What is Advanced Security Audit ? More than any other system active directory in an organization important in security perspective. Even a small change in Organization’s AD can cause a major business impact. Preventing any unauthorized access, unplanned change in AD environment should prevent in first place but if similar thing happened in your AD environment you should have enough information to answer questions such as what has changed?, when it happened and who did it ?
As you know the computer security threats are changing every day, sometime the default event logs may not help to answer above questions. Microsoft understand these modern requirements and with windows 2008 R2 they introduce “Advanced Security Audit Policy”. This give you 53 options to tune up the auditing requirement and you can collect more in granular level information about your infrastructure events. It is have 10 categories and in this demo I am going to talk about the “DS Access” category which is focused on Active Directory Access and Object Modifications.
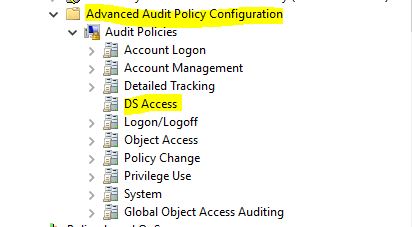
Configure Advanced Security Audit Policy
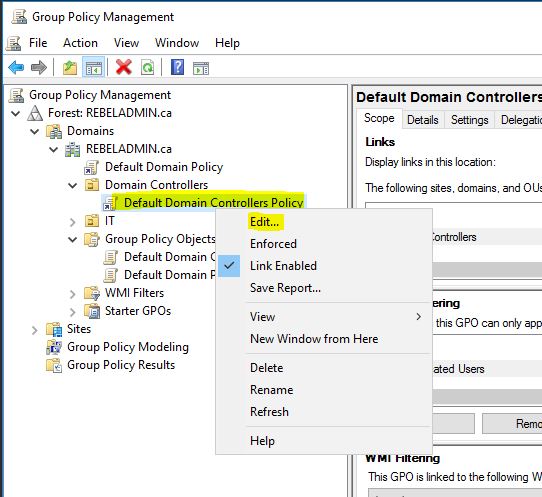
Advanced Security Audit Policy is need to enable via GPO. These events happens records on Domain controllers. There for the policy should only target the Domain Controllers. This can enabled on “Default Domain Controllers Policy” in AD.
In my Demo I am using AD server with Windows 2016 TP4.
1) Log in to the Server as Domain Admin
2) Load Group policy management editor using Server Manager > Tools > Group Policy Management
3) Expand the Domain Controllers OU, then right click on Default Domain Controllers Policy and edit.
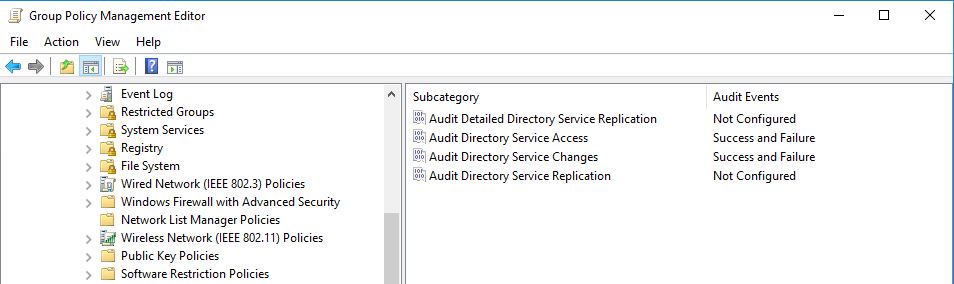
4) Go to Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies > DS Access
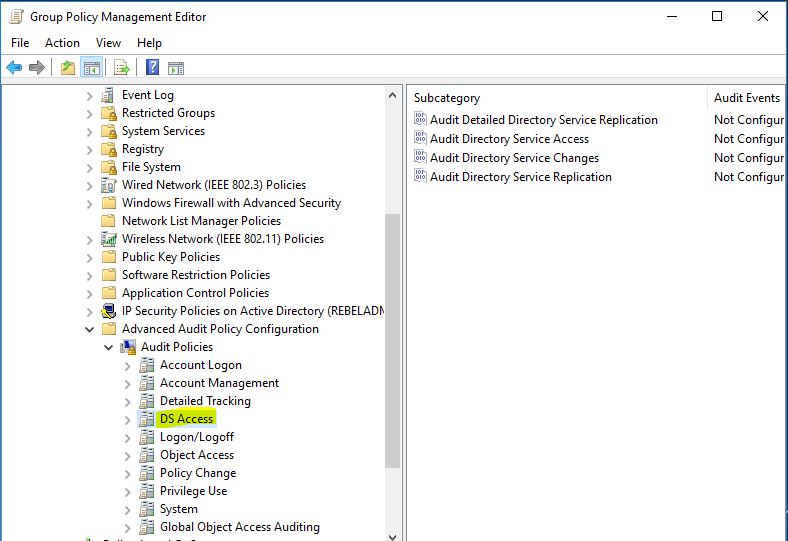
There are 4 subcategories under DS Access. Let’s see what each and subcategory capable of.
Audit Detailed Directory Service Replication
This security policy setting can be used to generate security audit events with detailed tracking information about the data that is replicated between domain controllers. This audit subcategory can be useful to diagnose replication issues.
If its enabled following events will be appear in logs
|
Event ID |
Event message |
|
4928 |
An Active Directory replica source naming context was established. |
|
4929 |
An Active Directory replica source naming context was removed. |
|
4930 |
An Active Directory replica source naming context was modified. |
|
4931 |
An Active Directory replica destination naming context was modified. |
|
4934 |
Attributes of an Active Directory object were replicated. |
|
4935 |
Replication failure begins. |
|
4936 |
Replication failure ends. |
|
4937 |
A lingering object was removed from a replica. |
Audit Directory Service Access
This security policy setting determines whether the operating system generates events when an Active Directory Domain Services (AD DS) object is accessed.
These events are similar to the Directory Service Access events in previous versions of Windows Server operating systems.
If its enabled following events will be appear in logs
|
Event ID |
Event message |
|
4662 |
An operation was performed on an object. |
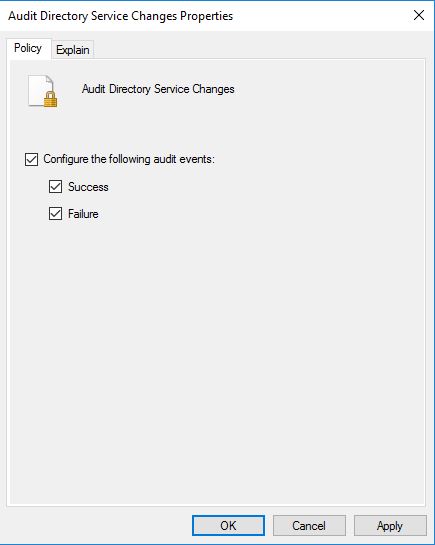
Audit Directory Service Changes
This security policy setting determines whether the operating system generates audit events when changes are made to objects in Active Directory Domain Services (AD DS). The types of changes that are reported are:
• Create
• Delete
• Modify
• Move
• Undelete
Directory Service Changes auditing, where appropriate, indicates the old and new values of the changed properties of the objects that were changed.
If its enabled following events will be appear in logs
|
Event ID |
Event message |
|
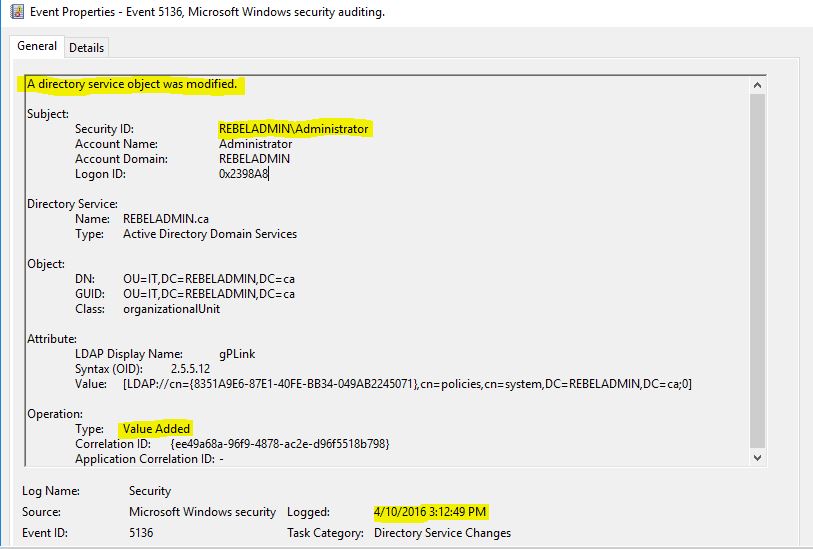
5136 |
A directory service object was modified. |
|
5137 |
A directory service object was created. |
|
5138 |
A directory service object was undeleted. |
|
5139 |
A directory service object was moved. |
|
5141 |
A directory service object was deleted. |
Audit Directory Service Replication
This security policy setting determines whether the operating system generates audit events when replication between two domain controllers begins and ends.
If its enabled following events will be appear in logs
|
Event ID |
Event message |
|
4932 |
Synchronization of a replica of an Active Directory naming context has begun. |
|
4933 |
Synchronization of a replica of an Active Directory naming context has ended. |
According to Microsoft best practices https://technet.microsoft.com/en-us/library/dn487457.aspx i am going to enable
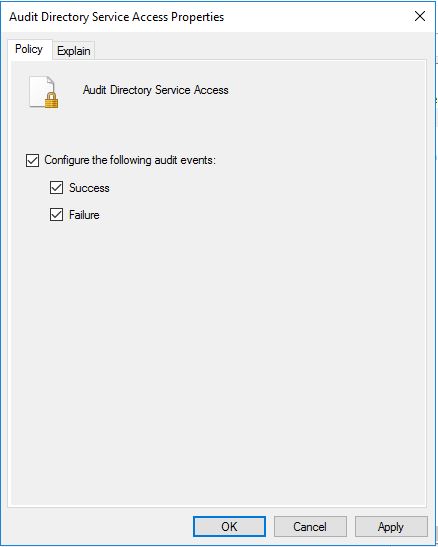
Audit Directory Service Access
Audit Directory Service Changes
Sub categories for both success and failure events. To do that double click on each subcategory and enable audit events.
After GPO apply now I can see the new events under logs. For testing I added new GPO under IT OU and in logs I can see the detail info about the activity.
If any question about the post feel free to ask me on rebeladm@live.com


