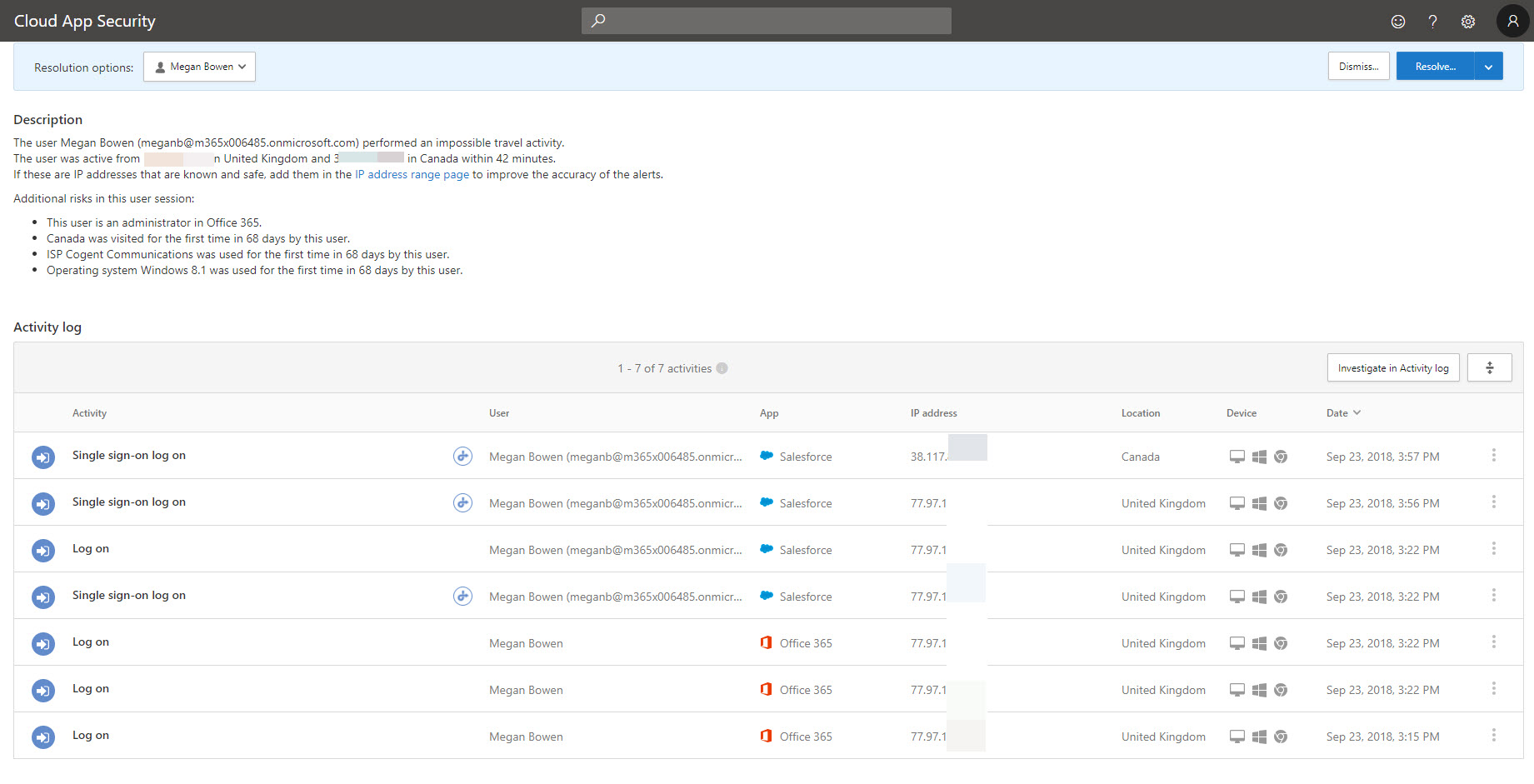
Let’s assume one of user in your sales team log in to https://myapps.microsoft.com and launch salesforce app successfully from his office in UK. Few minutes later the same user made successful login from Canada. Unless user is using remote connection, it is not impossible. Still someone can’t travel that fast ?. Azure Active Directory capable of detect this type of impossible sign-in activities. However, detection type for this kind of activities is “offline”. Which means reporting latency for these alerts are between 2 to 4 hours.
Azure cloud app security also capable of detecting these types of activities but it is real-time as it detects activities based on sessions. It helps administrators to react faster and protect infrastructure from potential breach. In this demo, I am going to demonstrate how to fine tune built in azure cloud app security policy for Impossible travel activity and prevent breach.
Before we start, first we need to integrate SaaS app with cloud app security. In my previous post I demonstrate how to do that. So please go ahead and read it on http://www.rebeladmin.com/2018/09/step-step-guide-block-data-download-using-azure-cloud-app-security/
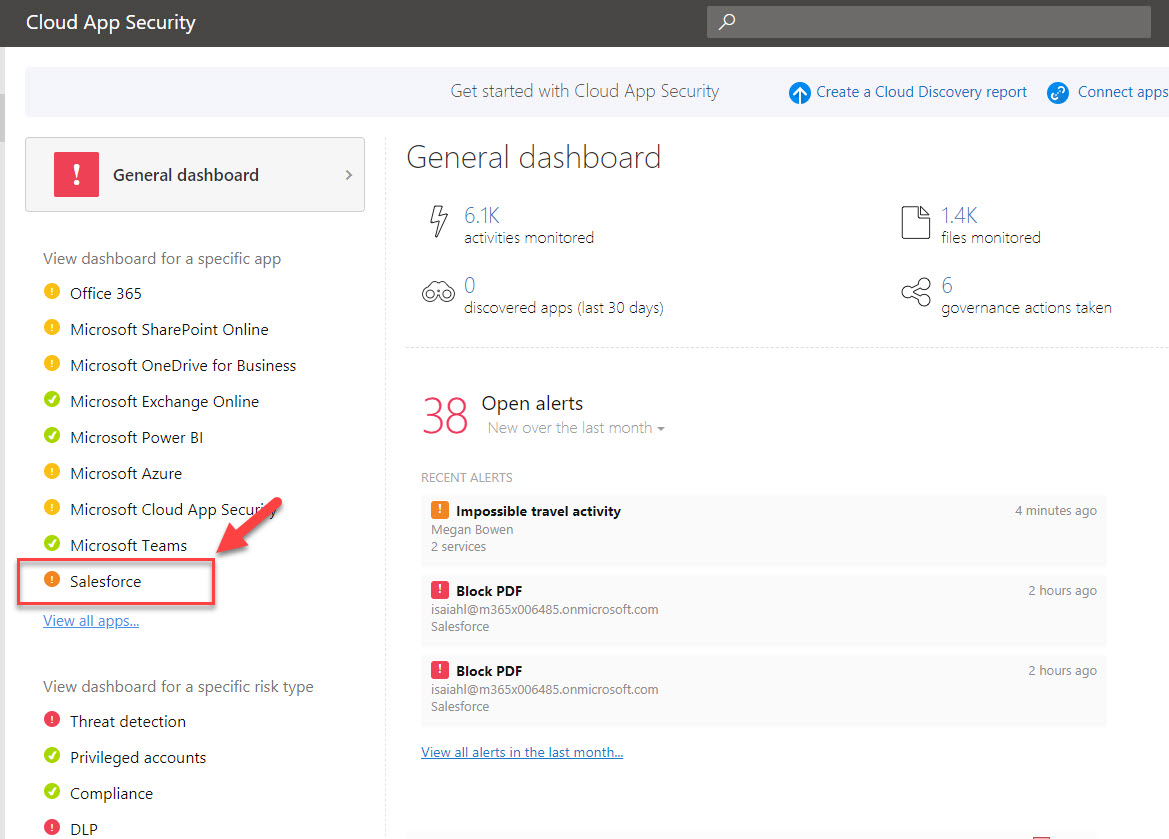
In my demo I am using salesforce app.
1. Once integration is done, log in to https://portal.cloudappsecurity.com as global administrator.
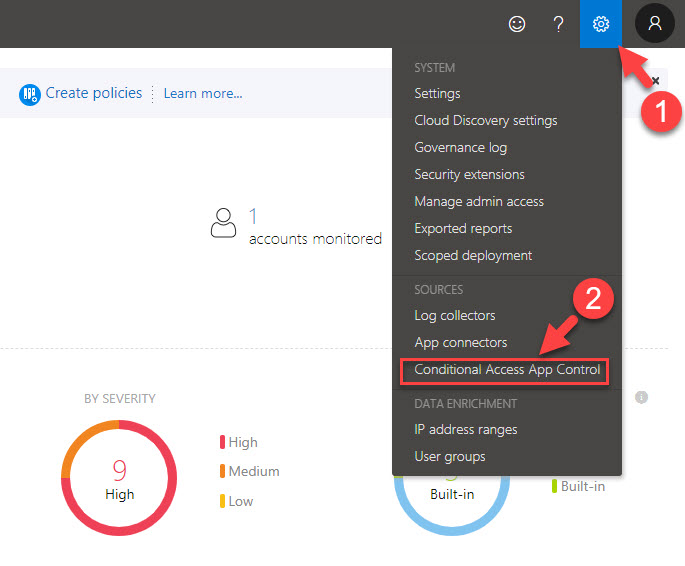
2. Then go to Settings | Conditional access app control
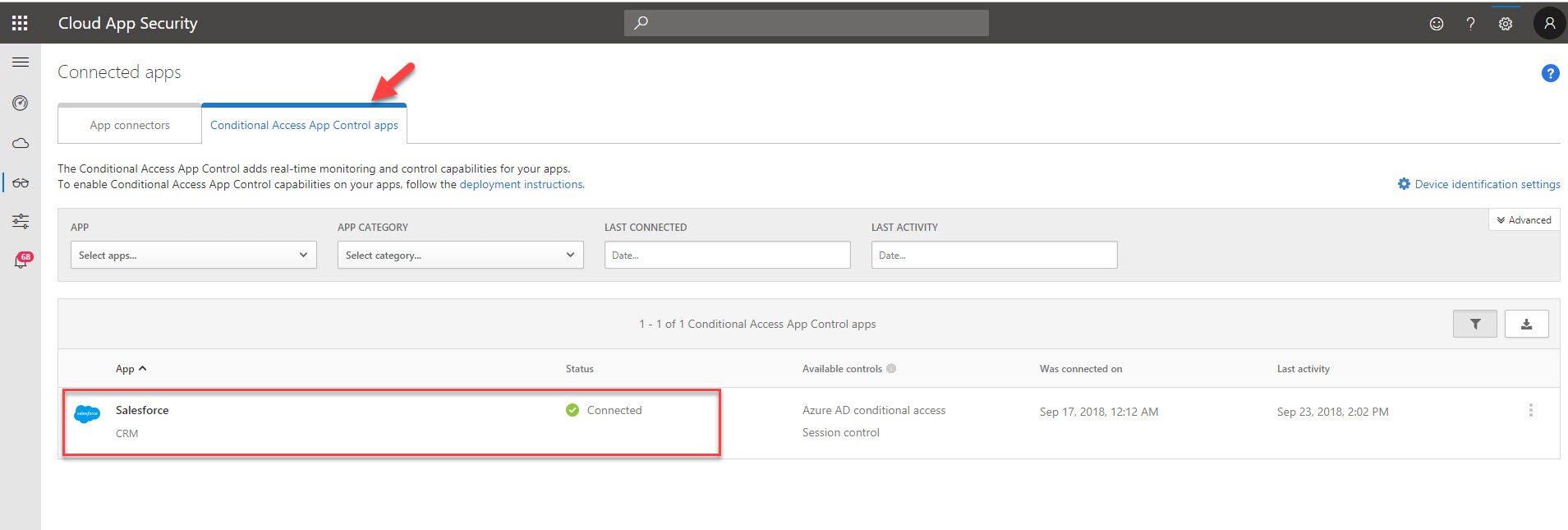
3. There you should be able to see your app under Conditional access app control tab. It should be in healthy connected status.
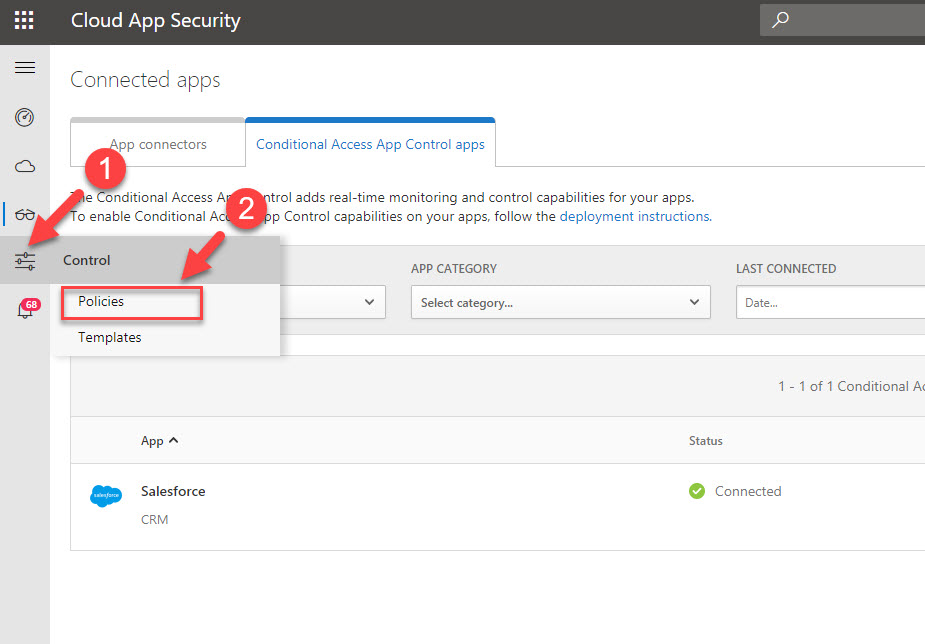
4. Then click on Control | Policies
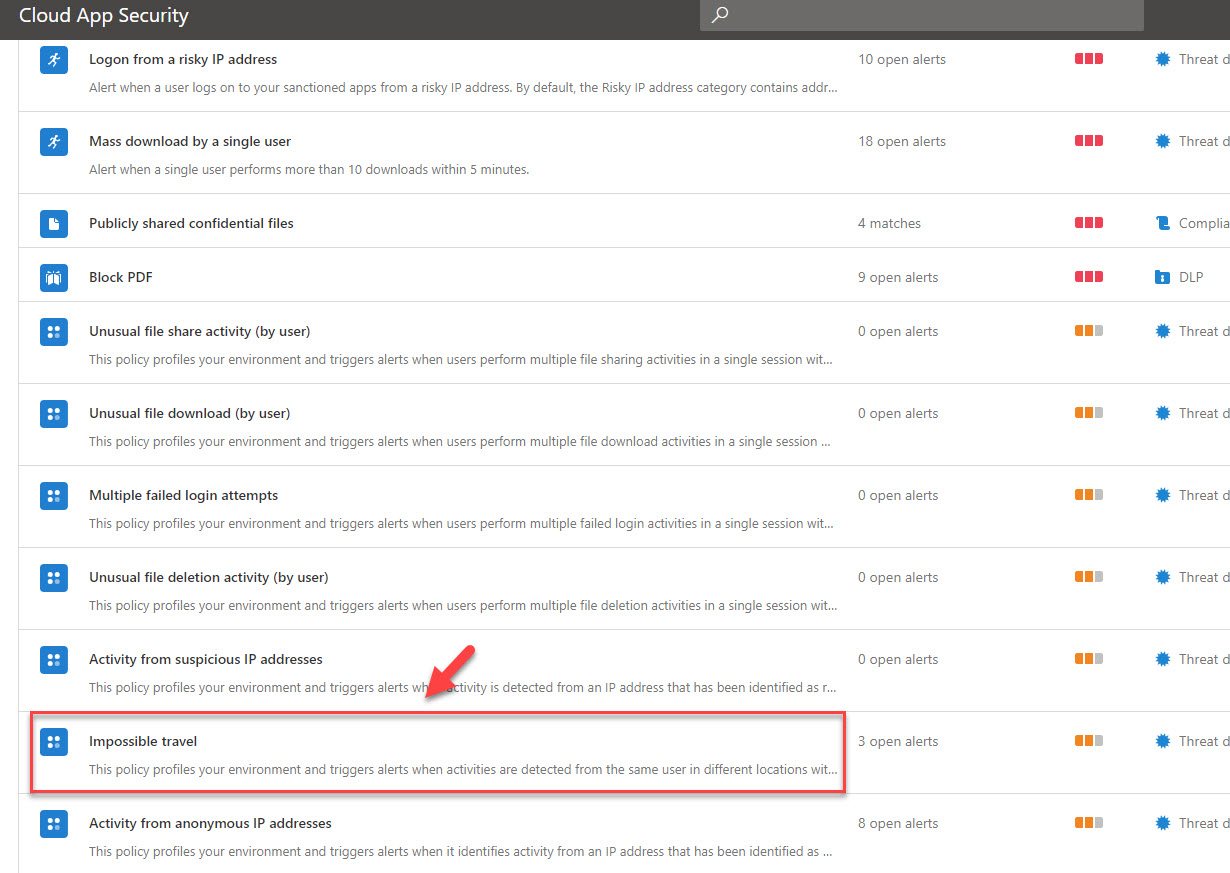
5. Under policies, click on impossible travel policy
6. This is a built-in policy. as you can see it doesn’t have any actions attached to it. if CAS detect such activity, it will still be reported under CAS dashboards.
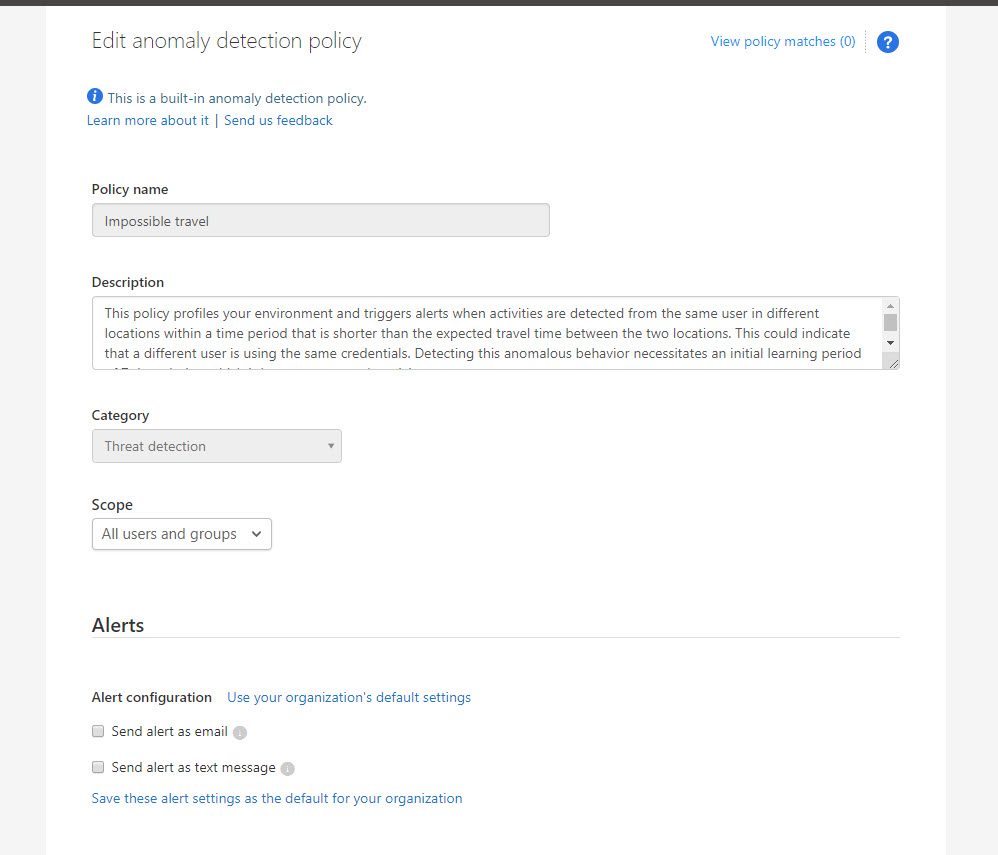
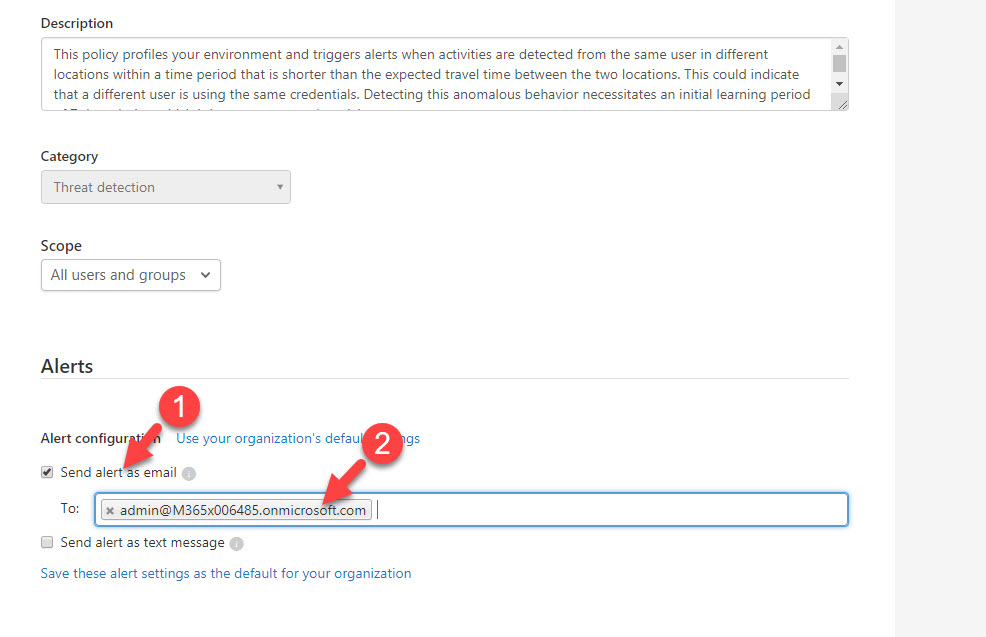
7. In my environment, I like to get an alert if its detect such activity. To do that, click on Send alert as email option under Alerts. Then define email address in text box.
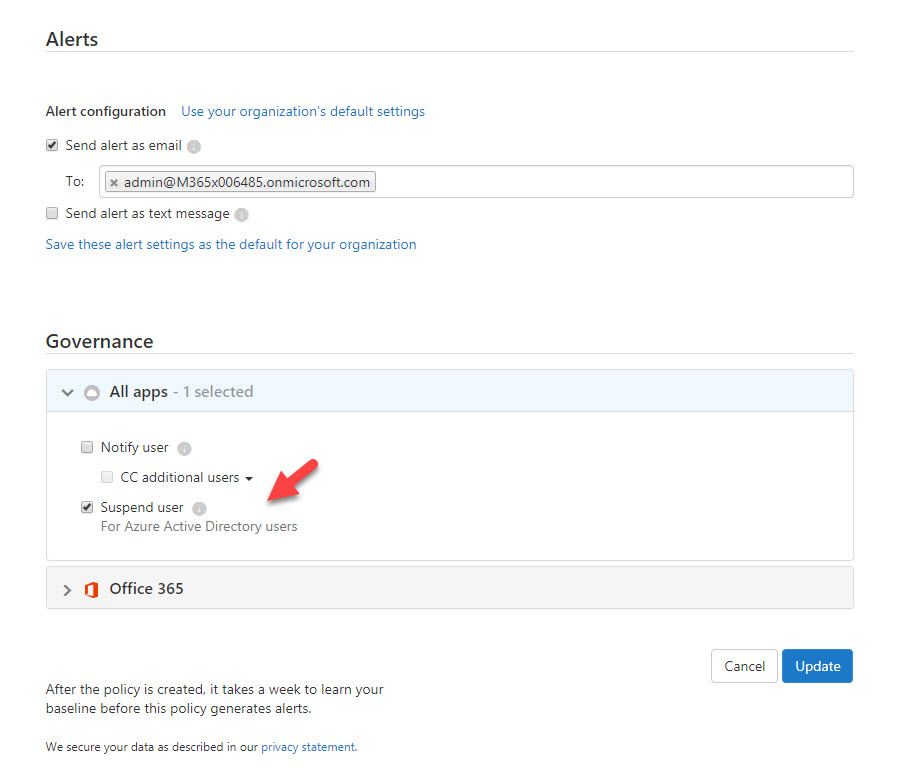
8. I also like to suspend the user account, so it gives my team enough time to review the alert and do the necessary adjustments. To do that, click on All apps under Governance and click on Suspend user check box.
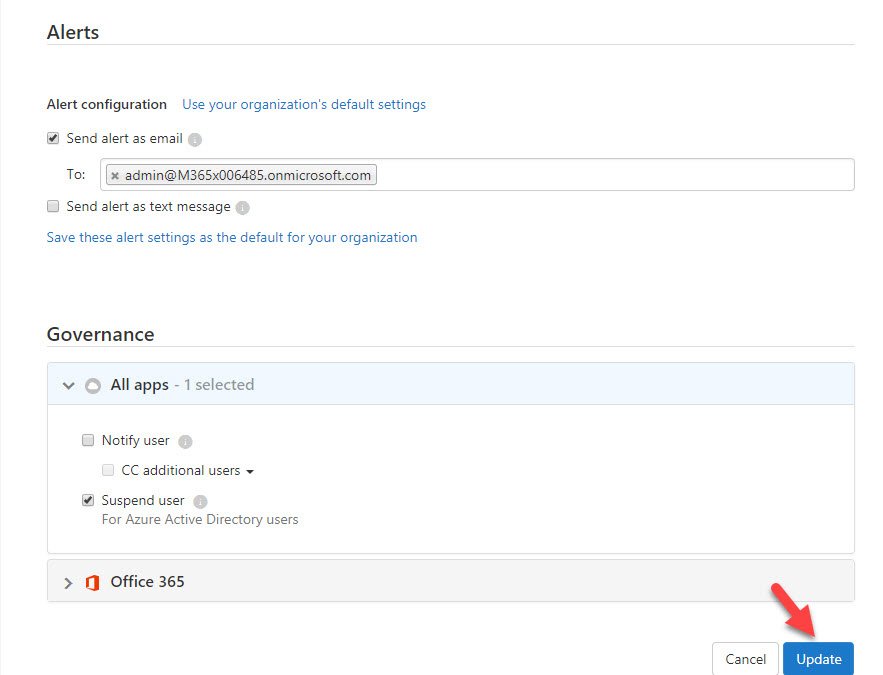
9. To complete the action, click on Update.
10. Policy is updated now. For testing I am login from two VMs located on two different locations.
11. Once the login is done, I came back to https://portal.cloudappsecurity.com. Then click on Salesforce app.
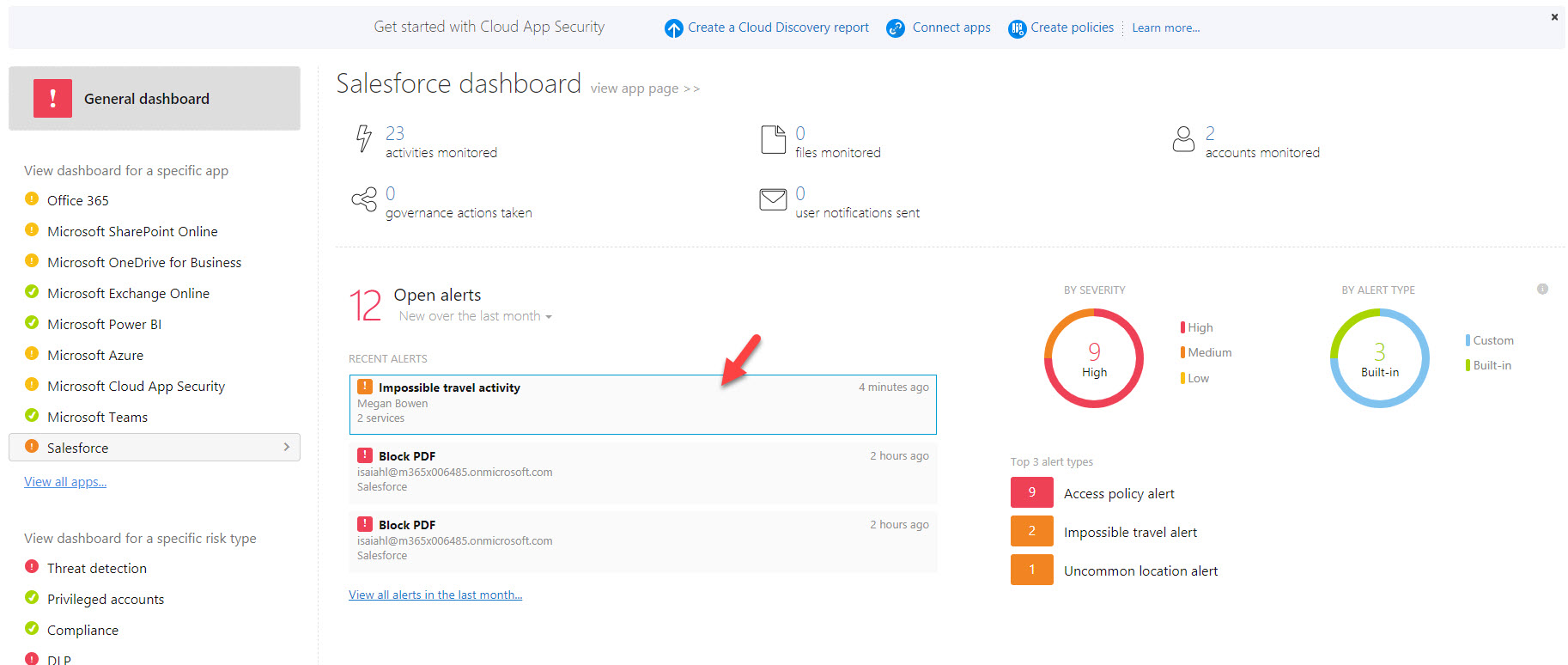
12. Under the alerts I can see it detected impossible travel activity. Click on it to view more details.
13. In there we can see in-details error description & activity log.
14. According to policy, I also should get email alert. When I log in to email I can see email alert for the activity as expected.
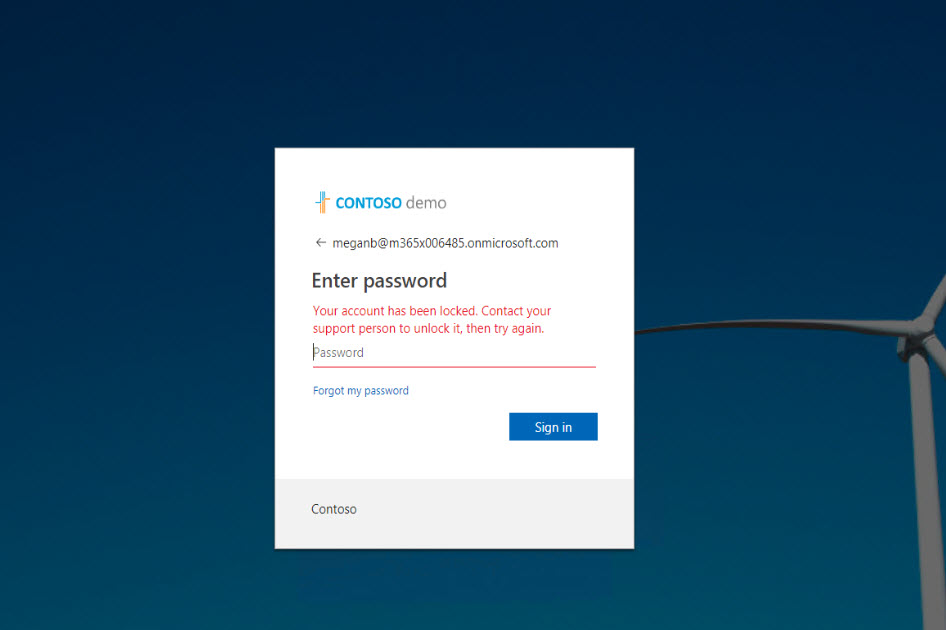
15. According to policy it also should suspend the user account. When I try to login again as the same user I got following account lock out error.
Cool ha? As expected policy detects the activities in real-time and take necessary actions as defined.
This marks the end of this blog post. If you have any further questions feel free to contact me on rebeladm@live.com also follow me on twitter @rebeladm to get updates about new blog posts.




I am currently using the impossible travel alert for Office 365 logins. However, the alert goes off even if the login from an impossible travel location was unsuccessful.
This has made this alert useless because these unsuccessful logins are happening all the time as bots and bad actors are constantly trying to log in to my users accounts.
Is there a way to set the alert to only kick off if the login was successful?
Thanks,
Paul
This is also detecting account login via VPN in different location. How can we exclude that ?
also, failed logins are also coming as alert. can we exclude them to reduce number of false positive.