Why Windows LAPS Important ? As we know, every Windows machine, including domain-joined ones, comes with a built-in local administrator account. In addition to this default account, organizations often employ multiple local administrator accounts for various operational needs. Unfortunately, these local administrator accounts frequently have a shared password. While changing the password of a domain account is relatively straightforward and can be done from any domain controller, altering the password of a local account presents certain practical challenges, especially when managing a large number of devices.
Nevertheless, safeguarding these local administrator accounts is of utmost importance to prevent pass-the-hash attacks and limit lateral movements within the network. Microsoft has provided the Local Administrator Password Solution (LAPS) to manage local administrator accounts on domain-joined computers. Windows LAPS replaces the use of a common user account with a common password and ensures that an identical password is issued to every computer. The passwords for these local administrator accounts are securely stored in Active Directory.
Excitingly, Microsoft has recently announced Entra ID support for the Windows Local Administrator Password Solution. This means that we can now utilize Entra ID to store and recover the local administrator password for both Entra ID joined devices and hybrid Entra ID joined devices.
Currently, this feature is in the preview phase. It is accessible to all customers with Entra ID Free or higher licenses. However, please be aware that this feature is not supported for Entra ID registered devices.
Enabling this feature requires configuration on both the service side and the client side. There are two methods available to manage the client side configuration:
1) If the devices are already managed through Microsoft Endpoint Manager, we can utilize Windows LAPS policies for client side configuration.
2) If you are using group policies to manage the client side configuration, we can leverage group policies for the client side configuration.
In this blog post, I will demonstrate how to enable Windows LAPS with Entra ID and provide guidance on using group policies for managing the client side configuration.
Prerequisites
1) Devices must be Entra ID joined or hybrid Entra ID joined.
2) Required minimum of Cloud Device Administrator permission to enable Windows LAPS with Entra ID.
3) Required minimum of following Windows OS.
• Windows 11 22H2 – April 11 2023 Update
• Windows 11 21H2 – April 11 2023 Update
• Windows 10 20H2, 21H2 and 22H2 – April 11 2023 Update
• Windows Server 2022 – April 11 2023 Update
• Windows Server 2019 – April 11 2023 Update
4) Following roles can recover the password,
• Cloud Device Administrator
• Intune Administrator
• Global Administrator
5) If it is custom role, it must have microsoft.directory/deviceLocalCredentials/password/read permission to recover password.
6) Local Administrator account in computers – If you are using custom local administrator account make sure to setup it in all the targeted computers. Windows LAPS will not create local administrator accounts.
After ensuring that all the prerequisites have been met, the next step is to enable the Windows LAPS feature.
Enable Local Administrator Password Solution (LAPS)
To enable LAPS,
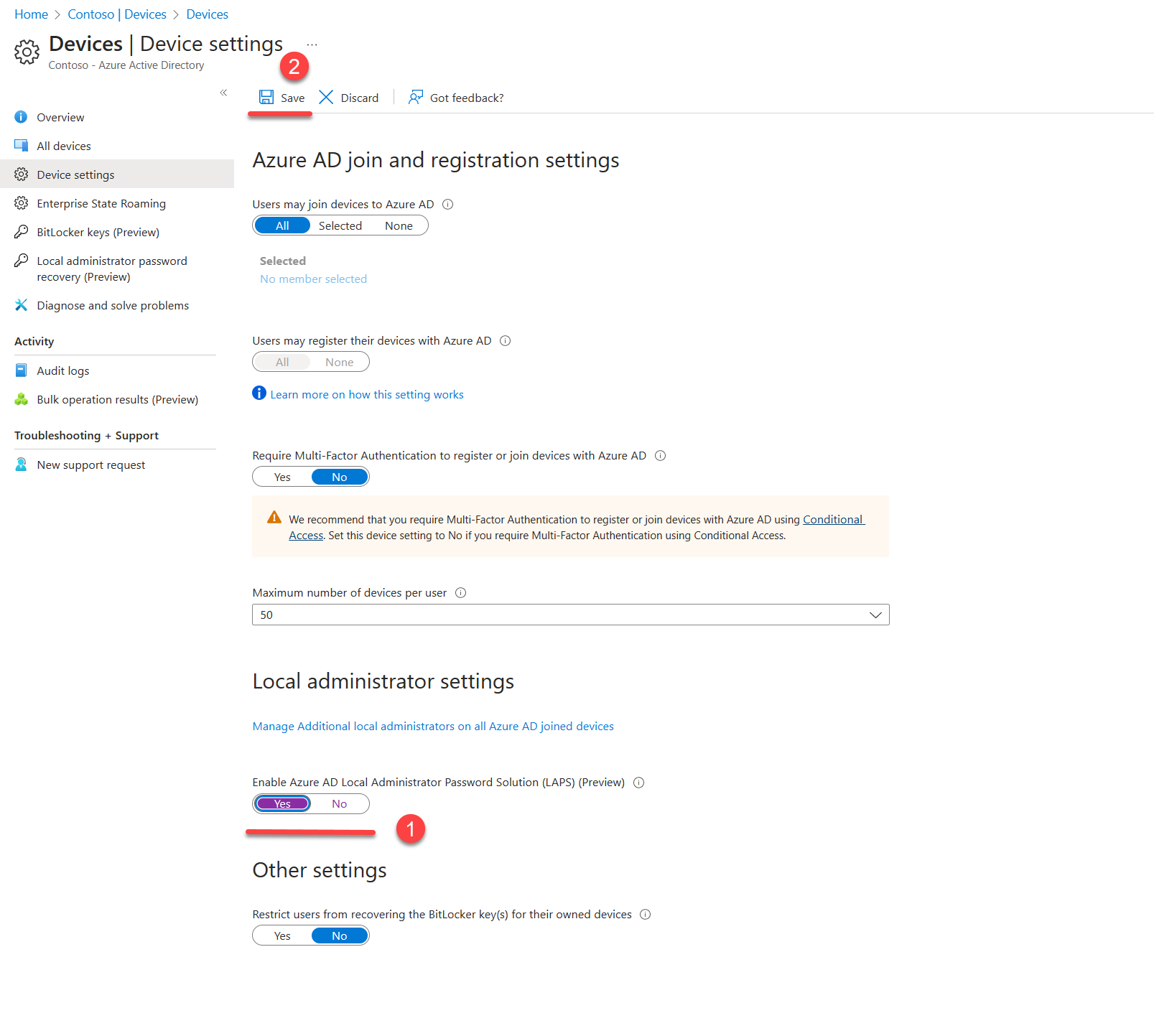
1) Log in to Azure portal as Cloud Device Administrator (or higher).
2) Go to Azure Active Directory | Devices | Device settings
3) In settings page, click Yes for the Enable Local Administrator Password Solution (LAPS) (Preview) setting and then click Save.
This completes the service side configuration. Next step of the configuration is to setup Group Policy to configure client side settings.
Configure Windows LAPS Group Policy
There are multiple ways to manage Windows LAPS settings. But in here we are going to use the new Group Policy Object which installed as part of Windows at %windir%\PolicyDefinitions\LAPS.admx
To configure group policy,
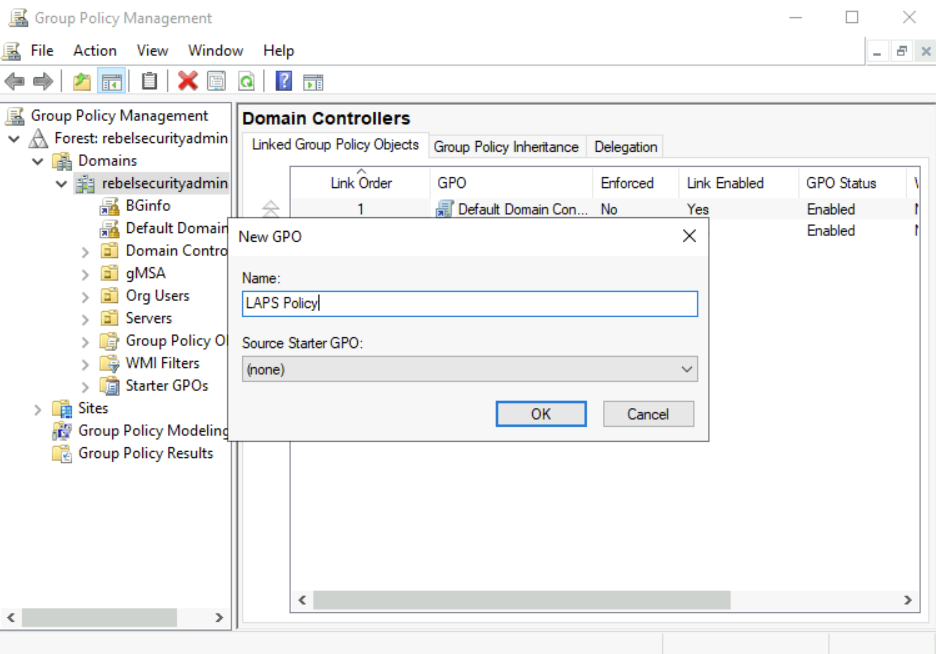
1) Open Group policy Management Editor
2) Create New Group Policy Object
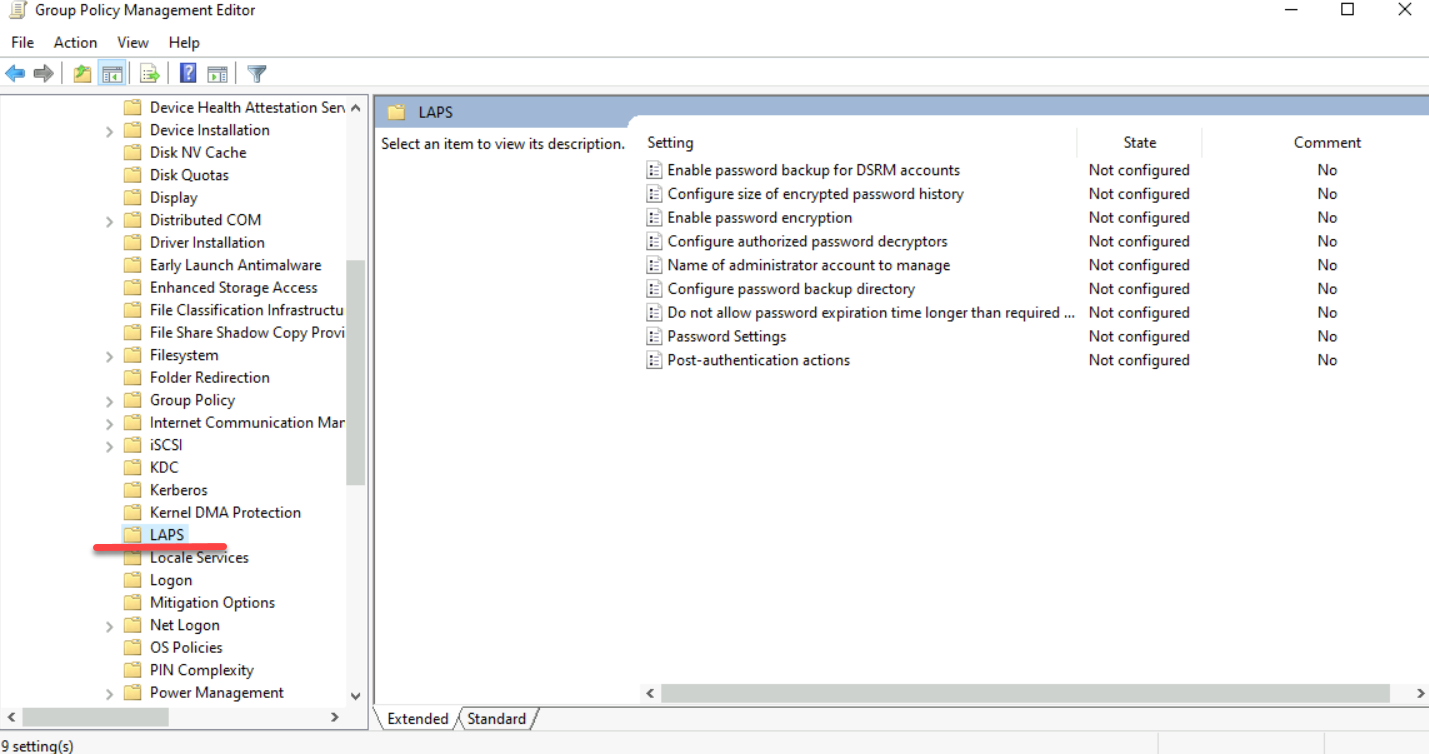
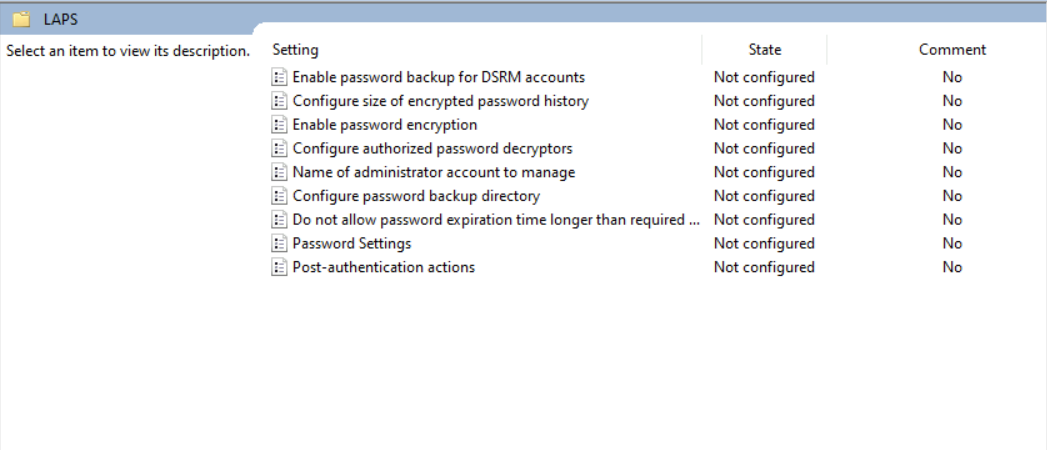
3) Then go to Computer Configuration | Policies | Administrative Templates | System | LAPS
4) Within the policy settings, there are several options available. However, it is important to note that when selecting the option to back up the password to Azure Active Directory, only a subset of these settings are applicable. More info about this is available on Configure policy settings for Windows LAPS | Microsoft Learn
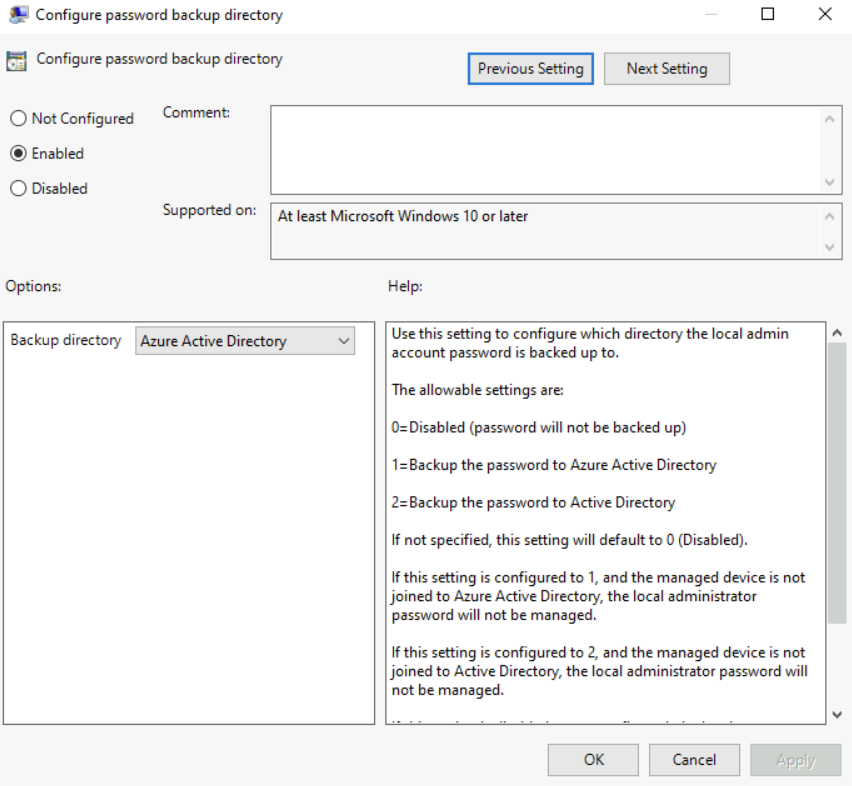
Configure password backup directory
Use this setting to configure which directory the local admin account password is backed up to.
The accepted settings are,
0– Disabled
1– Backup the password to Azure Active Directory
2– Backup the password to Active Directory
In this demo we will be setting this policy setting to 1.
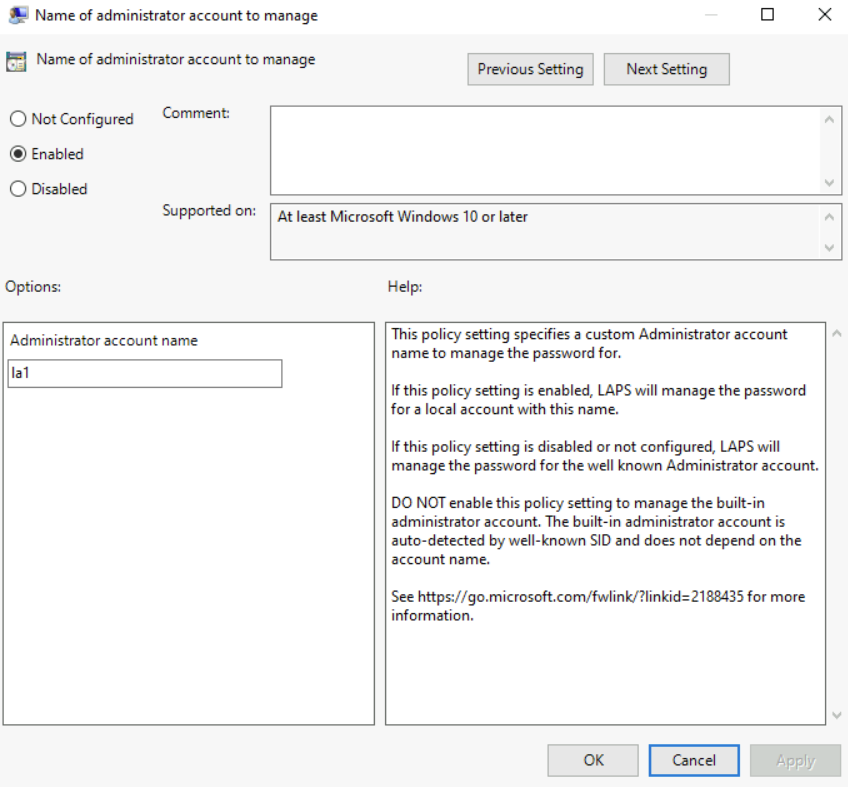
Name of administrator account to manage
By utilizing this policy setting, we have the ability to specify the name of the custom administrative account that LAPS should manage. If this policy setting is left unspecified, Windows LAPS will manage the password for the default local administrative account.
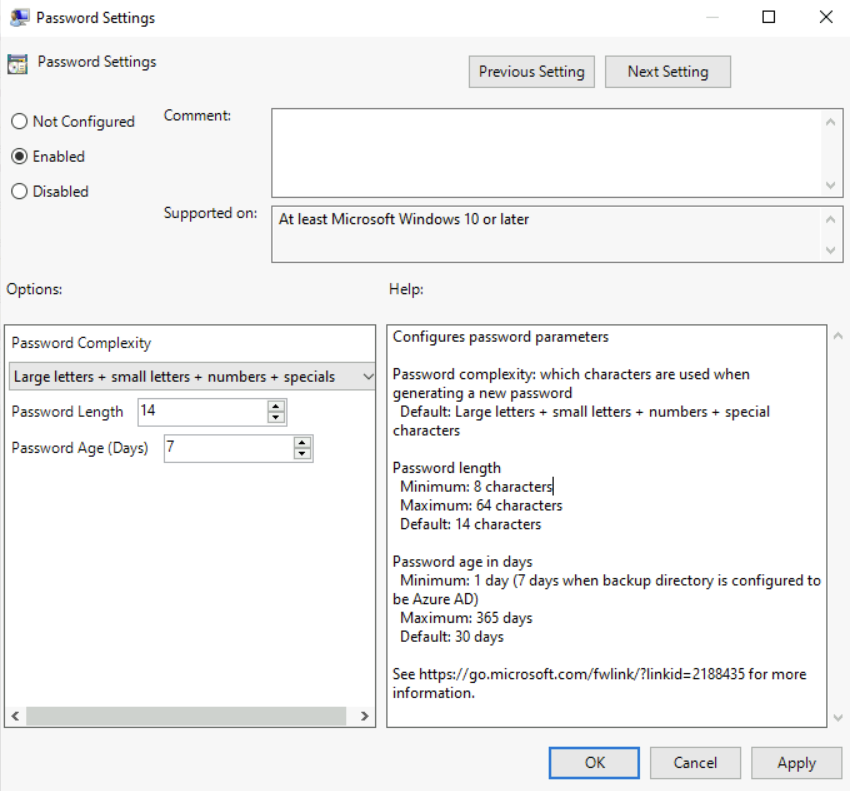
Password settings
Using this policy setting we can define following for the local administrator account.
• Password complexity requirements
• Password length
• Password age
Please note if the Entra ID used as backup directory the minimum password age should be 7 days. If its set to less than 7, the minimum value of 7 will be used anyway.
Post authentication actions
This policy configures post-authentication actions which will be executed after detecting an authentication by the managed account.
Grace period (hours) in this setting specifies the amount of time (in hours) to wait after an authentication before executing the specified post-authentication actions.
The following post-authentication actions can be used with the setting.
• Reset password
• Reset password and sign out
• Reset password and reboot
5) In this demo setup I have configured the following,
Configure password backup directory
Name of administrator account to manage
In this demo environment I am using a local administrator called la1
Password settings
6) One policy settings are in place, apply the policy to the targeted devices.
Testing
Once the policy is in place, the device will run it in every hour. If you want to forcefully process the policy you can run following command from the device.
Invoke-LapsPolicyProcessing
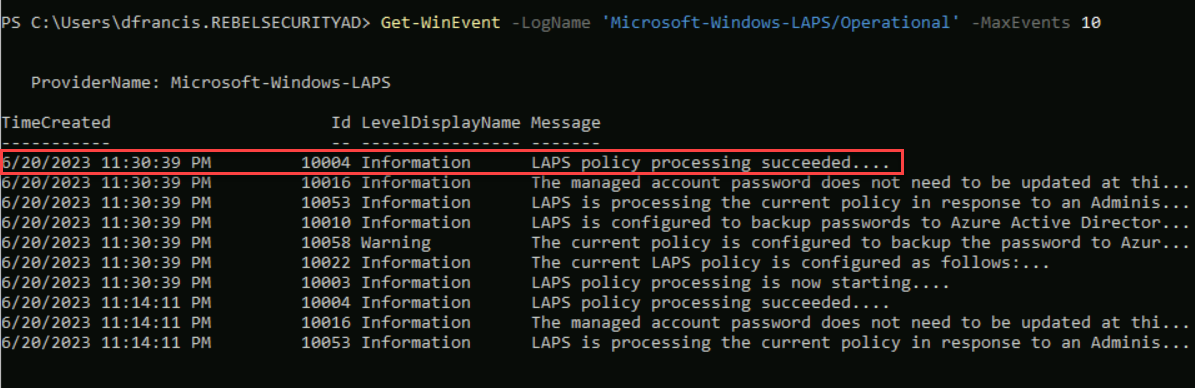
This will process the policy and we can confirm it by listing the LAPS events.
Get-WinEvent -LogName ‘Microsoft-Windows-LAPS/Operational’ -MaxEvents 10
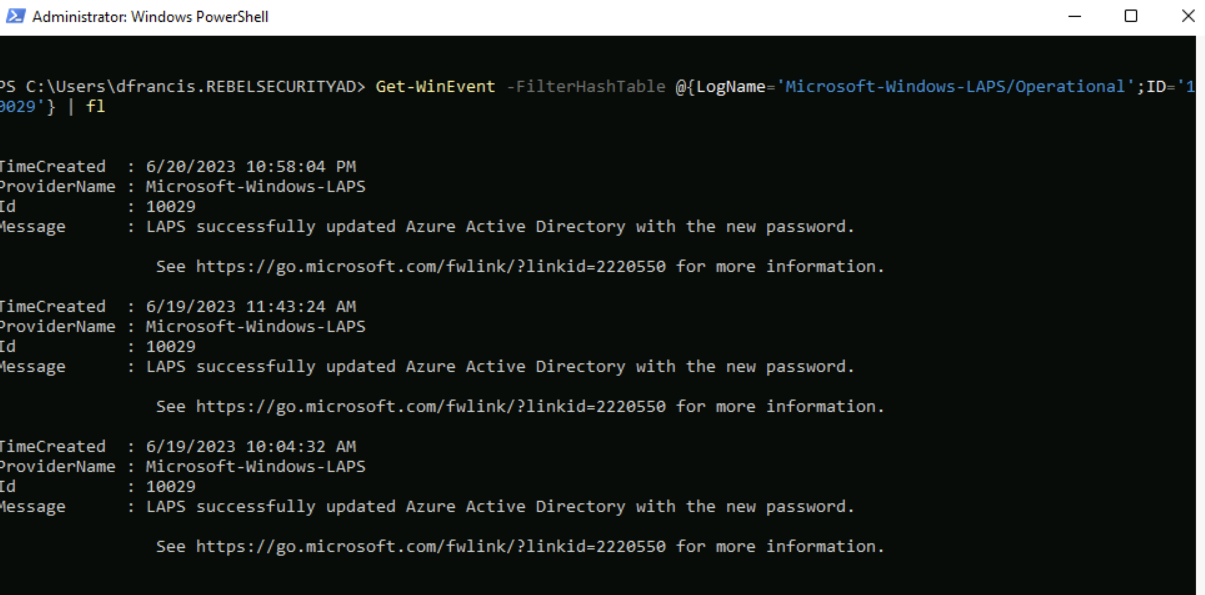
If the policy updated administrator account, the event will be recorded in log with id ‘10029’.
We can check it using following PowerShell command.
Get-WinEvent -FilterHashTable @{LogName=’Microsoft-Windows-LAPS/Operational’;ID=’10029′} | fl
As we can see the administrator account is updated. There are many methods to recover the password but in this demo I am going to use Azure portal for that.
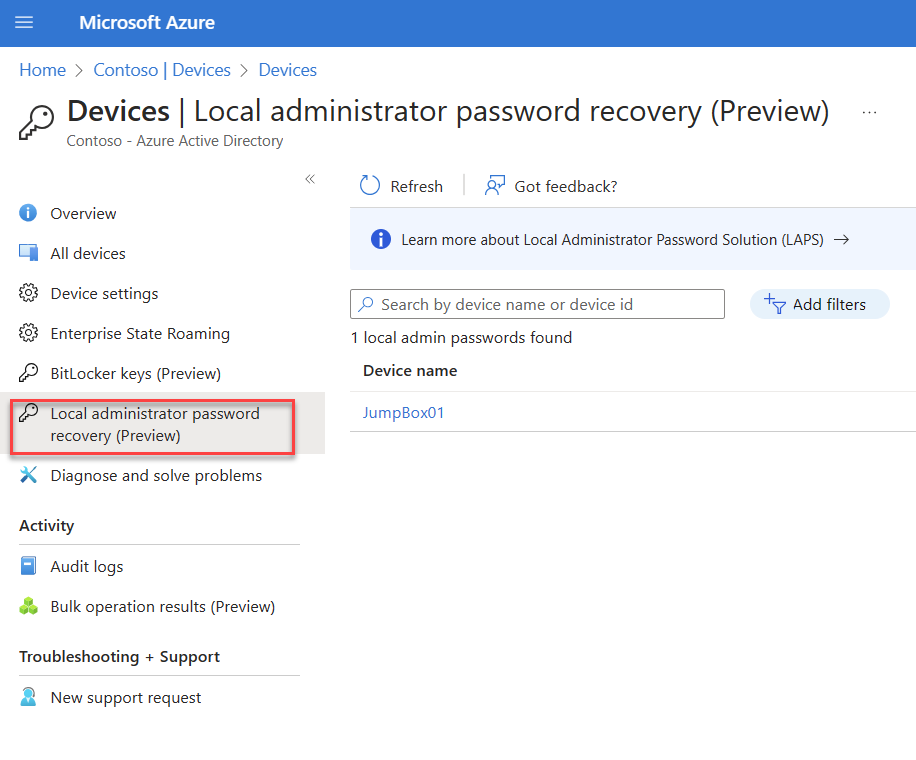
1) Log in to Azure Portal as a user who has permission to recover passwords (This was explained in prerequisites section)
2) Go to Azure Active Directory | Devices | Local administrator password recovery (Preview)
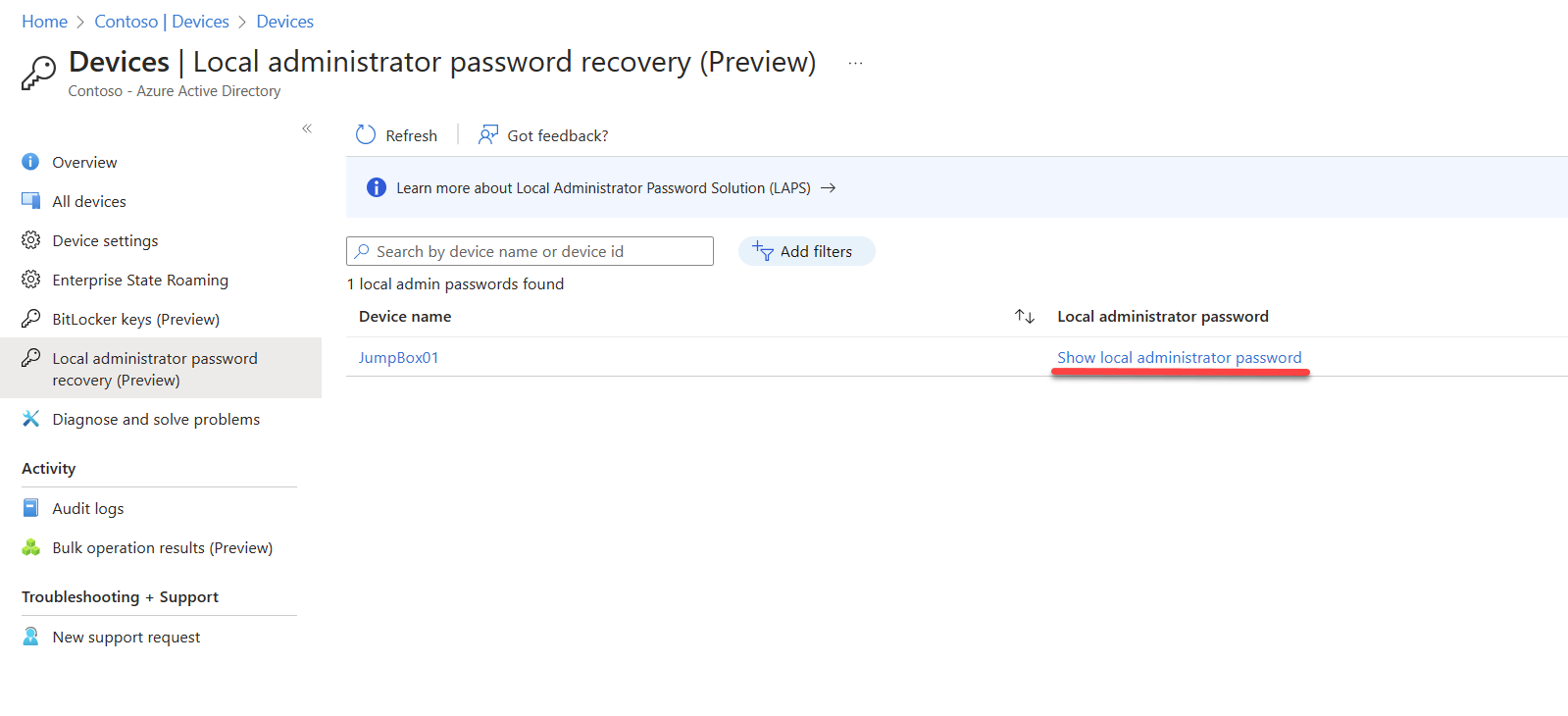
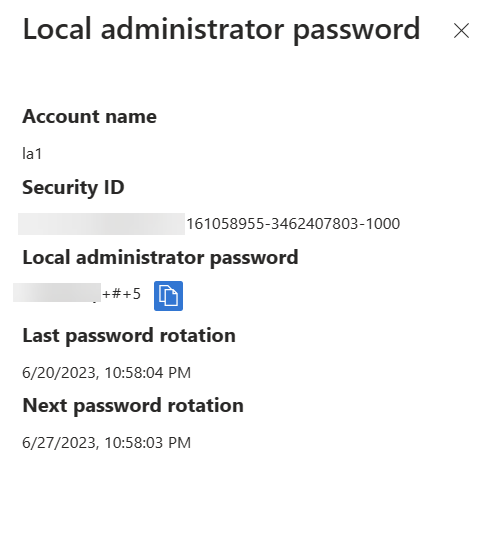
3) In the list search for the relevant device and then click on Show local administrator password
4) Upon execution, the action will prompt the password window to appear, presenting the password details, including the previous update timestamp and the next scheduled update.
As we can see the Windows LAPS with Entra ID is working as expected. This marks the end of the blog post and if you have any question feel free to reach me at rebeladm@live.com