In previous posts on PKI blog series we learned about theory part of PKI. If you didn’t read those yet, please go ahead and read those before start on deployment part.
How PKI Works? – http://www.rebeladmin.com/2018/05/how-pki-works/
Active directory certificate service components – http://www.rebeladmin.com/2018/05/active-directory-certificate-service-components/
PKI Deployment Models – http://www.rebeladmin.com/2018/05/pki-deployment-models/
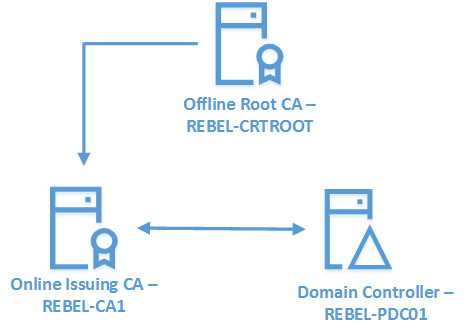
In this post I am going to demonstrate how we can setup PKI using Two-Tier model. I have use this model as it is the recommended model for mid and large organizations.
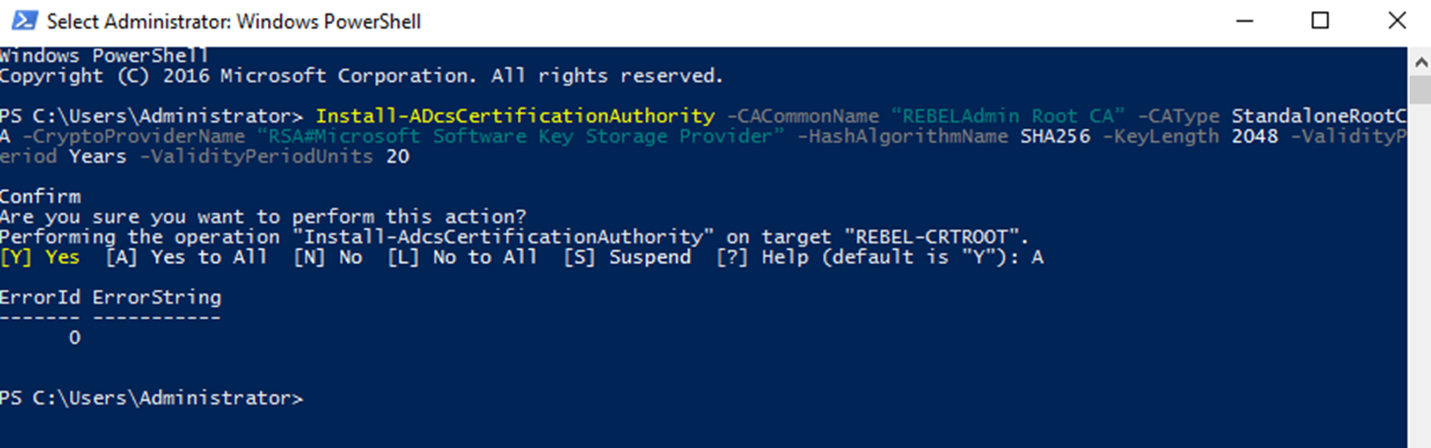
Add-WindowsFeature ADCS-Cert-Authority -IncludeManagementToolsInstall-ADcsCertificationAuthority -CACommonName “REBELAdmin Root CA” -CAType StandaloneRootCA -CryptoProviderName “RSA#Microsoft Software Key Storage Provider” -HashAlgorithmName SHA256 -KeyLength 2048 -ValidityPeriod Years -ValidityPeriodUnits 20certutil.exe –setreg ca\DSConfigDN CN=Configuration,DC=rebeladmin,DC=comInstall-WindowsFeature Web-WebServer -IncludeManagementToolsmkdir C:\CertEnroll
New-smbshare -name CertEnroll C:\CertEnroll -FullAccess SYSTEM,"rebeladmin\Domain Admins" -ChangeAccess "rebeladmin\Cert Publishers"certutil -setreg CA\CRLPublicationURLs "1:C:\Windows\system32\CertSrv\CertEnroll\%3%8%9.crl \n10:ldap:///CN=%7%8,CN=%2,CN=CDP,CN=Public Key Services,CN=Services,%6%10\n2:http://crt.rebeladmin.com/CertEnroll/%3%8%9.crl"|
Option |
Details |
|
0 |
No Changes |
|
1 |
Publish CRL to the given location |
|
2 |
Attach CDP extensions of issued certificates |
|
4 |
Include in CRL to find the delta CRL locations |
|
8 |
Specify if need to publish all CRL info to AD when publishing manually |
|
64 |
Delta CRL location |
|
128 |
Include IDP extension of issued CRL |
All these settings also can specify using GUI. In order to access it, got to Server Manager > Tools > Certificate Authority > Right click and select properties of the server > Go to the Extension Tab
There you can add all the above using GUI.
|
Variable |
GUI Reference |
Details |
|
%1 |
<ServerDNSName> |
DNS Name of the CA server |
|
%2 |
<ServerShortName> |
NetBIOS name of the CA server |
|
%3 |
<CAName> |
Given Name for the CA |
|
%4 |
<CertificateName> |
Renewal Extension of the CA |
|
%6 |
<ConfigurationContainer> |
DN of the Configuration Container in AD |
|
%7 |
<CATruncatedName> |
Truncated Name of the CA ( 32 Characters ) |
|
%8 |
<CRLNameSuffix> |
Inserts a name suffix at the end of the file name before publishing a CRL |
|
%9 |
<DeltaCRLAllowed> |
When this called, this will replace the CRLNameSuffix with a separate suffix to use the delta CRL |
|
%10 |
<CDPObjectClass> |
Object Class identifier for CDP |
|
%11 |
<CAObjectClass> |
Object Class identifier for a CA |
AIA Location
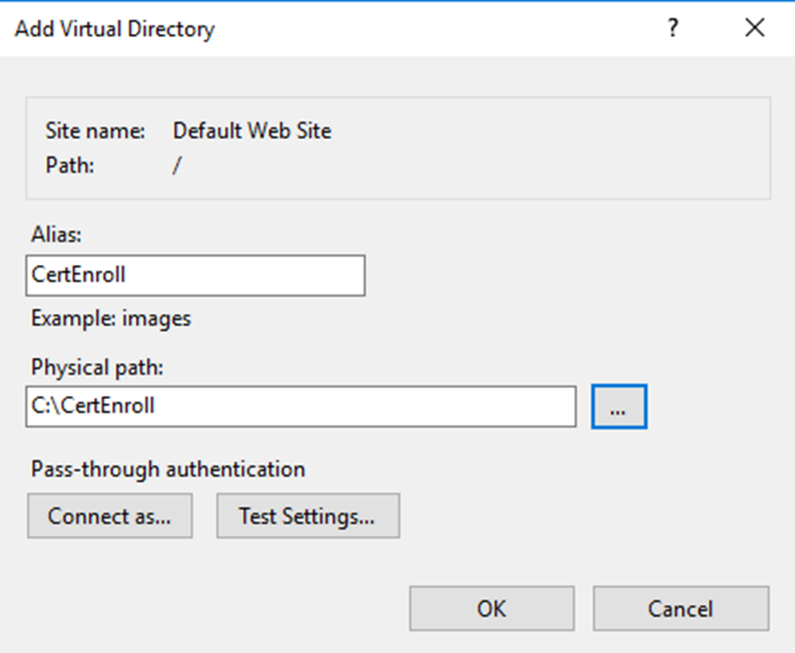
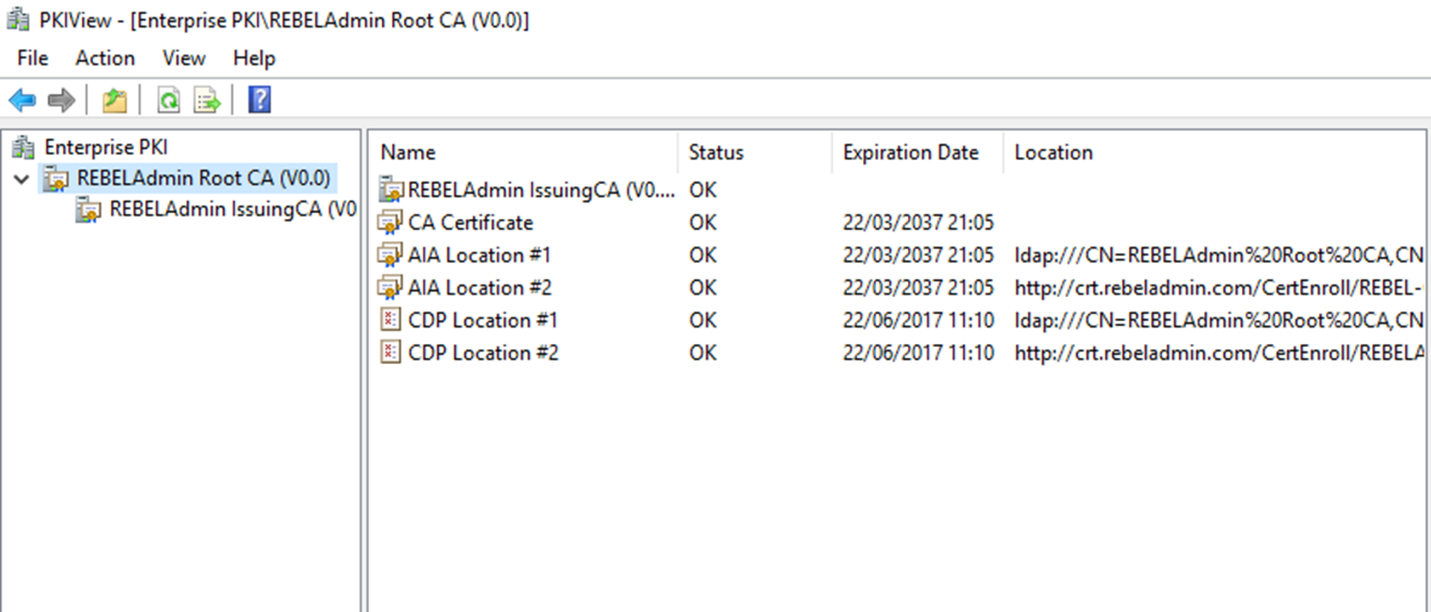
AIA (Authority Information Access) is an extension which is in certificate and it defines the location where application or service can retrieve issuing CA’s certificate. This is also a web based path and we can use the same location we used for the CDP.
This can be set using,
certutil -setreg CA\CACertPublicationURLs "1:C:\Windows\system32\CertSrv\CertEnroll\%1_%3%4.crt\n2:ldap:///CN=%7,CN=AIA,CN=Public Key Services,CN=Services,%6%11\n2:http://crt.rebeladmin.com/CertEnroll/%1_%3%4.crt"
The Options are very much similar to the CDP with few smaller changes.
|
Option |
Details |
|
0 |
No Changes |
|
1 |
Publish CA certificate to given location |
|
2 |
Attach AIA extensions of issued certificates |
|
32 |
Attach Online Certificate Status Protocol (OCSP) Extensions |
CA Time Limits
When we setup the CA we have defined CA validity period as 20 years. but it doesn’t mean every certificate it issue will have 20 years’ valid period. Root CA will issue certificates only to Issuing CAs. Certificate request, approval and renewal processes are manual. There for typically these certificates will have longer validity periods. In demo, I will set it for 10 years.
certutil -setreg ca\ValidityPeriod "Years"
certutil -setreg ca\ValidityPeriodUnits 10
CRL Time Limits
CRL also got some time limits associated.
Certutil -setreg CA\CRLPeriodUnits 13
Certutil -setreg CA\CRLPeriod "Weeks"
Certutil -setreg CA\CRLDeltaPeriodUnits 0
Certutil -setreg CA\CRLOverlapPeriodUnits 6
Certutil -setreg CA\CRLOverlapPeriod "Hours"
In above commands,
CRLPeriodUnits – Specify the number of days, weeks, months or years CRL will be valid.
CRLPeriod – Specify whether CRL validity period is measured by days, weeks, months or years.
CRLDeltaPeriodUnit – Specify the number of days, weeks, months or years delta CRL will be valid. For offline CA this should be disabled.
CRLOverlapPeriodUnits – This specify the number of days, weeks, months or years that CRL can overlap.
CRLOverlapPeriod – This Specify whether CRL overlapping validity period is measured by days, weeks, months or years.
Now we have all the settings submitted and in order to apply changes cert service need to be restarted.
Restart-Service certsvc
New CRL
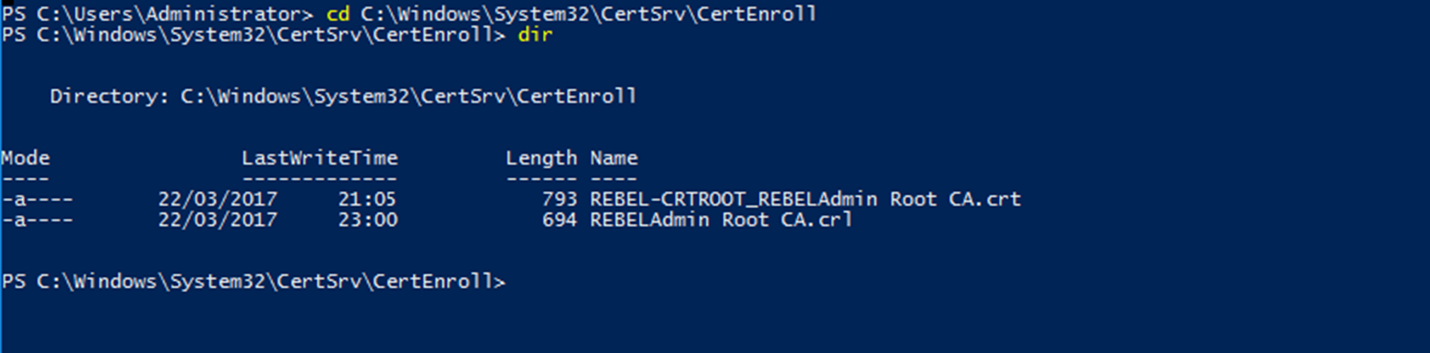
Next step is to create new CRL and it can generate using,
certutil -crl
Once it’s done, there will be two files under C:\Windows\System32\CertSrv\CertEnroll
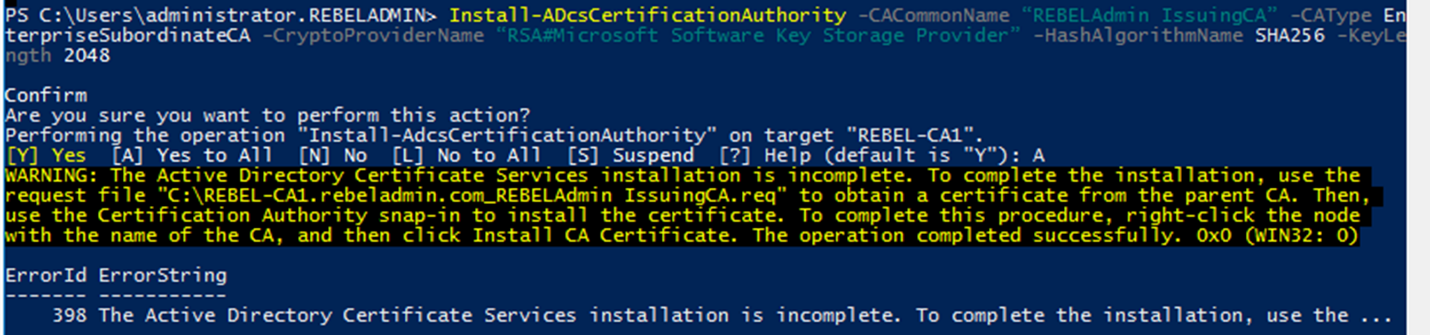
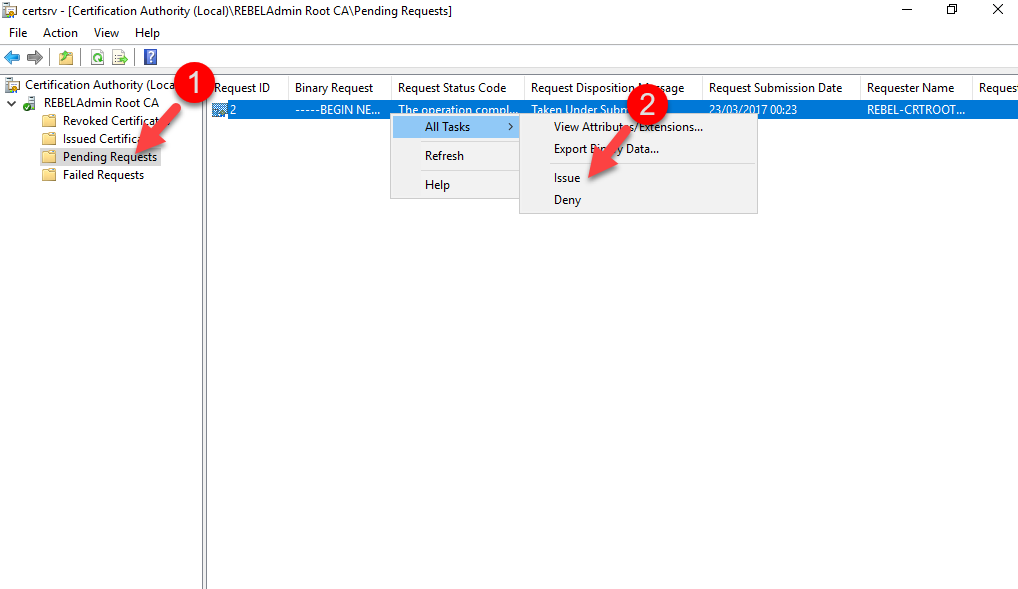
certutil –f –dspublish "REBEL-CRTROOT_REBELAdmin Root CA.crt" RootCAcertutil –f –dspublish "REBELAdmin Root CA.crl"Add-WindowsFeature ADCS-Cert-Authority -IncludeManagementToolsAdd-WindowsFeature ADCS-web-enrollmentInstall-ADcsCertificationAuthority -CACommonName “REBELAdmin IssuingCA” -CAType EnterpriseSubordinateCA -CryptoProviderName “RSA#Microsoft Software Key Storage Provider” -HashAlgorithmName SHA256 -KeyLength 2048Install-ADCSwebenrollmentcertreq -submit "REBEL-CA1.rebeladmin.com_REBELAdmin IssuingCA.req"certreq -retrieve 2 "C:\REBEL-CA1.rebeladmin.com_REBELAdmin_IssuingCA.crt"Certutil –installcert "C:\REBEL-CA1.rebeladmin.com_REBELAdmin_IssuingCA.crt"
start-service certsvccertutil -setreg CA\CRLPublicationURLs "1:%WINDIR%\system32\CertSrv\CertEnroll\%3%8%9.crl\n2:http://crt.rebeladmin.com/CertEnroll/%3%8%9.crl\n3:ldap:///CN=%7%8,CN=%2,CN=CDP,CN=Public Key Services,CN=Services,%6%10"certutil -setreg CA\CACertPublicationURLs "1:%WINDIR%\system32\CertSrv\CertEnroll\%1_%3%4.crt\n2:http://crt.rebeladmin.com/CertEnroll/%1_%3%4.crt\n3:ldap:///CN=%7,CN=AIA,CN=Public Key Services,CN=Services,%6%11"certutil -setreg CA\CRLPeriodUnits 7certutil -setreg CA\CRLPeriod “Days”certutil -setreg CA\CRLOverlapPeriodUnits 3certutil -setreg CA\CRLOverlapPeriod “Days”certutil -setreg CA\CRLDeltaPeriodUnits 0certutil -setreg ca\ValidityPeriodUnits 3certutil -setreg ca\ValidityPeriod “Years”Restart-Service certsvccertutil -crl



Install-AdcsCertificationAuthority should have an additional parameter if system does not contain a networkadapter: -DatabaseDirectory $(Join-Path $env:SystemRoot “System32\CertLog”)
Hi Dishan, I’m trying to install a PKI for learning step by step like you explain here. everything is working fine until the command:
certutil -crl > here I’m gonna get an error
(PS C:\Users\Administrator> certutil -crl
Certutil: -CRL command FAILED: 8x8007010b (WIN32/HTTP: 267 ERROR_DIRECTORY)
Certutil: The directory name is invalid.
PS C:\Users\Administrator> )
do you maybe have any hint, what I did wrong? or where I can check for errors?
Did you ever figure out the error? I get the same error.
This is caused by %WINDIR% in the CDP und AIA registry commands for the subordinate CA. Use “C:\Windows” instead and it works.