In previous part of this blog serious, I have explained how we can install Azure AD PowerShell module and how it can use it to manage Azure Active Directory directly using PowerShell Commands. If you not read it yet you can find it using http://www.rebeladmin.com/2017/02/manage-azure-active-directory-powershell-part-01/
In this post, I am going to explain about another set of cmdlets and the ways to use.
Some of the commands which we use for on-premises Active Directory Management works for Azure Active Directory too. only difference is the cmdlet itself. As an example, in on-premises AD, we use New-ADUser to add user, in Azure AD it becomes New-MsolUser. If you like to know further about command and its use, easiest way to start is using following commands.
Useful Azure Active Directory PowerShell commands
More information about a command can view using,
Get-Help New-MsolUser -Detailed
Technical Information about thecommand can view using,
Get-Help New-MsolUser -Full
Online information about the command can view using,
Get-Help New-MsolUser -Online
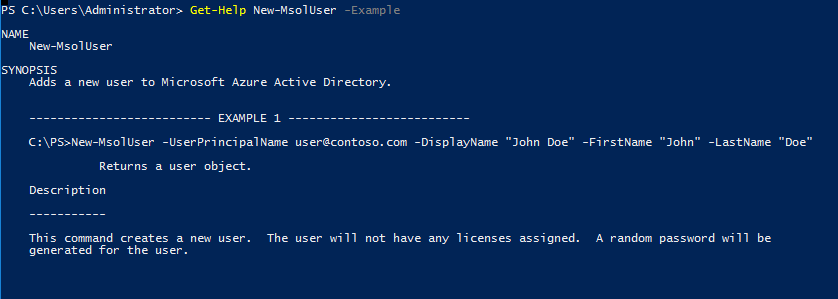
We also can view some example for the command using,
Get-Help New-MsolUser -Example
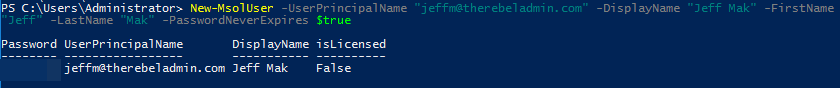
We can simply create new user using,
New-MsolUser -UserPrincipalName “jeffm@therebeladmin.com” -DisplayName “Jeff Mak” -FirstName “Jeff” -LastName “Mak” -PasswordNeverExpires $true
In order to create a user, you need to connect to Azure Active Directory with a user who has “Global Admin” role.
In above command UserPrincipalName specify the UPN and user password s set not to expire.
It is obvious sometime we need to change password of an existing account.
Set-MsolUserPassword -UserPrincipalName “jeffm@therebeladmin.com” -NewPassword “pa$$word”
The above command will reset the password for the jeffm@therebeladmin.com in to new password.
Instead of specifying password, following command will generate random password and force user to reset it on next login.
Set-MsolUserPassword -UserPrincipalName “jeffm@therebeladmin.com” -ForceChangePassword $true
Azure Active Directory does have predefined administrative roles with different capabilities. This allows administrators to assign permissions to users to do only certain tasks.
More details about these administrative roles and their capabilities can found on https://docs.microsoft.com/en-us/azure/active-directory/active-directory-assign-admin-roles
We can list down these administrative roles using
Get-MsolRole
According to requirements, we can add users to these administrative roles.
Add-MsolRoleMember -RoleName “User Account Administrator” -RoleMemberObjectId “e74c79ec-250f-4a47-80dd-78022455e383”
Above command will add user with object id e74c79ec-250f-4a47-80dd-78022455e383 to the role.
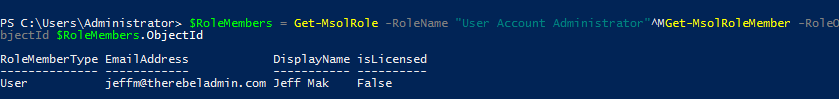
In order to view existing members of different administrator roles, we can use command similar to below.
$RoleMembers = Get-MsolRole -RoleName “User Account Administrator”
Get-MsolRoleMember -RoleObjectId $RoleMembers.ObjectId
This will list down the users with User Account Administrator role assigned.
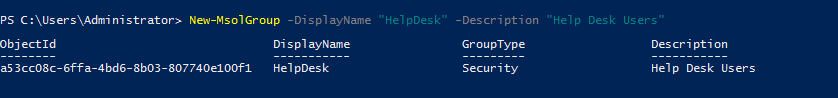
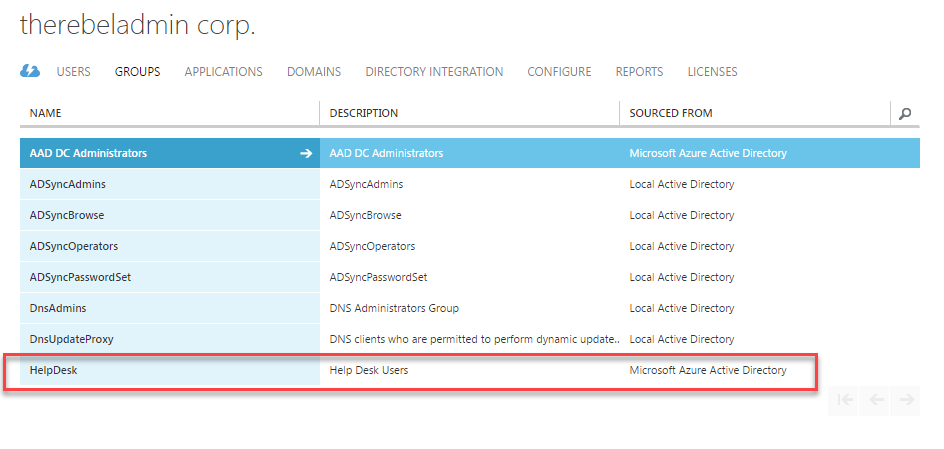
Apart from the roles, AD also have security groups.
New-MsolGroup -DisplayName “HelpDesk” -Description “Help Desk Users”
Above command creates a group called HelpDesk
A group contains members. We can add members to group using commands similar to below.
Add-MsolGroupMember -GroupObjectId a53cc08c-6ffa-4bd6-8b03-807740e100f1 -GroupMemberType User -GroupMemberObjectId e74c79ec-250f-4a47-80dd-78022455e383
This will add user with object id e74c79ec-250f-4a47-80dd-78022455e383 to group with object id a53cc08c-6ffa-4bd6-8b03-807740e100f1.
We can list down the users of the group using
Get-MsolGroupMember -GroupObjectId a53cc08c-6ffa-4bd6-8b03-807740e100f1
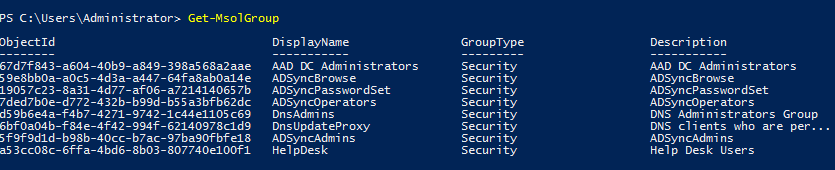
We can view all the groups and their group ids using
Get-MsolGroup
In order to remove member from the security group we can use Remove-MsoLGroupMember cmdlet.
Remove-MsoLGroupMember -GroupObjectId a53cc08c-6ffa-4bd6-8b03-807740e100f1 -GroupMemberType User -GroupmemberObjectId e74c79ec-250f-4a47-80dd-78022455e383
In order to remove a user from administrator role we can use Remove-MsolRoleMember cmdlet.
Remove-MsolRoleMember -RoleName “User Account Administrator” -RoleMemberType User -RoleMemberObjectId “e74c79ec-250f-4a47-80dd-78022455e383”
Above command will remove user with object id e74c79ec-250f-4a47-80dd-78022455e383 from the group User Account Administrator
This is the end of the part 2 of this series. In next part, we will look further in to Azure AD management with PowerShell.
If you have any questions feel free to contact me on rebeladm@live.com