Table of Contents
What is Microsoft Advanced Threat Analytics ? There are many ways to monitor Active Directory activities in an infrastructure. Some tools are just to monitor the AD services and some tools are to monitor services as well as the activities. Service level monitoring is the easy part and any monitoring tool with windows service monitoring can monitor the status of the AD services. Tools likes SCOM allows to monitor services in more granular level. it is not just monitoring status of the service, it also monitors the AD components and their activities. Windows event log also gives visibility over Active Directory service status and its activities. In a previous blog post I explained how we can enabled advanced active directory auditing which can help to understand what’s going on.
When it comes to security related events, only a tool with auditing capabilities can give some insight. However most of these tools do not give any advice or guidance based on the events it captured. It’s all depend on engineers who analysis those. As an example, an event I sees as a security related event may not see as a threat by a second line support engineer. This is a quite an issues as recent report from Microsoft shows it can take average of 146 days to identify an identity infrastructure security breach. We are fighting against human adversaries, it is obvious we cannot close all the doors. We need to expect a breach. If there is a breach or attempt there should be way to identify it quick as possible and prevent it.
Microsoft is maintaining Active Directory more than 20 years. Microsoft now also have Azure Active Directory. Every day they collect massive amount of security events related to active directory from many different sources. They used these data to build Microsoft Advanced Threat Analytics. It is a simple tool which can identify Active directory infrastructure security threats in early stage and notify engineers about it.
OMS or Microsoft Advanced Threat Analytics ?
Microsoft Operation Management Suite also have modules such as AD Assessment, Security and Audit which uses Microsoft Security Graph to identify Active Directory infastrcure threats. OMS not only audit AD activities, it also evaluates existing Active Directory infastrcure setup and provide guidelines to improve it. All these recommends are based on Microsoft security and deployment best practices. OMS also can integrate with Azure Automation to automate operation tasks. It allows engineers to attach a runbook to an alert. In ATA it is only detect and report the problem but it will not take any action about it. I am not saying any of them can replace the other one. Both have different capabilities and its up to you to choose the best one for your environment.
What Microsoft Advanced Threat Analytics can detect?
Things that ATA can detect can categorize under 3 areas.
Malicious attacks
- Pass-the-Ticket (PtT)
- Pass-the-Hash (PtH)
- Overpass-the-Hash
- Forged PAC (MS14-068)
- Golden Ticket
- Malicious replications
- Reconnaissance
- Brute Force
- Remote execution
- Malicious DPAPI
Abnormal behaviour
- Anomalous logins
- Unknown threats
- Password sharing
- Lateral movement
Security issues and risks
- Broken trust
- Weak protocols
- Known protocol
- Vulnerabilities
Microsoft Advanced Threat Analytics Components
Microsoft Advanced Threat Analytics Center – ATA center is the operation center. It receives information from ATA gateways and display the detected events in web interface. using ATA center, we also can setup administrators, configure email alerts settings, check the status of connection to gateways. It also can manage the update settings for the gateways.
Microsoft Advanced Threat Analytics Gateway – ATA Gateway monitors the traffic which comes to Active Directory Servers. it uses port mirroring technology for it. captured data will passed in to ATA center for evaluation.
Microsoft Advanced Threat Analytics Lightweight Gateway – This is the easiest method which can use to install ATA gateway. This component can directly install in Active Directory Domain Controller. However, it will increase the resource usage of the domain controller.
Microsoft Advanced Threat Analytics Deployment
There are three ways to deploy Microsoft Advanced Threat Analytics,
Using only ATA Gateways – In this deployment mode separate ATA gateways will be used. Domain controllers network ports need to mirror to ATA gateways servers so they can capture the traffic. this is the most reliable method as it will not make any impact on active directory domain controller performance.
Using only ATA Lightweight Gateways – This is most cost effective method of deployment. It will not require separate server and component will be directly install on Domain Controller. It also not required any network layer changes. Only requirement will be to increase the RAM and CPU for the Domain Controller.
Using both ATA Gateways and ATA Lightweight Gateways – In this method, both gateway types will be used. This is ideal deployment mode for branch office environment. In branch office, we can use ATA Lightweight Gateways as it monitor relatively lower traffic.
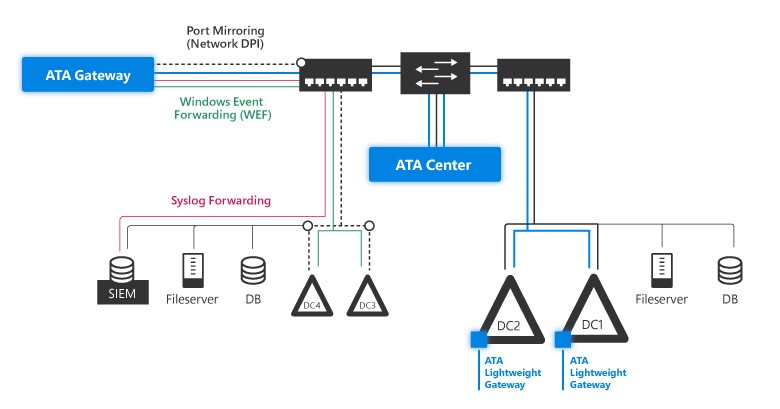
Image source : https://docs.microsoft.com/en-gb/advanced-threat-analytics/plan-design/media/ata-architecture-topology.jpg
Microsoft Advanced Threat Analytics Prerequisites
- ATA center need minimum of Windows server 2012 R2 with latest updates. Recommended at least 4 GB and 2 CPU.
- ATA center need to two IP addresses
- ATA Lightweight Gateway need minimum of Windows server 2012 R2 with latest updates. Recommended at least 6 GB and 2 CPU.
- SSL Certificate for ATA center and gateways. If there is no valid certificate (such as wild card or certificate from internal CA) we can still use self-signed certificate.
Now we have everything ready for the ATA deployment. In next part of this post, I will walk you through the deployment steps.
Hope this was helpful and if you have any question feel free to contact me on rebeladm@live.com



Hi Dishan,
Thanks for detailing the ATA. It was quite confusing for me on selection of ATA lightweight gateway and ATA Gateway. Deployment scenario you explained cleared my doubts.
Thanks again & All the best.