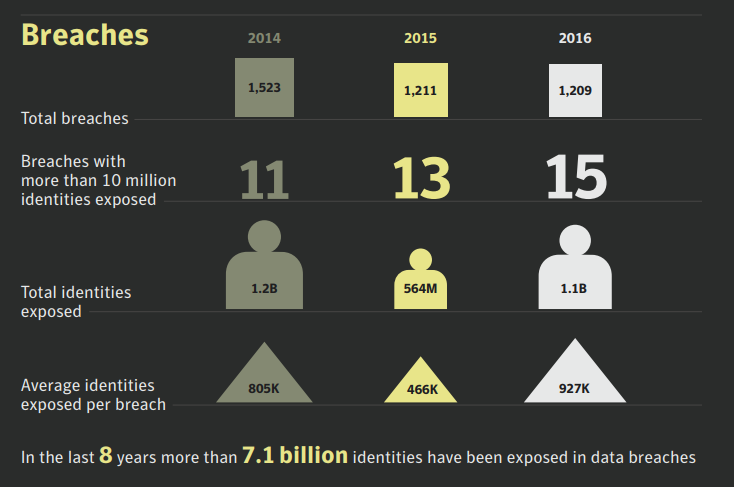
Symantec released their latest Internet Security Threat Report in early June. This report includes data about infrastructure threats for year 2016. It says, for year 2016, near 1.1 billion identities has been exposed. Also for last 8 years total identity breach is around 7.1 billion which is almost equal to total world population.
In Identity infrastructure breach, most of the time advisories get in to the system using a legitimate user name and password belong to an identity in that infrastructure. This initial breach can be result of malware, phishing or pass-the-hash attack. If it’s a “privileged” account, it makes easier for advisories to gain control over identity infrastructure. But it’s not always a must. All they need is some sort of a breach. Latest reports show after an initial breach it only takes less than 48 hours to gain full control over identity infrastructure.
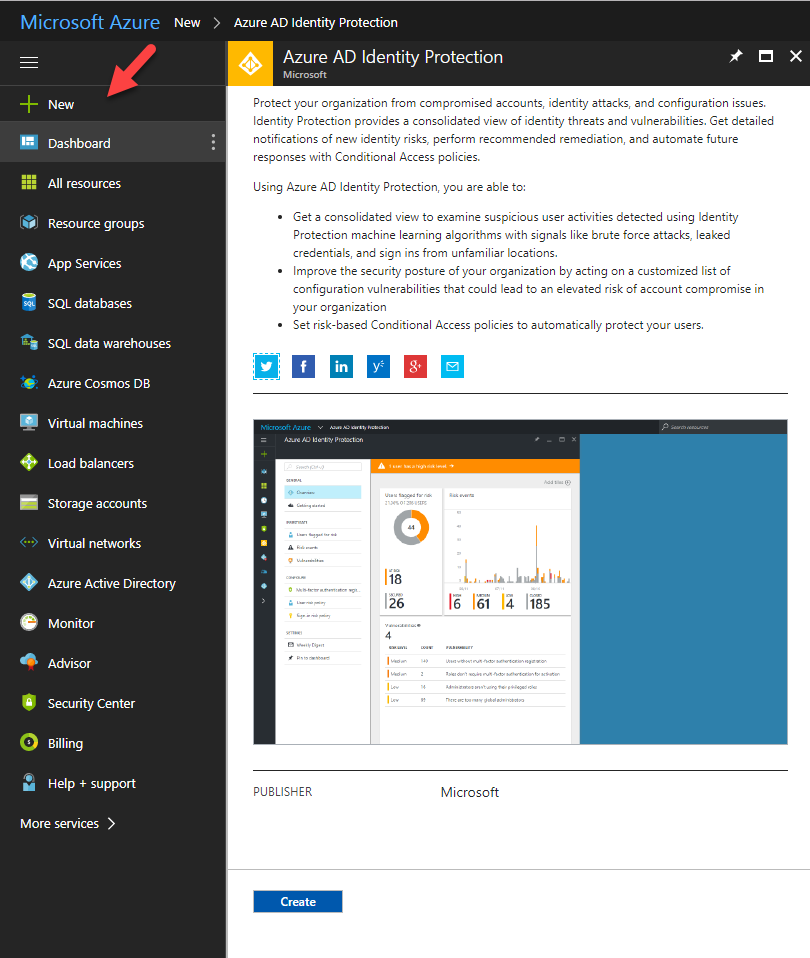
When we look in to it from identity infrastructure end, if someone provides a legitimate user name and password it allows access to the system. This can be from the user or an advisory. But by default, system will not know that. In local AD infrastructure, solutions like Microsoft Advanced Threat Analytics, Microsoft Identity Management helps to identify and prevent inauthentic use of identities. Azure Active Directory Identity Protection is a feature comes with Azure AD Premium, which can use to protect your workloads from inauthentic use of cloud identities. It mainly has following benefits.
• Detect vulnerabilities which affect the cloud identities using adaptive machine learning algorithms and heuristics.
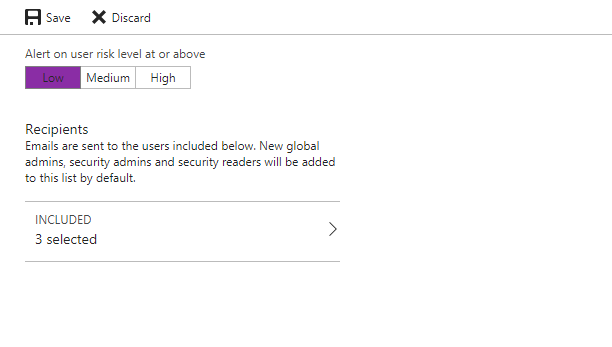
• Issue alerts and reports to detect/identify potential identity threats and allow administrators to take actions accordingly.
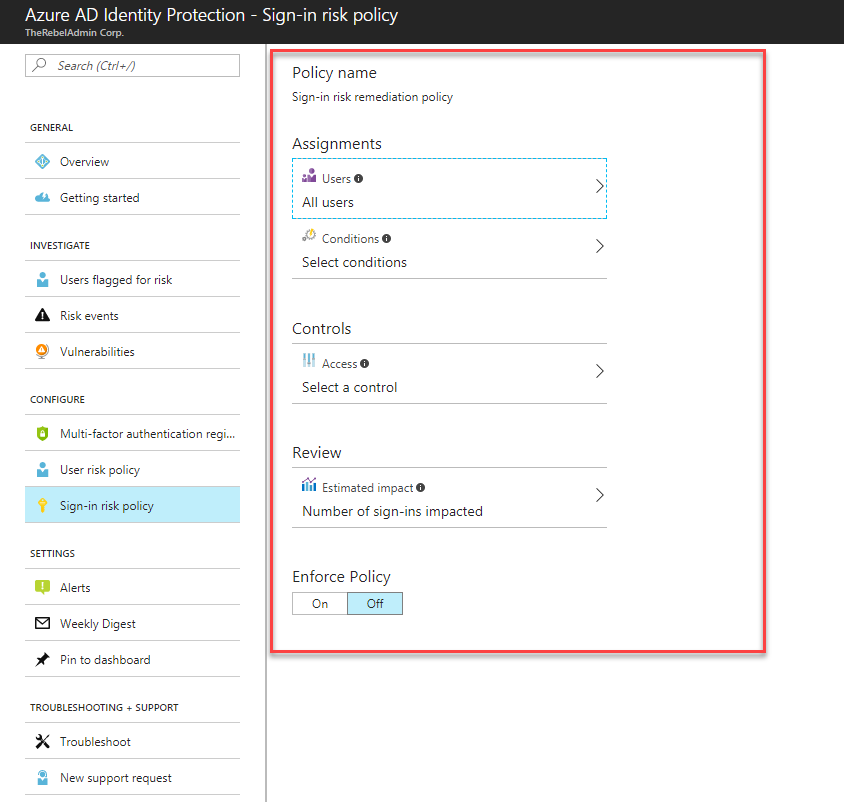
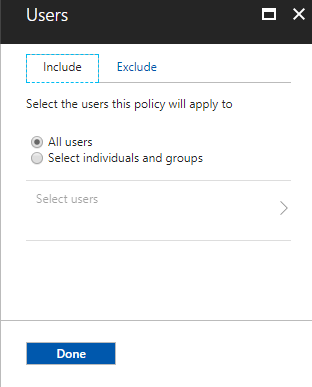
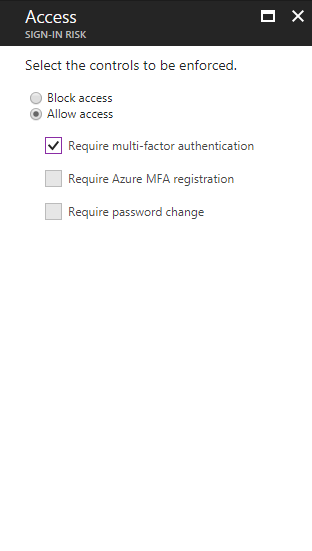
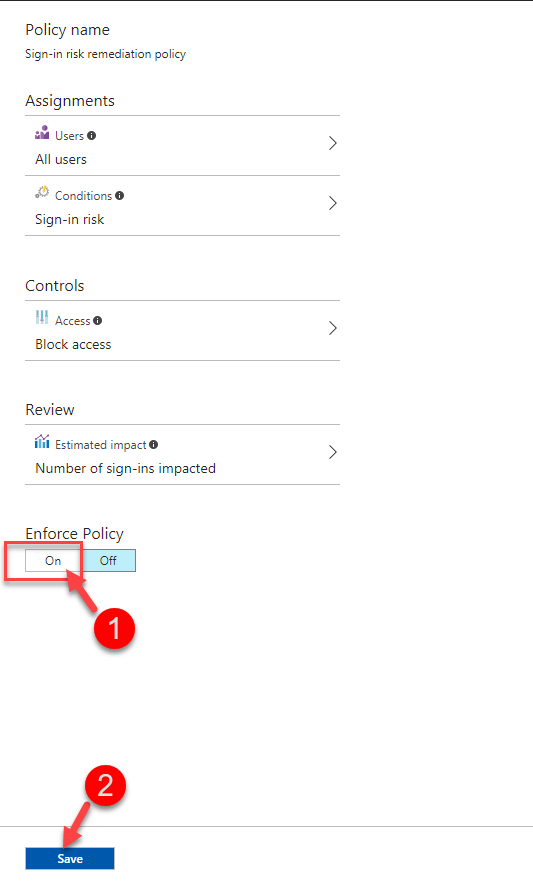
• Based on policies, force automated actions such as Block Access, MFA authentication or Password reset when it detects a suspicious login attempt.
According to Microsoft https://docs.microsoft.com/en-us/azure/active-directory/active-directory-identityprotection Azure AD Identity protection has following capabilities.
Detecting vulnerabilities and risky accounts:
• Providing custom recommendations to improve overall security posture by highlighting vulnerabilities
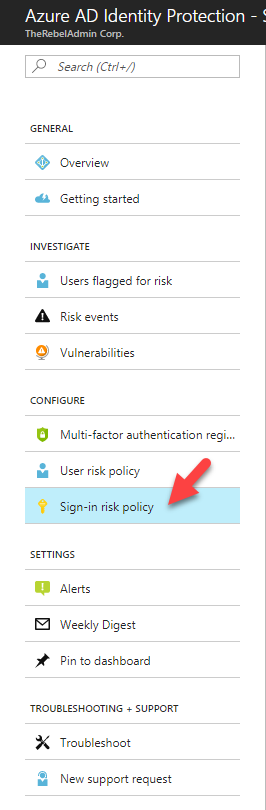
• Calculating sign-in risk levels
• Calculating user risk levels
Investigating risk events:
• Sending notifications for risk events
• Investigating risk events using relevant and contextual information
• Providing basic workflows to track investigations
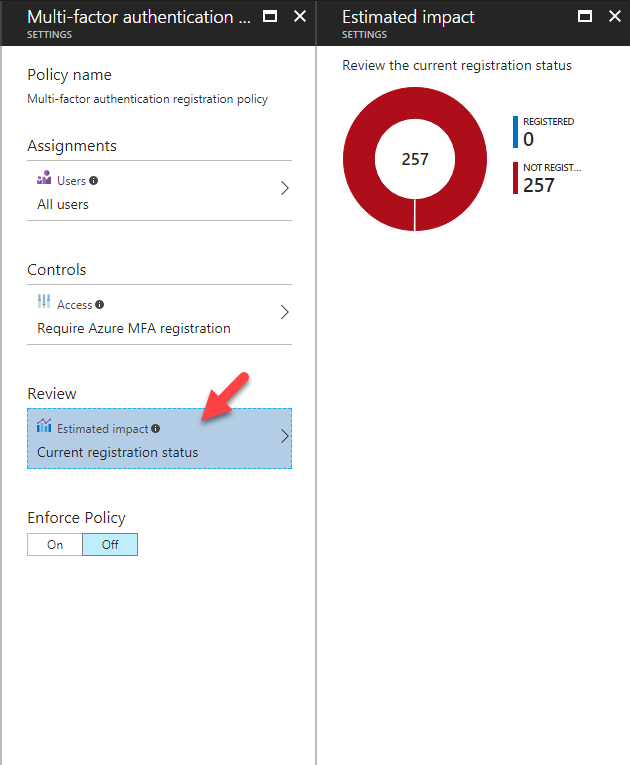
• Providing easy access to remediation actions such as password reset
Risk-based conditional access policies:
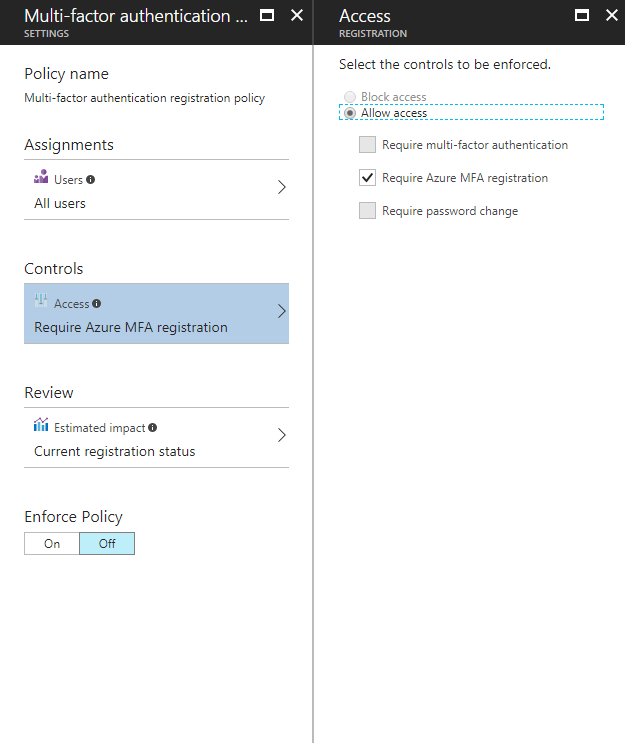
• Policy to mitigate risky sign-ins by blocking sign-ins or requiring multi-factor authentication challenges.
• Policy to block or secure risky user accounts
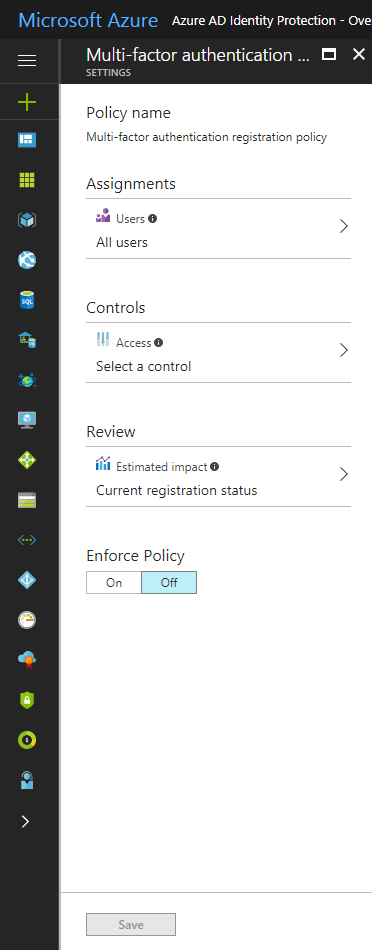
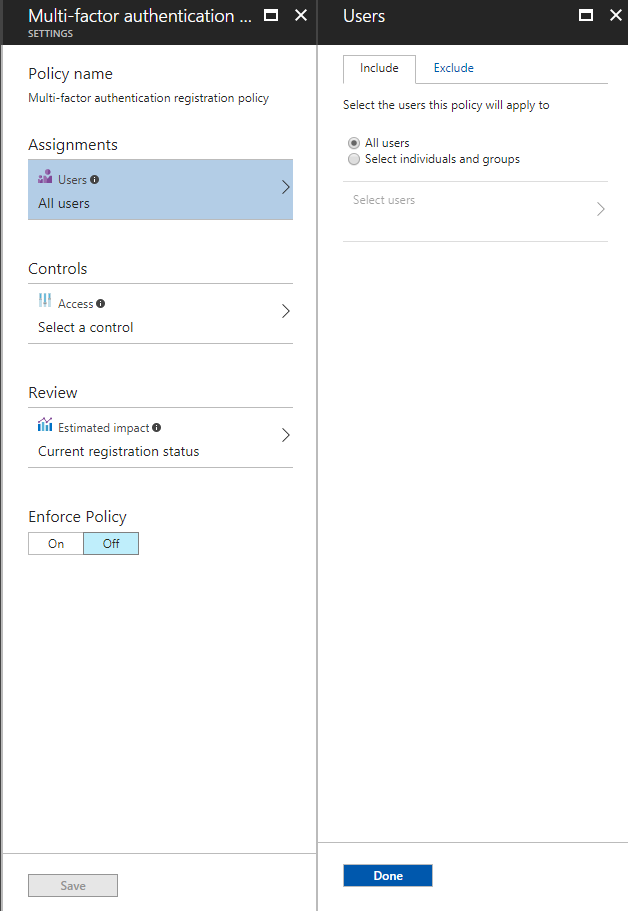
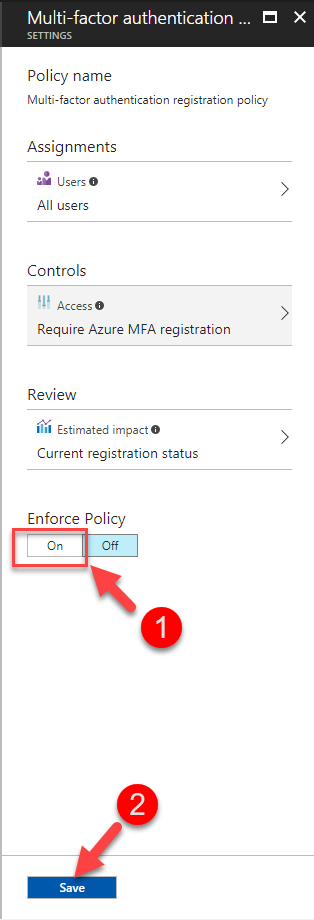
• Policy to require users to register for multi-factor authentication
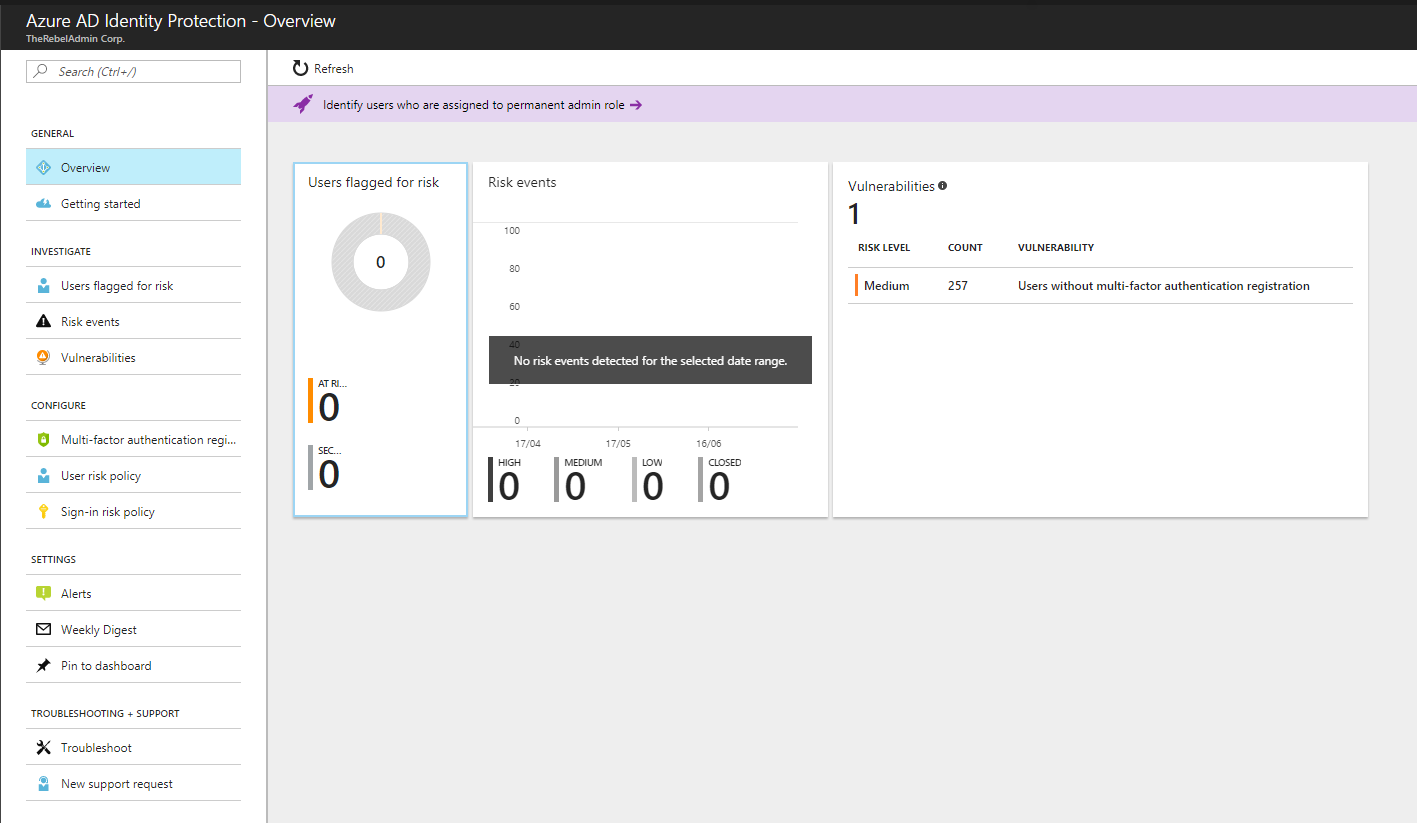
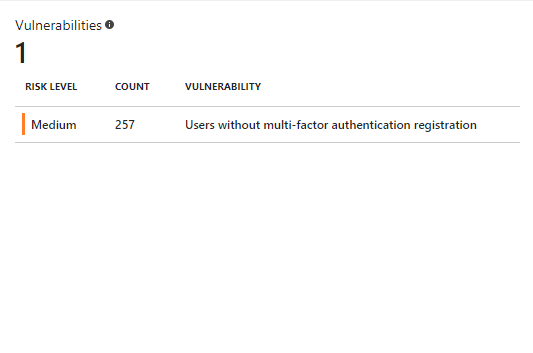
Azure Active Directory Identity Protection detect and report following as vulnerabilities,
• User logins without Multi-Factor Authentication
• Use of unmanaged cloud apps – These are the applications which is not managed using Azure Active Directory.
• Risk events detect by Azure Privileged Identity Management – This is another additional service which can use to manage and monitor privileged accounts associated with Azure Active Directory, Office 365, EMS etc.
More info about these events can find on here