Active Directory is great tool, no doubt about it, administrators can do their magic to manage resources in infrastructure with it. But same time if someone able to gain access to AD account with privileges, easily they can use those across the domain joined resources. So the protection of the AD infrastructure is critical.
Microsoft continues with implementing new security features to the Active Directory Services to protect infrastructures with emerging threats. “Protected Users Group” also a great feature implemented with windows server 2012 R2 active directory services to protect “High Valued” accounts in AD infrastructure. Advantage of this feature is member of this security group will have “non-configurable” protection automatically. I think it’s a good point especially for security feature. When have configurable options admins make changes to make their life easier and sometime losing the whole concept about security. With this security group the only way to modify the protection for account is to remove it from the group.
To use this feature the primary domain controller needs to be run on windows 2012 R2 domain functional level and devices should need to run minimum of windows 2012 R2 or windows 8.1.
What it does?
According to Microsoft,
1. The member of the Protected Users group cannot authenticate by using NTLM, Digest Authentication, or CredSSP. On a device running Windows 8.1, passwords are not cached, so the device that uses any one of these Security Support Providers (SSPs) will fail to authenticate to a domain when the account is a member of the Protected User group.
2. The Kerberos protocol will not use the weaker DES or RC4 encryption types in the pre-authentication process. This means that the domain must be configured to support at least the AES cipher suite.
3. The user’s account cannot be delegated with Kerberos constrained or unconstrained delegation. This means that former connections to other systems may fail if the user is a member of the Protected Users group.
4. The default Kerberos Ticket Granting Tickets (TGTs) lifetime setting of four hours is configurable by using Authentication Policies and Silos, which can be accessed through the Active Directory Administrative Center (ADAC). This means that when four hours has passed, the user must authenticate again.
This protection should not use for accounts for service and computers.
This table includes the properties of the group
|
Attribute |
Value |
|
Well-known SID/RID |
S-1-5-21-<domain>-525 |
|
Type |
Domain Global |
|
Default container |
CN=Users, DC=<domain>, DC= |
|
Default members |
None |
|
Default member of |
None |
|
Protected by ADMINSDHOLDER? |
No |
|
Safe to move out of default container? |
Yes |
|
Safe to delegate management of this group to non-service admins? |
No |
|
Default user rights |
No default user rights |
How to add member to the group?
To add user,
1) Log in to the Domain controller as Domain admin or Enterprise Admin
2) Go to Server Manager > Tools > Active Directory Users and Computers
3) Then under “Users” can find the “Protected Users” group
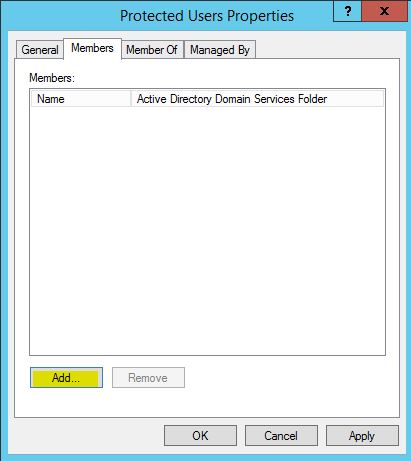
4) Double click to open the group properties and under the “members” tab you can add the users, groups
Hope this help, If you have any questions about the post feel free to contact me on rebeladm@live.com