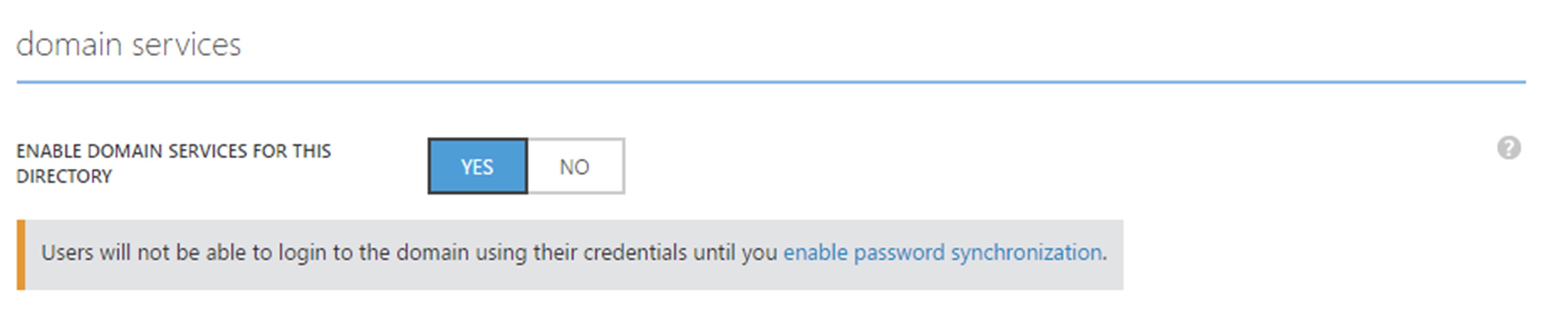
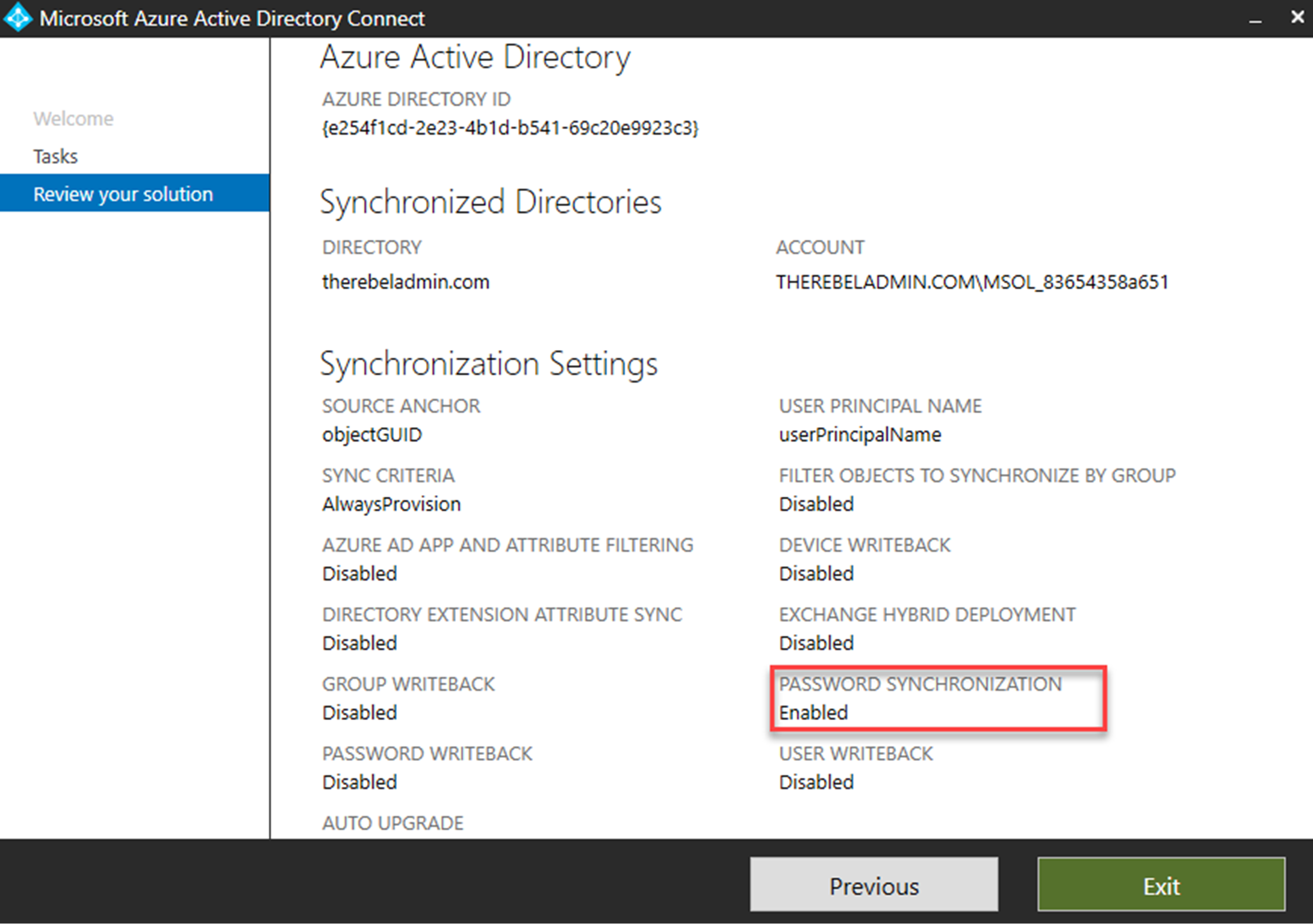
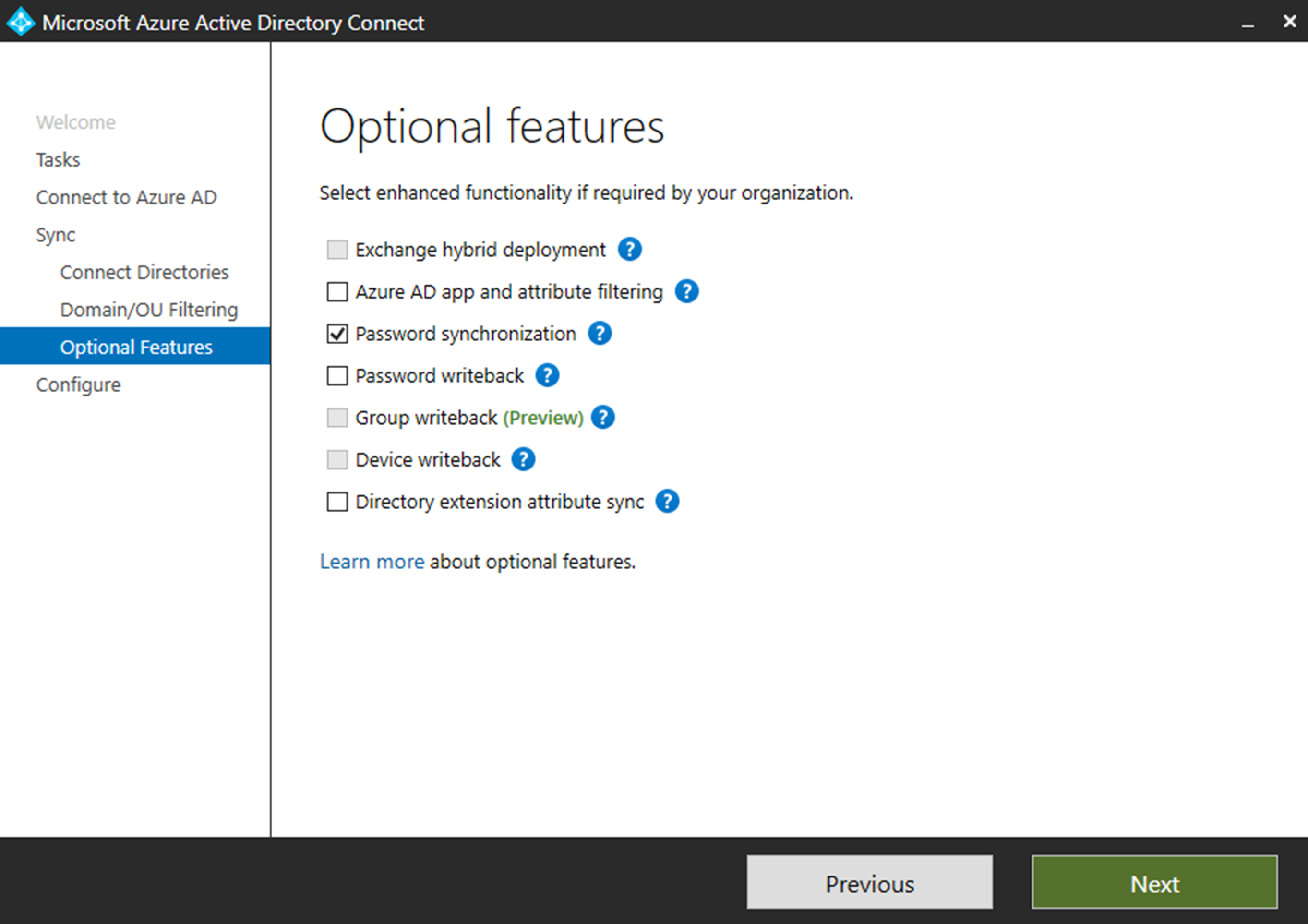
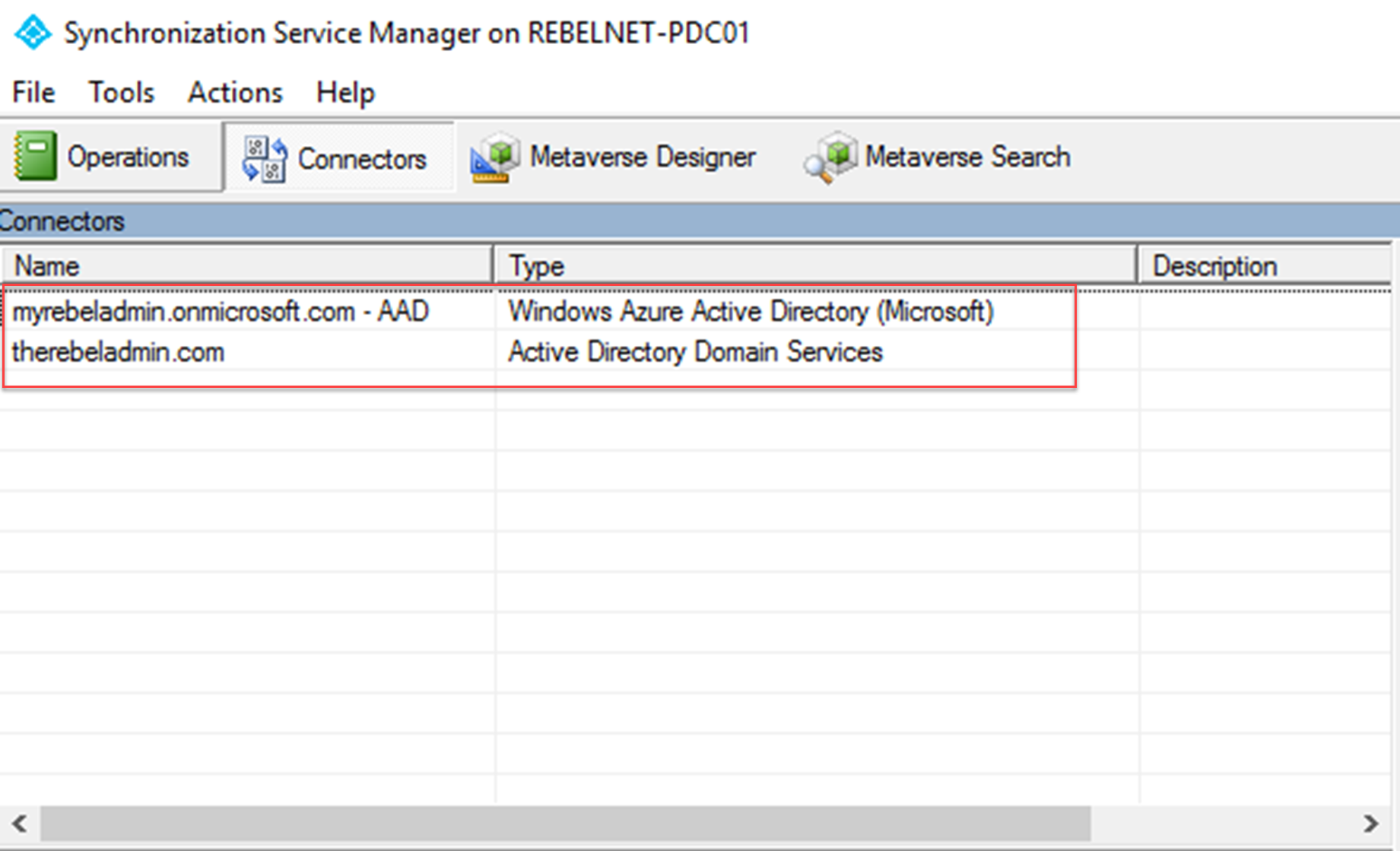
Azure AD Connect allows engineers to sync on-permises AD data to Azure AD. If you use express settings for the AD connect setup, by default it enables the password synchronization as well. This allows users to use same Active Directory password to authenticate in to cloud based workloads. This allow users to use single login details without maintaining different passwords. It simplifies the user’s login experience as well as reduce the helpdesk involvements.
Windows Active Directory uses hash values, which is generated by hash algorithm as passwords. It is not being saved as clear text password and it is impossible to revert it back to a clear text password. There is misunderstanding about this as some people thinks Azure AD password sync uses clear text passwords. In every 2 minutes’ intervals Azure AD connect server retrieves password hashes from on-premises AD and sync it to Azure AD per user-basis in chronological order. This also involves with encryption and decryption process to add extra security to password sync process. In event of password change it will sync to Azure AD in next password sync interval. In healthy environment, maximum delay to update password will be 2 minutes.
If the password was changed while user has open session, it will affect on next Azure authentication attempt. It will not log out the user from existing session. Also, password synchronization doesn’t mean SSO. Users always have to use corporate login details to authenticate to Azure Services. You can find more information about SSO using https://docs.microsoft.com/en-us/azure/active-directory/connect/active-directory-aadconnect-sso
Enable synchronization of NTLM and Kerberos credential hashes to Azure AD
However Azure AD Connect does not synchronize NTLM and Kerberos credential hashes to Azure AD by default. So, if you had Azure AD directory setup and only enabled Azure Domain Services recently make sure you check following,
$adConnector = "<CASE SENSITIVE AD CONNECTOR NAME>" $azureadConnector = "<CASE SENSITIVE AZURE AD CONNECTOR NAME>" Import-Module “C:\Program Files\Microsoft Azure AD Sync\Bin\ADSync\ADSync.psd1” $c = Get-ADSyncConnector -Name $adConnector $p = New-Object Microsoft.IdentityManagement.PowerShell.ObjectModel.ConfigurationParameter "Microsoft.Synchronize.ForceFullPasswordSync", String, ConnectorGlobal, $null, $null, $null$p.Value = 1 $c.GlobalParameters.Remove($p.Name) $c.GlobalParameters.Add($p) $c = Add-ADSyncConnector -Connector $c Set-ADSyncAADPasswordSyncConfiguration -SourceConnector $adConnector -TargetConnector $azureadConnector -Enable $false Set-ADSyncAADPasswordSyncConfiguration -SourceConnector $adConnector -TargetConnector $azureadConnector -Enable $true