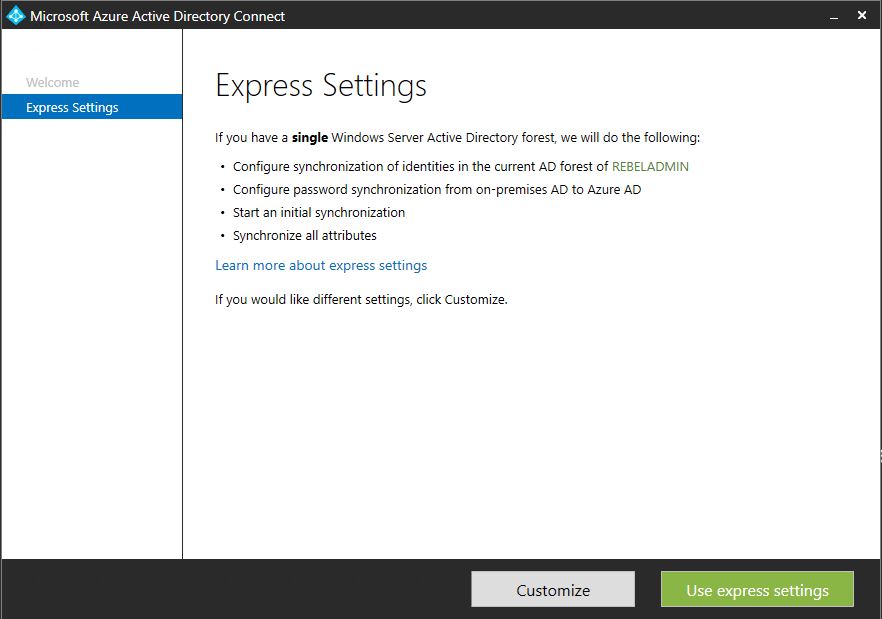
8) In next window, I will use express settings.
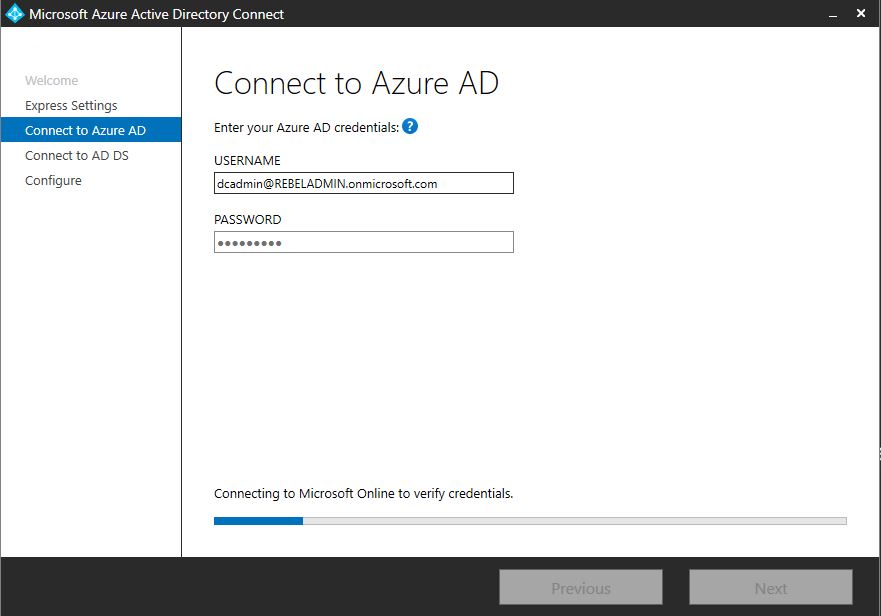
9) In next window, provide the Azure AD connect info
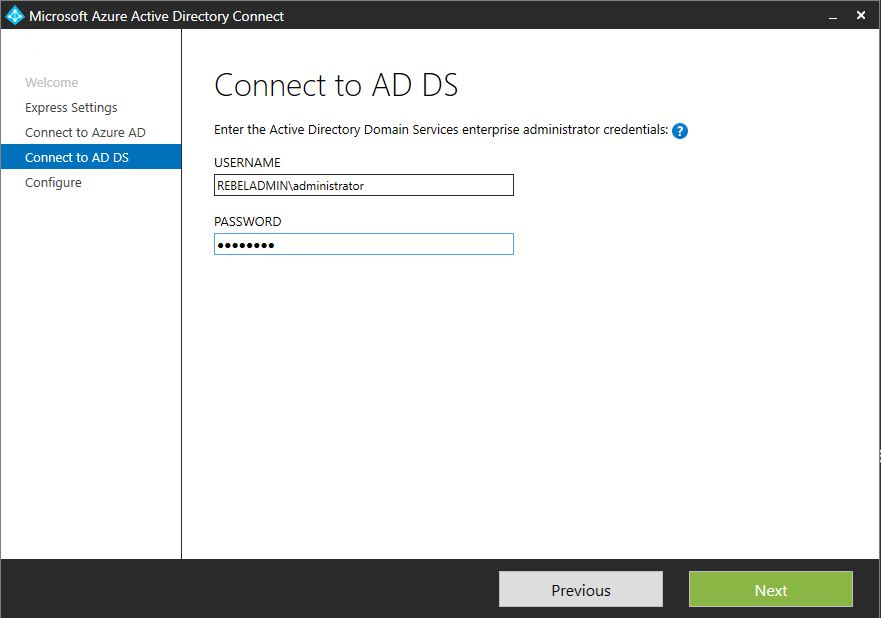
10) Then type the AD admin credentials and click next
11) Then in next window, click install to start the installation and synchronization
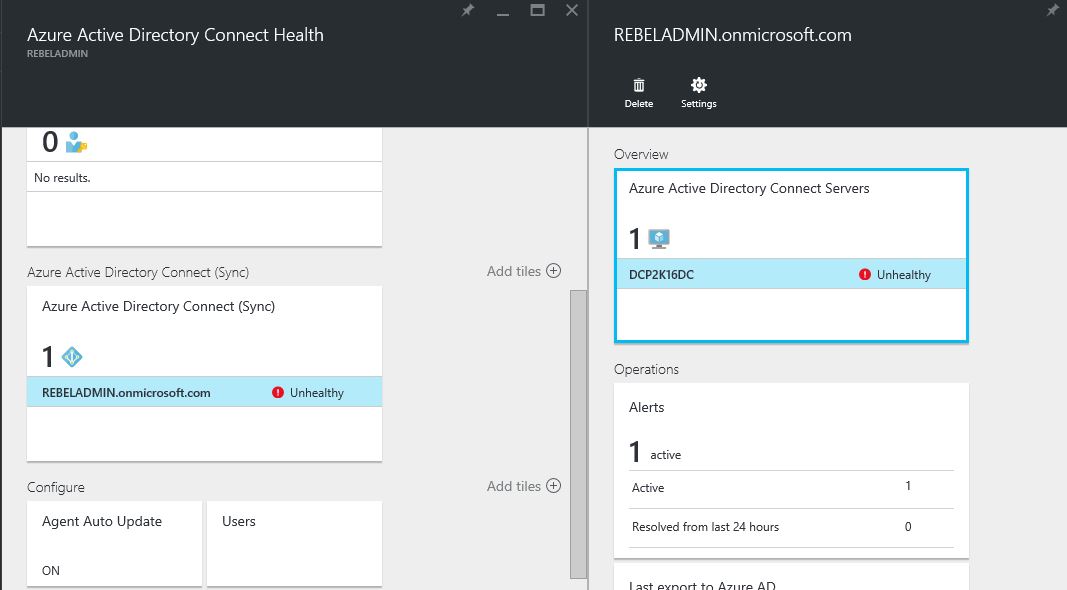
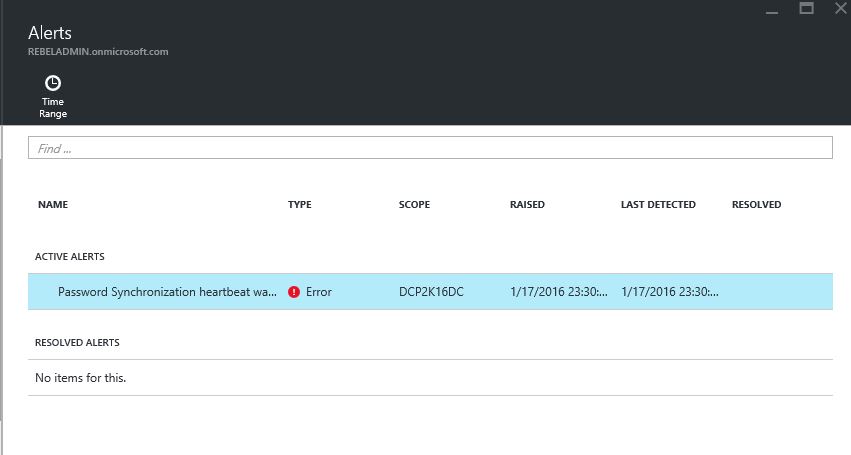
12) After the sync completes, log back in to the azure AD connect health and you can see the monitoring info.
if you have any question feel free to contact me on rebeladm@live.com
image source : https://acom.azurecomcdn.net/80C57D/cdn/mediahandler/docarticles/dpsmedia-prod/azure.microsoft.com/en-us/documentation/articles/active-directory-aadconnect-health/20151223054713/aadconnecthealth2.png