This is the Part 03 of the Microsoft Defender for Identity blog series and so far in this series, we learned about,
Part 01 – Microsoft Defender for Identity Overview
Part 02 – Create Directory Service Account
Similar to Part 02, in this blog post also I am going to talk about another Microsoft Defender for Identity prerequisite. Microsoft Defender for Identity collects information from Windows Event logs to enrich the content of findings. Domain controllers do not collect these specific events by default and we need to enable Advanced Audit Policy settings using a group policy to enable the relevant event collection.
Microsoft Defender for Identity is interested in following windows events,
• 1644 – LDAP search
• 4662 – An operation was performed on an object
• 4726 – User Account Deleted
• 4728 – Member Added to Global Security Group
• 4729 – Member Removed from Global Security Group
• 4730 – Global Security Group Deleted
• 4732 – Member Added to Local Security Group
• 4733 – Member Removed from Local Security Group
• 4741 – Computer Account Added
• 4743 – Computer Account Deleted
• 4753 – Global Distribution Group Deleted
• 4756 – Member Added to Universal Security Group
• 4757 – Member Removed from Universal Security Group
• 4758 – Universal Security Group Deleted
• 4763 – Universal Distribution Group Deleted
• 4776 – Domain Controller Attempted to Validate Credentials for an Account (NTLM)
• 7045 – New Service Installed
• 8004 – NTLM Authentication
Source : https://docs.microsoft.com/en-us/defender-for-identity/configure-windows-event-collection
Enable Logging for Microsoft Defender for Identity
Let’s go ahead and see how we can enable these event collections. To do that,
1. Log in to one of the Domain Controllers or to a server with GPMC access as a Domain Administrator
2. Then go to Server Manager | Tools | Group Policy Management
3. Right-click on Domain Controllers Organizational Units and select Create a GPO in this domain, and Link it here …
4. Provide a name for the new policy and click on OK.
5. Then right-click on the new policy and click on Edit.
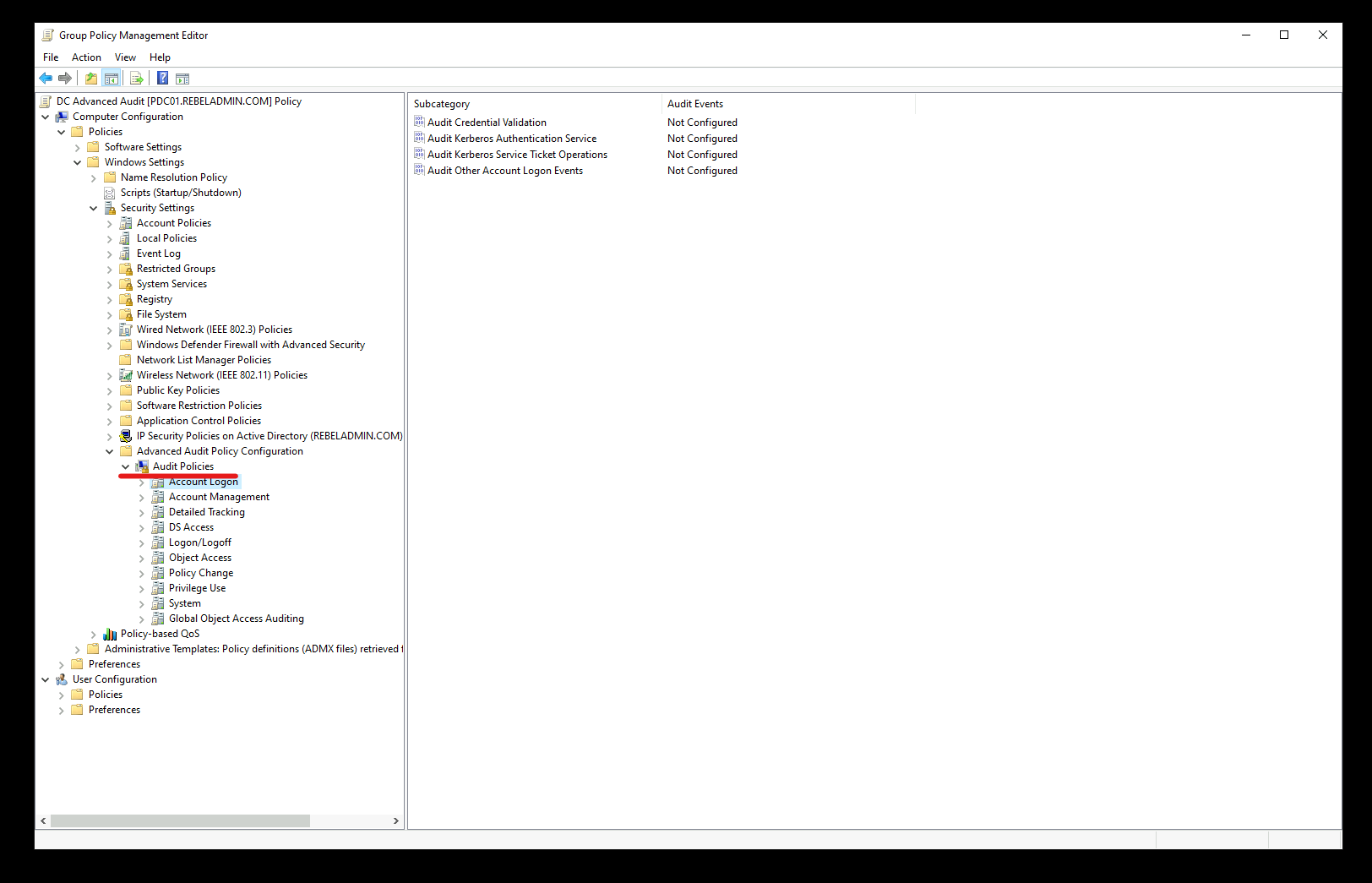
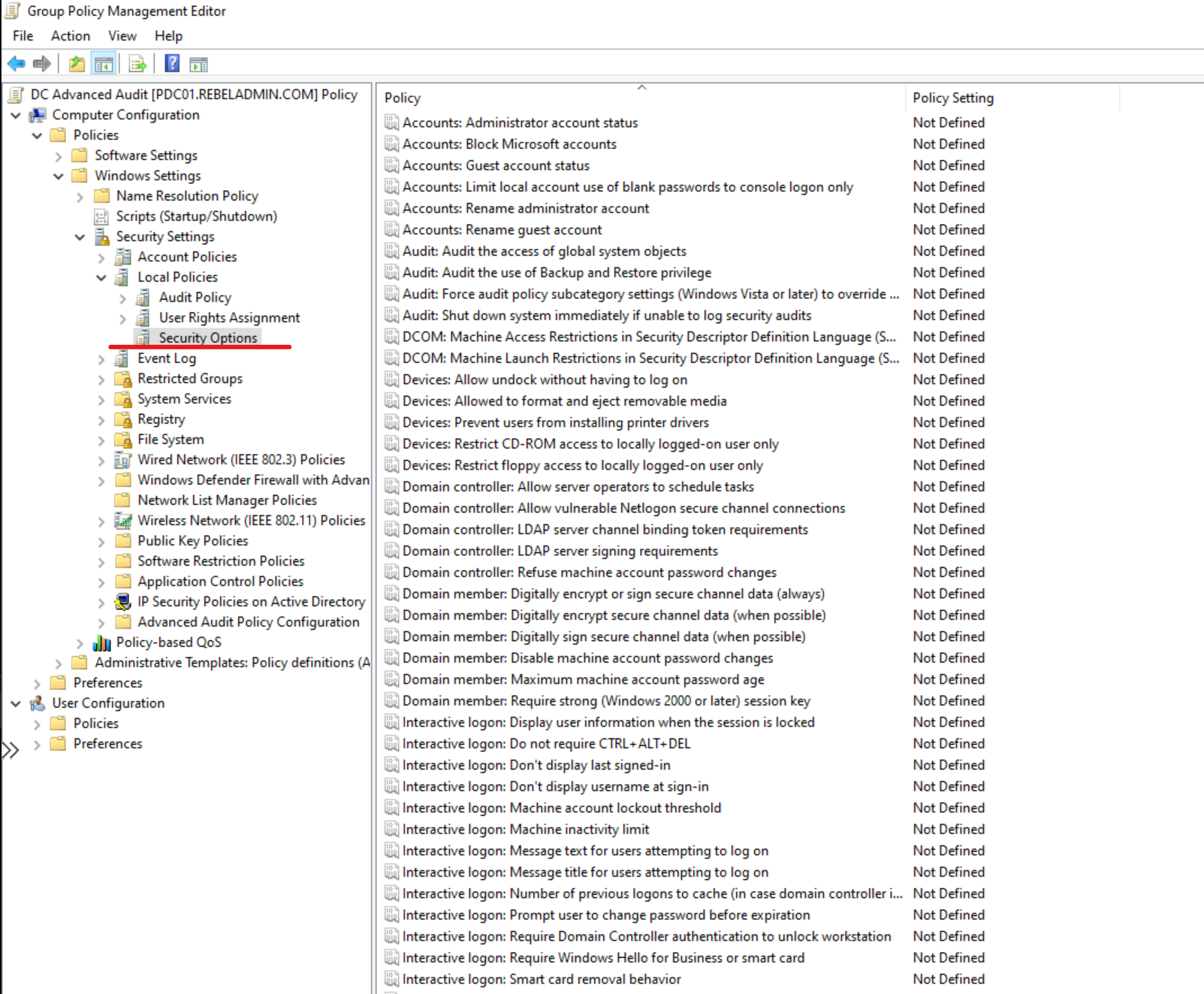
6. Go to Computer Configuration | Policies | Windows Settings | Security Settings | Advanced Audit Policy Configuration | Audit Policies. In there you can see a number of different policy settings.
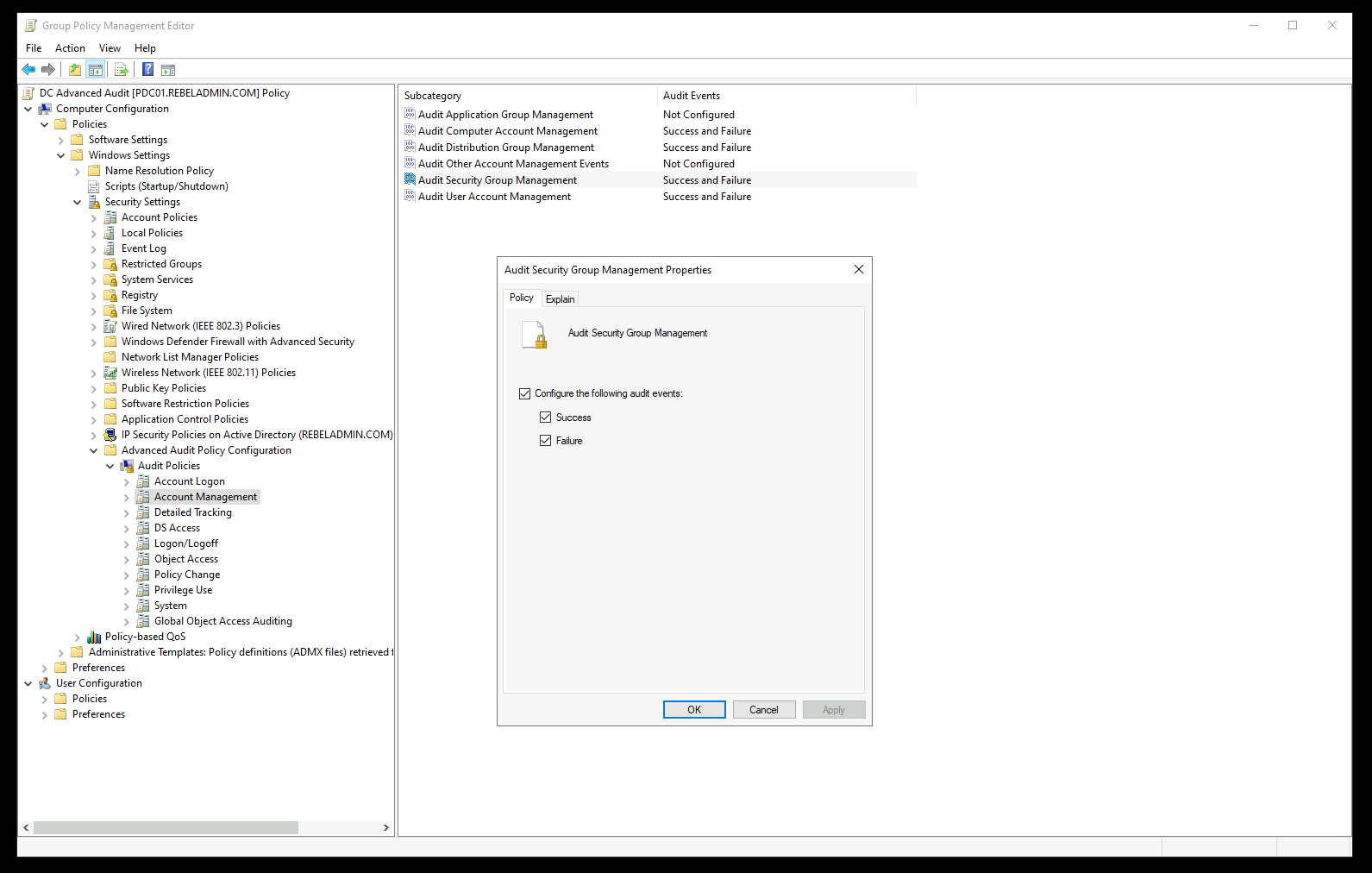
From the list, enable the following policy settings for both Success and Failure events.
| Policy | Policy Setting | Events | Audit Events |
| Account Logon | Audit Credential Validation | 4776 | Success and Failure |
| Account Management | Audit Computer Account Management | 4741, 4743 | Success and Failure |
| Account Management | Audit Distribution Group Management | 4753, 4763 | Success and Failure |
| Account Management | Audit Security Group Management | 4728, 4729, 4730, 4732, 4733, 4756, 4757, 4758 | Success and Failure |
| Account Management | Audit User Account Management | 4726 | Success and Failure |
| DS Access | Audit Directory Service Access | 4662 | Success and Failure |
| System | Audit Security System Extension | 7045 | Success and Failure |
This completes the initial configuration of the policy but we need to do some further policy changes to enable additional event collections.
Additional Configuration for NTLM Authentication events (8004)
Windows Event 8004 captures NTLM authentication data and we need to do some additional policy configuration to enable it. These additional policy settings are only applying to Domain controllers. To enable the policy settings we can use the same group policy we created in the previous step.
1. Right-click on the new policy we created in the previous step and click on Edit.
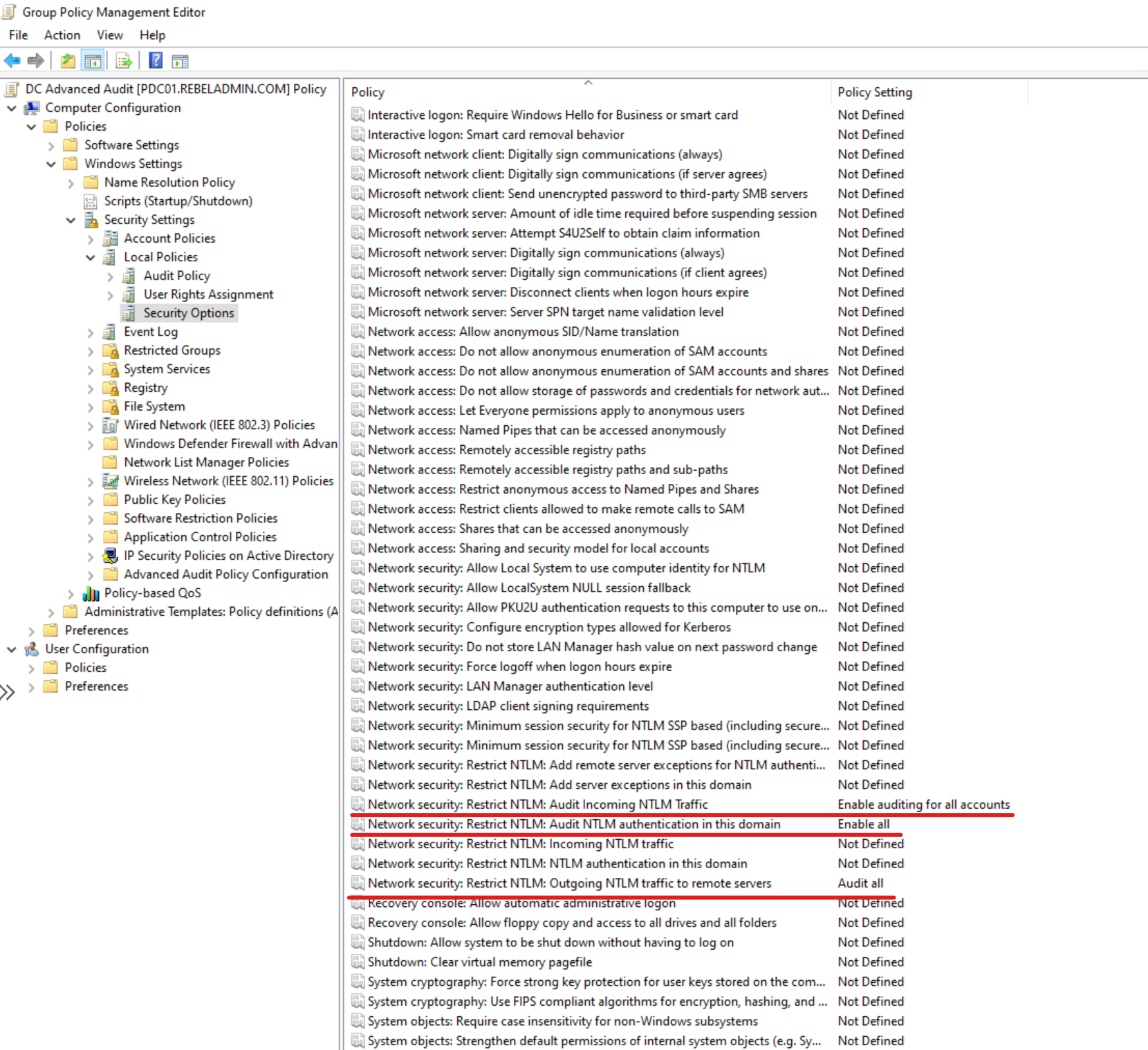
2. Go to Computer Configuration | Policies | Windows Settings | Security Settings | Local Policies | Security Options.
3. From the list of policies, configure the following with given values.
| Policy | Policy Setting |
| Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers | Audit All |
| Network security: Restrict NTLM: Audit NTLM authentication in this domain | Enable All |
| Network security: Restrict NTLM: Audit Incoming NTLM Traffic | Enable auditing for all accounts |
The above configuration will enable the event 8004 collections.
Additional Configuration for LDAP search events (1644)
Windows Event ID 1644 records information such as User, Client, Filter, and Visited entries related to LDAP queries. In a compromised environment, attackers may use LDAP searches to identify Accounts and Resources. This event collection is not enabled in Domain controllers by default and we have to use registry entries to enable it. To do that, open a notepad and paste the following values.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NTDS\Diagnostics]
“15 Field Engineering”=dword:00000005
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NTDS\Parameters]
“Expensive Search Results Threshold”=dword:00000001
“Inefficient Search Results Threshold”=dword:00000001
“Search Time Threshold (msecs)”=dword:00000001
After that, save the file as .reg file. Then double click on the file to create the relevant registry keys.
Additional Configuration for AD object audit events (4662)
Windows Event ID 4662 records information about AD object access such as SID, Account name, Account Domain, Object Type, Object Name, and Operation Type. Let’s see how we can enable this for all objects in the domain.
1. Go to Server Manager | Tools | Active Directory Users and Computers
2. Then go to View and enable Advanced Features
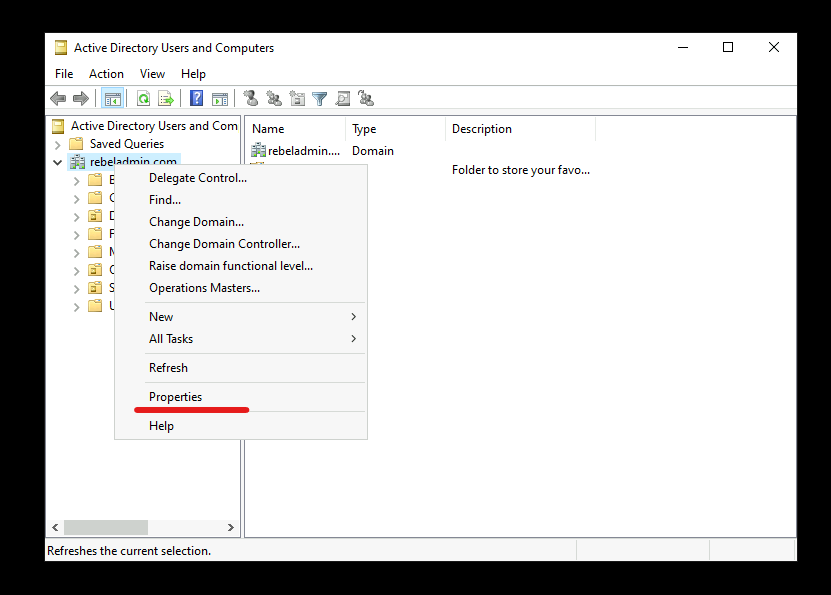
3. Right-click on the Domain name and click on Properties.
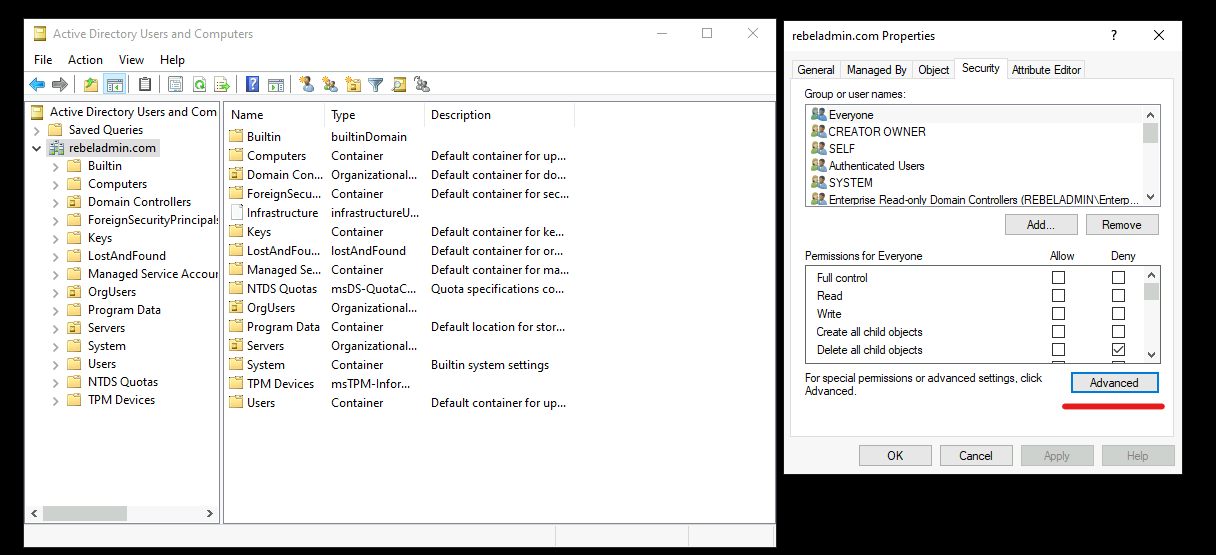
4. Go to Security tab and click on Advanced
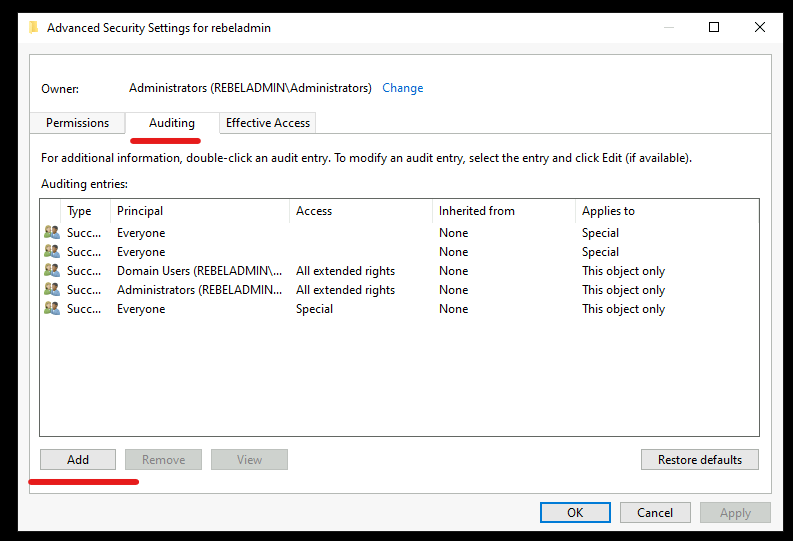
5. In Advanced security setting window, click on Auditing tab and then click on Add
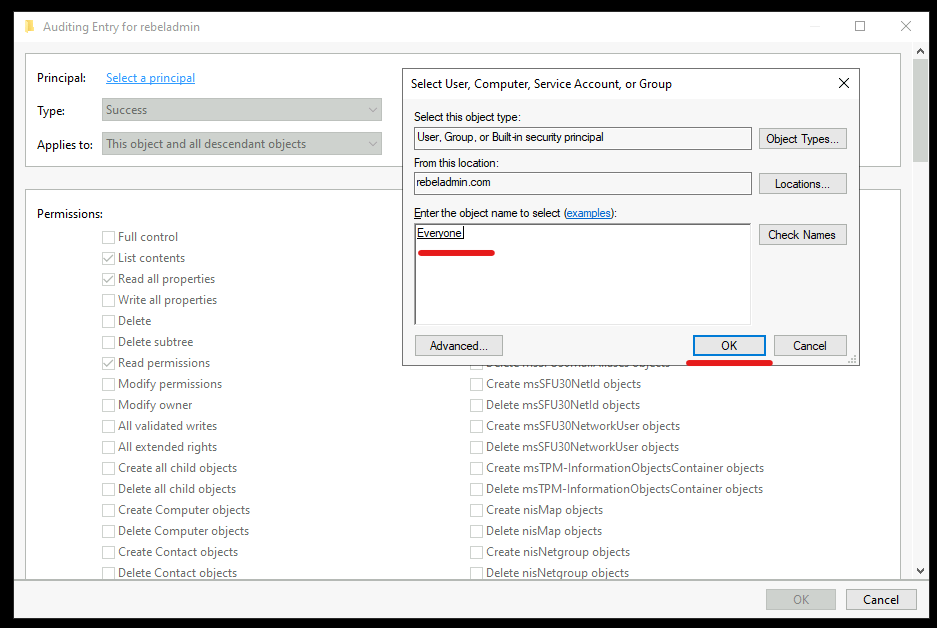
6. From the list, search for Everyone and then click on OK.
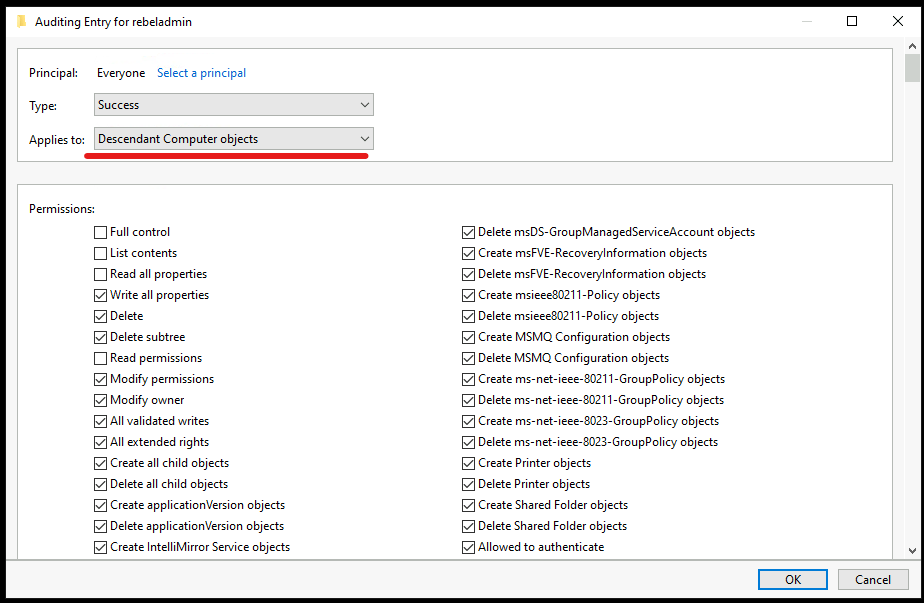
7. Then in the selection window use the following settings,
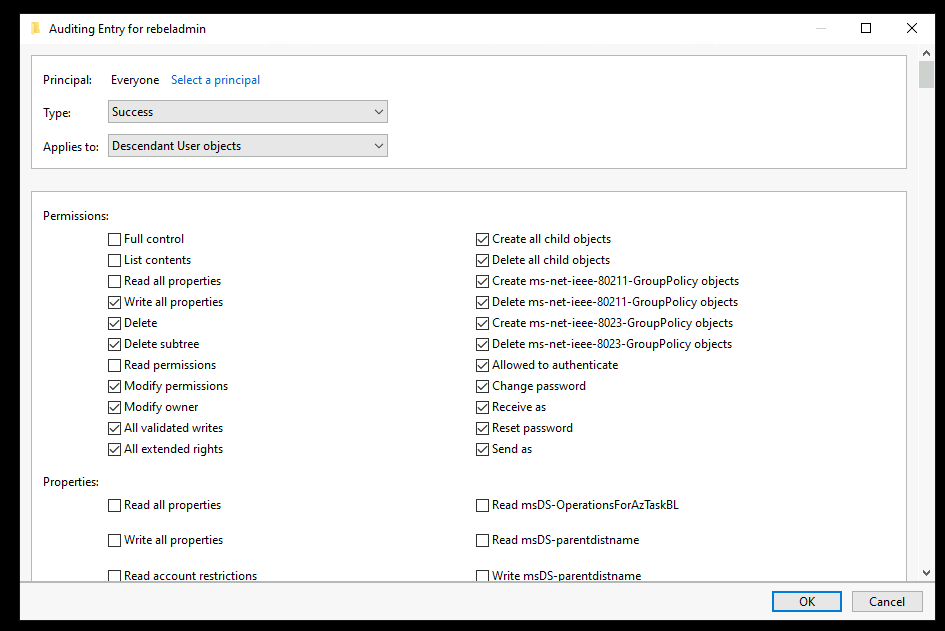
• Type – Success
• Applies to – Descendant User objects
• Permissions – First clear all selections and then select Full Control. After that uncheck Full Control, List contents, Read all properties, Read Permissions and click OK.
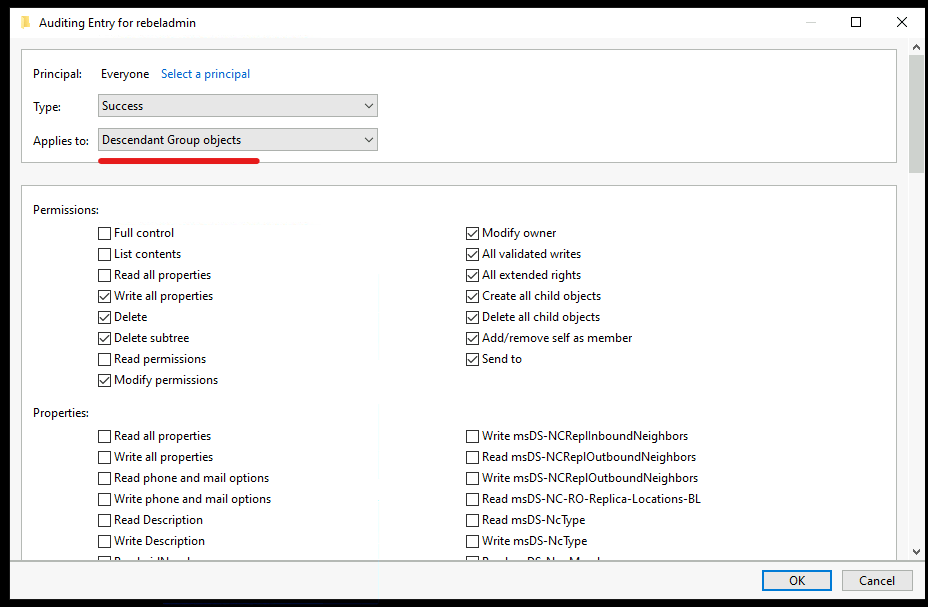
8. Repeat the same settings for Descendant Group Objects and Descendant Computer Objects.
9. Then click OK to apply changes.
This completes the configuration of Windows event collection for Microsoft Defender for Identity. If you are using ADFS in your environment, you need to do some additional configuration. More information about that available at https://docs.microsoft.com/en-us/defender-for-identity/configure-windows-event-collection . Also if you have further questions, feel free to contact me at rebeladm@live.com.