This is the part 3 of the series which explain about “Trusts” between infrastructures. If you not checked the other 2 parts yet you can find them in here.
Configuring Trusts – Part 1
Configuring Trusts – Part 2
In this article I will cover up the rest of the concepts, terms, involves with setting up a trust.
Security Identifier (SID) filtering
Microsoft Systems uses a structure known as SID to express its identities. Its act as a token. SID filtering is used to block users in trusted forest or domain being able to elevate their privileges in local forest or domain. This is important for external trusts as when you trusting you can control rights to provide credentials between domains.
By default windows 2012, windows 2012 R2 have SID filtering enabled. If you wish to disable this, you can do it using following commands. (https://technet.microsoft.com/en-us/library/cc794801(v=ws.10).aspx)
To disable SID filter quarantining for the trusting domain
Netdom trust <TrustingDomainName> /domain:<TrustedDomainName> /quarantine:No /userD:<DomainAdministratorAcct> /passwordD:<DomainAdminPwd>
To disable SID filter quarantining for the trusting forest
Netdom trust <TrustingDomainName> /domain:<TrustedDomainName> /enablesidhistory:Yes /userD:<DomainAdministratorAcct> /passwordD:<DomainAdminPwd>
It is recommended to keep the default enabled state unless you have critical reason.
Name Suffix Routing
In an organization it may have different UPN (User Principle Name) suffixes used with in its forest. For example Contoso LTD. May use contoso.com, mycontoso.net, companyA.org as name suffixes. But when you creating a trust you may not need to allow users from all these suffixes. With Name suffix routing we can enable or disable the UPN suffixes which will involve with the trust operations.
I will demonstrate how we can do this in next post which will go more in to real world configurations.
Trust Authentications
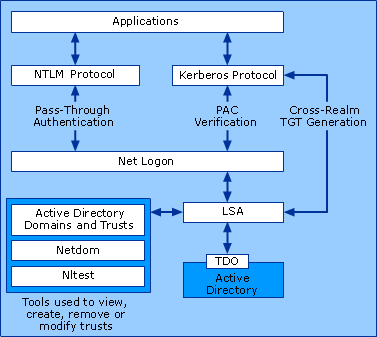
Trusts can use 2 authentication protocols. By default it uses Kerberos Version 5. If it’s not supporting it use NTLM Authentication. In order to initiate a trust, the administrator need to be a member of domain admin group or enterprise admin user group. Trust needs to initiate in both sides.
Trust Components (https://technet.microsoft.com/en-us/library/cc773178(v=ws.10).aspx)
Before initiate trusts it is important to make sure following ports are open in both sides.
UDP Port 88 – Kerberos Protocol
TCP and UDP Port 387 – LDAP
TCP Port 445 – Microsoft SMB
TCP Port 135 – Trust endpoint resolution
This is the end of a part 3 of the configuring trust series and in next article let’s look in to real world setups. If you have any questions regarding the post feel free to contact me on rebeladm@live.com