In my previous blog post, I explained how to use Entra ID lifecycle workflow to trigger actions based on user attribute changes. You can find the step-by-step guide here: Configure Entra ID lifecycle workflow to trigger mover task on user profile changes. In that post, I used an attribute assigned to a set of users to define the workflow scope. Now, we can also use Custom Security Attributes values of users to further customise the workflow scope.
Custom Security Attributes
In Microsoft Entra ID, Custom Security attributes are used to store information, group objects, or provide fine-grained access control to Azure resources. These attributes can be used not only with cloud-only users but also with directory-synced users from on-premises Active Directory. To add a custom security attribute to Entra ID users, follow the guide on adding or deactivating custom security attribute definitions in Microsoft Entra ID.
Use Case
In this demo I am trying to cover the following use case. I already has an Entra ID lifecycle workflow for Rebeladmin Engineering Team. In their workflow scope is based on department attribute value.
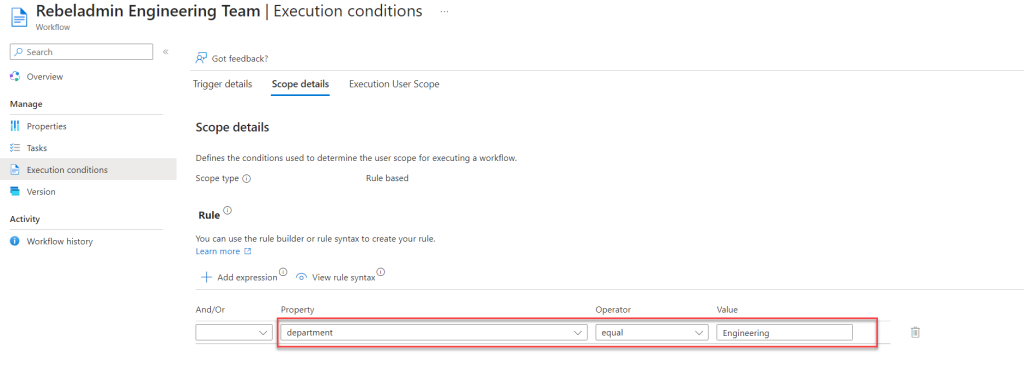
I am going to extend this further by using a Custom Security Attribute to filter users who are in the engineering department and also part of the Project A engineering team. To achieve this, I will use the ProjectA custom attributes set and the ProjectTeam Custom Security Attribute that I have already set up.
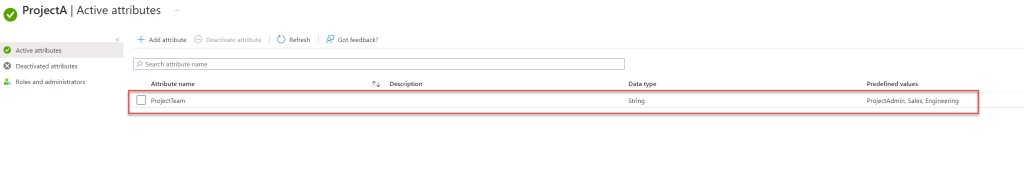
Prerequisites
- To create or modify an Entra ID lifecycle workflow, you need the Lifecycle Workflow Administrator role.
- To view or use Custom Security attributes values, you need the Attribute Assignment Administrator role, which is not assigned to Global Administrators by default.
- Existing Entra ID lifecycle workflow – Custom Security attributes can be used to further customise the user scope. However, they cannot be used as the primary attribute for the workflow scope. A Lifecycle workflow cannot rely solely on a Custom Security attribute value; it must be used in conjunction with another primary attribute value. For example, in my demo, I will use a workflow lifecycle that already uses the department attribute value to scope users.
Configuration
Let’s go ahead and see how we can configure the Entra ID lifecycle workflow to use Custom Security Attributes
- Log into the Entra ID portal at https://entra.microsoft.com/ with the roles of Lifecycle Workflow Administrator and Attribute Assignment Administrator.
- Navigate to Identity Governance > Lifecycle Workflows.
- Open the Entra ID Lifecycle Workflow by selecting it to access its properties.
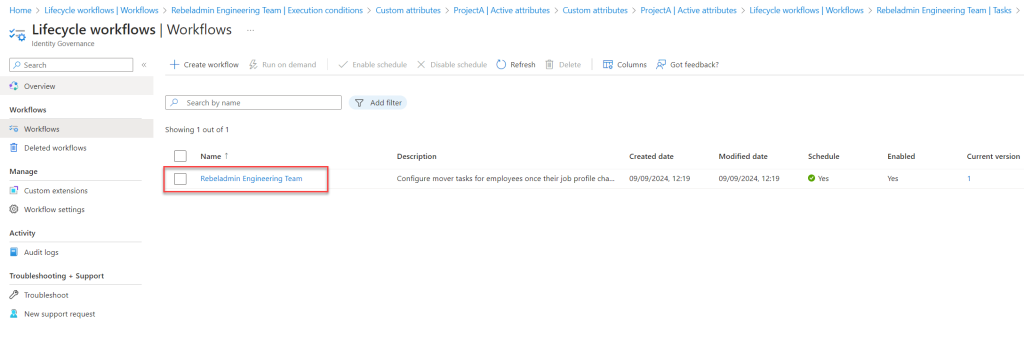
- Go to Execution Conditions and select Scope Details.
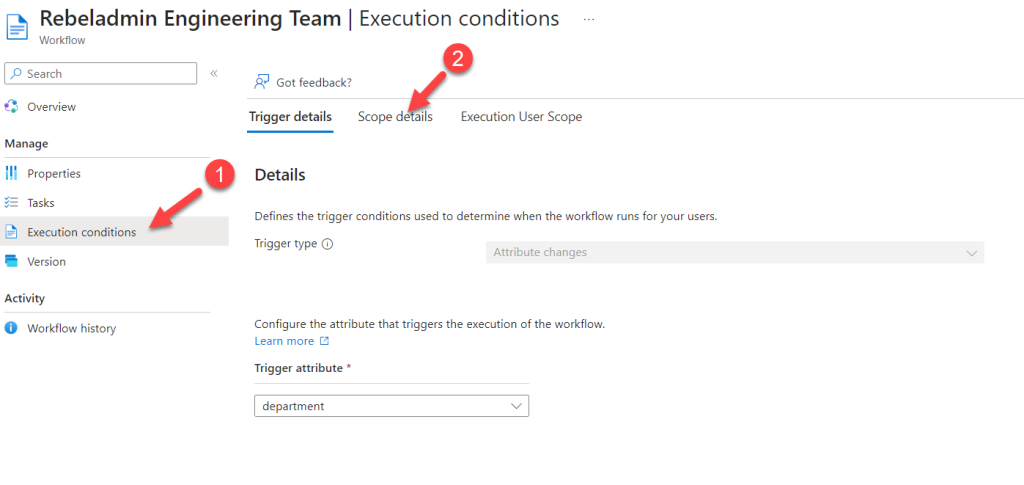
- Click on + Add Expression.
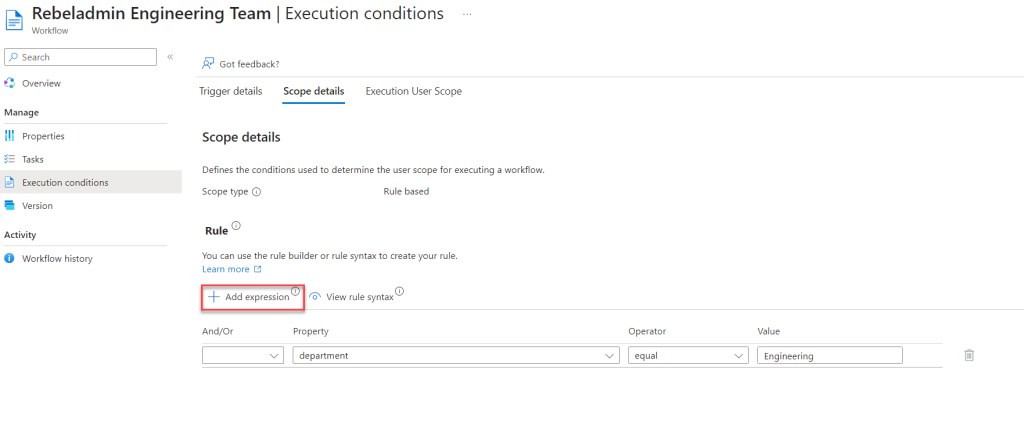
- From the list, choose the Custom Security Attribute value. For this demo, it’s set to customSecurityAttributes/ProjectA/ProjectTeam.
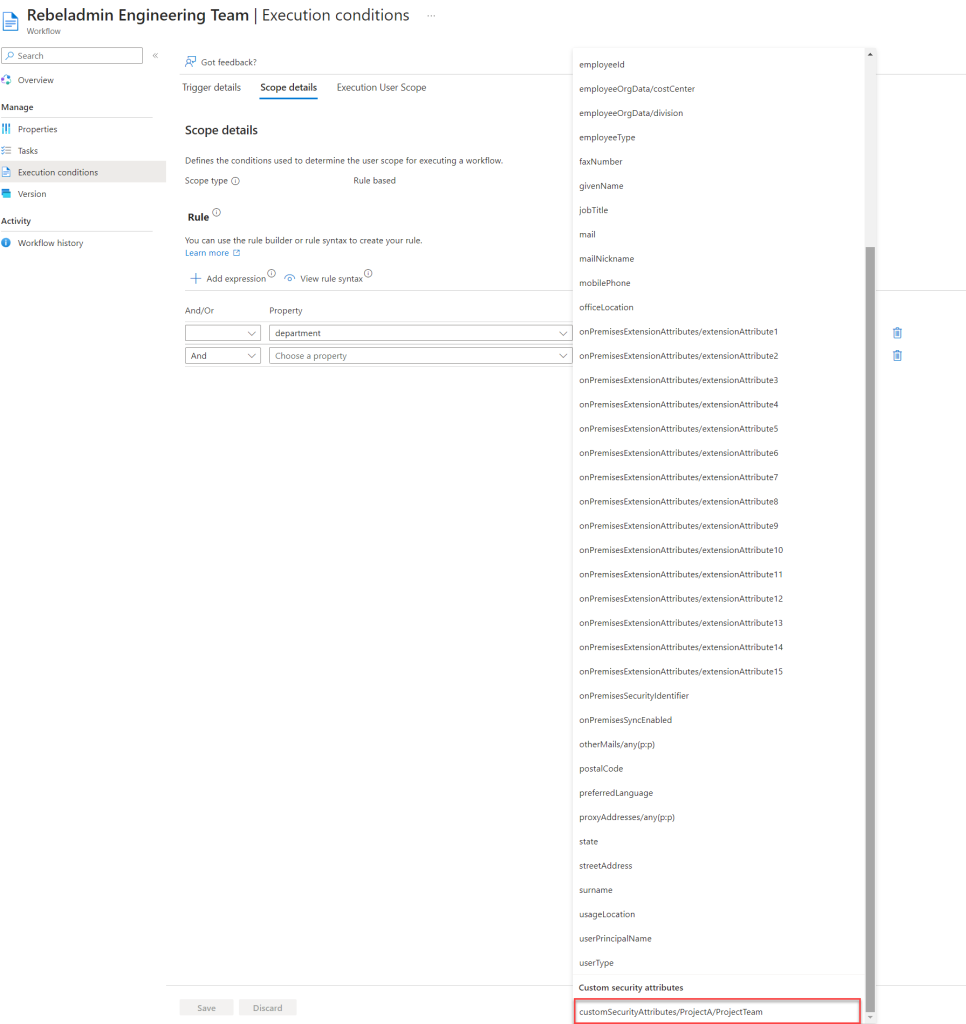
- Set the value according to your requirements. In this example, we’re targeting users in the Project A Engineering team.
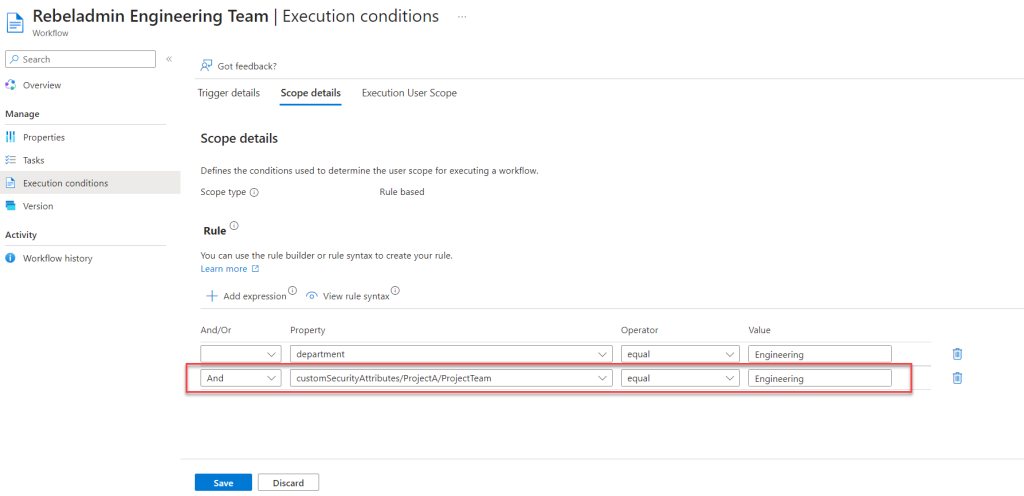
- Click Save to apply your changes.
Testing
The Entra ID Lifecycle Workflow is now configured to use Custom Security Attributes. Let’s see it in action:
- I have a user with the Custom Security Attributes value assigned as defined in the workflow.
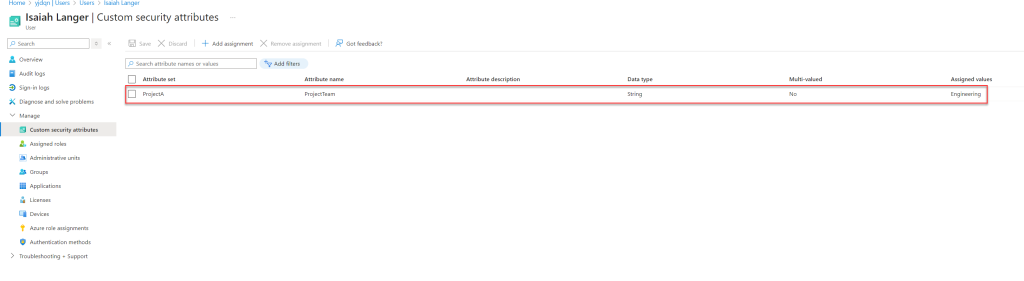
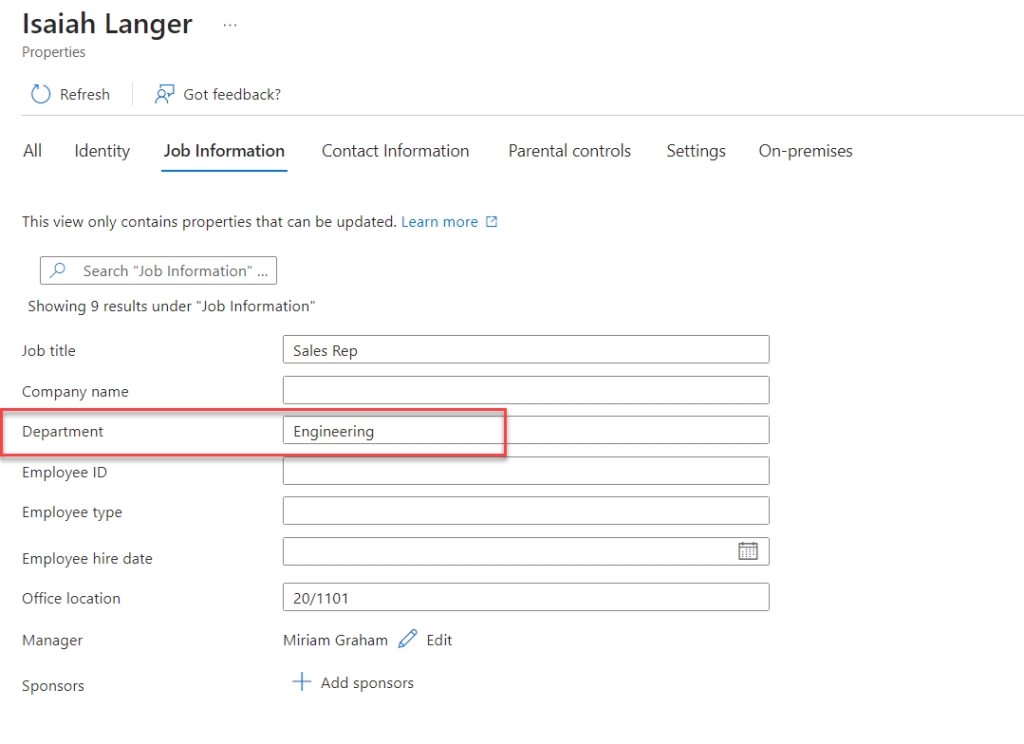
- This user is also a member of the Engineering department.
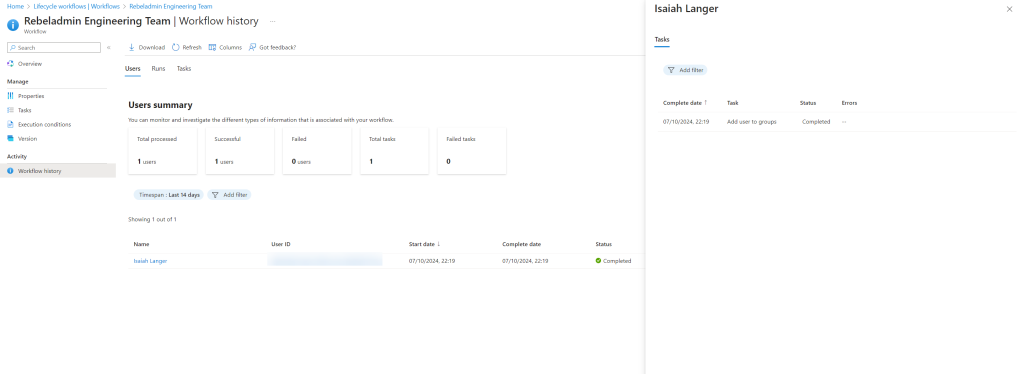
Once the workflow is processed, let’s go to Lifecycle Workflows and select the workflow we modified. Under Workflow History, we can verify that the user has been successfully added to the group.
I hope you now have a better understanding of how to use Entra ID Lifecycle Workflow with custom security attributes. If you have any questions, feel free to contact me at rebeladm@live.com.


