Azure Bastion is a PaaS service that provides seamless RDP/SSH connectivity to virtual machines via Azure portal. When we use Azure Bastion, virtual machines do not require public IP address to connect even if the VM is in a different VNET (same or different subscription). As long as Bastion subnet can reach the remote network (via VNET peering, VPN), we can use the Azure Bastion service to connect. Azure Bastion now supports IP-Based connectivity to on-premises, Azure, and non-azure virtual machines. It means as long as Azure bastion can reach remote networks via Express route, Site-to-Site VPN, or Peering, we can initiate IP-based RDP/SSH connection to virtual machines. Normally when we need to connect to VM via Azure bastion, we use the VM page to connect but with this new feature, we will use Azure bastion itself to initiate the connectivity. That will provides a seamless RDP/SSH access experience to Azure and Non-Azure virtual machines.
In this blog post, I am going to demonstrate how we can enable IP-based connection on the existing Azure bastion.
Prerequisites
Before we move forward with the configuration make sure you have the following,
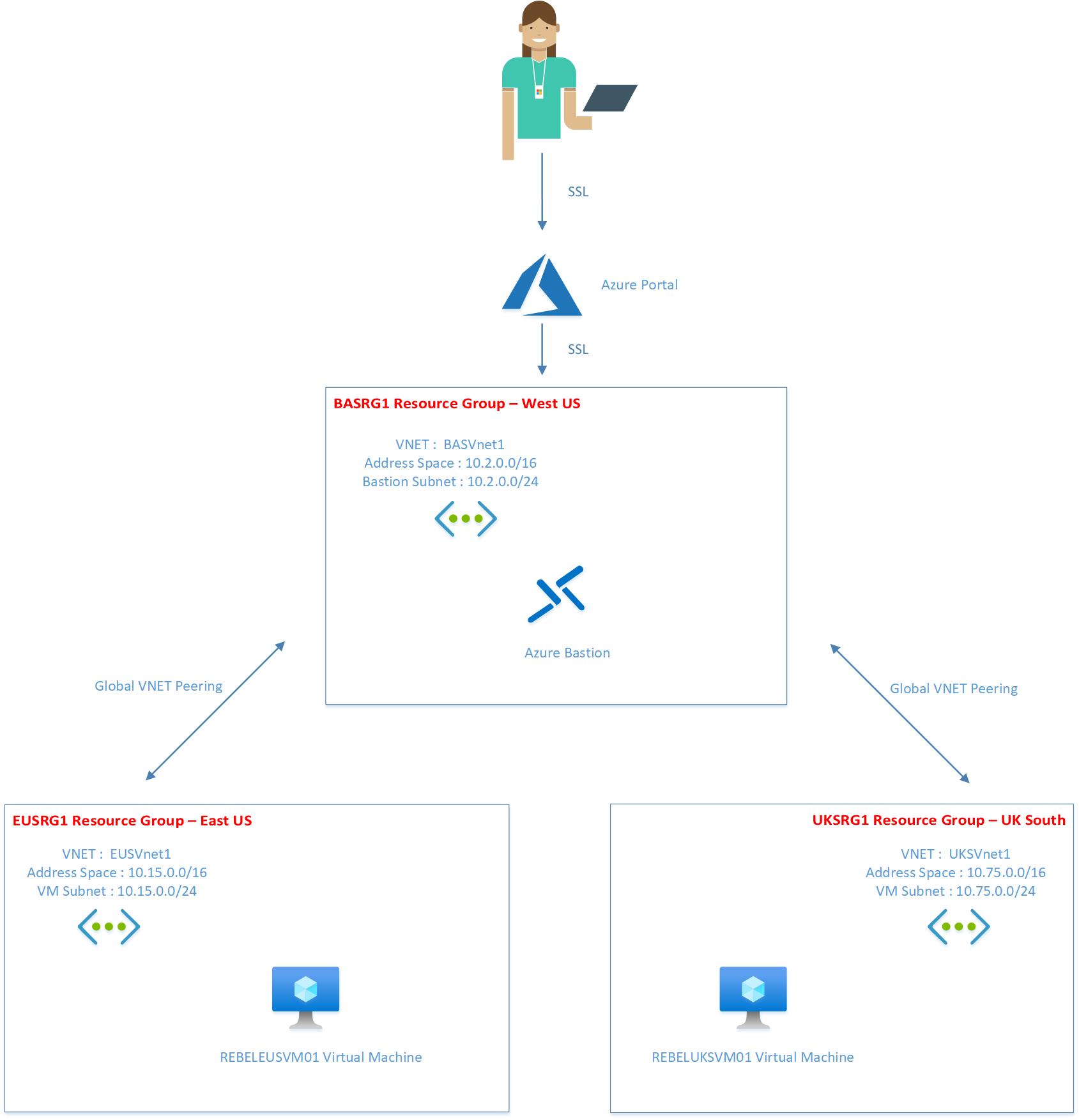
• Azure Bastion Deployed – You need to have already deployed the bastion with the relevant connectivity. Ideally, it should follow hub-spoke network topology and install Azure bastion in the hub network. All other networks will connect to the hub network. If you are using an express route or site-to-site VPN, those networks also should be reachable from the hub network. For this demo, I am using the following setup.
Here I have created three resource groups in three different Azure regions. Each resource group will have its own Azure virtual network. For the connectivity, we will be using the hub-spoke network topology. EUSVnet1 & UKSVnet1 are Spoke virtual networks and BASVnet1 is the Hub virtual network. Both Spoke virtual networks will have Global VNet peering with Hub virtual network. I have deployed the Azure Bastion service on the hub virtual network (BASVnet1). A step-by-Step guide to set up this environment is available on https://www.rebeladmin.com/2020/11/step-by-step-guide-how-to-use-azure-bastion-with-global-vnet-peering/
• Virtual machines in the remote network for testing
Configuration
To enable the IP-based connectivity,
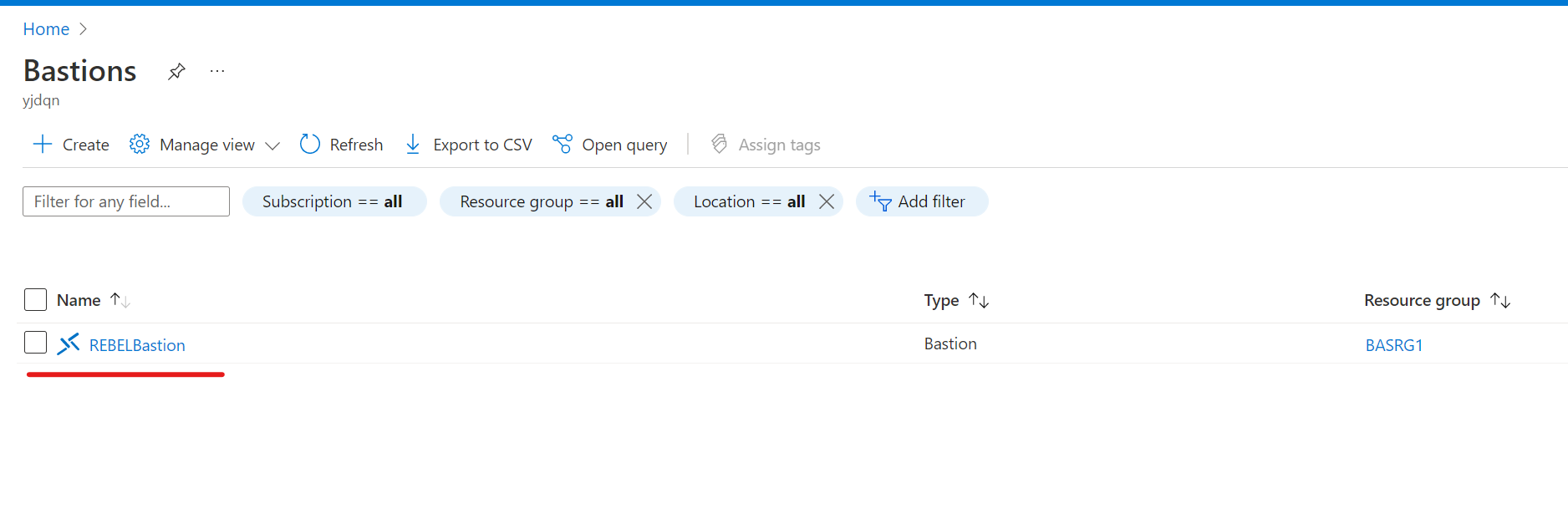
1) Go to Azure portal
2) Then search for Bastions
3) From the list, click on the relevant Azure Bastion deployment.
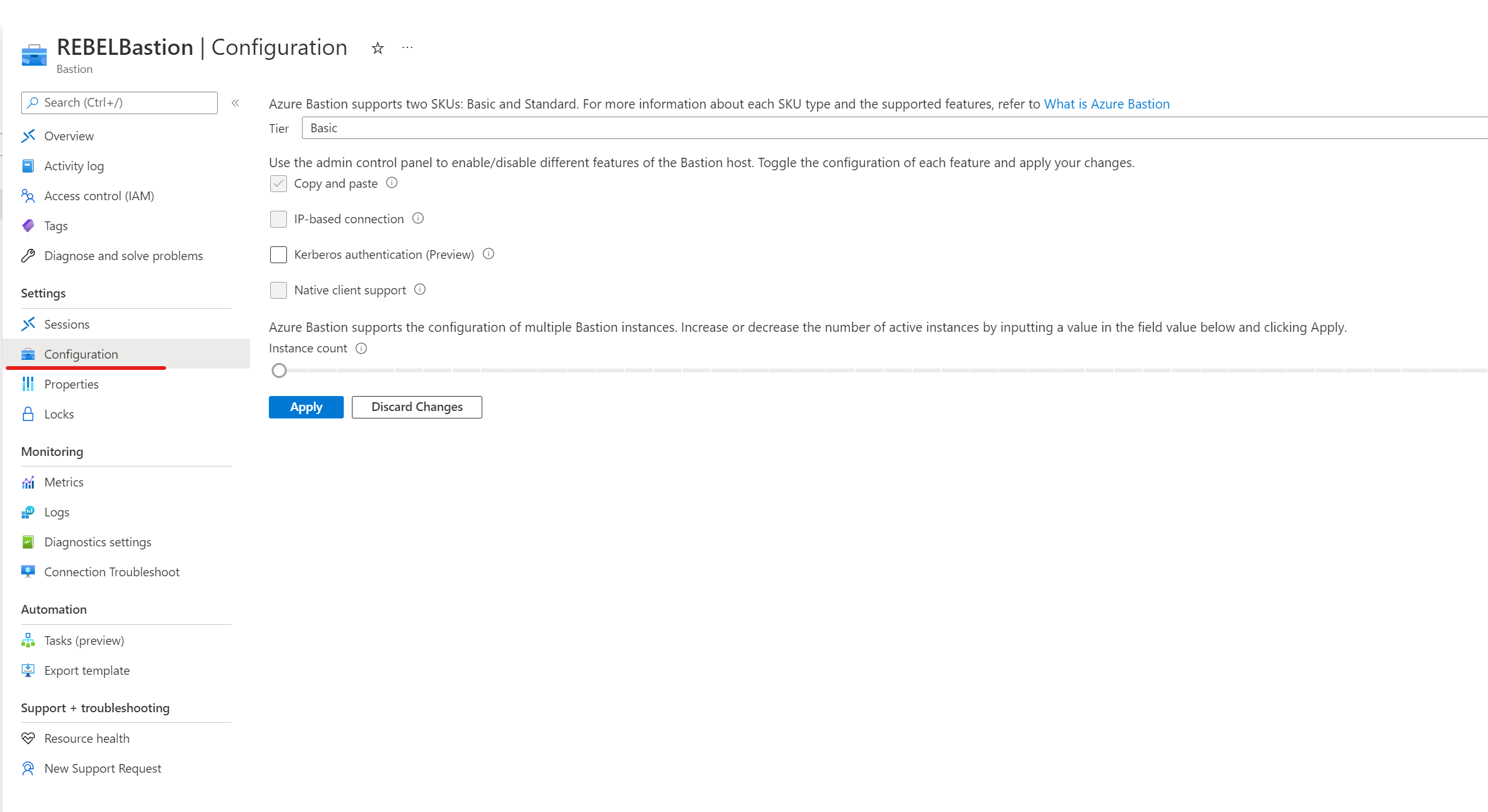
4) Then click on Configuration
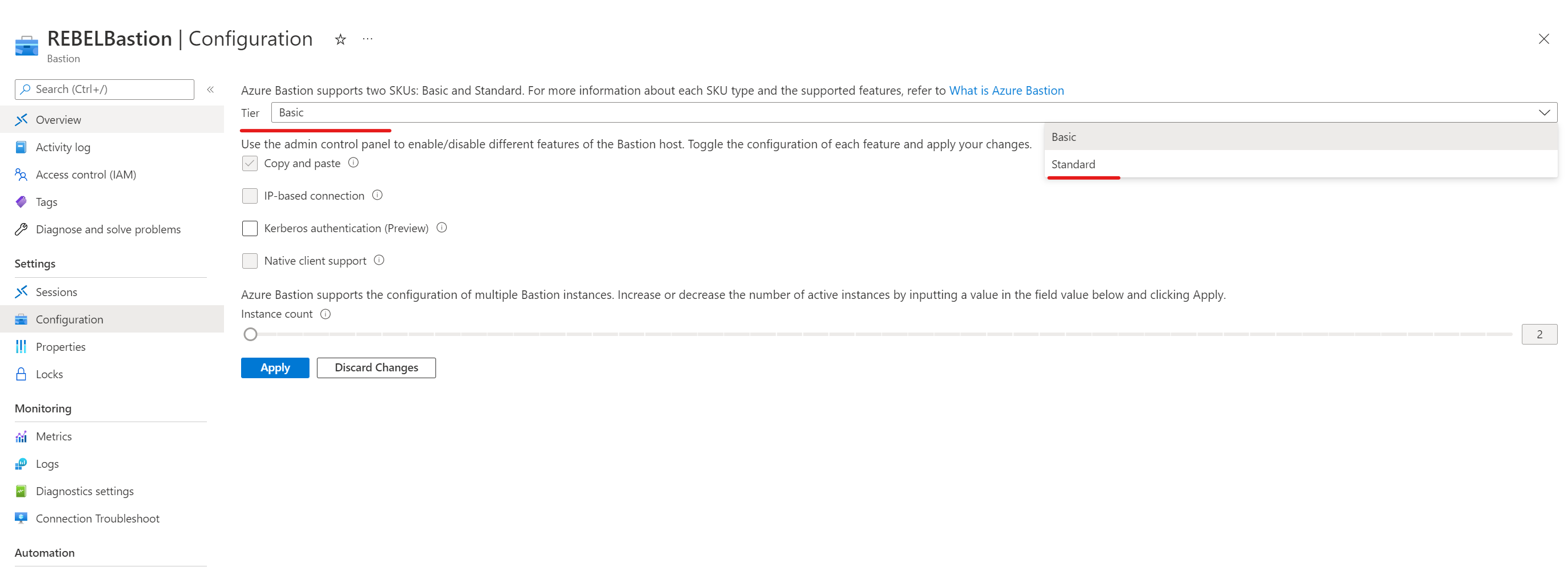
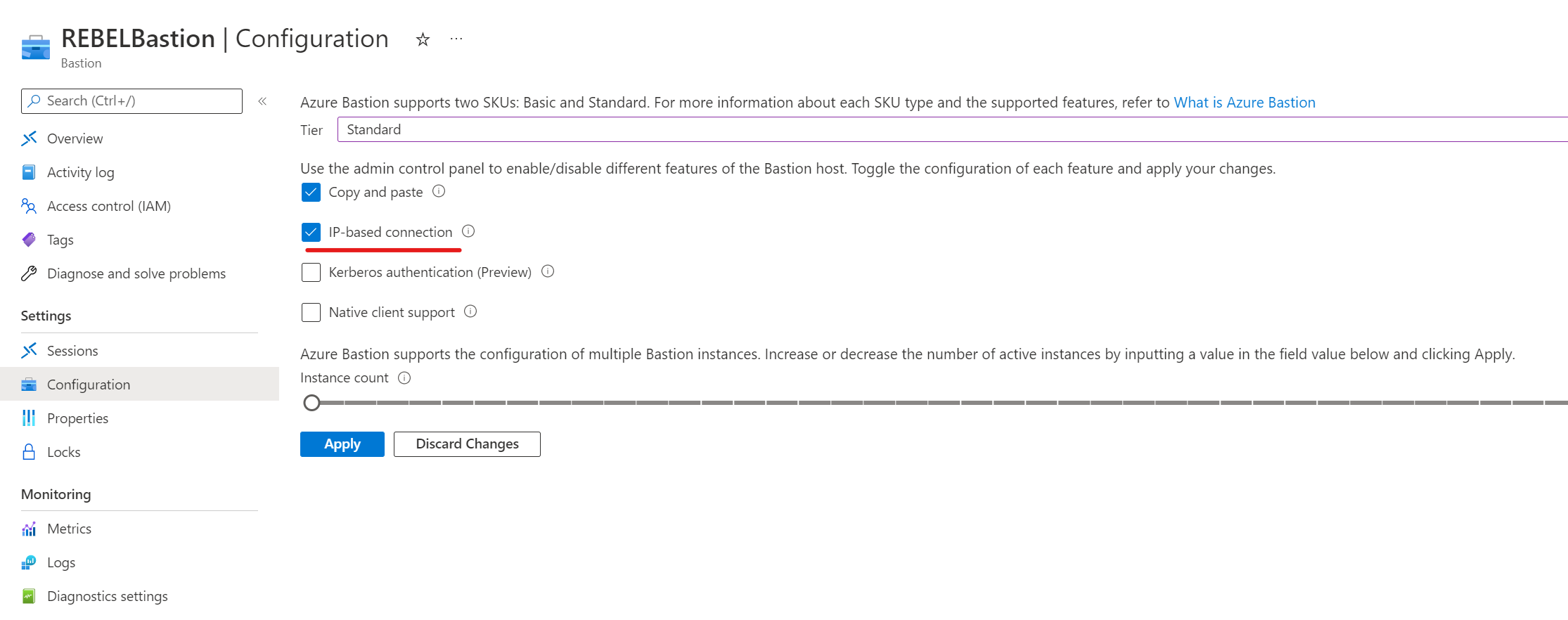
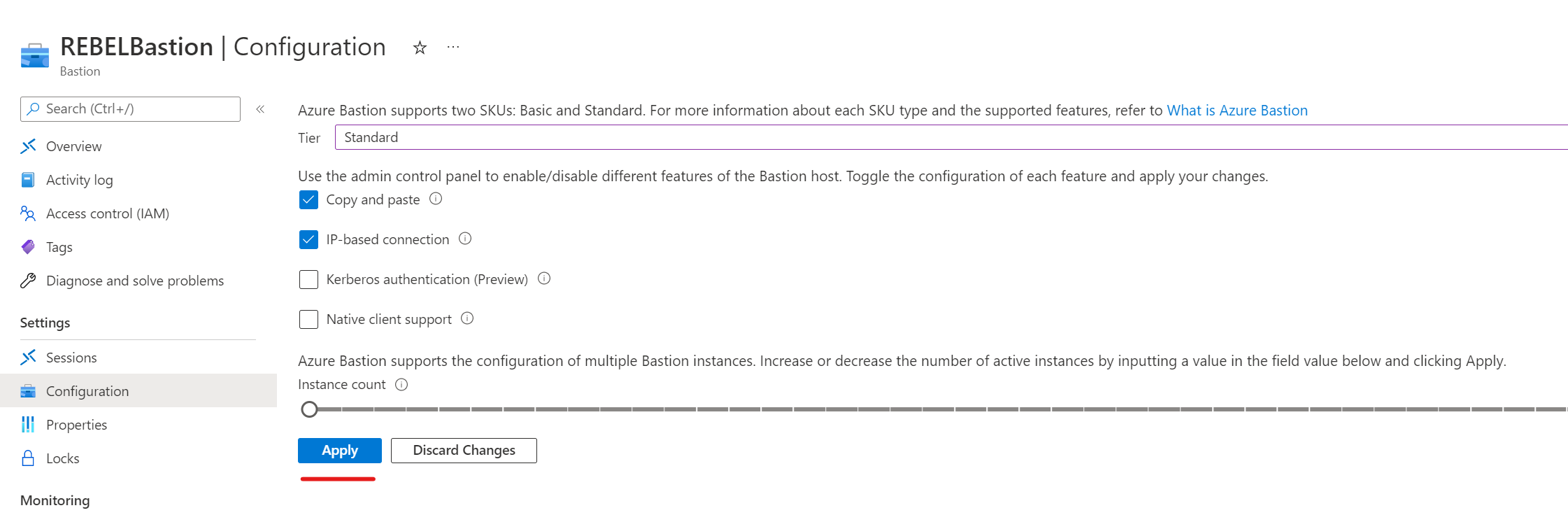
5) Under the Tier, make sure it is using Standard SKU. This feature required a standard SKU. If it’s set to Basic SKU, click on the drop-down and select Standard.
6) Then from the feature list select IP-based connection.
7) Then to apply changes click on Apply
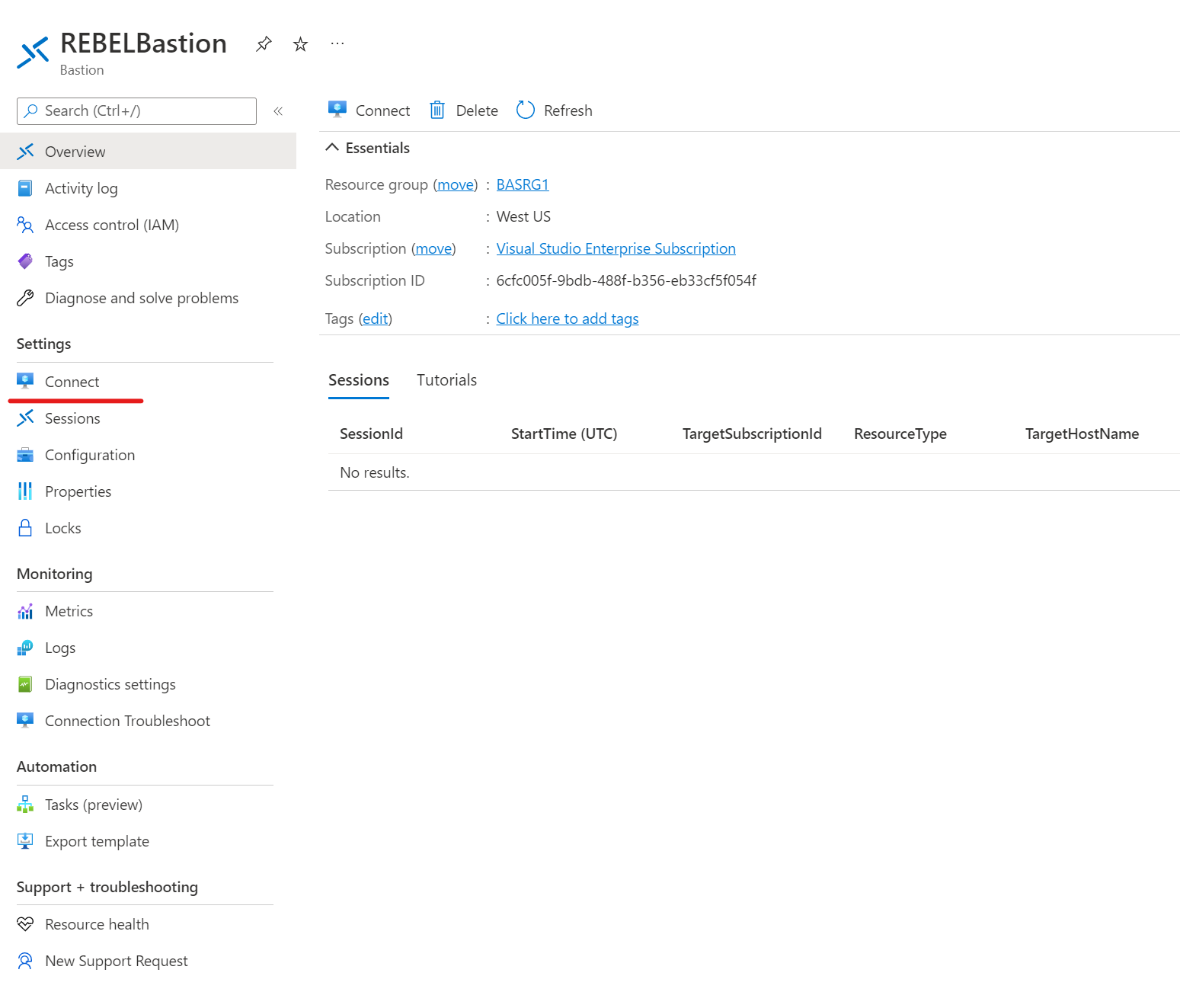
8) Once the changes are applied, we can see a new connect setting on the Bastion page.
Testing
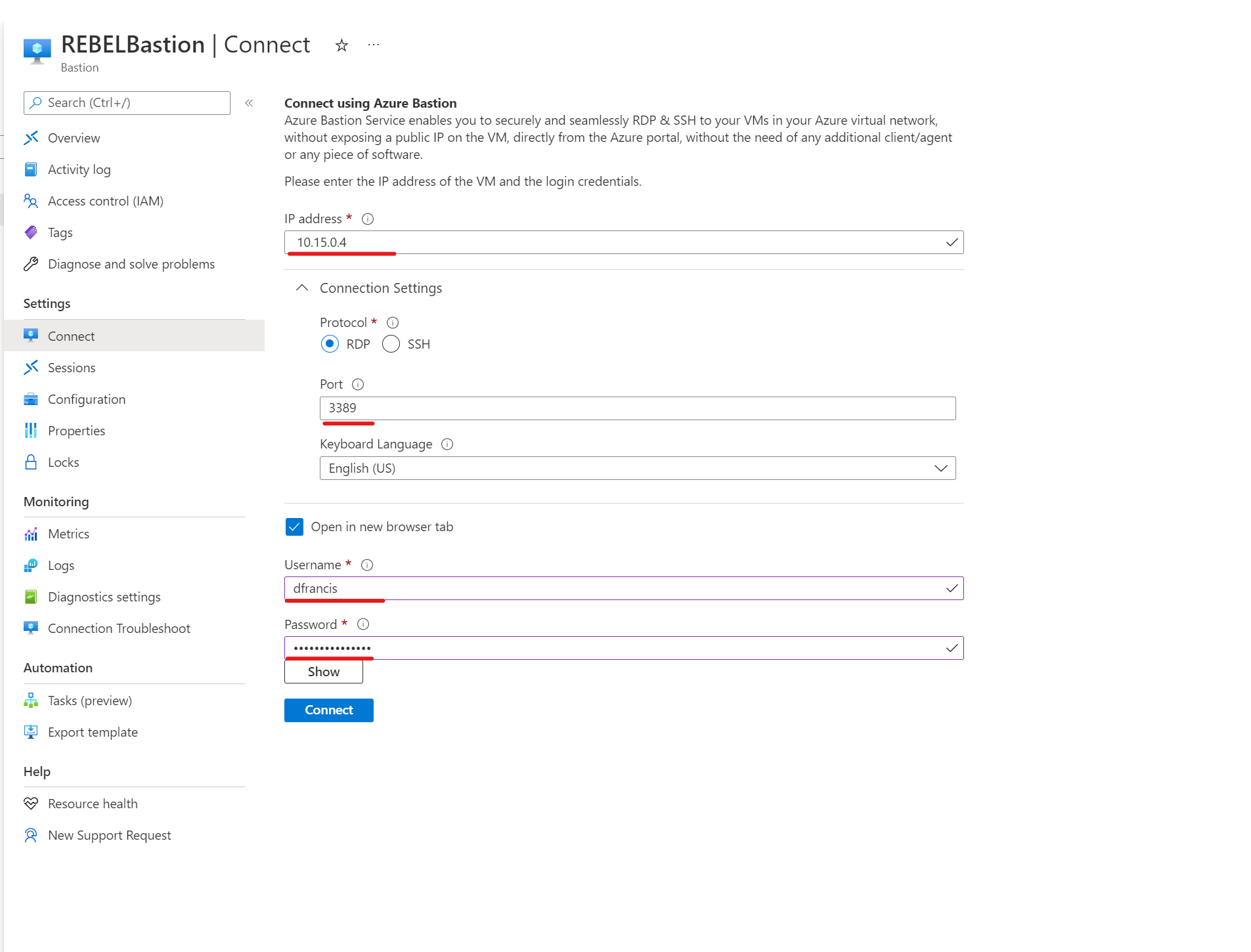
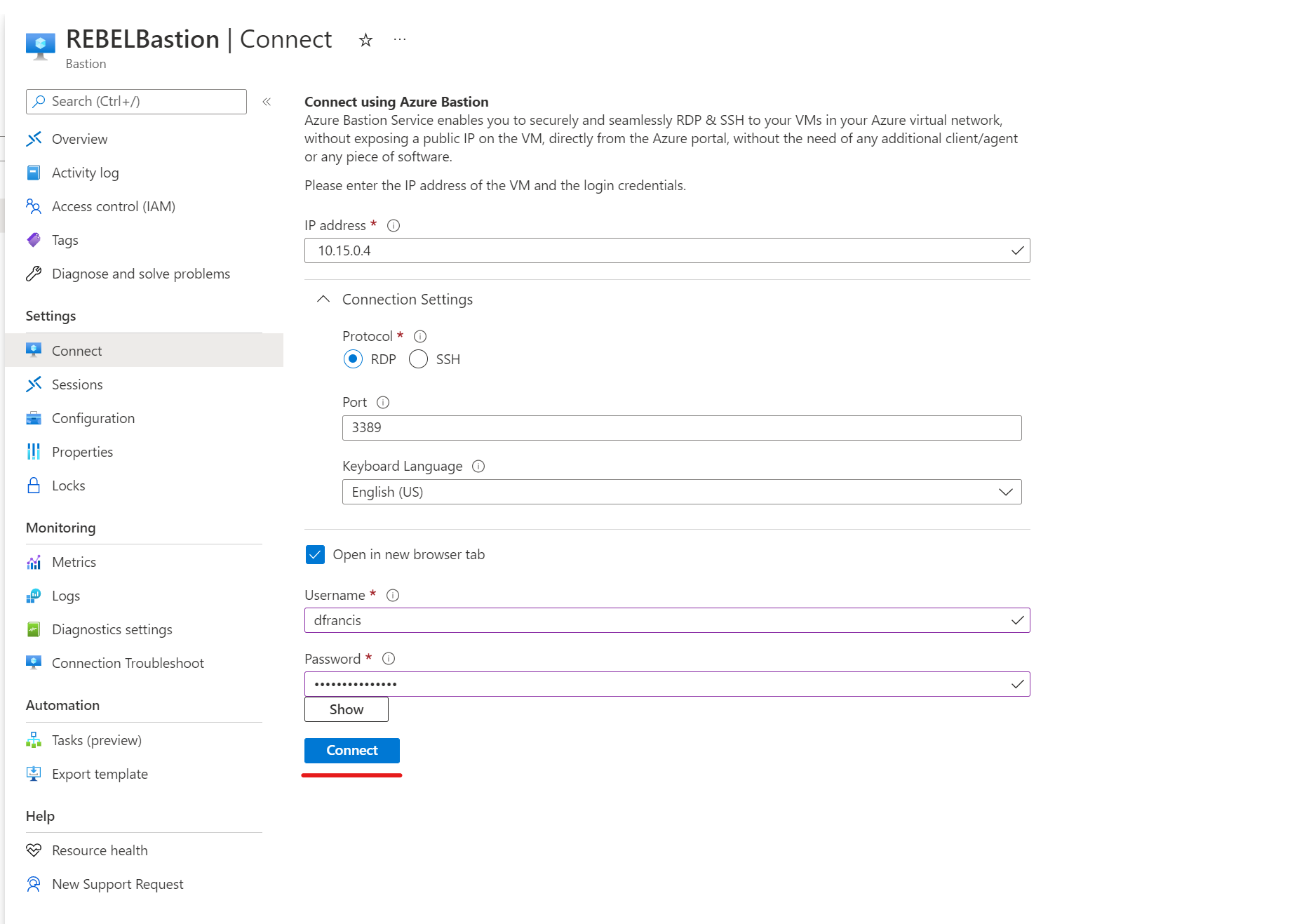
To test the connectivity, first I have chosen a VM running on EUSVnet1 (East US) which has IP 10.15.0.4. To proceed,
1) Click on Connect on Azure Bastion page.
2) Then fill in the relevant info such as IP address, port, username, and password.
3) In the end, click Connect to initiate the connection.
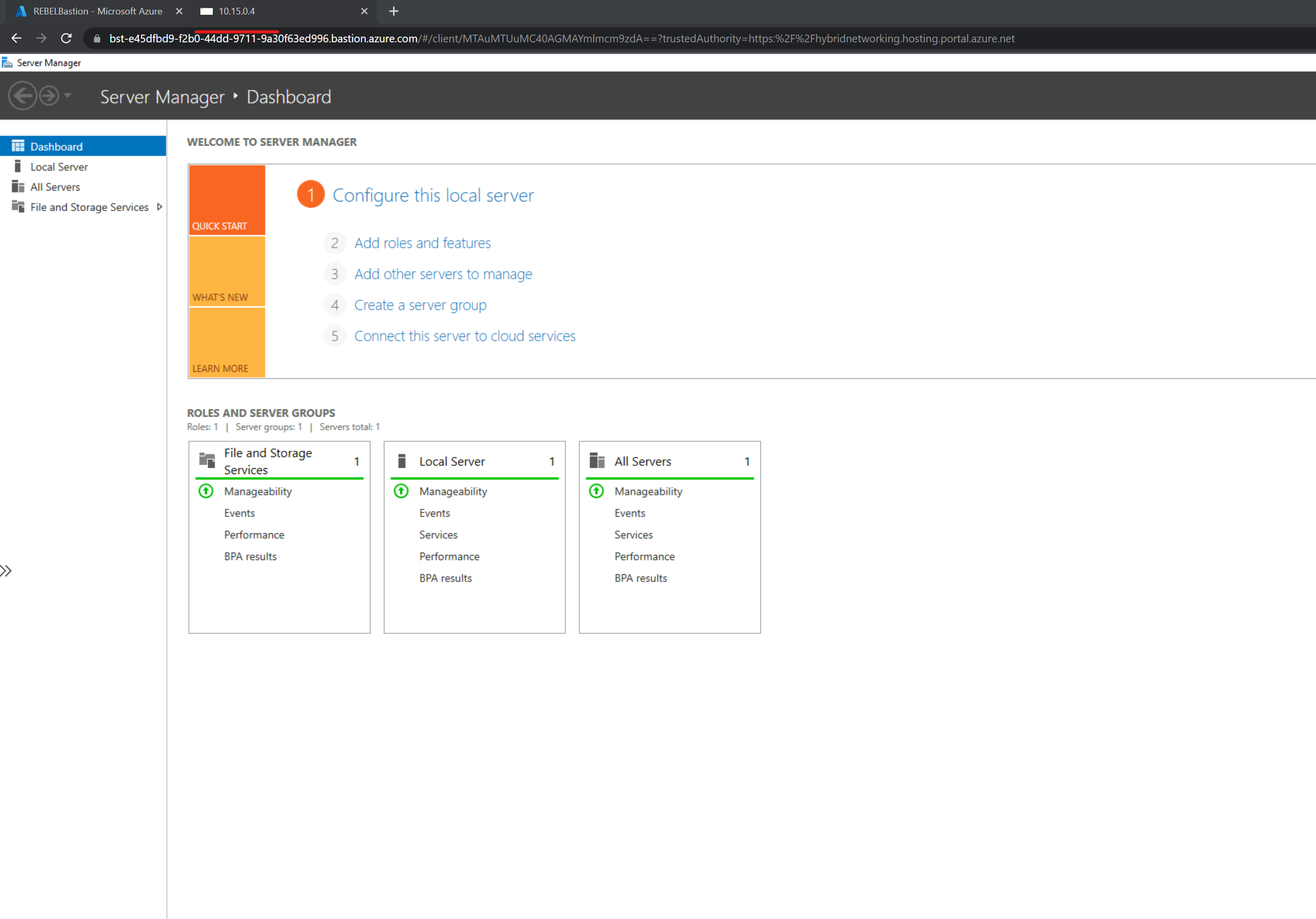
4) As expected I was able to connect to the VM (10.15.0.4) using an IP-based connection.
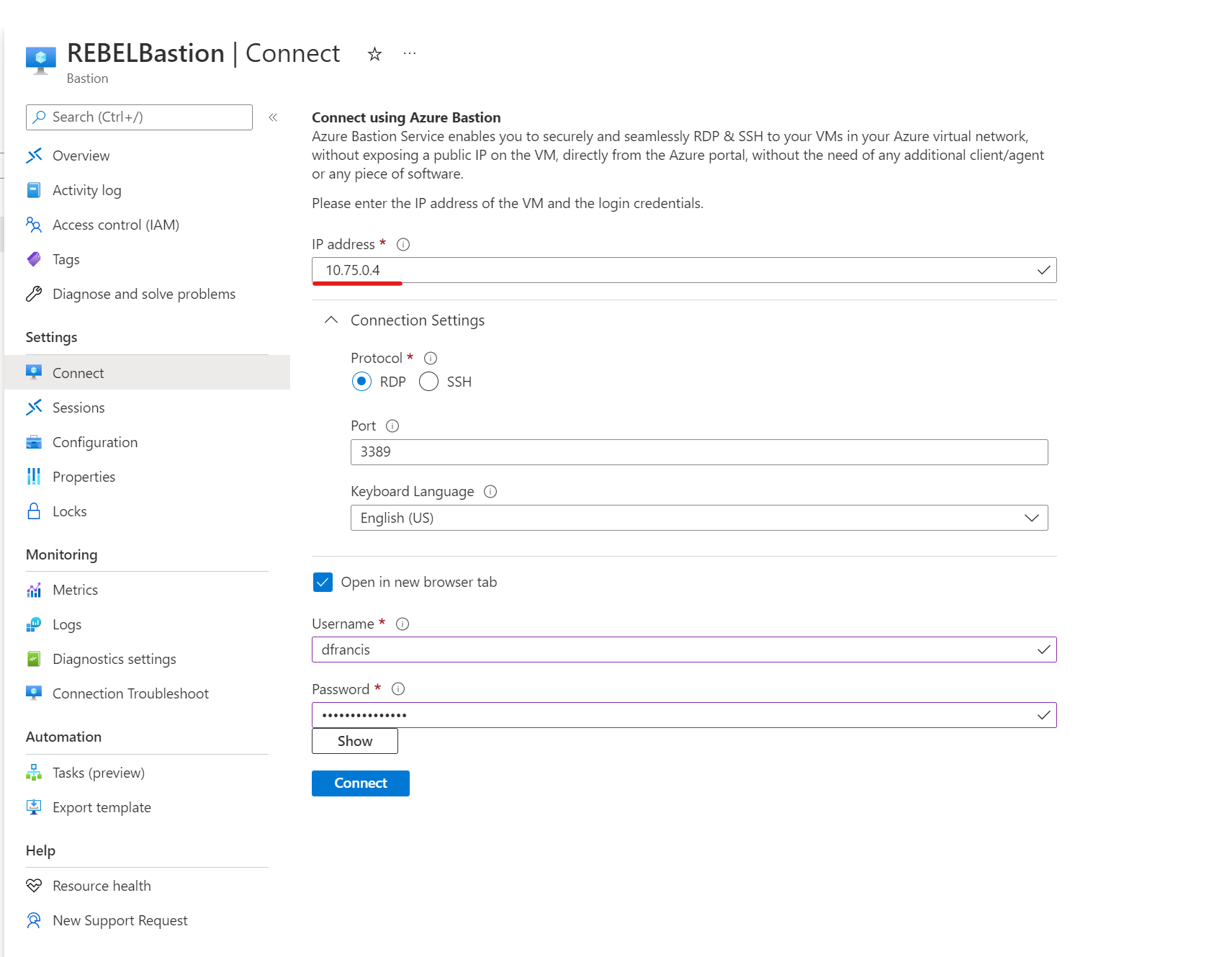
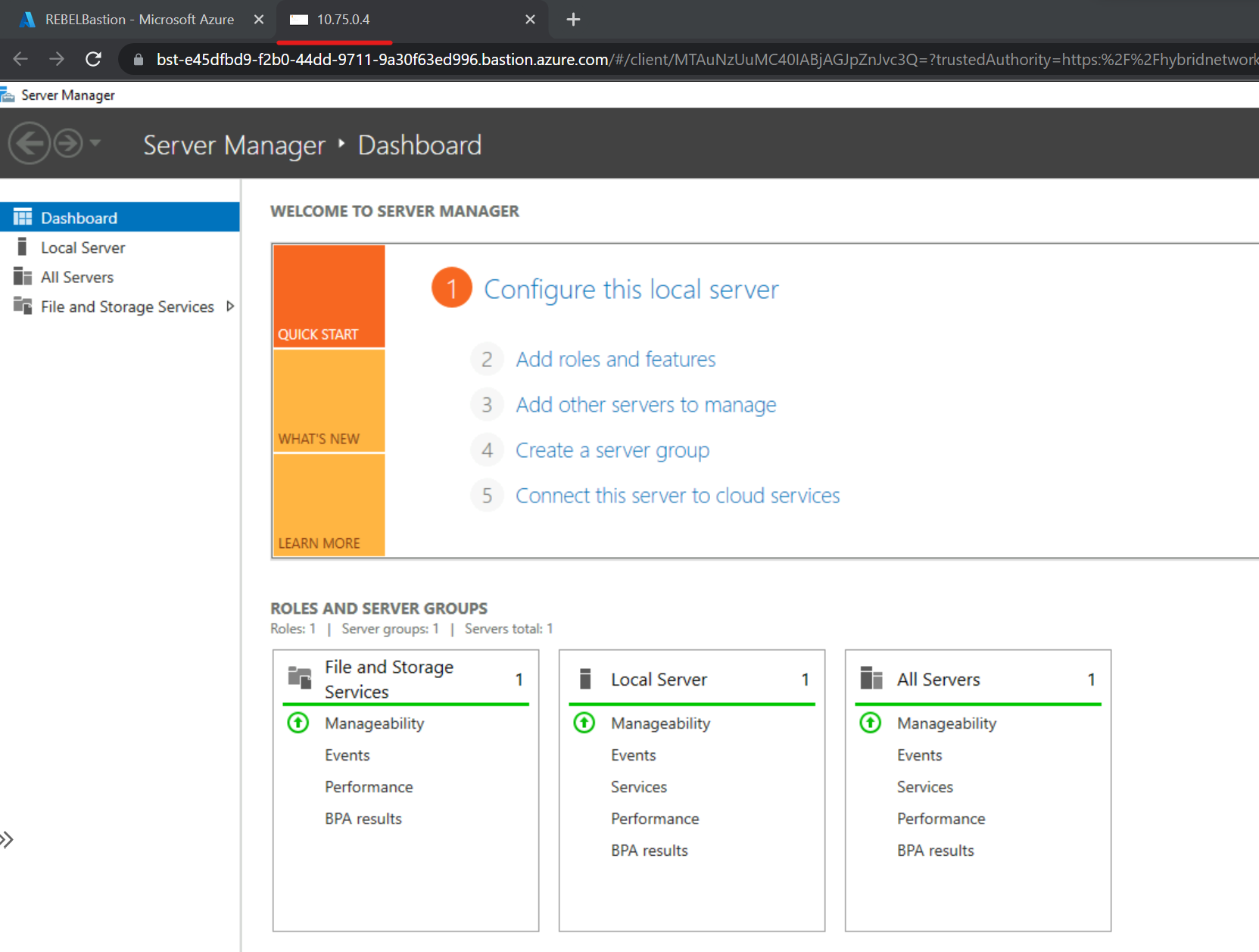
5) I also test with VM running on UKSVnet1 (UK South) which has IP address 10.75.0.4 and I was able to connect without an issue.
As we can see above, the IP-based connection with Azure Bastion is working as expected. If you have any further questions about this, feel free to contact me at rebeladm@live.com. Also, follow me on Twitter @rebeladm to get updates about new blog posts.