People use safes, security boxes to protect their valuable things. In digital world “Data” is the most valuable thing. Passwords, Connection Strings, Secrets, Data encryption/decryption keys protects access to different data sets. Whoever have access to those will also have access to data behind it (of cause they need to know how to use those ?). So how we can protect those valuable info? People use different methods. Some use third party software installed on PC to do it. If its large environment some use web application so multiple people have access to it. different vendors use different methods to protect these types of valuable data. Microsoft Azure Key vault is a service which we can use to protect Passwords, Connection Strings, Secrets, Data encryption/decryption keys uses by cloud applications and services. Keys stored in vaults is protected by hardware security modules (HSMs). It is also possible to import or generate keys using HSMs. Any keys process that way will be done according to FIPS 140-2 Level 2 guidelines. You can find about FIPS 140-2 Level 2 using https://www.microsoft.com/en-us/trustcenter/Compliance/FIPS
Benefits of using Key Vault
• Keys saved in vault will be served via URLs. Developers, engineers do not need worry about securing keys. Application or service do not see the keys as vault service process behalf of them.
• Customers do not have to disclosure their keys to vendors or service providers. They can manage their own keys and allow to access those keys via urls in vendor or service provider applications. Vendor or service providers will not see the keys.
• By design Microsoft can’t extract or see customer keys. So, its further protected in vendor level too.
• HSMs are FIPS 140-2 Level 2 validated. So, any industry required to comply with these standards are protected by default.
• Key usage details are logged. So, you know what’s happening with your keys.
An Azure Administrator is allowed to do following using Azure Key Vault,
• Create or import a key or secret
• Revoke or delete a key or secret
• Authorize users or applications to access the key vault, which allow them to manage or use its own keys and secrets
• Configure key usage
• Record key usage
More info about Azure Key vault can find under https://docs.microsoft.com/en-us/azure/key-vault/key-vault-overview
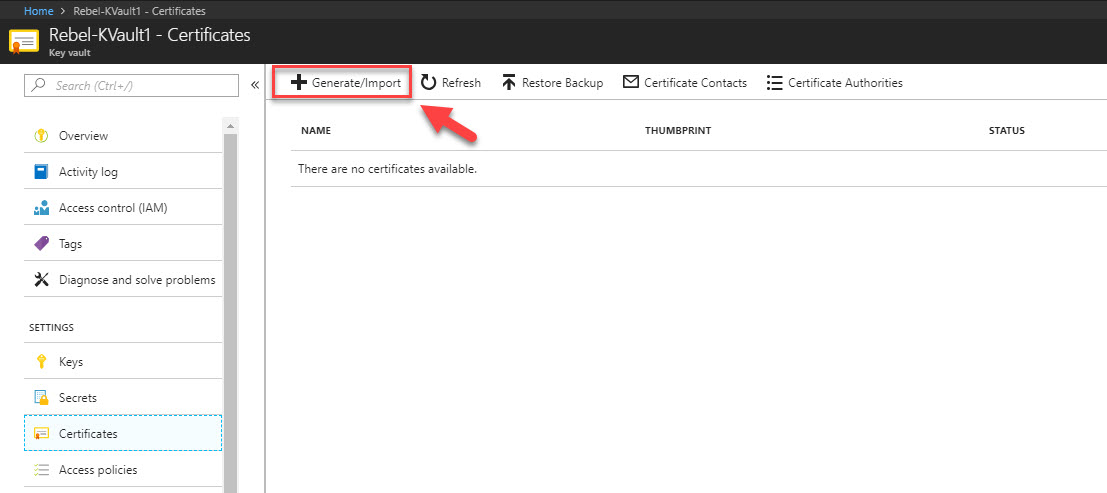
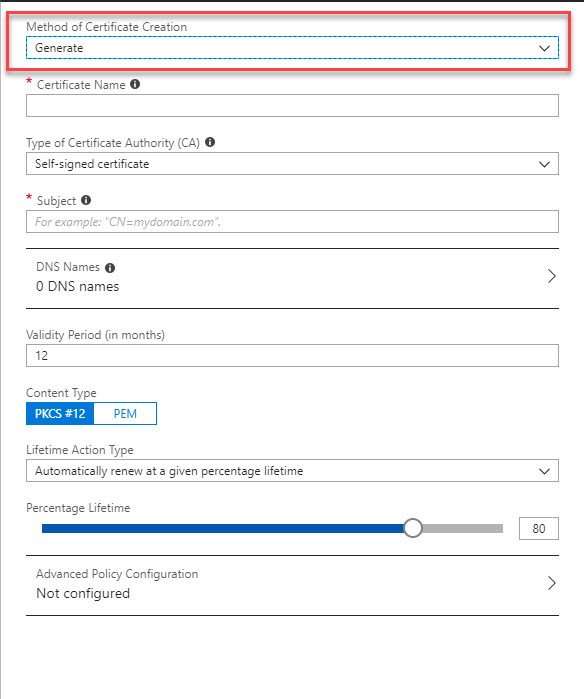
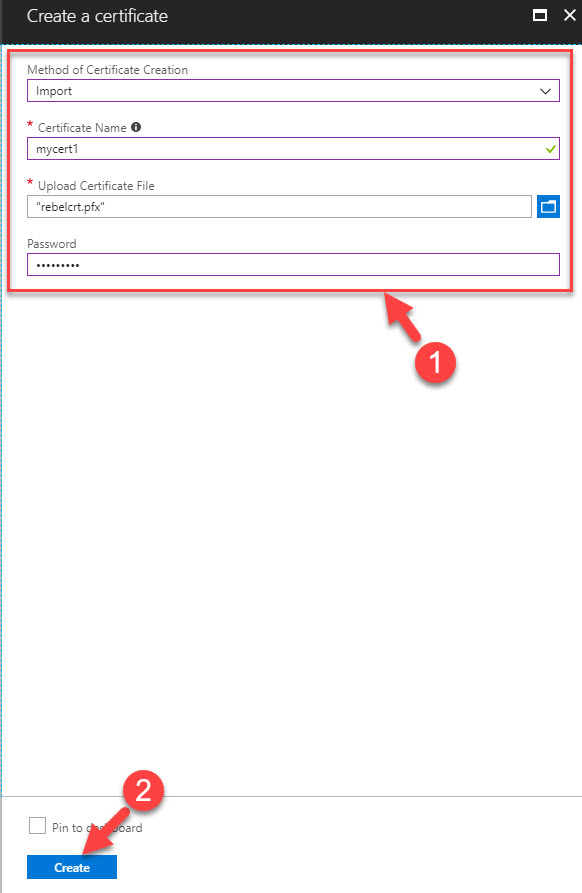
Let’s go ahead and see how we can setup and use Azure Key Vault service.
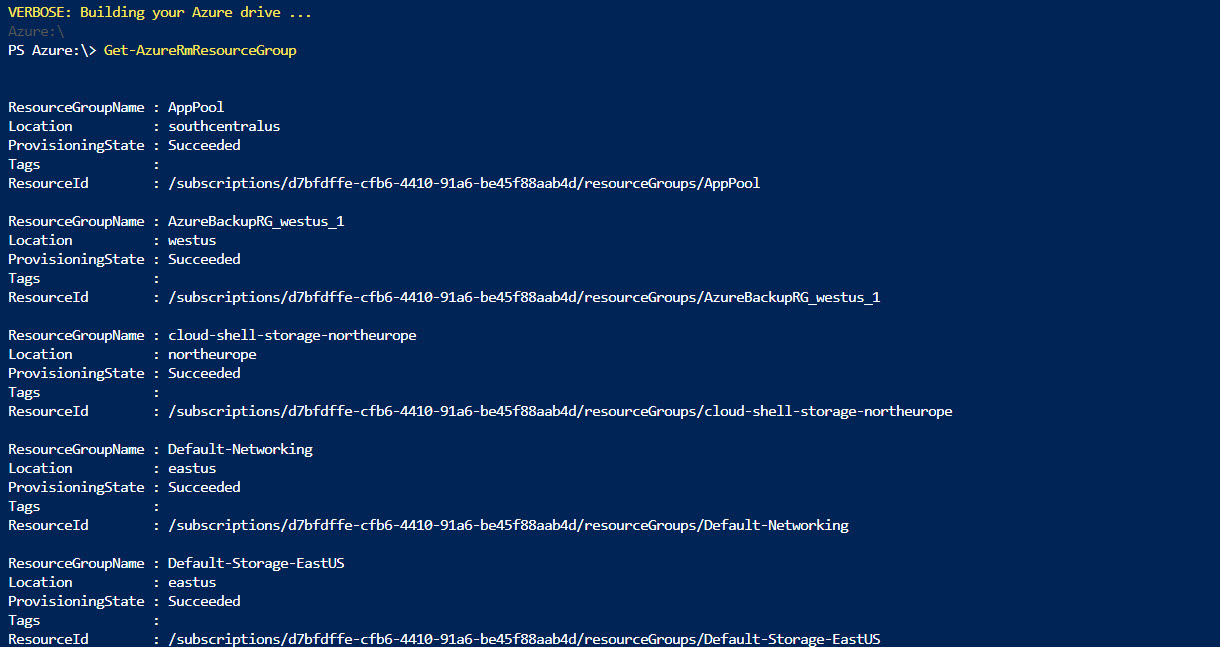
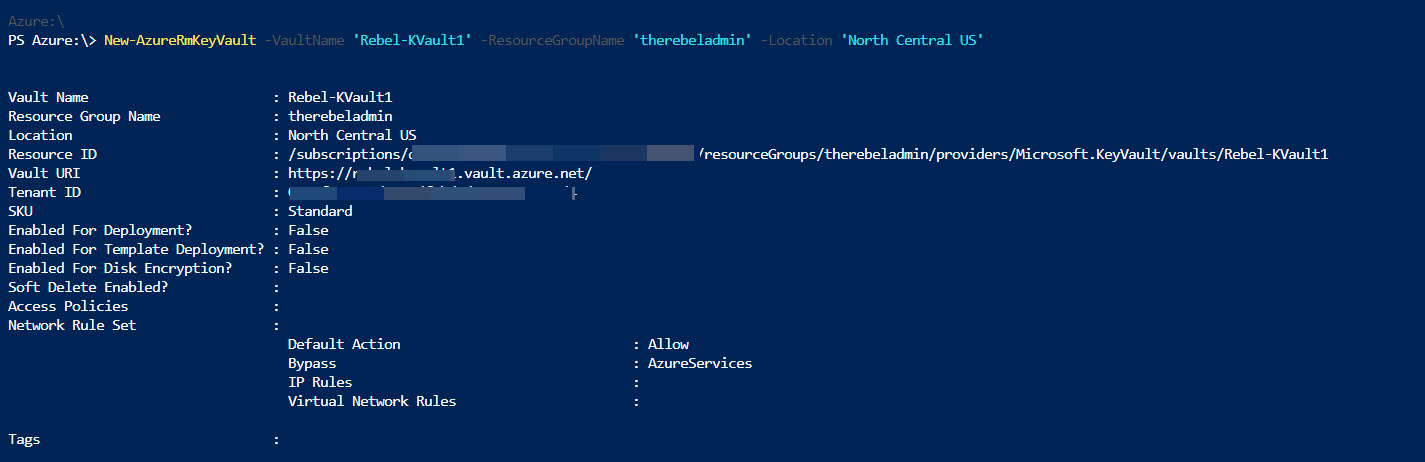
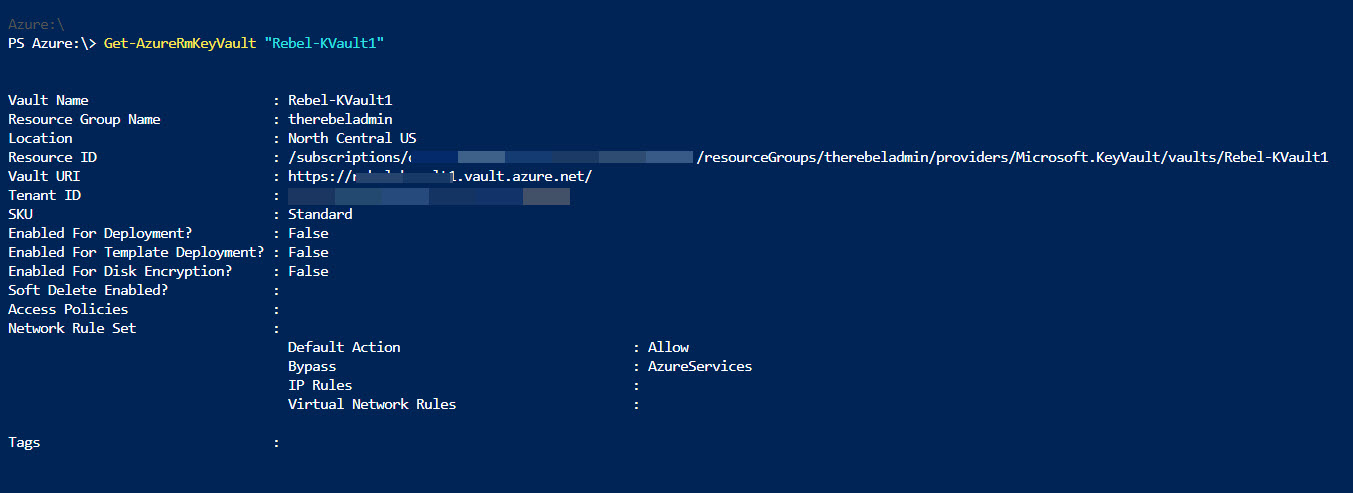
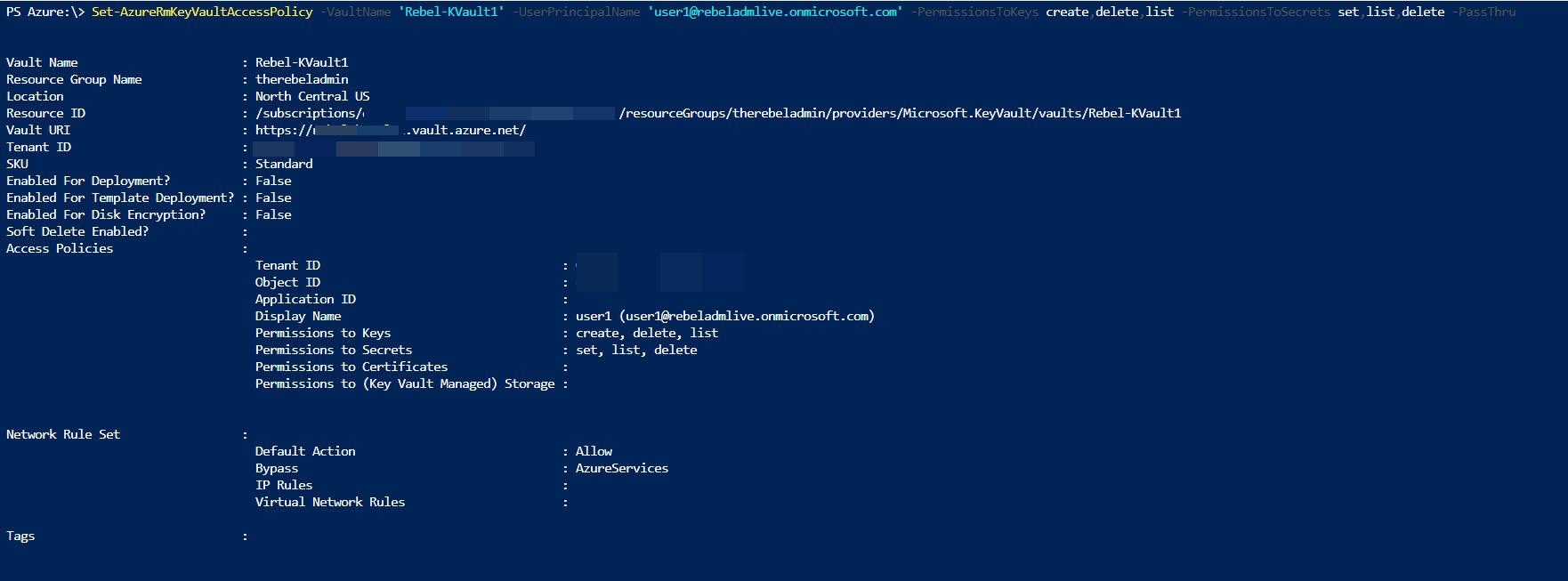
Get-AzureRmResourceGroup to list down resource groups. So, we can select the resource group to associate the new key vault. New-AzureRmResourceGroup -Name RGName -Location WestUSGet-AzureRmLocationNew-AzureRmKeyVault -VaultName 'Rebel-KVault1' -ResourceGroupName 'therebeladmin' -Location 'North Central US'Get-AzureRmKeyVault "Rebel-KVault1"Set-AzureRmKeyVaultAccessPolicy -VaultName 'Rebel-KVault1' -UserPrincipalName 'user1@rebeladmlive.onmicrosoft.com' -PermissionsToKeys create,delete,list -PermissionsToSecrets set,list,delete -PassThruSet-AzureRmKeyVaultAccessPolicy -VaultName 'Rebel-KVault1' -ServicePrincipalName 'http://crm.rebeladmin.com' -PermissionsToSecrets Get
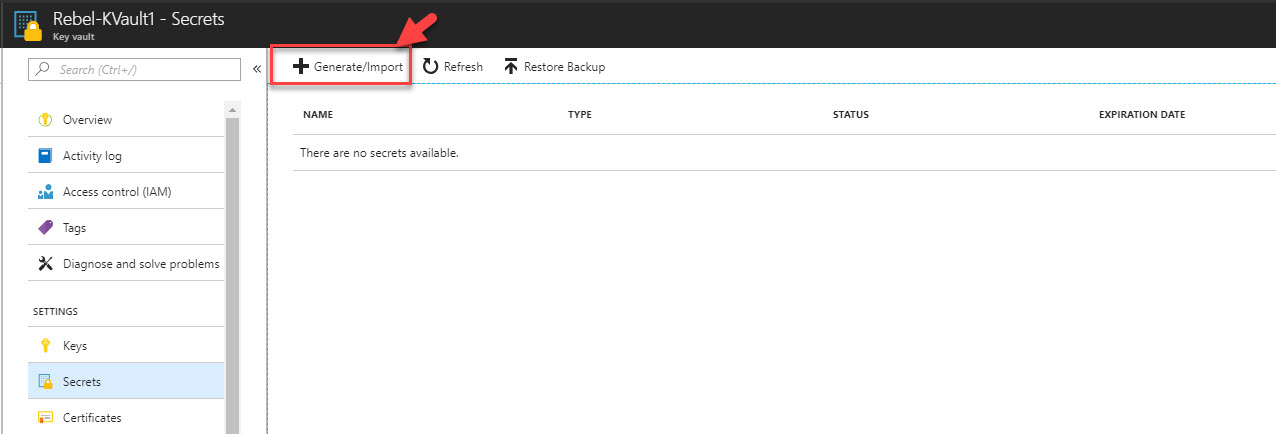
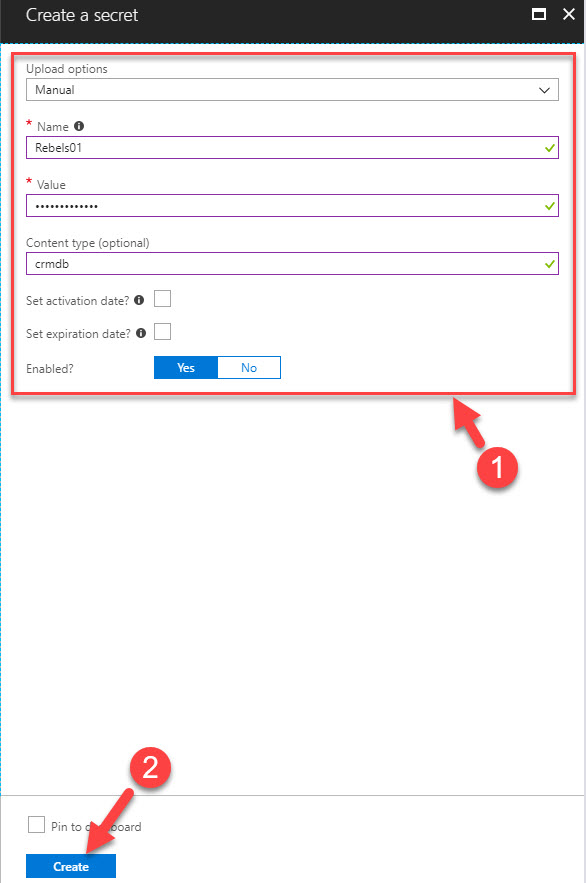
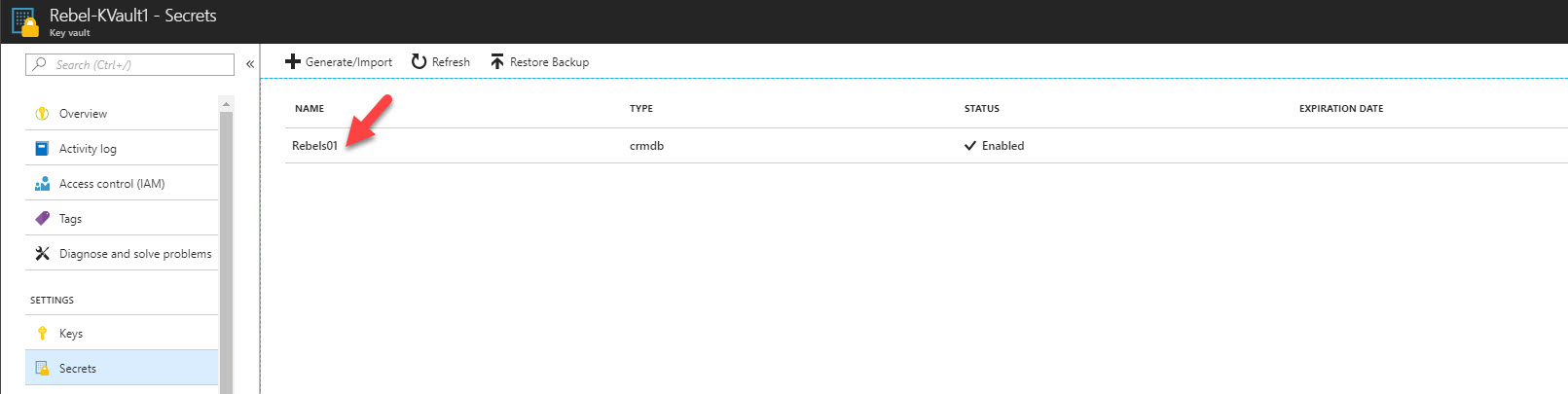
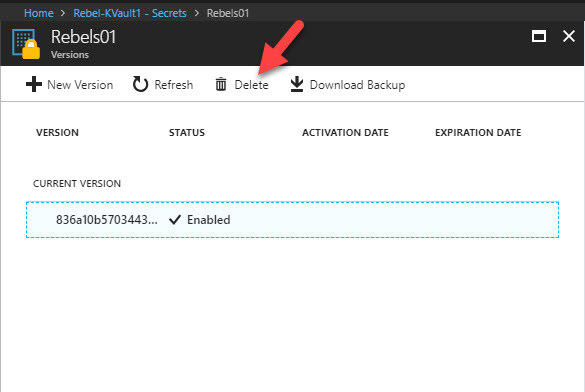


Superb!