AD DS security is key for any environment as it is foundation of identity protection. Before look in to improvements of AD DS security in an environment, it is important to understand how Active Directory authentication works with Kerberos. In this post I am going to explain how AD authentication works behind the scene.
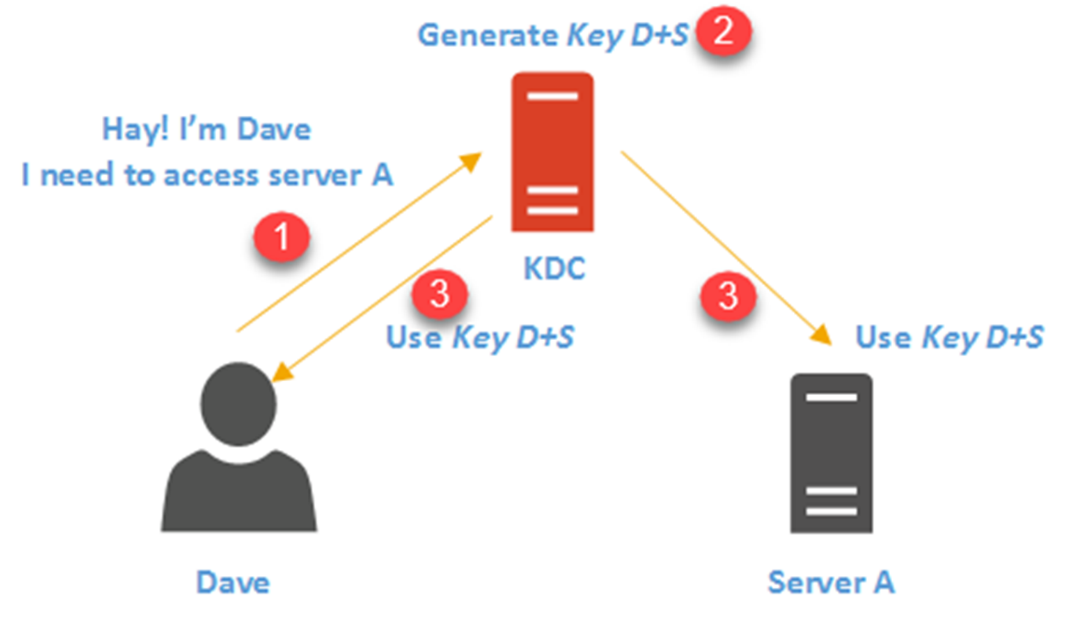
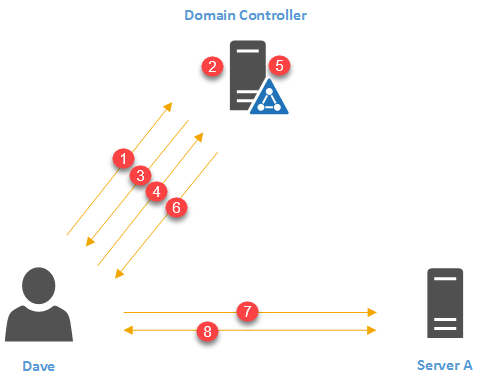
In infrastructure, there are different types of authentication protocols been used. Active Directory uses Kerberos version 5 as authentication protocol in order to provide authentication between server and client. Kerberos v5 became default authentication protocol for windows server from windows server 2003. It is an open standard and it provides interoperability with other systems which uses same standards.
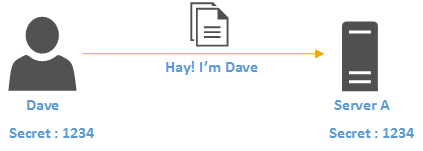
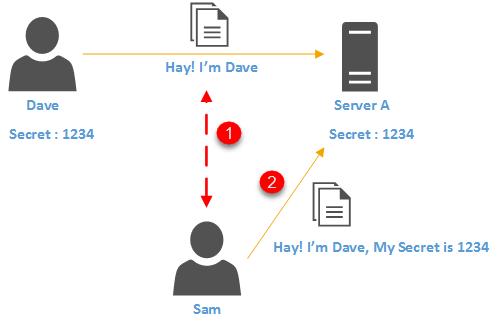
Kerberos protocol is built to protect authentication between server and client in an open network where other systems also connected. The main concept behind authentication is, two parties agreed on a password (secret) and both use it to identify and verify their authenticity.



Thank you for this detailed information on AD communication. I just need to know if you have any book which can explain all the communication details from client to all servers briefly?