As a network administrator, network student its important to have clear understanding over the OSI model. Also its important to understand its process through network process.
In this post i will explain a simple IT process using OSI model. Lets assume your HR Manager sends an email to Head of IT by using her email client regarding a meeting. let's see how the email will deliver through the 7 layers.
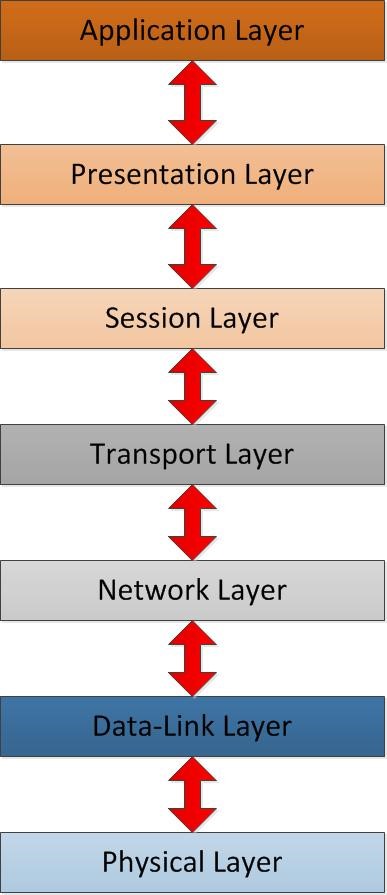
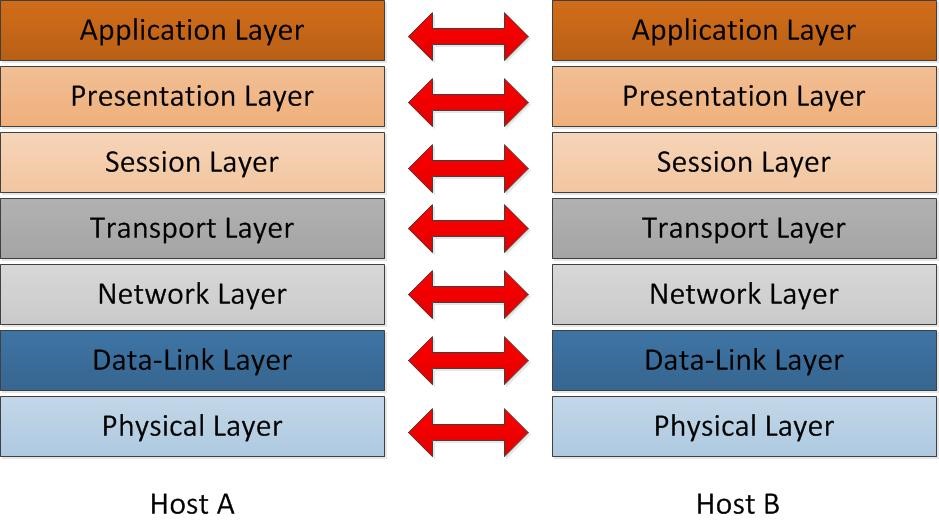
When computer communicates with another host, it’s goes through all 7 layers top to bottom or bottom to top. In one side these layers can talk to its upper layer or lower layers.
Each of these layers talks to the corresponding layer in the other side when it communicates. For ex- application layer from one end will only talk to application layer on the other side. It cannot talk to any other layer which means application layer cannot talk to presentation layer on the other side.
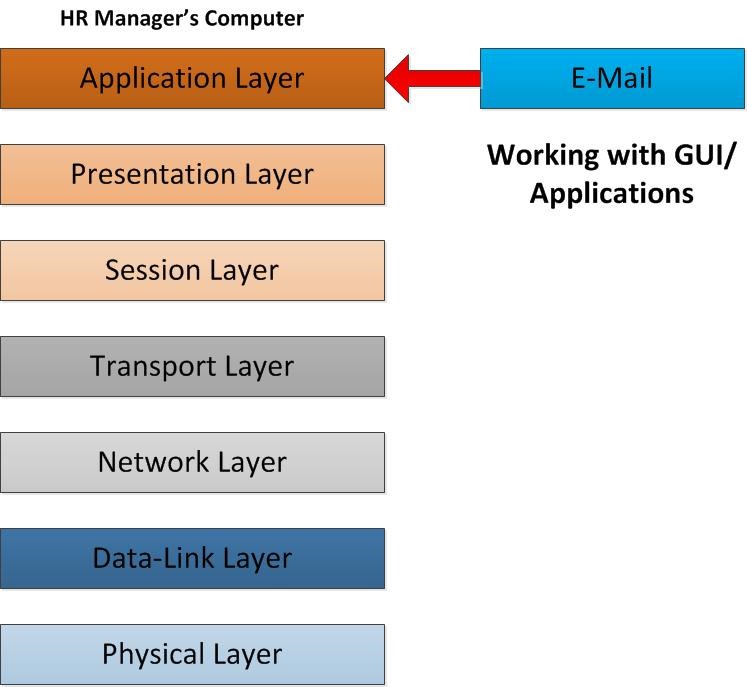
So let’s move in to the given scenario. As the first step HR manager sends the email. To sends the email from his computer he may using email client. It can be outlook express, MS office outlook, Thunderbird, Mac mail etc. This process is goes in to Application Layer of the OSI model. It’s provides the interface for the user to tell the computer how to handle the data. In this scenario since its emails the email client will use SMTP protocol and command to tell computer how to handle those data.
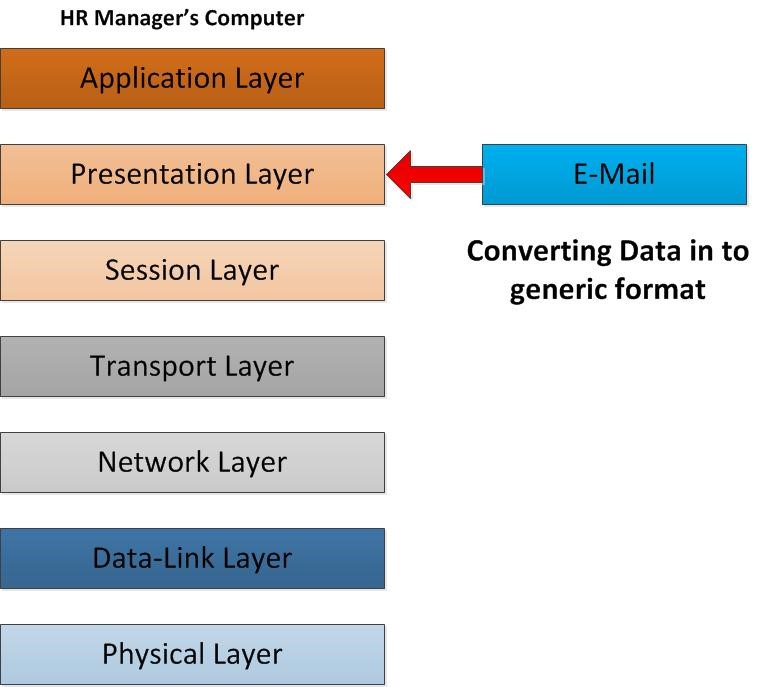
Then the email starts to operate on the Transport Layer of the OSI model. In this layer the email content will be converting in to network formats. It’s defines how the data will be presented. So the E-mail text will be converting in to ASCII and images will specify as TIFF, JPEG, etc. other important thing that will happen in this layer is data encryption and data compression. With encryption it defines the how secure the communication should happened going down through the OSI Layer. For example in this layer you can use SSL (secure socket layer) for the encryption of the data. With compression of data in this layer can improve the through put of the data along the lower layers.
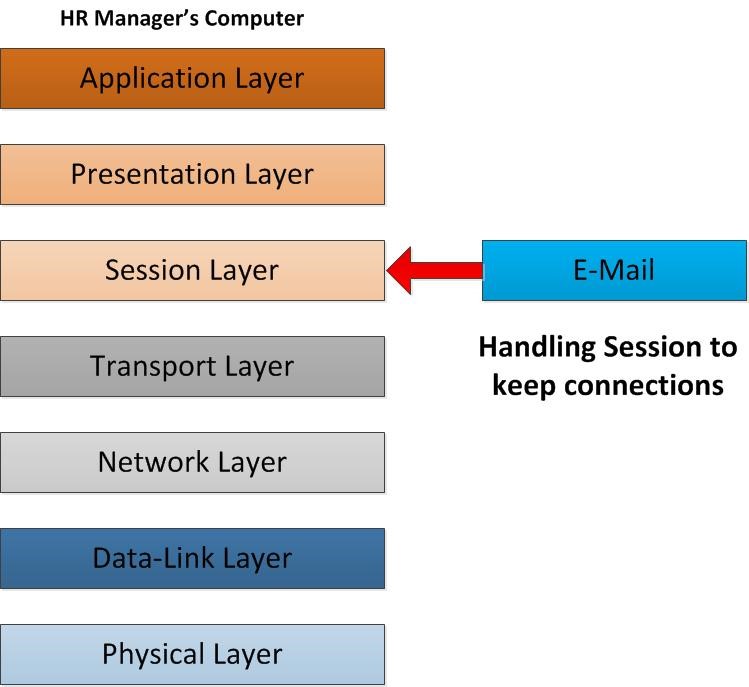
As the email is starts to operate in session layer it will be responsible for starting, handling and terminating the connection with the other end. So in this scenario this session layer responsible with keep the connection with the IT Head to deliver the email correctly. In computer in given time it’s not only one connection made to different hosts. For example while HR manager send email he may also having a website open in internet explorer. So when data packets send/receive how computer knows this data packet should go to this application? Another way if he opens 2 websites same time how computer know the receiving packet should go to which browser tab? The answer is session layer. Session layer creates, manage and terminate the “connections” to the relevant host. This is doing by based on the port numbers. Its separate the connections using random ports so the connections are not mixed up. Without connections the data will not flow through the OSI Layers.
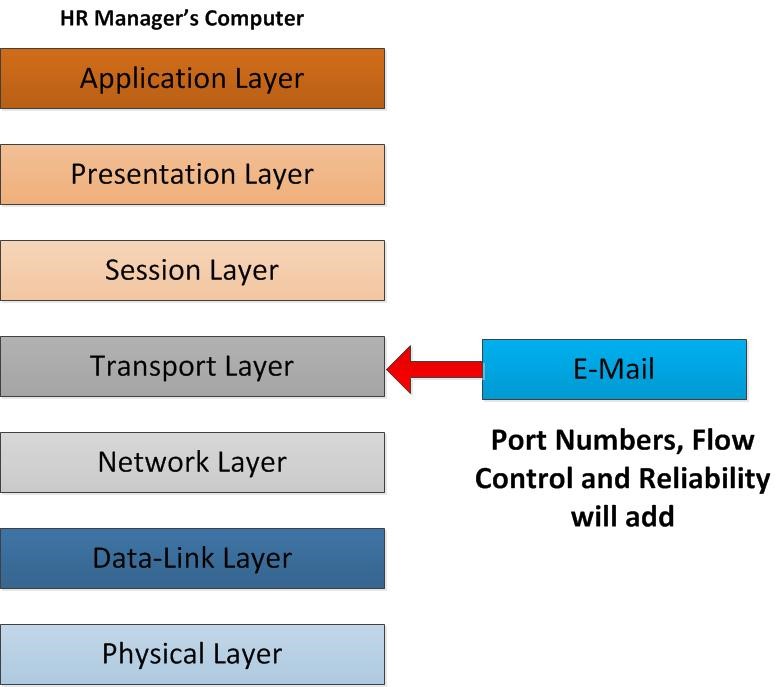
As email going down to the next layer, its starts to operate in transport layer. This is the layer which will decide the reliability and the flow control. In this the email data from HR Manager will break in to segments to transmit over. In here it need to be select is this going to be transmit as TCP packets or UDP packets. With TCP packets it’s defines the reliability. It’s always acknowledging the transfer of the data packet. So from sender end once TCP packet go to receiver end it confirms as the packet is received so sender always know the packet is transfer properly as he wish. UDP in other side is faster but no reliability. It doesn’t provide any acknowledgment of packet transfer. In this scenario the email will use TCP port number 25 which use the SMTP protocol. Sender port as well the receiver port will define in this layer, since receiver also get it as email it going to be port 25. It’s going to be reliable data packet transfer. The other important thing is in this layer since its break in to segments; once the other parties receive the packet he should be able to reassemble it in correct order. This flow control also defines by this layer. When other user receives these packets he can reassemble it in correct order.
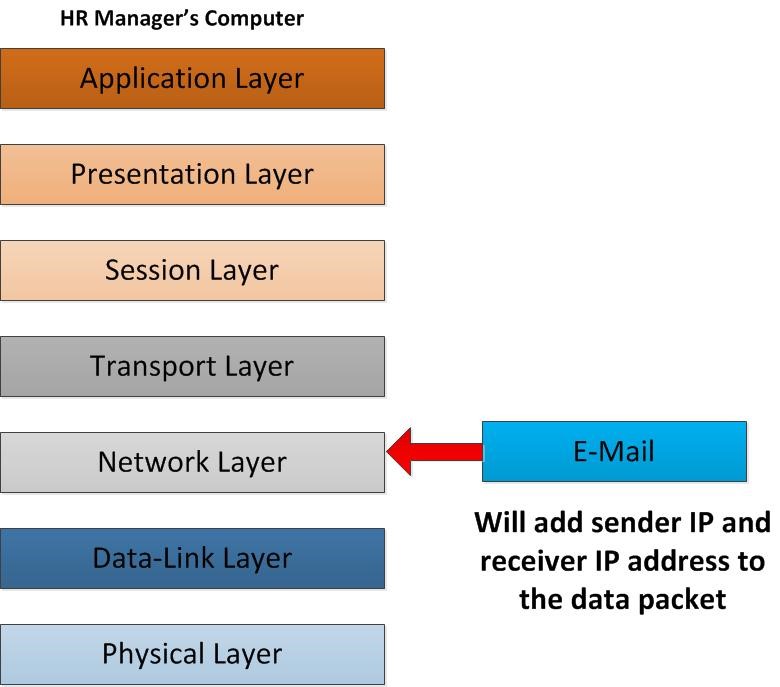
As the email data packet flow in to network layer it defines how the routing of this data packet will happens. To send data packet from one location to another there should be some way of identify the exact receiver among all the hosts. It’s like sending a postal mail to someone. To identify that house among all the houses in the area it have address so when mail send to that address it will deliver properly checking on these addresses. So in this layer from HR manager computer to the IT head’s computer it will define the routes how from which location to which it should deliver. It does add the sender IP address and receiver IP address to the data packet. Now each data packet knows where it should go to.
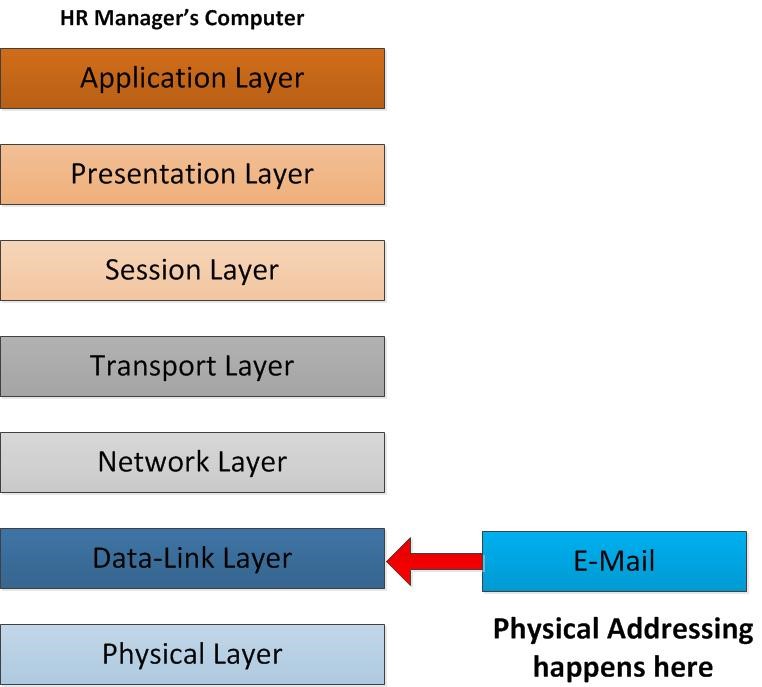
As the packet move further down along the layer net it reach to the Data Link layer. Now the email data packet will be prepare to send over the Ethernet. For that the data packet will be converts in to data frames. As we know in network layer the packet was modified with the sender IP and the receiver IP address. Once the data receive by receiver’s network how exactly it knows it should goes to exactly to this computer? The Head of IT may be checking emails from different network with lot of computers so when email packets reach this network there should be way to send it to exact computer. It’s like this let’s say you send postal mail to a friend house. In that house if there is 5 peoples how postman known to whom it goes to. If you mentioned the name of the receiver he knows where it goes. So data link layer it do the same thing. It’s defines the Physical address also known as MAC address to the data frame. MAC address mainly burned in address for the NIC. That is unique address there want be 2 MAC address with same value. So with this address it can easily identify exactly to which host the packet should deliver to. In the data frame in this layer it will add the sender MAC address as well as the Receiver Mac address and send it over.
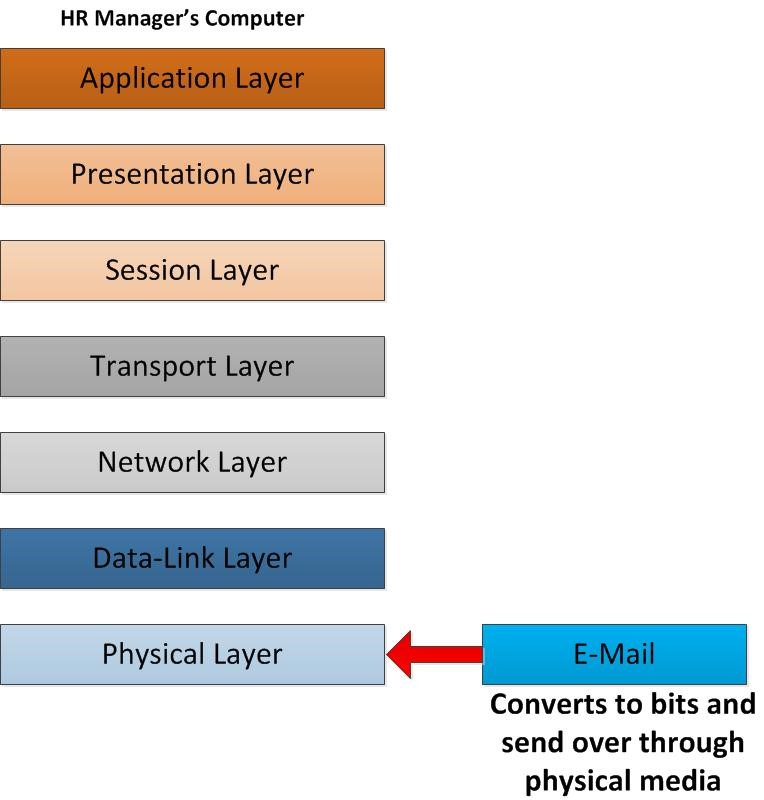
Now the data is ready for transmit over to receiver side. In physical layer it’s going to be preparing data frames. In this physical layer the data frame will be converts in to bits. After it converts it will be send over the physical media which means through your NIC, Ethernet Cable, Wireless connection etc. in this layer there is not much preparation or activity than that.
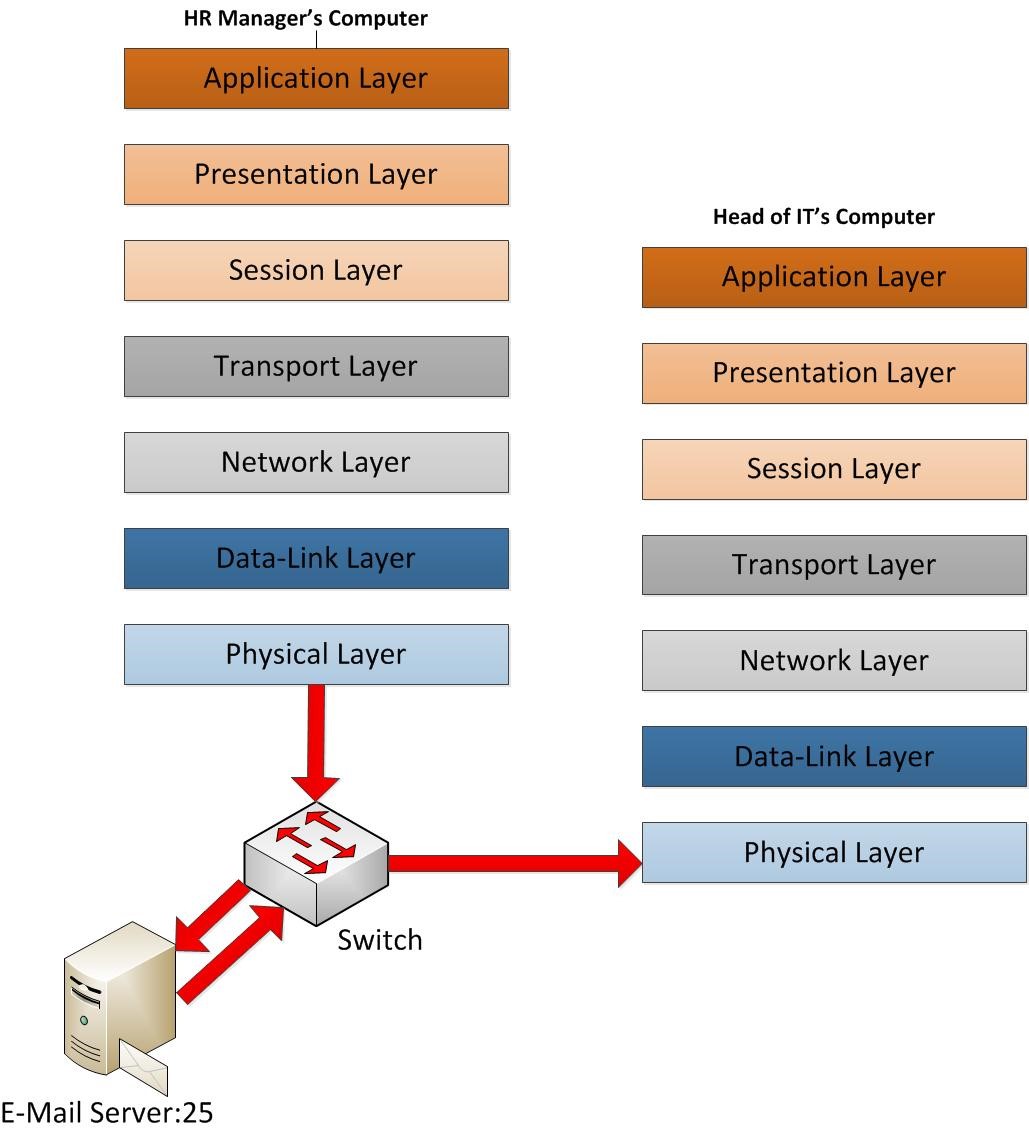
Now the data frames are off from the sender machine. Now it’s in its way to receiver end. But still it has to pass several major points. As soon as its leave the NIC its first stop place will be the switch that sender computer is connected to. So the only layers it will operate in this process is the data link layer and physical layer which means in the data frame the data link layer information will be modified with the destination MAC address and sender MAC address. So in given scenario the sender MAC is HR manager’s NIC MAC and destination Mac is going to be the switch port. That’s the only change will happened in data frame. Then it will look for the E-mail Server because to deliver email first it should go to e-mail server. In this scenario I assumed it’s in same office environment. So its looks for the E-mail server and its headers again get modify with the MAC addresses so destination will be E-mail server NIC Mac address and sender is the switch port MAC. Now switch checks weather this destination can be reach. The same time remember it’s removed the old data link layer MAC address as those no need. So if switch can find it in its ARP table its then route the data frame to the NIC of the E-mail Server. If it cannot find what it do is it sends this to network layer where routers are working so its check network layer and check if original destination of email server is in same network or now and if not it send it out as it knows how to handle those paths. And then it will go point to point with modifying its headers based on destinations.
But in here I had assumed it’s connected in same network so it will not reach out via router. Once E-mail server receives the request it will process and send it to receiver mail box. Then again email server will send the new data frame to the switch to process it to the receiver. In that frame again the data link layer headers will be modified and add the new destination and sender MAC address. Then switch again have to find the receiver destination. The process is exact same as it follows to find the email server first place. Once it found the correct port the data frames will be delivering via Ethernet cable which is works under physical layer.
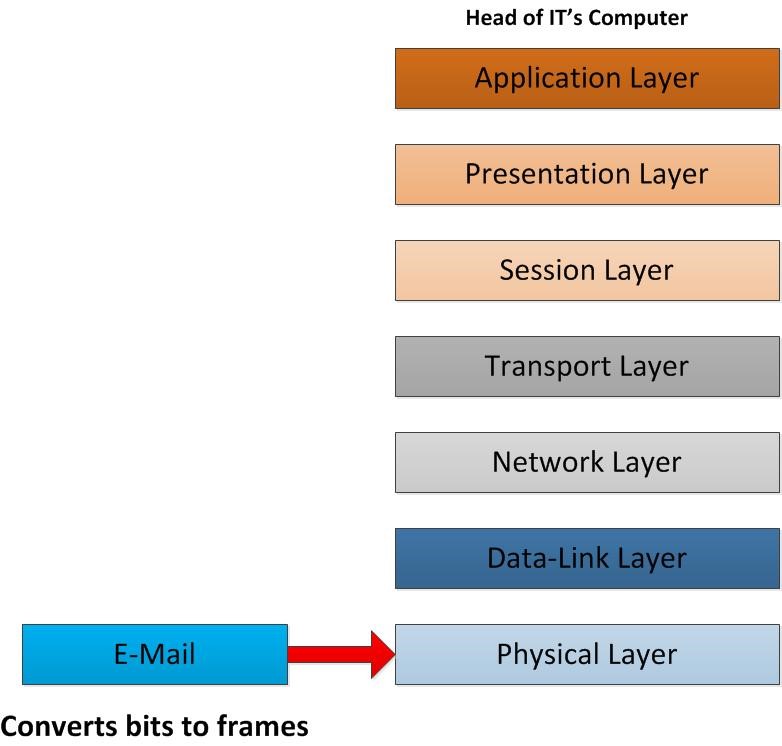
Once its reach by the NIC card of the receiver end which means the physical layer of the Head of IT’s end its start to remove the header information that was added from the sender and gets the data inside it. In the physical layer it will convert the bits in to the data frames and send it for further process from data link layer.
Once the data packet comes in to data link layer it removes the all the information about MAC address that embedded in to frame’s header. Then it converts that frames in to the IP Packets. After that its sending packets to network layer.
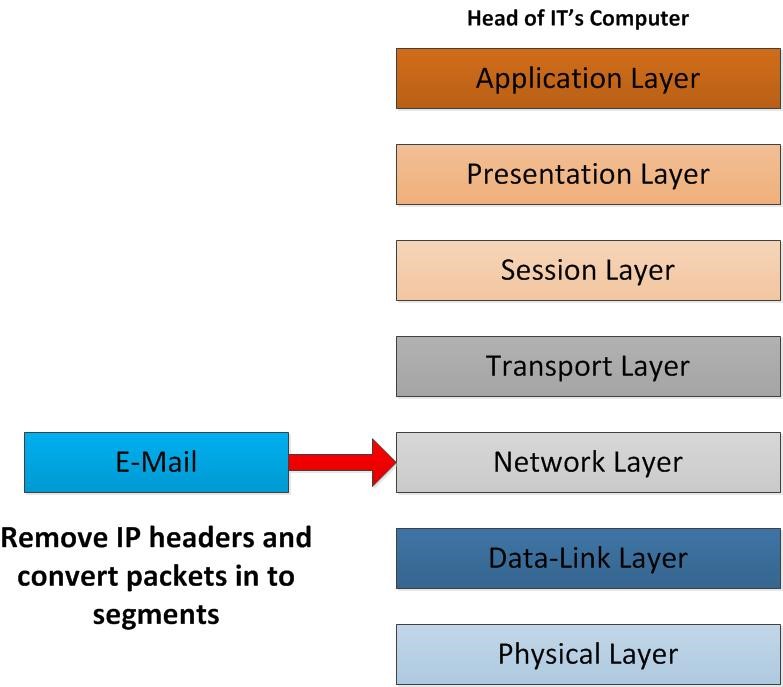
Once network layer receive the packets it’s remove the IP header information. This will includes all the information about the sender IP address and Receiver IP Address. Since packet is received in the correct party those information will not needed any more. After removing those data it will convert these IP packets to segments and send it over to transport layer.
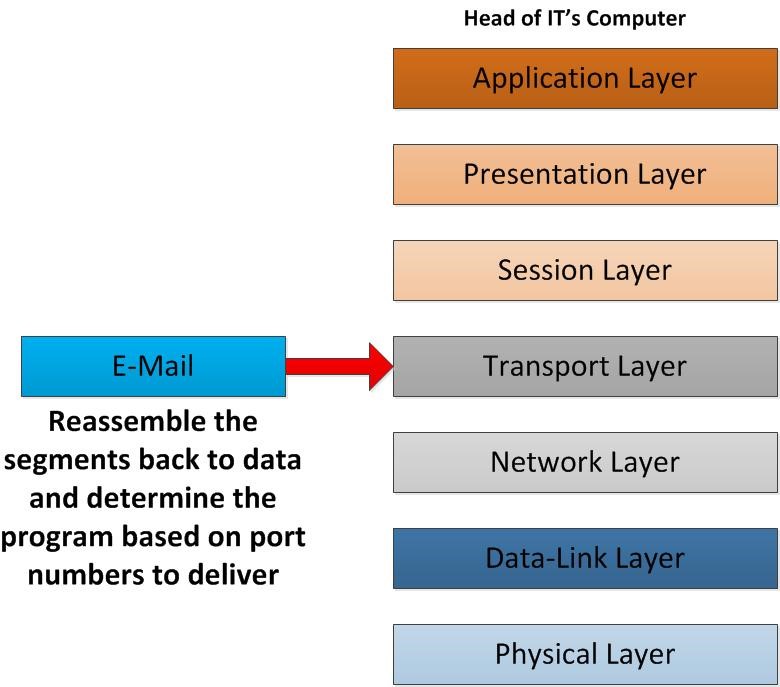
When data segments move to the transport layer, based on the protocol it used for ex- TCP it will reassemble them in to the order. In sender side it was break the data in to segments before its start the transmit. In receiver end it needs to make in to proper order and make the actual data of it. Another important thing is its reads the port that used in the segments and determine in to which application the data should pass in to. Based on this only it identifies it’s HTTP, SNMP, FTP data. In our scenario it’s based on SMTP TCP Port 25. After convert this segments to actual data it will pass in to session layer.
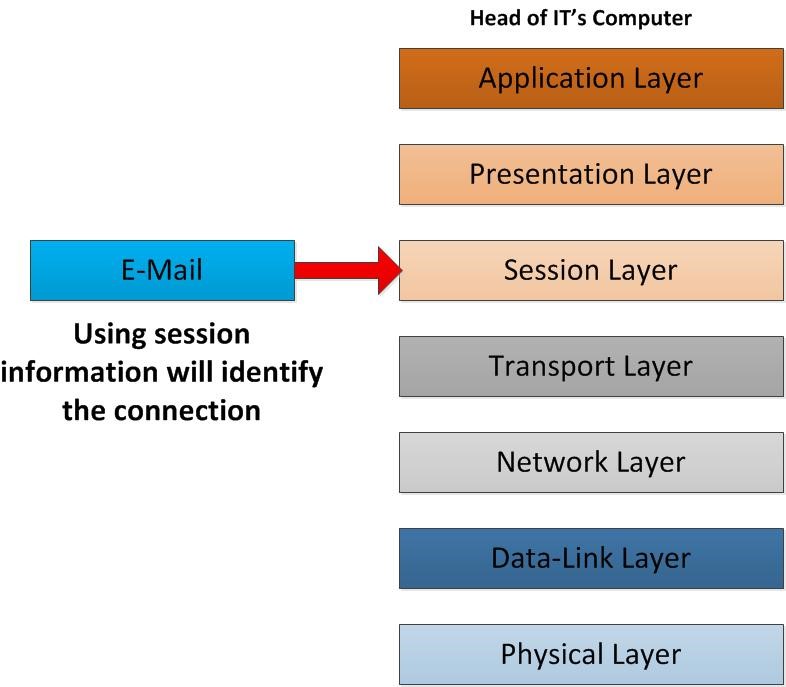
Once data reach the session layer based on session information it will identify the communication type this data belongs to. Let’s say user have few email applications such as outlook express, incredimail etc. all these are working with SMTP port 25 but there should way to identify for which mail client this should delivers. To make this connection, this session information helps. Once connection made is made its move the data in to presentation layer.
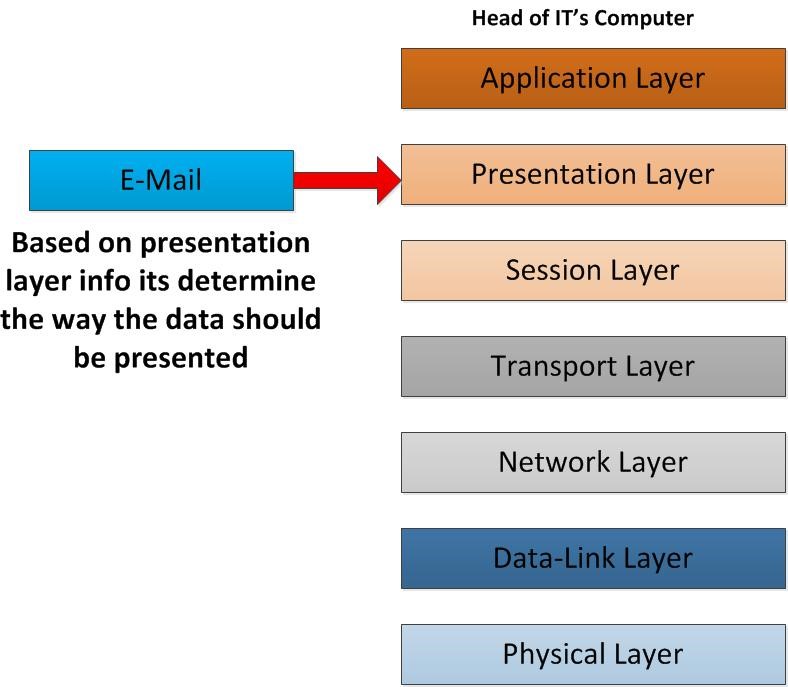
As it reaches the presentation layer it used the info to determine the way it should presented in the applications. If there were ant encryption happened from sender’s presentation layer it will be decrypted in here. If there were compression happened on the data it will be decompress in this layer. Once all these done now it’s ready to presented to the receiver which is Head of IT.
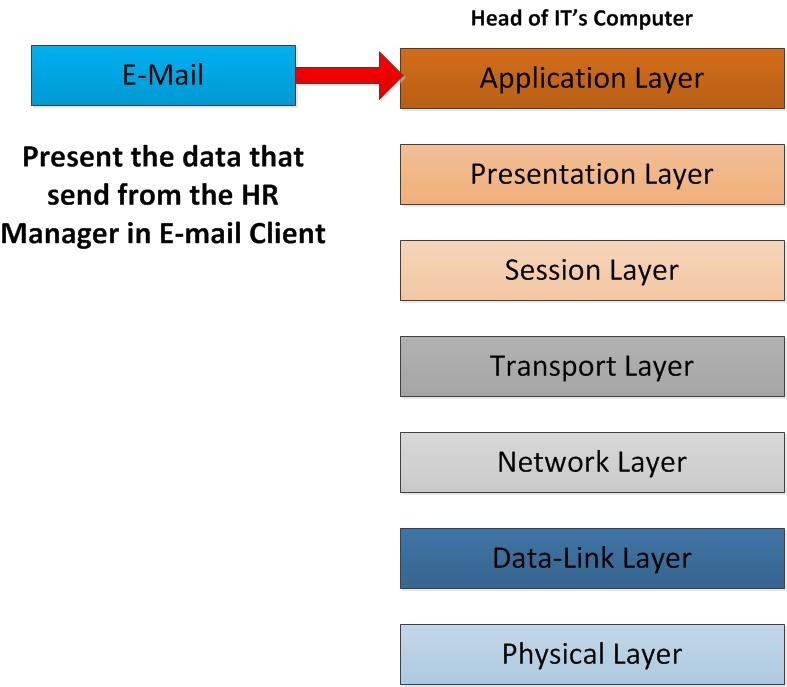
Now it’s everything ready to present the content that HR manager sends in Head of IT’s E-mail Client. All the header details that were added now removed and only the data will be deliver to his email client. With this the whole process is completed successfully.




You solved my problem sir. Thank you very much.
Wow, What a neat document, Thank you sir.
Thank you so much for such a wonderful explanation .You saved my day 🙂
very concise and super explanation!
Thank you so much for detailed explanation.