In an active directory infrastructure, we use group policies to push security settings and other computer configuration from central location. It can be apply for computer level or user level. In an organization it’s important to maintain proper design on group policies and its hierarchy as complexity, applying order can cause issues on network.
This is very important when you deals with multi-site environment. Because these group policies can be bottleneck to the bandwidth usage between remote sites to the main site. This is something most administrators do not pay attention. I agree it’s depend on the group policies and its use, but for ex- let’s assume we have 10 group policies from to apply users in remote site. The link between locations are 512kb, just imagine if 100 workstations log on in morning and initiate these group policies how much bandwidth will use? Also what about a user logs from remote location? Can we expect they always get good speed?
Well, Microsoft have an answer for this. Before apply group policies to a workstation it check for the connection speed from distributing server to workstation, by default any link speed below 500kbps Microsoft take as Slow-Link. Once it’s detected a slow-link, it will automatically block some of the group policies. So if you having issues with getting all the group policies on workstation on remote location (can be even in local network if NIC are maxed out due to its activities or virus) this is one place to check.
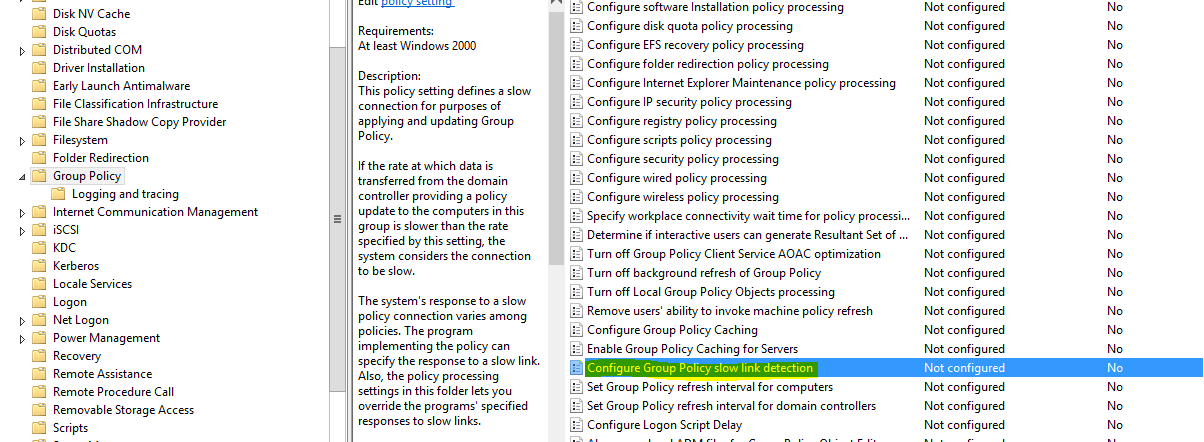
Here is list of components will process and will not process in slow-link detection.
|
Component |
Pushed |
|
Administrative Templates |
Yes |
|
Group Policy Preferences |
Yes |
|
Security |
Yes |
|
802.3 Group Policy |
Yes |
|
EFS |
Yes |
|
IE maintenance |
Yes |
|
Internet Explorer Zone Mapping |
Yes |
|
IP Security |
Yes |
|
QoS Packet Scheduler |
Yes |
|
Microsoft Offline Files |
Yes |
|
Software Restriction Policies |
Yes |
|
Windows Search |
Yes |
|
Wireless |
Yes |
|
Deployed Printer Connections |
No |
|
Disk Quotas |
No |
|
Folder Redirection |
No |
|
Scripts |
No |
|
Software Installation |
No |
How to change this default limit?
We can change the default limit as per our infrastructure needs. To do this,
Log in to the DC server as the domain admin or enterprise admin.
Then Server Manager > Tools > Group Policy Management
Then go to the relevant policy and right click on and edit.
This setting can be change on computer configuration level or user configuration level. Both are located in same path. Policies\Administrative Templates\System\Group Policy
In here there is option called, configure group policy slow link detection
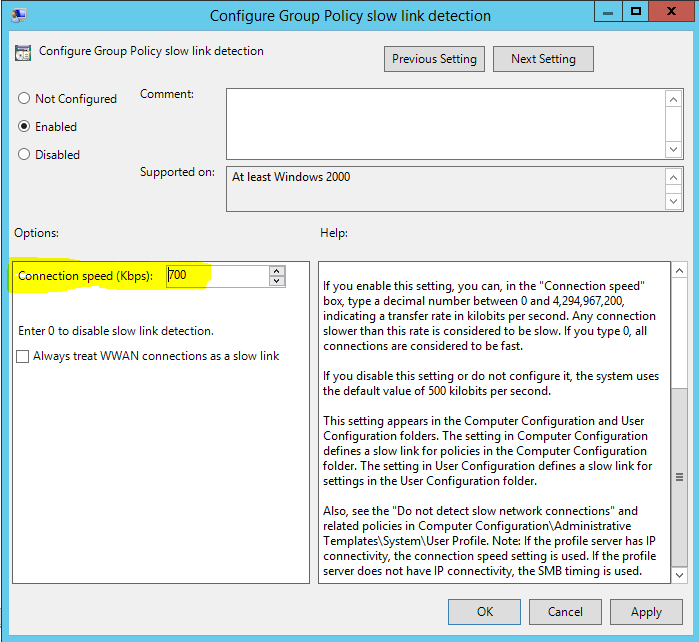
Double click on it to change. By default it is in not configure status. Even if you disable this or not configure it, system still detects any link below 500kbps as slow-link.
Once it is enabled, you can set speeds in kbps (kilobyte per second).
If you set speed to 0 it will disable this feature. Also we can force system to think all WWAN connections as slow links.
If you have any question about the post feel free to contact me on rebeladm@live.com