If we need to set up a connection between two independent networks (not between VLANs), we have to use a virtual private network (VPN) connections. In Azure, we use VNets to create private networks. If we need to communicate between two VNets, we have to use one of the following methods,
• VNet-to-VNet Connection – The communication happens between two VPN gateways. This is easy to set up, compare to the site-to-site VPN method.
• Site-to-Site VPN – This is similar to creating VPN connection to the on-premises network. It also uses VPN gateway, but it gives more control over the local network gateway.
• VNet Peering – This method doesn't use VPN gateways and it routes the traffic via Microsoft backend infrastructure. More information about VNet peering is available on https://docs.microsoft.com/en-us/azure/virtual-network/virtual-network-peering-overview
In this demo, I am going to demonstrate how to create a VNet-to-VNet connection. These types of connections can establish between,
• Virtual Networks in the same region
• Virtual Networks in different regions
• Virtual Networks in different subscriptions
In this demo, I am going to create a VNet-to-VNet VPN connection between two virtual networks in two different regions.
According to the above diagram, EUSVnet1 virtual network will be running on East US Azure region and UKSVnet1 virtual network will be running on UK South Azure region. Let's see how we can establish a VPN gateway connection between these two networks. Before start, please make sure you have the following in place.
• Valid Azure Subscription – You can also use free azure subscription for testing purpose. https://azure.microsoft.com/en-gb/free/
• Azure PowerShell Module – In this demo I am going to use PowerShell. Please make sure you have Azure PowerShell module installed. More info about it can find under https://docs.microsoft.com/en-us/powershell/azure/install-az-ps?view=azps-2.6.0
Create Resource Groups
The first step of the configuration is to create new resource groups in different regions.
To do that,
1. Launch PowerShell console and connect to Azure using Connect-AzAccount
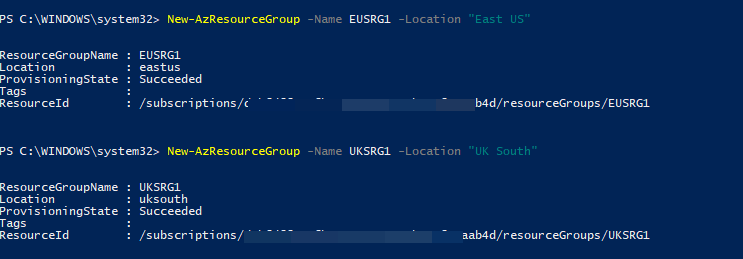
2. Then create EUSRG1 under East US Azure region by using,
New-AzResourceGroup -Name EUSRG1 -Location "East US"
In the above command, -Name parameter specifies the resource group name and -Location parameter specify the Azure region.
3. Next step is to create UKSRG1 resource group in UK South Azure region by using,
New-AzResourceGroup -Name UKSRG1 -Location "UK South"
Configure EUSVnet1
According to the plan, EUSVnet1 address space is 10.15.0.0/16. It is a class B IP address range. We do not need the entire range for workloads. Therefore, I am going to create two small subnets under it.
• VM Network – 10.15.0.0/24
• Gateway subnet – 10.15.255.0/27
In the above, VM network is going to use for virtual machines and Gateway Subnet is going to use for the VPN gateway setup.
To continue,
1. As the first step, let's create some variables.
$subn1 = New-AzVirtualNetworkSubnetConfig -Name VMNet1 -AddressPrefix 10.15.0.0/24
$gwsubn = New-AzVirtualNetworkSubnetConfig -Name "GatewaySubnet" -AddressPrefix 10.15.255.0/27
In the above, we define the two new subnets. The gateway subnet name must stay as GatewaySubnet. Otherwise, VPN gateway configuration fails.
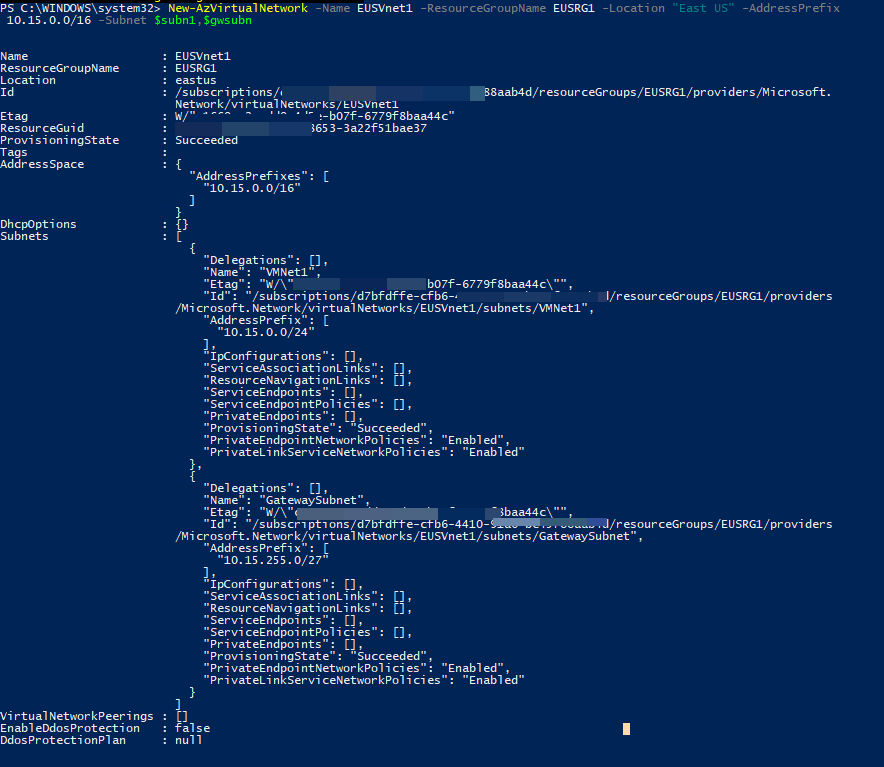
2. Now it is time to create EUSVnet1,
New-AzVirtualNetwork -Name EUSVnet1 -ResourceGroupName EUSRG1 -Location "East US" -AddressPrefix 10.15.0.0/16 -Subnet $subn1,$gwsubn
In above, -AddressPrefix parameter defines the VNet IP address range and -Subnet defines the subnets under the virtual network.
3. The next step of the configuration is to request a public IP address for the gateway. It can be done using,
$gatewayip1 = New-AzPublicIpAddress -Name EUSVnet1GW1 -ResourceGroupName EUSRG1 -Location "East US" -AllocationMethod Dynamic
Here, the public IP address allocation method is Dynamic. We can't use a static IP address here. Also, the result of the command, passed into a variable for future use.
4. Then let's prepare some variables which are going to use in the gateway configuration.
$v1 = Get-AzVirtualNetwork -Name EUSVnet1 -ResourceGroupName EUSRG1
$sub1 = Get-AzVirtualNetworkSubnetConfig -Name "GatewaySubnet" -VirtualNetwork $v1
$gwipconfig1 = New-AzVirtualNetworkGatewayIpConfig -Name gwipconf1 -Subnet $sub1 -PublicIpAddress $gatewayip1
In above, New-AzVirtualNetworkGatewayIpConfig command used to create an IP configuration for gateway (using previously created gateway subnet & public IP address)
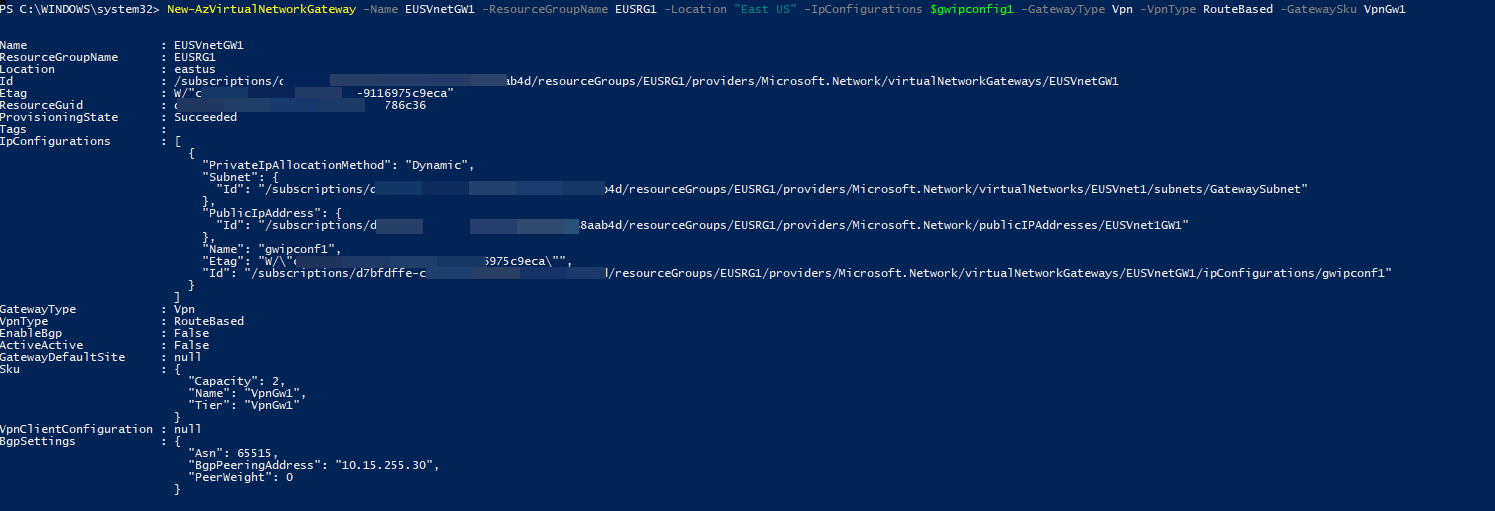
5. Finally, we can create the gateway using,
New-AzVirtualNetworkGateway -Name EUSVnetGW1 -ResourceGroupName EUSRG1 -Location "East US" -IpConfigurations $gwipconfig1 -GatewayType Vpn -VpnType RouteBased -GatewaySku VpnGw1
In above, VPN type must be set to router-based. For the GatewaySku, we can use one of the following – Basic, Standard, HighPerformance, UltraPerformance, VpnGw1, VpnGw2, VpnGw3, VpnGw1AZ, VpnGw2AZ, VpnGw3AZ, ErGw1AZ, ErGw2AZ, ErGw3AZ. Based on the sku, the VPN gateway pricing will be changed. In this demo, I am using VpnGw1 SKU. Once the command is processed, it can take up to 45 minutes to complete the gateway configuration.
Configure UKSVnet1
Using the same steps, we also need to create relevant subnets and VPN gateway for UKSVnet1 virtual network. For this network 10.75.0.0/16 is the address space. We need to create following subnets under it,
• VM Network – 10.75.0.0/24
• Gateway subnet – 10.75.255.0/27
1. The first step is to create few variables which will be used later in the configuration.
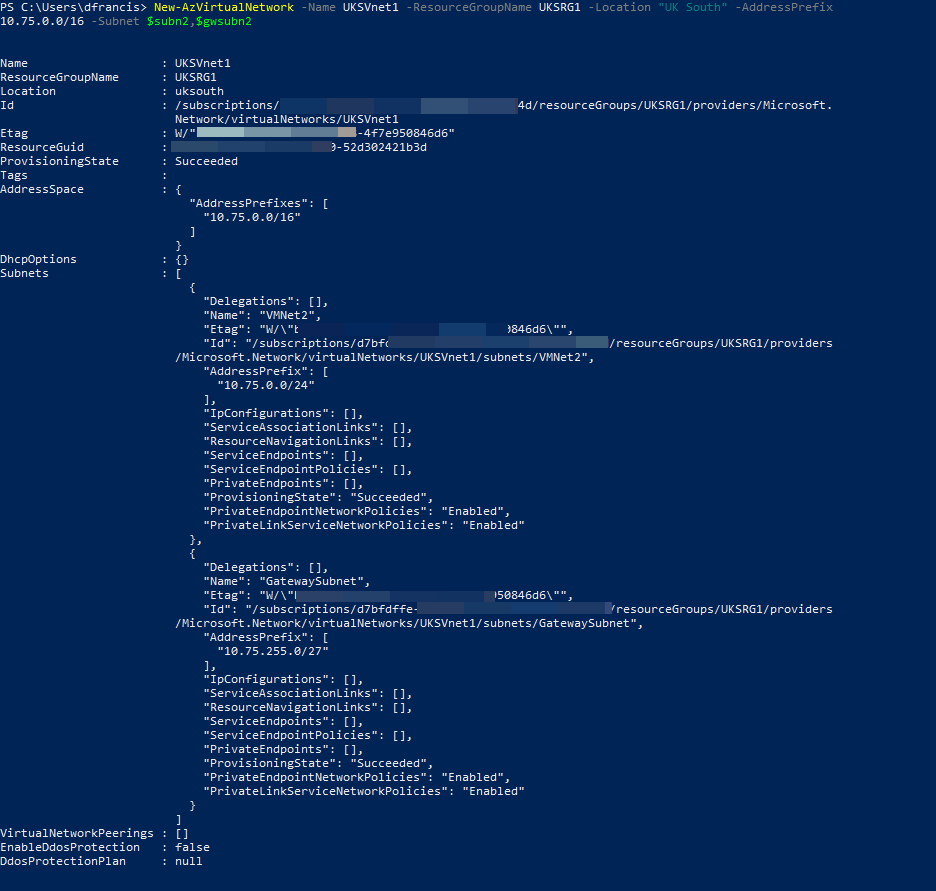
$subn2 = New-AzVirtualNetworkSubnetConfig -Name VMNet2 -AddressPrefix 10.75.0.0/24
$gwsubn2 = New-AzVirtualNetworkSubnetConfig -Name "GatewaySubnet" -AddressPrefix 10.75.255.0/27
2. Then let's create the UKSVnet1 virtual network.
New-AzVirtualNetwork -Name UKSVnet1 -ResourceGroupName UKSRG1 -Location "UK South" -AddressPrefix 10.75.0.0/16 -Subnet $subn2,$gwsubn2
3. We also need a public IP address for the gateway.
$gatewayip2 = New-AzPublicIpAddress -Name UKSVnet1GW1 -ResourceGroupName UKSRG1 -Location "UK South" -AllocationMethod Dynamic
4. Then we need to few more variables for gateway configuration.
$v2 = Get-AzVirtualNetwork -Name UKSVnet1 -ResourceGroupName UKSRG1
$sub2 = Get-AzVirtualNetworkSubnetConfig -Name "GatewaySubnet" -VirtualNetwork $v2
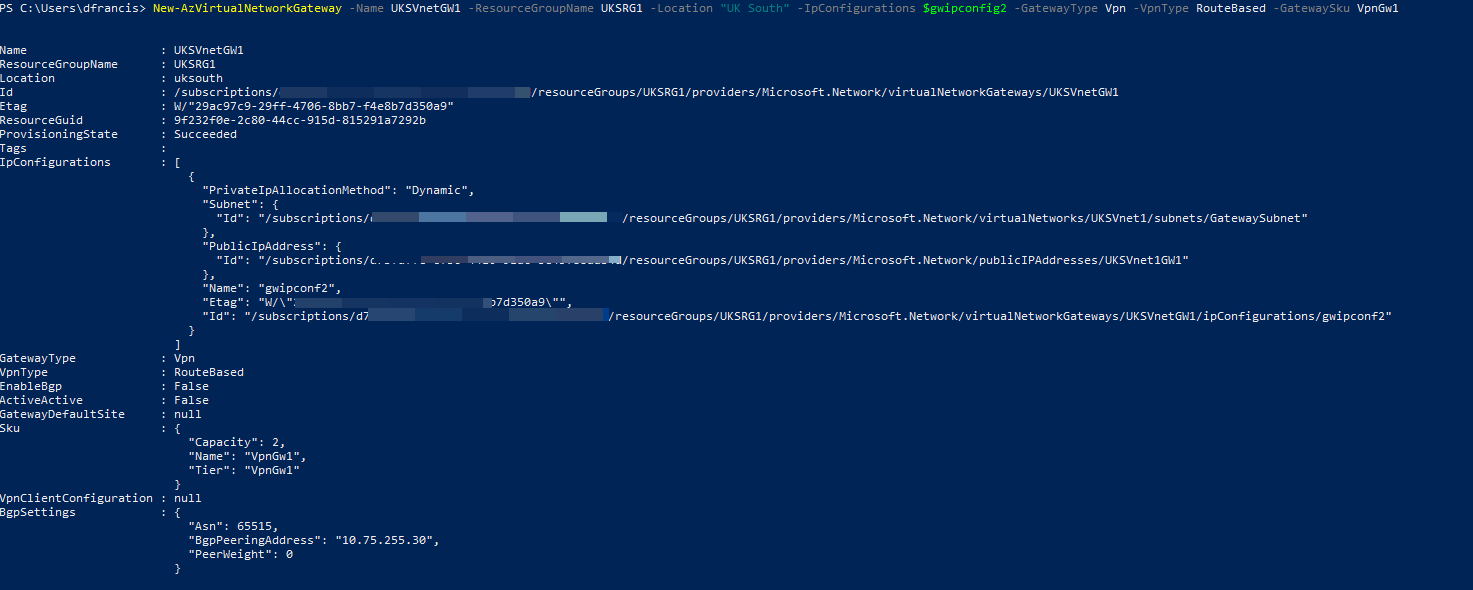
$gwipconfig2 = New-AzVirtualNetworkGatewayIpConfig -Name gwipconf2 -Subnet $sub2 -PublicIpAddress $gatewayip2
5. Finally, we can create the gateway using,
New-AzVirtualNetworkGateway -Name UKSVnetGW1 -ResourceGroupName UKSRG1 -Location "UK South" -IpConfigurations $gwipconfig2 -GatewayType Vpn -VpnType RouteBased -GatewaySku VpnGw1
Establish the Connection
Now we have both gateways ready. The next step is to establish the connection.
1. First, we need to declare some variables.
$EUSgw = Get-AzVirtualNetworkGateway -Name EUSVnetGW1 -ResourceGroupName EUSRG1
$UKSgw = Get-AzVirtualNetworkGateway -Name UKSVnetGW1 -ResourceGroupName UKSRG1
In the above, I am retrieving both gateway details.
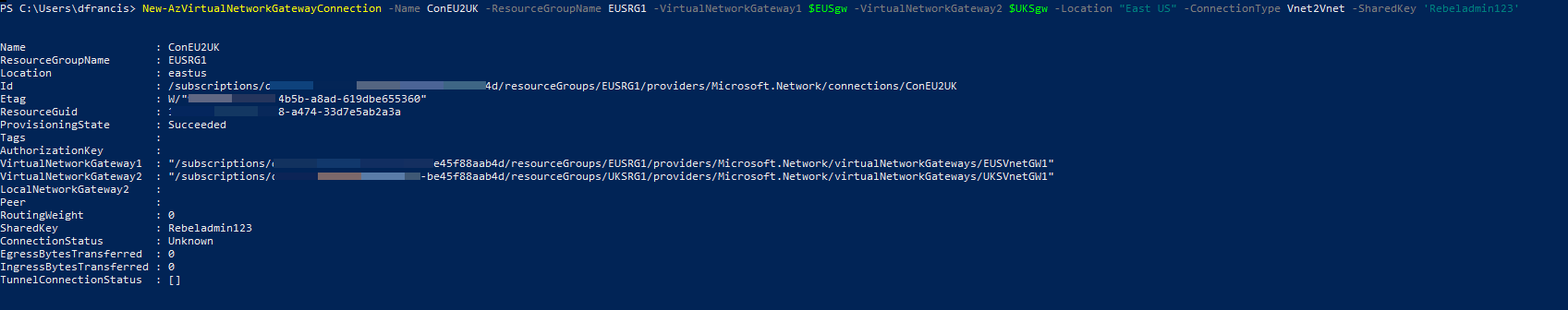
2. Then let's establish a connection from EUSVnet1 to UKSVnet1
New-AzVirtualNetworkGatewayConnection -Name ConEU2UK -ResourceGroupName EUSRG1 -VirtualNetworkGateway1 $EUSgw -VirtualNetworkGateway2 $UKSgw -Location "East US" -ConnectionType Vnet2Vnet -SharedKey 'Rebeladmin123'
In above, I am using the Vnet2Vnet connection type. I am also using pre-shared key 'Rebeladmin123' to establish the connection. This can be changed to a value you required.
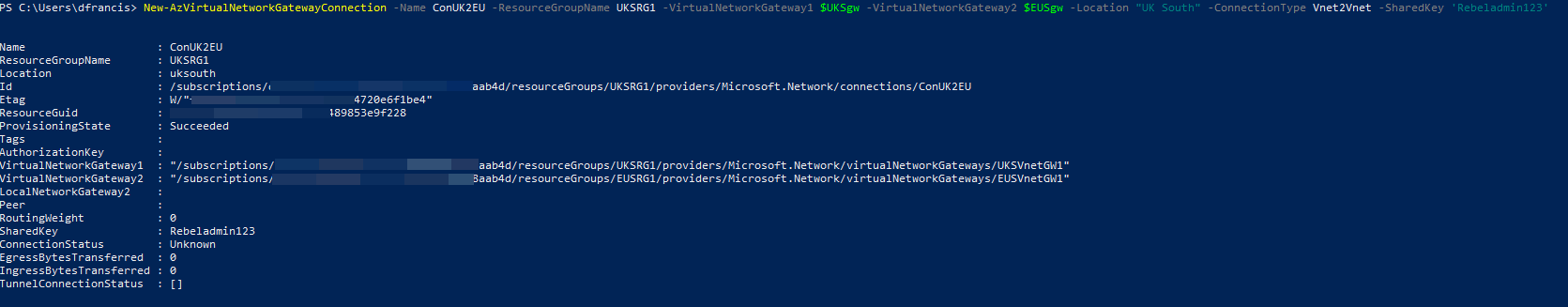
3. In previous step we create a one-way connection. We also need to create a connection from UKSVnet1 to EUSVnet1.
New-AzVirtualNetworkGatewayConnection -Name ConUK2EU -ResourceGroupName UKSRG1 -VirtualNetworkGateway1 $UKSgw -VirtualNetworkGateway2 $EUSgw -Location "UK South" -ConnectionType Vnet2Vnet -SharedKey 'Rebeladmin123'
This completes the connection setup between gateways. The next step is to test the connectivity.
Verify the connectivity
We have completed the hard part. The next step is to verify the connectivity.
1. To verify the connection from EUSVnet1 to UKSVnet1, we can use the following command,
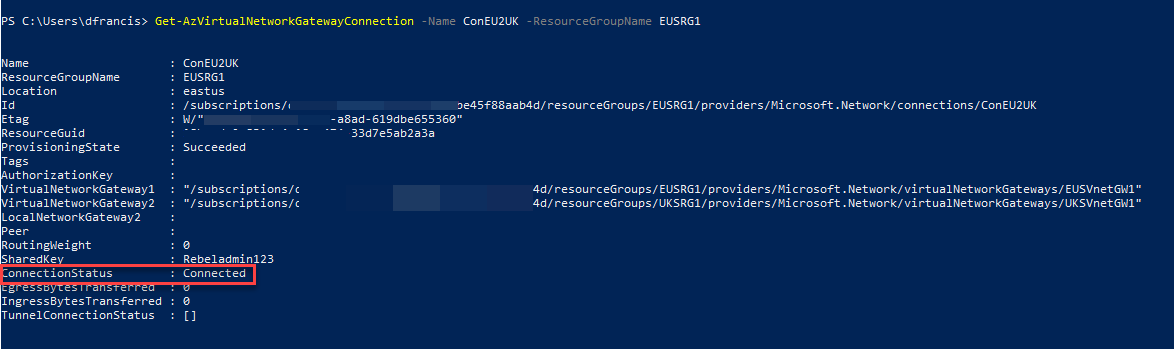
Get-AzVirtualNetworkGatewayConnection -Name ConEU2UK -ResourceGroupName EUSRG1
In the output, we can see the connection status as connected.
2. To verify the connection from UKSVnet1 to EUSVnet1,
Get-AzVirtualNetworkGatewayConnection -Name ConEU2UK -ResourceGroupName EUSRG1
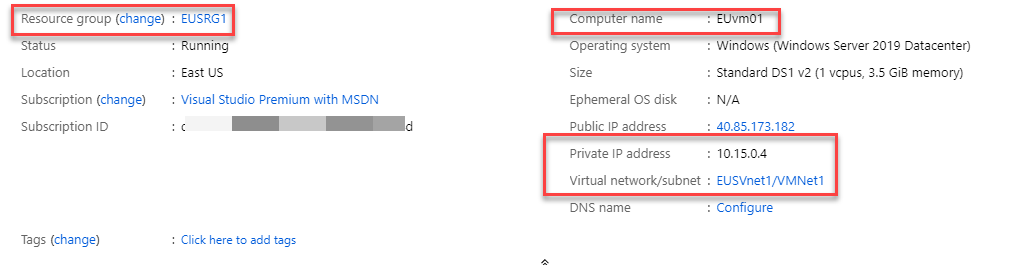
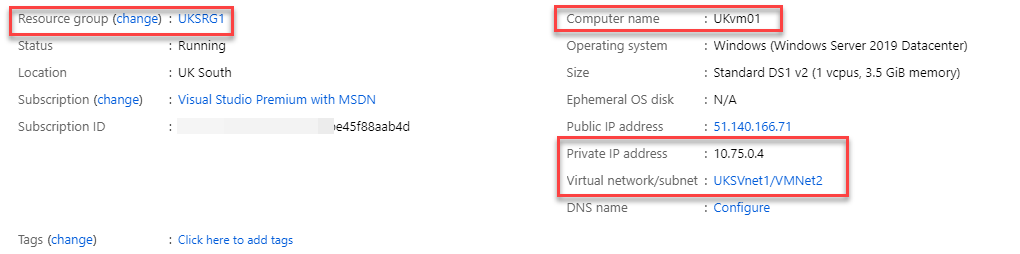
3. I have a virtual machine under each virtual network.
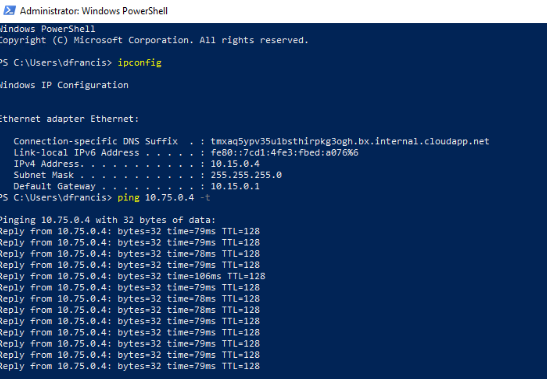
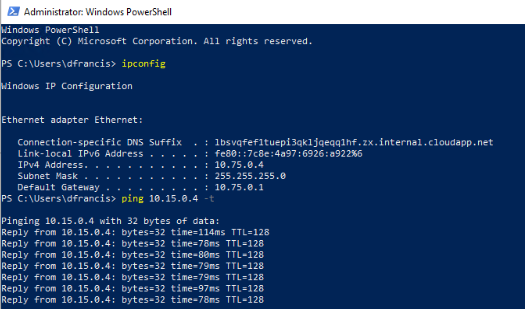
EUvm1 is setup under EUSRG1 resource group & it has private IP address of 10.15.0.4
UKvm01 is setup under UKSRG1 resource group & it has private IP address of 10.75.0.4
Now as expected, I can ping each other.
From EUvm1 to UKvm01
From UKvm01 to EUvm1
As we can see, the connectivity between two virtual networks is working as expected. This marks the end of this blog post. If you have any further questions feel free to contact me on rebeladm@live.com also follow me on twitter @rebeladm to get updates about new blog posts.